Spear-phishing statistics from 2014-2015
Learn the best practices for developing a security awareness training program that is engaging. Engaging awareness programs have been shown to change more users' behavior and are seen as an asset for your organization instead of annoyance.
Phishing simulations & training
-----------------------------------------------------------------------------------------------
What is spear-phishing?
A spear-phishing attack consists of a message (in an email, SMS or in some instant messaging application) that is carefully crafted in order to lure a person into downloading a malicious attachment, or clicking on a malicious link. It differs from traditional phishing attacks in that spear-phishing attacks require research before they are executed.
A traditional phishing attack might occur when someone sends a message to thousands or even millions people with the text "OMG! I cannot believe you are in that video <LINK>" whereas a spear-phishing attack would consist of examining carefully the target and his habits. For example, if you mark yourself as attending an event in New York next week but you have set your location to Boston in Facebook an attacker might send a message resembling this: "Hi, John. I heard you are going to New York next week. While you are there, you should definitely check this wonderful restaurant <LINK SUPPOSEDLY TO A RESTAURANT> there, I am sure you would love it!"
Trend Micro's predictions for 2014 pinpoint that in 2014 spear-phishing attempts amongst other targeted attacks will increase in volume as cyber criminals take advantage of open-source research. But is there any proof that spear-phishing increased from January 2014? How about its increase compared to 2015? Did it also increase between 2013 and 2014? The graphic below sheds some light on these questions.
How widespread is spear-phishing, and what are the attack volume trends?
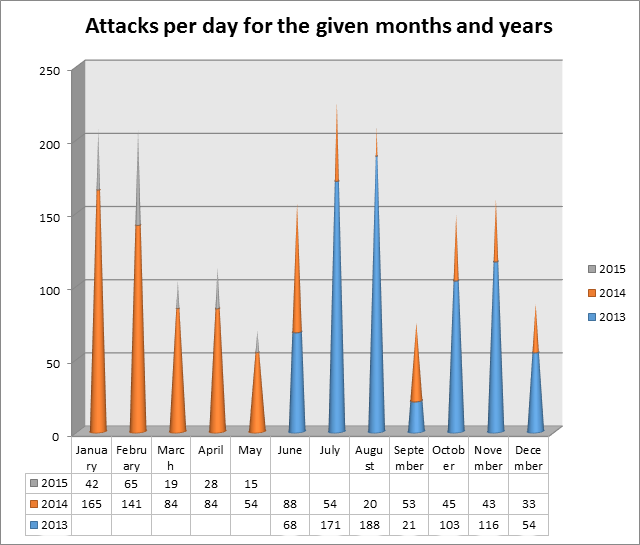
The chart does not include the first 5 months of the year 2013 and it includes the months of year 2015 up to but not including June. However, it provides sufficient data for some conclusions to be made. You can see that the first five months of 2015 has ended with a substantially lower number of spear-phishing attacks compared to 2014 which could lead to us to the conclusion that spear-phishing attacks are declining in volume. You can also see that the prediction of Trend Micro that spear-phishing attacks would increase in 2014 mat not necessarily be fulfilled if you compare the last 7 months of 2013 with the last 7 months of 2014 but we do not have the whole picture for that period.
Most used attachment extensions for spear-phishing in 2014
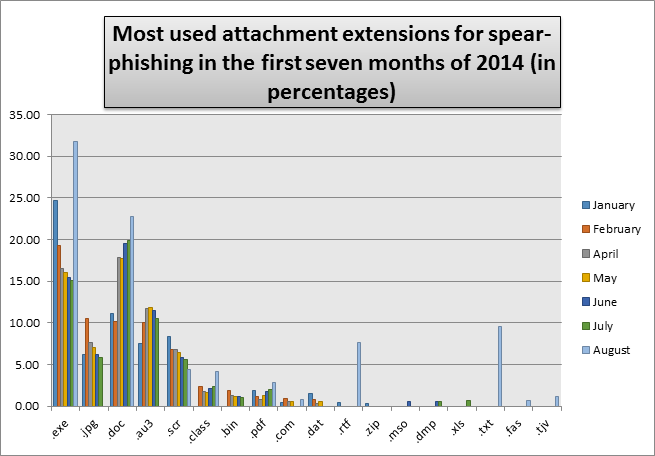
You can definitely spot a trend here. There are certain file types which are being repeatedly used throughout the months and in large volumes. Those are file types that are either executable (and therefore can easily execute arbitrary commands on the system/add remote access), widely used file types which would have a better chance of being accessed or/and file types which are used by programs which have many known vulnerabilities.
