3 steps to get your business cybersecurity-ready in 2022
Imagine sitting down on Monday morning with a cup of coffee and powering up your computer, but instead of being welcomed with your login screen, you’ve got a message that spans your screen reading “Pay $200,000 in the next 48 hours to receive a decryptor to unlock your files.”
This scenario was a reality for approximately 37% of global organizations impacted by ransomware, malicious software that blocks access to a computer or files until a payment is made to a threat actor, in 2021.
The prevalence of ransomware also revealed the impact of cyber incidents can go far beyond fiscal consequences, disrupting healthcare, food manufacturing (meat supplier JBS) and utility providers (Colonial Pipeline) last year. In 2022, cybersecurity experts predict this trend will continue as remote work, e-commerce and cloud-hosted services gain popularity.
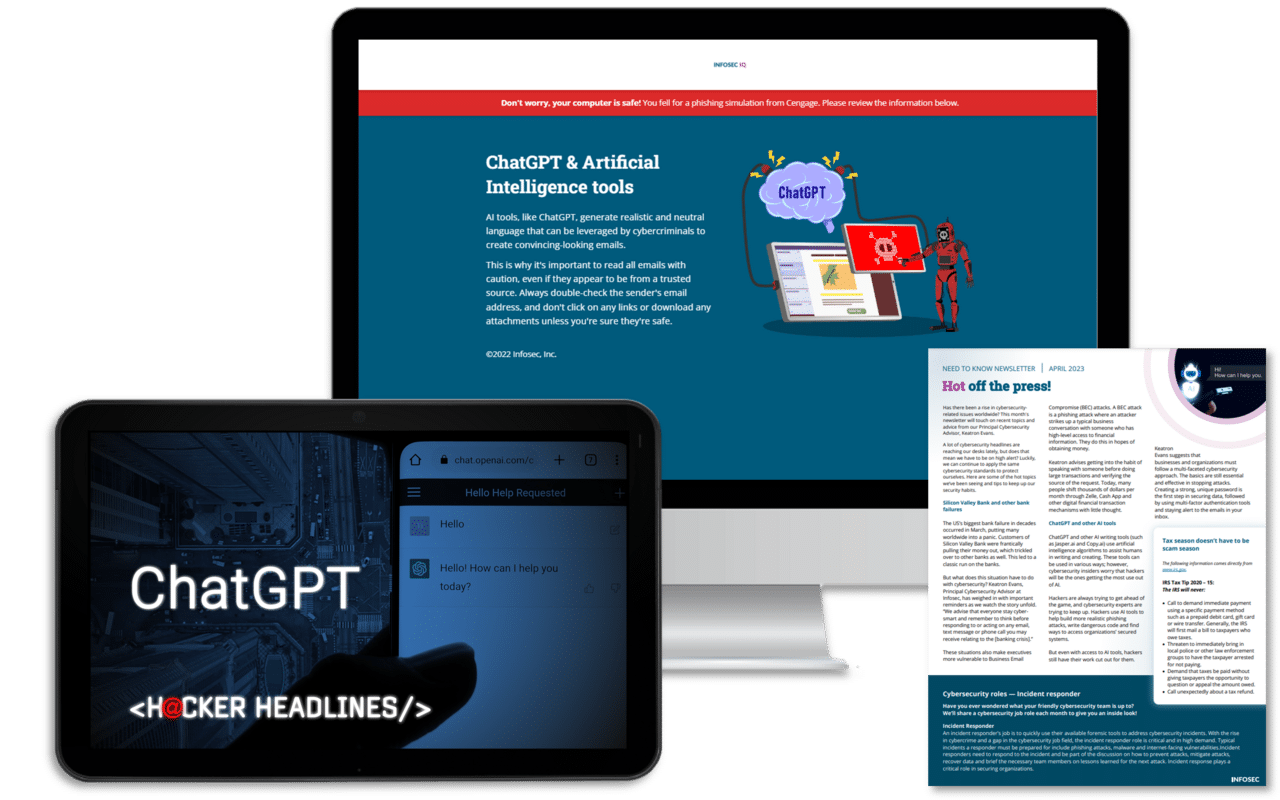
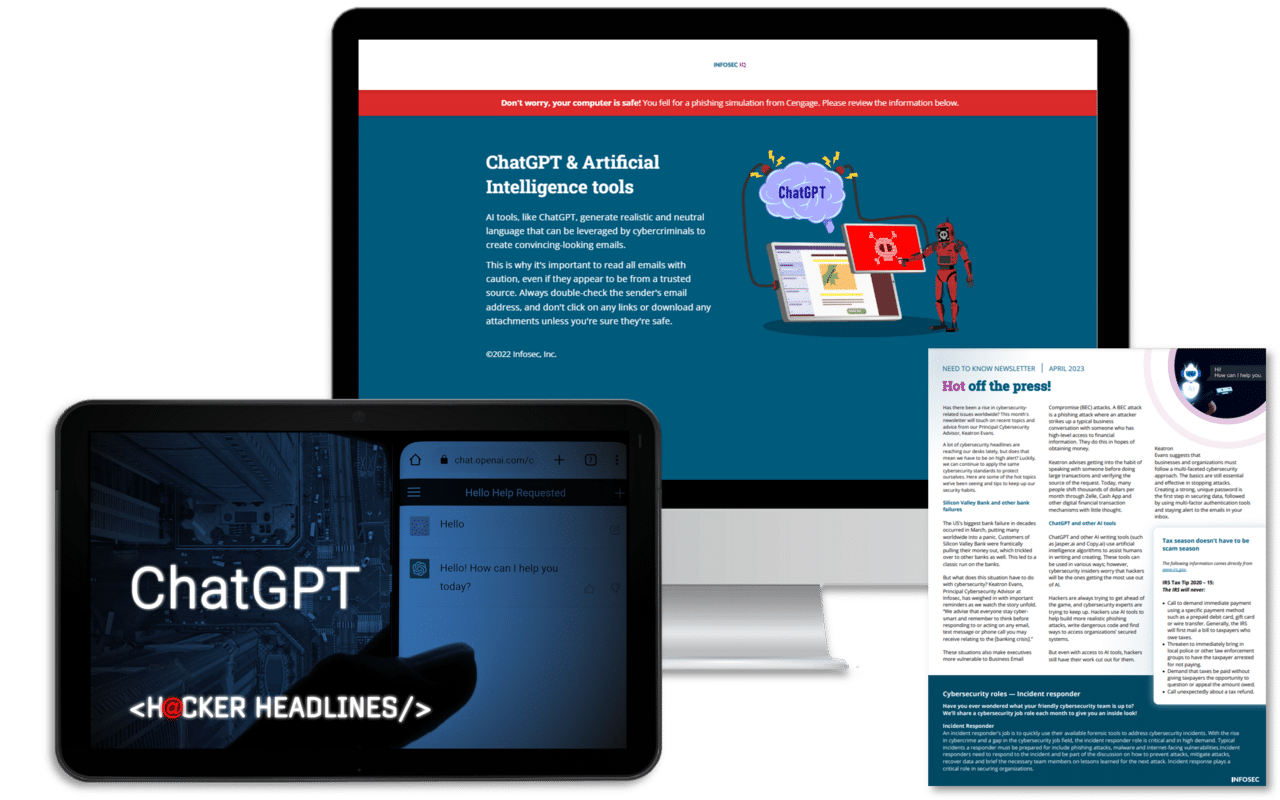
ChatGPT training built for everyone
With a new year upon us, here are three steps businesses should take now to mitigate cybersecurity risks and prepare for 2022.
