The ZeroAccess Botnet Revealed
There has been a large spread of Botnet-related threats in the web world recently. Now when we talk about botnets, it is basically a collection of code linked to each other through some communication mechanism through which it may get commands to perform certain actions. These may be also known as a collection of bots/zombies that are controlled a central server through commands. A very practical example is in case of distributed denial of service attacks in which a collection of bots (botnet) attack a particular IP address or a client and hamper its services. A recent article was covered in my article on the Spamhaus Ddos Attack.
On similar lines, the ZeroAccess Botnet is a specialised Trojan horse that affects the Windows operating systems and downloads malware to an infected machine to form a botnet. Read about how we reverse-engineered the ZeroAccess trojan here. With reference to Symantec's analysis of this Trojan, it is said to use an advanced rootkit to hide itself. To set up its own botnet system, this Trojan creates its own hidden file system, downloads more malware from the connected environment, and opens up a back door for access on the compromised system. The attacker is then able to perform actions as per his requirements and the victim's system becomes a part of the botnet. The name ZeroAccess has been coined due to the fact that a string found in the kernel driver code points to the original project folder ZeroAccess. It is also code named max++ due to its capability of creating a kernel object __max++>
Learn Digital Forensics
[caption id="" align="alignnone" width="632"]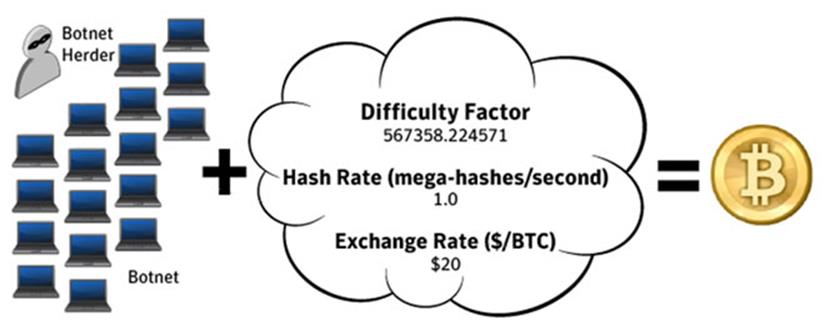 Click to Enlarge[/caption]
Click to Enlarge[/caption]
In a recent report, FortiGuard Labs revealed ZeroAccess as the number one threat this quarter as reported by FortiGate devices worldwide. Now the attack vector of ZeroAccess was primarily focussed on Bitcoin mining. Bitcoin is an online digital currency, not managed by any government, that relies on an Internet-based network. It is being heavily used in the underground market for illegal activities such as drug trafficking, arms dealing, black hat hacking, etc. These Bitcoins are mined by unblocking blocks of data that produce a pattern when the Bitcoin hash algorithm is applied to that data. The miners use high-end machines with graphics card for GPU processing to unlock these mines. The machines, once set, can be allowed to run the algorithms endlessly and keep mining the Bitcoins. GPUs are more efficient in the mining applications than CPUs, so usually you would find multiple graphic cards attached with a high-end CPU which makes a deadly Bitcoin mining machine. A recent study by Bloomberg calculated $150,000 in power costs due to large consumption by these powerhouse mining machines.

Back to the ZeroAccess Botnet: It was originally founded in July 2011 and it has affected around 9 million systems. This botnet usually spreads around through a series of attack vectors such social engineering, where a user would be lured upon clicking a malicious executable. Now this malicious executable may be packed up as a keygen or named as well-known software. In both scenarios, a user gets compromised once he clicks the executable. The user may be compromised also through an advertising campaign that makes a user click a particular advertisement and in turn gets redirected to a malicious website. Its attack vectors further include a manual infection scheme in which a person is paid for installing a rootkit on a system in exchange for money. The rates vary from about $100 for every 1000 infections and are estimated to go up to $500. Another dangerous motive it had was to make money through the pay-per-click advertisement campaigns. This task was performed by downloading an application from the exploit kit or the command server and does web searches using this application for the specific advertisement. Once the advertisement is found, it clicks on the advertisement which gives revenue to the program user.
Kaspersky has recently reported that spammers have launched a fraudulent social engineering campaign, using Skype, that sends messages to contacts containing links of malicious websites. Once the system infects a system it uses the system's processing power to mine Bitcoins.