The file extensions .com and .exe contain an executable file. It is easy to gain remote access when a user downloads and opens such a file. The file itself could easily be a malware with a nice icon or/and a tricky and luring file name such as your-ex-taking-drugs.jpg.exe or with added Unicode character U+202E that can trick systems into displaying file names like myjpg.exe into appearing like myexe.jpg . The .exe file format is mostly used in Windows.
The file extension .jpg is generally more secure than .exe as it is not an executable file but a binary image but it can still contain malicious code and get you infected. In most cases, exploiting the .jpg extension happens when the user opens the image in some picture viewing program that has flaws in it which themselves could be exploited by the malicious image to gain access to the system. For example, if you use include() function to read images in PHP attackers can inject PHP code within the image that will be executed by your server. A benefit for attackers is that .jpg files can be read by most famous operating systems.
The file extension .doc belongs to the Microsoft Word program in Windows, it is highly used and vulnerabilities in the program exist such as VBA macros which could allow arbitrary commands to run on the user's machine.
.scr is the file extension for Windows screensavers but it can also allow code to run on your system.
.au3 holds a file created with AutoIt v3 and its purpose is to automate commands for Windows similar to Windows Powershell which makes it dangerous itself.
Most used attachment extensions for spear-phishing in 2015
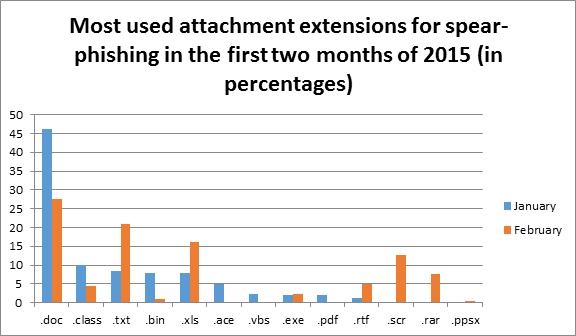
You can see that in the first two months of 2015 the exploit tactics have changed. The .exe file type has fallen out of favor probably due to being widely recognized as malicious and has become ineffective and because security systems on the users' machines and in email clients/applications detect and block the malicious attachments. We see a big increase in the .txt file usage. .txt files are mostly harmless but attackers probably rely on inserting double file extension or using the left to right override Unicode character. A txt file can contain a virus but you would not execute it unless you open it with the right program. We also see a dramatic increase of exploiting vulnerabilities in Excel applications (.xls). There is a new file format for Excel documents since 2007 (.xlsx) but many people out there are still using the old .xls extension. There are more than 20 vulnerabilities for Microsoft Excel dating back to 2002 that attackers may try to utilize to launch DoS attacks in cvedetails.com alone (http://www.cvedetails.com/vulnerability-list/vendor_id-26/product_id-410/opdos-1/Microsoft-Excel.html)
Top ten industries targeted by spear-phishing in 2014
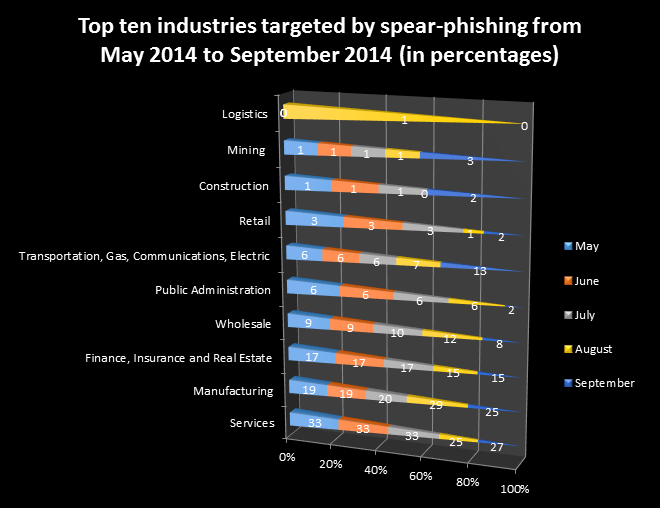
Within the chart, you can spot that attacks against manufacturing has increased from May to September. Symantec believes the manufacturing sector became a top target for cyber criminals since 2013 because attackers are aiming at the supply chain – contractors and subcontractors are more susceptible to attacks than governments and are often in possession of valuable intellectual property. It further believes that by targeting manufacturing companies in the supply chain attackers also collect sensitive information about larger companies. We see that the services sector is taking a top place but it does not increase in popularity. The services sector is preferred for its immediate financial benefits and monetization in most cases but subsectors such as the financial services can also provide value in the long-term such as data about commercial projects, access to aggregated data amongst many other reasons.
