The System Networking of Biometrics
Overview of Last Articles
Our past articles (in total, five of them) have reviewed what it takes to procure and deploy a Biometric System. As it was reviewed, implementing one be a very a daunting task, even if it is the simplest of implementations.
For example, even if a Biometric Modality is just being used for a Single Sign On Solution (SSO), there is still much planning which needs to be done. The intent of an SSO is to replace the use of the password.

FREE role-guided training plans
However, since the employees of a business or a corporation are so used to using the username/password combination, the drastic change to using a Fingerprint Recognition or an Iris Recognition System could cause much resistance regarding adoption. Therefore, careful planning is required to ensure that all will go well.
On the other extreme, if a large scale Biometrics implementation is to be done, this will be a very complex task. For instance, there could be a combination of Biometric modalities which could be used with another, and all of them networked together and connected to a central server.
The other considerations are if these modalities will be used as the primary means of defense, or if it will be tied into a legacy Security system; and the databases which need to be created (this is where the Biometrics Templates will be stored, and the Verification/Identification transactions will take place).
To properly plan for all of these scenarios, a Biometrics Project Management plan is needed. This process details all of the Security requirements which the anticipated deployment will meet, and all of the tools, accessories, and software which will go with it. It involves many stakeholders, ranging from the C-Level Executives to the IT staff to the Network/Security Administrators, and even the employees.
It is important to keep in mind also that this is a process which evolves over time and can take a great deal of effort to accomplish. However, in the end, the efforts will have paid time, with the end resultant being a smooth and successful deployment, with a high rate of end user adoption.
However, as our last article reviewed, before the full-blown implementation can be accomplished, it must first be examined in a test environment. This will help to ensure that any issues will be resolved and that the modalities will operate and deliver results in the environment they are intended to be placed in.
To also confirm that all will go well, the use of Biometric Middleware was also reviewed. For example, if two modalities are being used which have no existing connectivity with each other (such as using a Facial Recognition System in tandem with a Signature Recognition System), then the Middleware is needed to act as the "conduit" between the two.
Finally, it is also important to remember that once a Biometric procurement and deployment has been successfully accomplished, it too will need to be maintained and upgraded over time.
Just like the planning process was dynamic in nature, so too is making sure that the new Biometric System is successful in meeting the needs of the business or corporation, and will continue for the intended period in which they will be used.
As mentioned earlier, it is quite possible that the Biometric modalities will all be networked together, in some sort of fashion. There are different methodologies which can be used, with differing advantages and disadvantages. This is the focal point of these next articles.
An Introduction to the Networking Topologies
A very important aspect of the overall Biometric System Architecture is that of the networking systems which can be applied. When a C-Level Executive thinks about a Biometric System, the image of a standalone Fingerprint Scanner or even that of an Optical Sensor attached to a wireless device or a Smartphone very often comes to mind. However, that often gets overlooked is that many Biometric modalities can be networked physically together or even via wireless protocols.
In fact, many Biometric Systems of today consist of not just one device; they consist of many devices which are all interlinked together and can communicate with another in real time. Because of this interlinking functionality, the sharing of Biometric Templates when and where as needed can accomplish in just a matter of a few seconds, as well as the metadata which is associated with the Templates.
Network Processing Loads
When the Biometric Devices are all connected with one another, the Transaction Processing Load for the Verification and Identification based applications can be shared with distributed network resources. A perfect example of this is that of an international airport. Today, both Facial and Iris Recognition is being used to track and identify passengers from all over the world.
Because of this sheer bulk, it is impossible for just one Facial Recognition or Iris Recognition to conduct all of these large scale identifications. Therefore, many devices are placed at the various, strategic locations throughout the airports. They are all networked together to ensure that all of the Transaction Processing is equally distributed amongst all of the modalities.
Also, another key advantage with networking all of the Biometric Devices together in such a large environment is that if there is a system failure in one trunk of the segment, the other modalities will be able to quickly make up for any downtime in just a matter of a few minutes.
Also, from a surveillance perspective, if there happens to be terror suspect covertly lurking in the background, there is a much higher statistical probability that he or she will be picked up by one of these modalities, somewhere at some point from within this network.
A Networking Scenario
The other major type of networking scenario that can take place is when all of the Biometric Devices are all still interlinked with another; but in turn, all of these modalities in the overall system design are also connected to a Central Server (perhaps even more than one server can be utilized, which is best exemplified by the AFIS Biometric Databases which are administered by the FBI).
A good example of this is that of Physical Access Entry. Imagine if you will, a very large corporation or business such as that of a warehouse with literally thousands of employees. Suppose that Fingerprint Recognition is the modality of choice, and the respective scanners are installed all over the factory space, at the major points of entry and exit.
Obviously, just one Fingerprint Scanner cannot do all of the work of confirming the identity of each and every employee (theoretically it could, but technically, it would overload the Central Processing Unit in just a matter of minutes).