Through a recent analysis, Kaspersky discovered this is Trojan.Win32.Jorik.IRCbot.xkt. As discovered by Symantec, the Trojan gets distributed using the Blackhole Exploit Toolkit and Bleeding Life Toolkit. The Blackhole toolkit is an exploit toolkit that has been recently in the news because of its large usage by the hackers. When a victim visits a site that has been infected by a malicious iframe, this iframe redirects the user to the Blackhole exploit server. Also when a user visits the Blackhole server website, the server gets activated to exploit the vulnerabilities on the user's browser. Nowadays we have multiple applications on the user machine, such as Internet Explorer, Java, Adobe, and many more. These are often not updated and hence the toolkit easily exploits the client-side defenses. Symantec recently revealed a few vulnerabilities that the Blackhole and Bleeding Life toolkit exploited. These are:
- Microsoft Windows Help and Support Center Trusted Document Whitelist Bypass Vulnerability (BID 40725)—The Microsoft Help and Support Center was prone to a trusted document bypass vulnerability that allowed remote untrusted attackers to access arbitrary help documents, which led to various attacks.
-
Microsoft MDAC RDS.Dataspace ActiveX Control Remote Code Execution Vulnerability (BID 17462)—The Microsoft MDAC RDS.Dataspace ActiveX control was vulnerable to remote code execution. An attacker could exploit this issue to execute code in the context of the user visiting a malicious web page.
-
Sun Java Runtime Environment ActiveX Control Multiple Remote Buffer Overflow Vulnerabilities (BID 34931)—Sun Java runtime environment was prone to multiple remote buffer-overflow vulnerabilities because the application failed to perform adequate boundary checks on user-supplied data.
- Adobe Reader 'util.printf()' JavaScript Function Stack Buffer Overflow Vulnerability (BID 30035)—Adobe Reader was prone to a stack-based buffer-overflow vulnerability because the application fails to perform adequate boundary checks on user-supplied data.
-
Adobe Acrobat and Reader Collab 'getIcon()' JavaScript Method Remote Code Execution Vulnerability (BID 34169)—Adobe Acrobat and Reader were prone to a remote code-execution vulnerability because the software failed to sufficiently sanitize user-supplied input.
- Adobe Reader and Acrobat 'newplayer()' JavaScript Method Remote Code Execution Vulnerability (BID 37331)—Adobe Reader and Acrobat were prone to a remote code-execution vulnerability. An attacker could exploit this issue to execute arbitrary code.
Ultimately a Trojan gets downloaded on the victim computer and posts a unique id to the command and control server. The registry changes that this Trojan is said to make in the victim system are:
- HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServices[FILE NAME OF INFECTED DRIVER]"ImagePath" = "*"
- HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServices[FILE NAME OF INFECTED DRIVER]"Type" = "1"
- HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServices[FILE NAME OF INFECTED DRIVER]"Start" = "3"
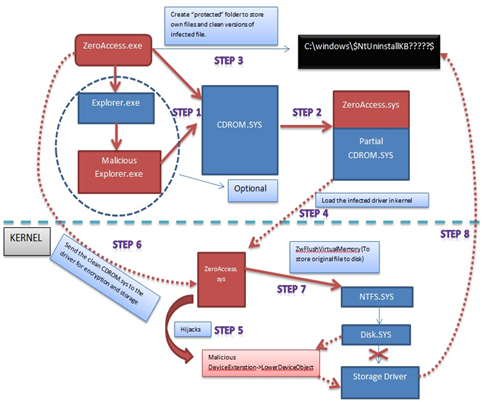
This may be also in the form of a keygen/crack as discussed earlier for commercial software. The websites hosting these cracks often contain malware. We had recent news of the advertisement servers being infected with malicious code and, as such, the websites running their advertisement campaign in turn were affected. Once a user simply clicks on the executable of these toolkit servers, the dropper would silently suspend a part of Windows file protection (WFP) that handles the repair of protected Windows operating system files. Then this Trojan overwrites a system driver with its own kernel mode driver and loads it. The driver file is located alphabetically between %System%Driversclasspnp.sys and %System%Driverswin32k.sys is overwritten with the Trojan's own code. The communication largely depends on peer-to-peer technology, making it possible for the authors to improve upon the Trojan and add functionality.