We also see an increase of attacks against the broad set of sectors Transportation, Gas, Communications and Electricity and other minor changes of the other sectors. Attacks against public administration remain relatively static throughout the examined period except for the last examined month (September) where they decrease in favor of the utilities sector.
In the examined months, Services, Manufacturing and Finance, Insurance and Real Estate are the sectors that are targeted the most by spear-phishing messages.
Top ten industries targeted by spear-phishing in 2015
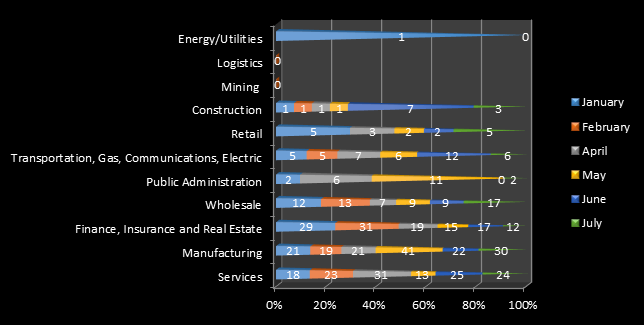
You can see that May 2015 reveal a peak in spear-phishing attacks against the manufacturing industry while July also shows a large increase of spear-phishing attacks against the wholesale sector. Nils Onsager, the Director of Security Information Technology of CohnReznick warns that small manufacturers should also worry as they may be objects of cyber-attacks as well. The fact that they are small usually means they are easier to hack as they do not have the necessary technological sophistication and they could easily become targets of attacks. As we discussed before, manufacturing companies often hold precious intellectual property. The thing is that small manufacturing firms frequently possess intellectual property belonging to larger manufacturers, which makes them an easier target while still remaining lucrative for attackers.
The wholesale sector is highly targeted (especially in July) as it is yet another data-rich sector similar to the services, finance and retail sectors. Frequently, the attacks on those sectors target customer lists or IP as Tom McDermott, director of the CohnReznick Advisory Group stated.
The mining and the logistics sectors are no longer in the top 10 in the examined months of 2015 and attacks against the public administration seem to vanish from the top 10 in July after hitting a peak in May 2015.
In the examined months, similar to 2014, Services, Manufacturing and Finance, Insurance and Real Estate remain the sectors that are receiving the highest volume of attacks. In 2015, we see again a peak in the attacks against the Transportation, Gas, Communications and Electric combined sectors (in June) However, we also see peaks in the attacks against the Wholesale (July) and the Public Administration (May) sectors.
How effective is phishing and spear-phishing?
It has been estimated in 2015 that it takes 1 minute and 20 seconds for an employee in a company to open a phishing email. Taking the bait that quickly leads to lack of time to detect and defend against phishing. According to Verizon, 23% of recipients open the phishing emails. Of course, just opening it would most likely do no harm but it has been estimated that 11% of the recipients actually open the shady attachments or follow the links provided there. The Verizon's report also shows that once the attackers gain access they begin to download data within minutes and seconds leaving little response time. It seems like the response times to unauthorized access are ameliorating because in 37% of the breaches, the attack was contained in a few hours. To compare, FireEye reported in 2012 that the average cyberespionage attack remains unnoticed for 458 days on average.
