5 Reasons for Segmenting Your Phishing Simulation Campaigns
- Phishing campaigns are part of security awareness education and training
There are several important reasons for why you would want to segment your phishing simulation campaigns. The first reason is that phishing simulation campaigns are (or should be) an integral part of your overall security awareness education and training program, which should be role-based. The effectiveness of the role-based approach to security awareness education has been recognized by the key information security standard bodies. NIST, in its Special Publication 800-16 rev.1, "Role-Based Model for Federal Information Technology/Cybersecurity Training", states that organizations "need to identify the roles within their specific organization" and "tailor the required or needed skills and knowledge to those roles." PCI Security Standards Council lists determining roles as one of the best practices in organizational security awareness because it would "help organizations deliver the right training to the right people at the right time." Furthermore, some guidance documents, such as FedRAMP Penetration Test Guidance, directly suggest conducting phishing exercises targeted at specific roles (namely the cloud service provider system administrators). If your role-based security awareness education program includes a Phishing module (as it should), one of the best ways to measure its effectiveness would be to run a role-based phishing campaign.
- You want to spear phish
Another reason for segmenting your phishing simulation campaigns is that the attack that is most dangerous to your organization will be tailored to specific recipients. Traditional, or "mass" phishing is still out there, of course. Why wouldn't it be: it costs nothing, requires minimal technical skills, and no information about the target is needed other than the email address, so return on investment is quite high here, even if the number of victims is relatively low. However, most enterprises nowadays face a much more serious threat of spear-phishing attacks. Spear-phishing targets specific individuals or groups using information that is relevant to them to make the bait more attractive. Depending on how determined the attackers are, they may spend months gathering information about your company: names, positions, phone, numbers, samples of internal and external correspondence, contact information of vendors, contractors, and customers, etc. Then one day your employee Alice receives an email from the CEO asking to transfer some funds to a bank in China. The email is using your company's official template, there are no grammar or punctuation errors, it is addressed to Alice by name, and even uses some specific wording that is characteristic to your CEO. And you recently expanded your business to China, so transfer like this is not something out of ordinary. Except this time the money went straight into the pockets of some bad guys who did their homework. This is an example of "CEO fraud", a type of spear-phishing attack that has cost organizations more than $2.3 billion over the past three years, according to FBI. On the other hand, an email offering Bob (who is an avid Star Wars fan with active social media presence) free tickets to a "sneak preview" of the new Star Wars movie can be just as dangerous if it contains malware that will allow attackers access to your internal network. So it would make sense for your simulated phishing campaigns to be targeted at specific individuals and groups as well. Send fake requests to transfer funds to employees whose responsibilities include transferring funds, and send fake Facebook invites to "watch the fight" to employees who are into UFC. What if you have an employee whose role is to transfer money and who likes watching people pummeling each other in a cage? Include them in both groups! It is easy to do with InfoSec Institute's PhishSim, part of the SecurityIQ platform.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
Additionally, segmentation is helpful when employees change their functional roles within the company. With learner groups in place, you won't have to create a new campaign every time a learner gets promoted of transferred to a different department. Just move that learner to the appropriate group and he or she will be automatically included in the phishing campaigns you are running against that group.
- Groups are not always the same as roles
Creating learner groups by functional role within the organization is just one of the possible approaches you can take to segment your phishing campaigns. With the flexibility offered by SecurityIQ PhishSim, you can align your groups with roles defined for security awareness education while also creating learner groups based on different criteria. Creating a group for new hires would be a good idea. You may create several New Hire groups, one for each quarter, for example. You may want to create groups within the same functional role based on geographical regions related to their work, so employees working with Austrian partners would receive phishing emails in German while representative handling Chinese accounts will be phished in Cantonese. If your policies allow, you may obtain information from HR about the banks your employees are using, and group them based on that, so the loyal Chase customers won't ever get Bank of America notifications. We already mentioned sports and movie fans, so the sky is the limit here, just don't get carried away (which is easy to do with a tool like PhishSim) and make sure your learner groups serve a purpose. Once you've caught yourself creating a group for learners whose cat's name is Oliver, it may be a good idea to take a break.
- You want to randomize your campaigns
Helpfulness is one of the human traits often abused in social-engineering attacks (phishing included). It can also hurt the effectiveness of your simulated phishing campaigns if you have employees who are so "helpful" that would do a disservice to their colleagues by notifying them about an ongoing phishing campaign. "Oh, watch out guys, just got another Low Balance Alert! Security is out to get ya!" If you think that this is something that may likely happen in your organization, try introducing a bit of organized chaos to your campaign. Segmentation helps here as well. You can split your groups into even smaller groups, then select different batteries of templates for each group, and start your campaigns a day or two apart. Timing options can be easily customized in Phishsim (see the image below).
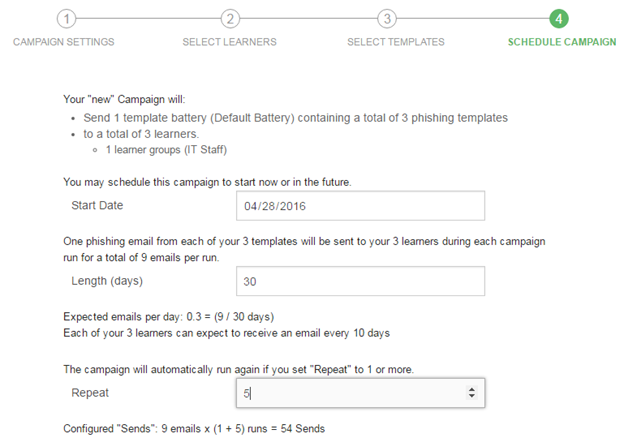
Remember that your groups don't have to contain the same number of people. You can create groups with only one learner if you need to. So when Jim yells out "Here comes a fake Dropbox share!" but he's the only one getting it, maybe next time he will think twice. Don't worry; you will still be able to generate cohort reports for all your campaign runs and see the overall results for all learners. SecurityIQ robust reporting features take care of that.
- You want to experiment
When you get your hands of such a powerful and flexible phishing simulator as PhishSim, you really want to use all of its features to the full extent. Read about a new phishing attack involving real estate transactions? Create a group of learners you know of that are currently involved in selling or buying a house. Create a group of "multiple offenders" and keep pounding them with batteries filled with templates from different categories and of different level of sophistication. After going through the interactive Phishing awareness module enough times (combined with whatever administrative measures your company may feel like implementing as an additional motivating factor), you will see their behavior change. Create a group that represents a cross-section of your organization. Create a group for learners who never fall for phishing baits and employ your most advanced phishing techniques against them: are the really that aware (in which case some sort of company-wide recognition may be appropriate to encourage such habits), or are they just really good at recognizing your simulated phishing emails?
Conclusion

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Whether you are running your simulated phishing campaigns against 100 or 10,000 learners, segmentation is always a good idea. Blanket approach rarely produces truly beneficial results, and this is especially true when applied to phishing. SecurityIQ PhishSim has all the features necessary to help you in instilling secure habits in your employees. IT is up to you to use this powerful tool in a way that will also save some time for, and some money and resource for your organization by delivering the training to the right people at the right time.