1. Take time to understand your business’s digital ecosystem and where it’ll grow in 2022
As the saying goes, you can’t know where you are going until you know where you have been. In cybersecurity, you can’t secure an asset if you don’t know it exists. All organizations should start the new year by auditing and inventorying everything (and that means everything) that exists in their digital ecosystem, what security measures are in place today and which suppliers and partners have access to that ecosystem.
A scenario many businesses experienced in 2021 was expanding their hybrid work environments by adding new devices, onboarding new employees remotely, moving to cloud hosting environments and adding new software suppliers to the mix. Each of these initiatives grows the number of ways a cybercriminal could gain access to your network and requires an understanding of how they’re being secured, updated and monitored beyond the implementation stage.
If you’re one of the many businesses migrating to cloud services in the new year, be aware of an expected increase of common cyberthreats in 2022 and prepare for how your business will respond if one occurs. As you start the new year, perform a thorough assessment to see what new gaps have been introduced in your environment, which existing gaps have widened and which ones have shrunk. Not all security gaps are apparent.
The Cybersecurity and Infrastructure Security Agency (CISA) provides free security readiness assessment resources for organizations looking for a systematic and repeatable approach to assessing the security posture of their cyber systems and networks.
2. Invest in security awareness before a cyber incident scare.
Phishing and business email compromise (BEC) will still be preferred tools for cybercriminals in 2022. While many businesses wait until after a scare or cyber incident happens to train their employees about what happened, being proactive and consistent reduces the chance of a threat actor making their way into your organization in the first place.
Both phishing and BEC use email and social engineering to gain your employees’ trust, trick them into providing information or clicking on a link and grant cybercriminals into your system or paying them directly. Since these popular and successful attack vectors rely on employees engaging with malicious emails, the most effective way to prevent these attacks is by teaching people about them, relating risks to people’s everyday lives and ultimately helping end-users be less susceptible to the attacks.
Better yet, adding this “human firewall” to your security strategy does not need to cost you significant time or resources. There are many free or low-cost options for providing security awareness training to your employees, including many free resources like phishing risk tests, training program roadmaps and security awareness resource toolkits with posters, presentations and quizzes to consistently engage your team.
3. Prep your IT team for new threats or find an IT partner who can
Cybersecurity is still an emerging field, especially for IT professionals who wear many hats. To help your business and IT teams respond to emerging cyberthreats, you should invest in training your technical IT and security staff.
We’ve seen even well-staffed teams struggle with responding to ransomware incidents in the past year, despite those same teams excelling when responding to everything else. There must be a more concentrated and directed effort to ransomware remediation in general, emphasizing tabletop exercises and hands-on training that put these skills to the test.
Imagine how overwhelming tasks like contacting authorities, preserving forensic evidence, managing internal expectations and restoring backups (in the many instances that a decryption key may not work) can be for teams not trained to manage a ransomware incident. These skills and processes are far too complicated and high risk for even seasoned IT professionals to “learn as they go.” Oftentimes, not having an established plan or training results in extended downtime, team burnout and the need for high-cost consulting services at the last minute. This scenario is just one example, but one that has often happened this year.
Phishing simulations & training
![]()
Managed security service providers (MSSPs) can be a valuable resource for SMBs, providing the expertise needed to secure infrastructure when they cannot dedicate a full-time staff member to security. If you don’t or can’t have this expertise in-house, take time now to form adequate partnerships with external experts before you need to utilize them. In 2021, many organizations that found themselves looking for a partner at the last minute paid much more than those with an ongoing partner who could help them every step of the way.
Putting your security to the test
Although there is no one-size-fits-all approach to measuring and establishing the “correct” level of security coverage, testing for vulnerabilities is an effective method to understand what coverage is needed. Penetration testing allows organizations to evaluate their security and IT infrastructure. At the same time, simulated phishing tests, cybersecurity assessments and culture surveys measure how prepared your employees are for the cyber threats they face and how likely they are to adopt behaviors that keep your organization secure.
By identifying vulnerabilities, organizations can plan to address their most significant weaknesses and set themselves up for a secure 2022.