The abundance of information on individuals and companies found online today enables really effective spear-phishing attacks and its usage as an entry point has been heavily exploited even in the past. It has been estimated in 2012 by Trend Micro that around 91% of cyberattacks begin with a spear-phishing email.
Spear-phishing attacks by the size of the targeted companies (in terms of employee count) for 2014
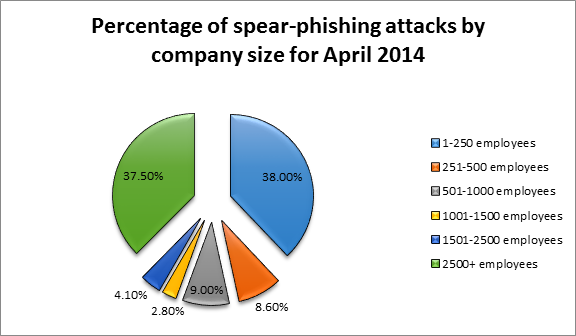
From the pie above, you can easily see that attackers preferred either very small companies or relatively big ones in April. Smaller companies are holding the first place in terms of attack volume probably because they have weaker online security and they frequently rely on cloud services some of which lack strong encryption mechanisms in place. If the small company has Fortune 500 companies as clients it becomes a luring entry point for further attacks as John Brandon puts it in an article of his. Another reason why small companies were the most target is simply that they are plentiful – there are around 28 million small businesses (with fewer than 500 employees) in the US alone according to Forbes.
Symantec's Internet Security Threat study revealed that cyberattacks against large companies rose with 40% in 2014 as it is exemplified in the spear-phishing attacks for April 2014. 5 out of every 6th company had been once targeted by spear-phishing or other email frauds. Big companies are lucrative targets - attackers can reap immediate financial benefit, sensitive data, IPs, glory and much more.
Let us examine whether this trend remains in the months of 2014 following April.
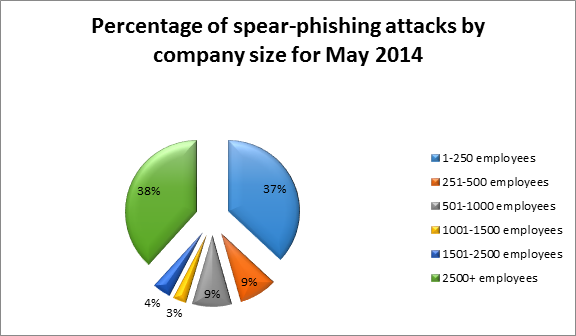
You can see that this trend continues in May. Bigger companies seem a bit more likely to be targeted than smaller ones for the course of the month.
Now let us examine the subsequent months in a single chart.
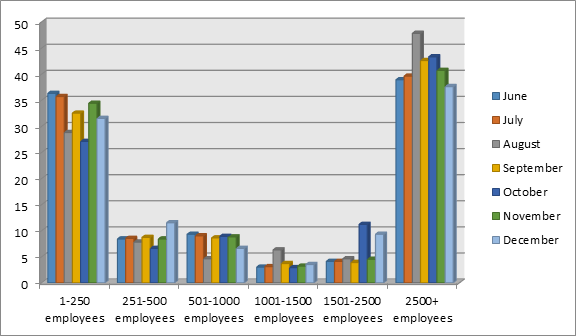
You can see the trend continues throughout the year 2014. The major difference compared to April is that the largest companies are holding the top 1 place in terms of attack volume from June to the end of the year. Companies with employees from 251 to 2500 are being targeted with differing intensity but it can clearly be seen that the main and preferred targets for cyber criminals are either the smallest companies or the biggest ones.
Changes in spear-phishing attacks against banks in 2015
In an article of her, Tracy Kitten pinpoints that spear-phishing attacks in 2015 have targeted bank employees instead of bank customers, as is the tradition. Instead of launching attacks against thousands of bank customers they try to directly infiltrate the bank itself. Banks have ameliorated their authentication mechanisms when it comes to services such as online and mobile banking and the attackers are now targeting the weakest link – the bank's employees. DMARC strives to prevent email spoofing by ensuring that attackers cannot spoof the domain of the company but it does not catch cases when the attackers are registering similar-looking domain names and using them to fool the victims that the email is coming from a trustworthy place.