However, with the Fingerprint Devices all networked together and to the Central Server(s), all of the Transaction Processing can take place in literally just two seconds or less, and very efficiently. This is because the sheer computing power and the resources that the Central Server(s) possess are much greater than that of just one Fingerprint Scanner.
The Biometric Networking Topologies
As it is obvious, both the C-Level Executive (in this case, the CIO) and the IT staff must have a broad understanding of the various networking topologies that a Biometric System can take up and how that particular networking will thus interface within the existing Security Infrastructure.
Thus, the goal of this and the coming articles is to provide the C-Level Executive with a basic understanding of the networking concepts and designs that a Biometric System can take on.
However, it is also important to keep in mind that the specific design of a network structure of a proposed Biometric System will be heavily dependent upon the new Security requirements, which will be dictated by the needs of the business or corporation.
However, it is important to review some key concepts which make up a network in general before attempting to explore the various networking topologies. This section will examine the following key aspects:
- Data Packets
- The Data Packet Subcomponents - Getting Ready for Network Transmission
Data Packets
In the world of networking, and even including that of Biometrics, one of the most fundamental units of connectivity is that of the Data Packet. For example, every time that an E-Mail is sent, or a Biometric Template is sent to a Central Server for storage and Verification/Identification processing; it is done via the Data Packet, as illustrated below:
In other words, for two Biometric Devices to communicate with the Central Server or even with each other, the data must first be broken down into smaller bits and travel across the network medium. Upon reaching the final point of destination, the data must then be "reassembled" again into a format which can be understood either by the next Biometric Device or the Central Server.
For instance, a regular size Biometric Template would be simply too big regarding size to traverse quickly and easily across the network medium. To accomplish the task, the Biometric Template must be broken down into very small bits, which are also known as the "Data Packets." This can also be thought of like the broken up Biometric Templates.
These Data Packets then travel across the network and are then put back together again into their original format once they arrive at their point of destination. As a result, the Central Sever or the next Biometric Device can then understand the data it has just received, and from there, proceed with the appropriate actions or processes.
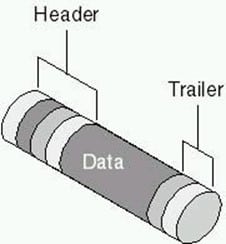
A Data Packet consists of a header, the payload, and the trailer. The header specifies the final destination of the Biometric Template (for example, whether or not it is the Central Server or another modality). The payload section consists of the broken-down version of the Biometric Template and its associated metadata.
The trailer possesses the ability via a mathematical algorithm (known specifically as the "Cyclical Redundancy Check" or "CRC") to ensure that the Data Packet gets to the right destination during the intended time frame. An illustration of a Data Packet with these components can be seen below:
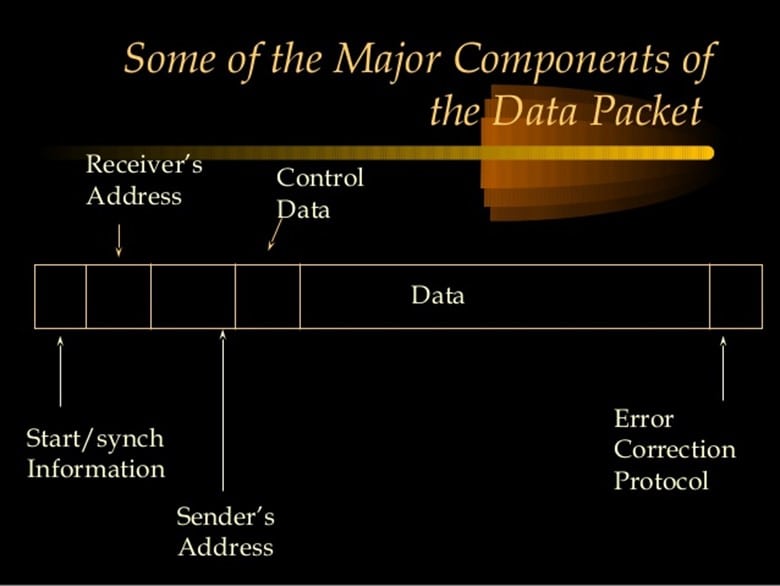
The Data Packet Subcomponents-Getting Ready for Network Transmission
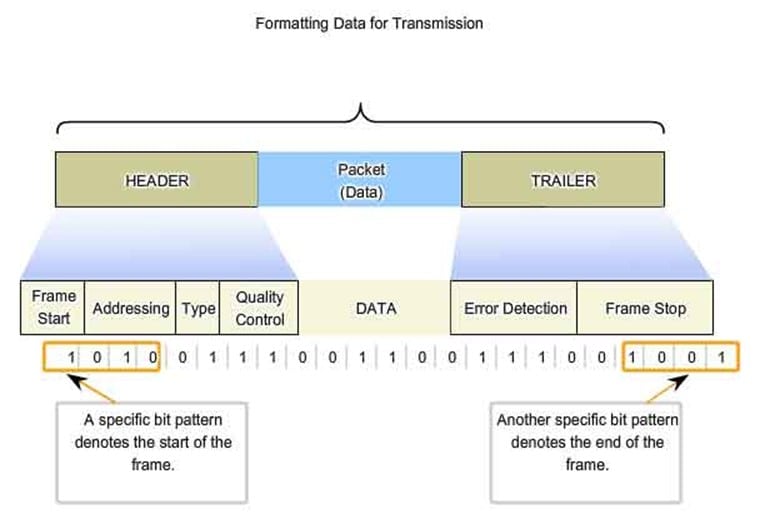
In technical terms, the Data Packet is broken down into various sub-components, which are described as follows:
-
4 Bits:
This specifies the version type of the Network Data Packet Protocol in which the Biometric Template resides in. Currently, there are two types of Network Protocol Data Packets, which are the IPv4 and the IPv6. Also, this segment of the Data Packet contains what is known as the Internet Header Length, and this specifies the exact length of the header of the Data Packet which contains the Biometric Template.