Here is an example attack vector from ZeroAccess, where a copy of the game Skyrim is made malicious by ZeroAccess. The installer was a NSIS archive. During the attack, a file was dropped at "%Profile%Application Dataskyrimlauncher.exe" and a screen showing the game installer appeared. Again in the background an encrypted 7zip file gets dropped and executed. These ZeroAccess droppers from exploit toolkits or malicious executables specially crafted to bypass antivirus detection. This technique is known as making the executable fully undetectable (FUD). The executable is tried and tested against different antivirus databases for evasion. These droppers have recently been using hardware breakpoints as part of its unpacking routine, which makes attaching a kernel debugger to the target system more challenging. An extremely cool feature of the ZeroAccess dropper is that a single dropper will itself install the malware depending on the architecture of operating system like 32 bit or 64 bit.
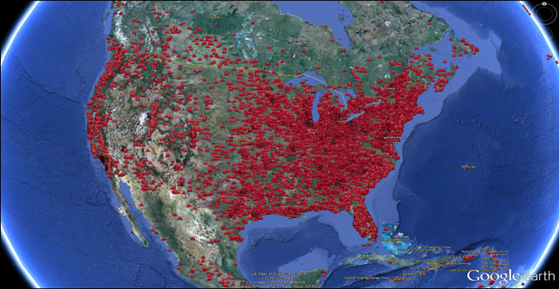
Here is an image of ZeroAccess botnet infections in USA as visualized in Google Earth posted by F-Secure on its blog.
Symantec published a security advisory for protection against the ZeroAccess Trojan. Users were asked strictly not to click on links that look fishy or advertisement popups claiming different prizes or other scenarios. They should not try to access cracks of copyrighted software that may be keygens for activating these cracked original softwares. The Trojan intelligently bypasses firewalls and makes a TCP connection on port 13620 with the command and control server. According to the advisory, it is advised to block access to these IP addresses through a firewall or on the router since the threat was observed to contact these IP addresses:
- 69.176.14.76
- 76.28.112.31
- 24.127.157.117
- 117.205.13.113
- 200.59.7.216
- 113.193.49.54
It was also found to contact the following NTP servers:
- ntp2.usno.navy.mil
- ntp.adc.am
- chronos.cru.fr
- wwv.nist.gov
- clock.isc.org
- time.windows.com
- time2.one4vision.de
- time.cerias.purdue.edu
- clock.fihn.net
- ntp.duckcorp.org
- ntp.ucsd.edu
- ntp1.arnes.si
- ntp.crifo.org
- tock.usask.ca
The ZeroAccess botnet is the first of the top five most prevalent pieces of botnet malware, followed by the Jeefo, Smoke, Mariposa, and Grum botnets.
References
http://en.wikipedia.org/wiki/Botnet
http://en.wikipedia.org/wiki/ZeroAccess_botnet
http://www.symantec.com/security_response/writeup.jsp?docid=2011-071314-0410-99
http://investor.fortinet.com/releasedetail.cfm?ReleaseID=755549
http://en.wikipedia.org/wiki/Bitcoin#Bitcoin_mining
http://techcrunch.com/2013/04/13/the-cost-of-a-bitcoin/
http://www.infoworld.com/t/mobile-security/bitcoin-mining-botnet-zeroaccess-jumps-top-security-threat-216185
http://www.symantec.com/connect/blogs/blackhole-theory
http://www.surfright.nl/en/hitmanpro/prevalence/january-2012
http://nakedsecurity.sophos.com/zeroaccess2/
http://www.symantec.com/security_response/writeup.jsp?docid=2011-071314-0410-99&tabid=2
http://blog.fortinet.com/Bitcoin-and-the-ZeroAccess-Botnet-/
http://www.f-secure.com/weblog/archives/00002430.html
http://www.c114.net/news/213/a727099.html
http://blogs.mcafee.com/mcafee-labs/targeting-zeroaccess-rootkits-achilles-heel
Learn Digital Forensics
http://www.dailytech.com/GPU+Roaring++You+May+Be+Infected+With+a+Bitcoin+Trojan+Says+Symantec/article22474.htm