Jay McLaughlin, the chief security officer of Q2ebanking, states that banks should invest time and money on employee education and in particular education which teaches employees how to identify social engineering techniques and not fall for them. He also proposes that banks modify their authorization and authentication mechanisms and implement the need-to-know principle so that if the credentials of one employee are leaked the cyber criminals cannot gain access to other accounts and files.
Industries at risk
Symantec provided a risk ratio of the different industries for 2014. The industry that is at most risk is Mining with 44% chance of being a subject to spear-phishing attacks. The second is the Wholesale industry with 34% chance followed by the Manufacturing industry with 33%. The last two places in the top five are taken by the Transportation, Communications, Electric, Gas & Sanitary Services and Public Administration.
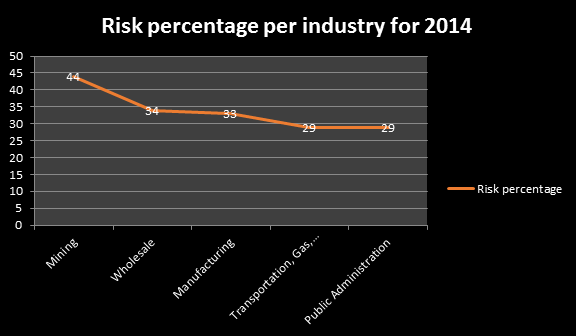
There are several reasons as to why the mining industry is at most risk from spear-phishing attacks.
One is that intelligence agencies and militaries of different states have been increasingly engaging in cyber warfare. They participate in economic warfare and espionage and the key industries of the targeted countries such as mining and metal often become victims. Reasons for this vary from collecting data, to assisting national companies in their contract negotiations to attempts to incapacitate the industry.
Another reason is that there are many activists who go to the extreme when their demands are not met and such key industries cannot meet the demands of everybody.
An important reason why they are at risk can be seen from the Global Information Security Survey for 2013-2014 written by EY. It appears that 44% of mining and metals personnel that were presented with a survey indicated that they do not have any threat intelligence program in place while 38% stated that there is only an informal threat intelligence program in their workplace. As security programs were not popular, it seems like the attackers' spear-phishing campaigns have a better chance of reaping success compared to some other industries.
Job titles targeted by spear-phishing campaigns in 2014
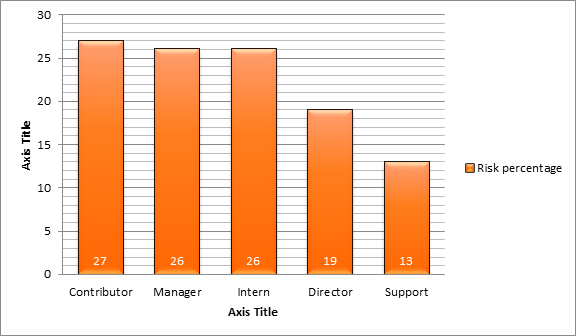
You can see that in 2014 individual contributors, managers and interns were picked the most for the spear-phishing campaigns.
See Infosec IQ in action
Conclusion
2014 saw a decreased number of spear-phishing emails compared to 2013. There were 73 spear-phishing emails per day on average in 2014 and 83 of them in 2013. Spear-phishing messages have also declined in the first part of 2015 compared to 2014. That does not mean spear-phishing is going away. It just means spear-phishing is changing; from the file types attackers use to the targets they choose for their campaigns and the way they launch their campaigns due to the living standard that is the Internet.