-
8 Bits:
This part of the Data Packet contains what is known as the "Quality of Service," or "QoS" for short. This merely refers to what the priority level the Data Packet will possess regarding the order of precedence upon reaching the Central Server or the next Biometric Device. These Bits also dictate, to a very small degree, which Biometric Template has what level of priority regarding Verification and Identification transaction processing. This part of the Data Packet also specifies the "Exact Time to Live." This is the number of hops across the network medium that the Data Packet is allowed to take to reach the Central Server or the next Biometric Device before it is expired and discarded. Obviously, it is important to keep the number of hops to the most minimal possible, to streamline network communications efficiency. It is in this part which specifies the Network Protocol that the Data Packet will travel across on (most likely it will be the TCP/IP Protocol).
-
16 Bits:
This contains the length of the Data Packet itself. The length is primarily determined by the size of the Biometric Template. This part of the Data Packet also possesses the Header Checksum, which is also known as the CRC Algorithm, as discussed in the last section. This is used to check for the integrity of the Biometric Template once it reach es the Central Server or the next Biometric Modality. The CRC Algorithm also detects any errors which may have occurred during the transmission of the Data Packet.
-
32 Bits:
This part of the Data Packet also houses the destination address (in other words, what the receiving point is). It also consists of the of the source IP Address from which the Data Packet originates (in these scenarios, it will always be the sending Biometric Device).
Conclusions
When implementing a Biometric System, there is no doubt that first deciding upon the choice of modality, the social implications it will bring, and the design of the related software applications (in particular the database) are of utmost importance. This is all addressed in the Biometric Project Management plan.
However, equal consideration has to be given to the network aspect of the Biometric System as well. Perhaps deploying just a few Biometric Devices in a standalone mode is not difficult, but imagine the implementation of many modalities in a very large corporation or business. All of these needs to be networked together, in some degree or another. There are many aspects which need to be taken in this regard.
For example, will all of these modalities be interlinked together in their own separate component in the overall network trunk, or will they be integrated into the existing Security system? If it is the latter, much sthought and consideration has to be given to the design of the overall Network Infrastructure so that the new Biometric devices will be able to co-exist effectively with the legacy Security devices.
Our next article will further review the networking aspect of Biometrics, with a focus upon the various Network Protocols, a technical review of TCP/IP, and the major Networking Topologies.
Sources
http://www.csl.mtu.edu/cs4451/www/notes/Network%20Topologies.pdf
http://www.mecs-press.org/ijcnis/ijcnis-v5-n10/IJCNIS-V5-N10-7.pdf
https://eprint.iacr.org/2016/803.pdf
https://pdfs.semanticscholar.org/aeb0/fef45207dde803a12493f56504ec989bf25e.pdf
https://www.ics.uci.edu/~givargis/pubs/J28.pdf
https://pdfs.semanticscholar.org/44d0/14961f7905e9c41caec792635b9a86774816.pdf
http://people.idsia.ch/~nagi/conferences/cspa_face_recognition.pdf
http://alumni.cs.ucr.edu/~drougas/publications/isorc2006services.pdf
http://cs.brown.edu/research/borealis/public/publications/sigmod04.demo.pdf
http://cs.brown.edu/research/db/publications/vldb07_tatbul.pdf
http://www.ecs.umass.edu/ece/wolf/pubs/globecom2004.pdf
http://www.ece.ubc.ca/~teerawat/publications/NS2/15-Packets.pdf
https://www.cs.princeton.edu/courses/archive/spring09/cos461/docs/lec03-packets.pdf
http://www.eurim.org.uk/activities/netgov/9911paperinternettech.pdf
http://www.ftdichip.com/Support/Documents/TechnicalNotes/TN_116_USB%20Data%20Structure.pdf
http://www.winlab.rutgers.edu/~narayan/PAPERS/wang_scheduling.pdf

What should you learn next?
http://www.o3bnetworks.com/wp-content/uploads/2015/02/white-paper_latency-matters.pdf