References:
- Holly Ellyatt, 'Global cyberattacks on big business up 40 percent in 2014', Available at: http://www.cnbc.com/2015/04/14/global-cyberattacks-on-big-business-up-40-percent-in-2014.html
- Symantec, 'Internet Security Threat Report', Available at: https://www4.symantec.com/mktginfo/whitepaper/ISTR/21347932_GA-internet-security-threat-report-volume-20-2015-social_v2.pdf
- Jason Nazar, '16 Surprising Statistics About Small Businesses', Available at: http://www.forbes.com/sites/jasonnazar/2013/09/09/16-surprising-statistics-about-small-businesses/
- John Brandon, 'Why Your Business Might Be a Perfect Target for Hackers', Available at: http://www.inc.com/magazine/201312/john-brandon/hackers-target-small-business.html
- Antony Savvas, '91% of cyberattacks begin with spear phishing email', Available at: http://www.techworld.com/news/security/91-of-cyberattacks-begin-with-spear-phishing-email-3413574/
- Kim Zetter, 'Email Phishing Attacks Take Just Minutes to Hook Recipients', Available at: http://www.wired.com/2015/04/email-phishing-attacks-take-just-minutes-hook-recipients/
- CohnReznick Advisory Group, 'Manufacturing – A Persistent and Prime Cyber Attack Target', Available at: http://www.cohnreznick.com/manufacturing-persistent-and-prime-cyber-attack-target
- EY, 'Cyber hacking and information security in mining', Available at: http://www.ey.com/GL/en/Industries/Mining---Metals/EY-Cyber-hacking-and-information-security-in-mining
- Symantec, 'Symantec Internet Security Threat Report Reveals Increase in Cyberespionage – Including Threefold Increase in Small Business Attacks', Available at: http://www.symantec.com/about/news/release/article.jsp?prid=20130415_01
- Nick Mazitelli and Mark Graham, 'A Cruel Interest: Attacker motivations for targeting the financial services sector', Available at: http://www.contextis.com/resources/blog/cruel-interest-attacker-motivations-targeting-fina/
- Trend Micro, 'Blurring Boundaries, 2014 Security Predictions for Small and Midsize Businesses', Available at: http://apac.trendmicro.com/cloud-content/apac/pdfs/business/white-papers/wp01_threat_predictions_smb_140127.pdf
- Symantec, 'Symantec Intelligence Report, May 2014', Available at: http://www.symantec.com/content/en/us/enterprise/other_resources/b-intelligence_report_05-2014.en-us.pdf
- Symantec, 'Symantec Intelligence Report, February 2014', Available at: http://www.symantec.com/content/en/us/enterprise/other_resources/b-intelligence_report_02-2014.en-us.pdf
- Symantec, 'Symantec Intelligence Report, January 2014', Available at: http://www.symantec.com/content/en/us/enterprise/other_resources/b-intelligence_report_01-2014.en-us.pdf
- Symantec, 'Symantec Intelligence Report, June 2014', Available at: http://www.symantec.com/content/en/us/enterprise/other_resources/b-intelligence_report_06-2014.en-us.pdf
- Symantec, 'Symantec Intelligence Report, July 2014', Available at: http://www.symantec.com/content/en/us/enterprise/other_resources/b-intelligence_report_07-2014.en-us.pdf
- Wikipedia, 'Comparison of executable file formats', Available at: https://en.wikipedia.org/wiki/Comparison_of_executable_file_formats
- Mindexception: out of context, 'Code injection – a simple PHP virus carried in a JPEG image', Available at: http://php.webtutor.pl/en/2011/05/13/php-code-injection-a-simple-virus-written-in-php-and-carried-in-a-jpeg-image/
- Symantec, 'Symantec Intelligence Report, August 2014', Available at: http://www.symantec.com/content/en/us/enterprise/other_resources/b-intelligence_report_08-2014.en-us.pdf
- Symantec, 'Symantec Intelligence Report, February 2015', Available at: https://www.symantec.com/content/en/us/enterprise/other_resources/b-intelligence-report-02-2015-en-us.pdf
- Symantec, 'Symantec Intelligence Report, July 2015', Available at: http://www.symantec.com/content/en/us/enterprise/other_resources/b-intelligence-report-07-2015-en-us.pdf
- Stackoverflow, 'Safety of opening .txt files', Available at: http://stackoverflow.com/questions/12982597/safety-of-opening-txt-files
- CVE Details, 'Microsoft » Excel : Security Vulnerabilities (Denial Of Service)', Available at: http://www.cvedetails.com/vulnerability-list/vendor_id-26/product_id-410/opdos-1/Microsoft-Excel.html






