Security Threats in Virtual World
What are virtual worlds?
A virtual world is an online world that simulates the real world in which the 'residents' can interact. Residents can participate in the creation of a virtual world, contributing virtual objects and social constructs like clubs, stores, etc.

FREE role-guided training plans
Virtual worlds are places with the following properties:
- Players present as individuals in the virtual world (their avatar or character). The avatar is a representation of a resident in a virtual world or an online game.
- Interaction takes places in Real Time.
- The world is shared, meaning the world is accessible to more than a member and so are the objects within it.
- The world has automated physics. For example: moving clouds, water movement, wind effect, etc.
Few examples of popular virtual worlds include Second Life, IMVU, Twinity, etc.
The virtual world is not just limited to that but it also exists in online gaming called MMORPG. A MMORPG or 'Massively Multiplayer Online Role Playing Game' is similar to virtual world, but usually includes a goal like accumulating points, defeating the enemy and more. Examples of MMORPGs include WOW (World of Warcraft), LOTR (Lord of the Rings) and Final Fantasy.
Here's what they look like:
Business Impact:
The influx of Fortune 500 companies like Toyota, Starwood and IBM in the virtual world of Second Life,also known as 'SL,' has generated much publicity in the year of 2006 and 2007(Reuters 2006). The virtual world landscape has changed substantially and it still keeps on changing with time. IBM employees use virtual worlds to host business meetings and conferences with its clients. Starwood Hotels created a virtual replica of Aloft Hotel in Second Life to enable potential customers to tour and experience their new product. Visitors could interact with features of hotels and visualize its interiors and poolside design architecture. Such events made a huge credence to the virtual worlds among the business community and propelled into the boardrooms of marketing firms and multinational companies.
People who play in these virtual worlds do it for several hours a day. On an average, the playing time exceeds 20 hours a week. But, they don't just spend time, they spend money. Two business models predominate:
First is subscription, pay a certain amount for a limit of time (usually months or years) to play. The second is free. Play is free but the in-world stuff that you buy from the developer isn't.
This increasing popularity of virtual worlds and MMORPGs adds another dimension to threats and risks.
Let's talk security shall we?
The rapid growth in popularity of online games and persistent virtual worlds has attracted the unwanted attention of both hackers and organized crime. While hackers generate havoc, cyber criminals exploit these trusted online system environments, using them for fraud and other illegal activities, including money laundering.
Many of the virtual worlds and online gaming (MMORPGs) allow players to conduct real money transactions, using real credit cards and other payment methods to exchange or purchase virtual credits with other players across the globe. The link between a real currency and a virtual trade attracts the organized criminals.
The following graph shows increased attacks on virtual worlds and MMORPGs in past years –Trend Micro:
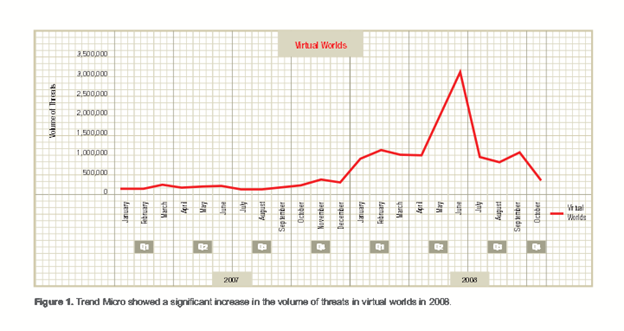
Of great concern to virtual world developers, government regulatory bodies and law enforcement agencies is the need to ensure that criminal activities and other anti-social behavior don't spread unchecked in virtual worlds.
Real world courtrooms have been used to dealing with criminal and anti-social activities within virtual worlds. In the Netherlands, a teenage user of the Runescape virtual world had been sentenced to jail for forcing his victim in the virtual world to handover virtual money and property (Feldmann 2008). The landmark lawsuit initiated by Kevin Alderman against avatar Volkov Catteneo demonstrated how an infringement of copyright within virtual worlds could be pursued through the real world justice system (Richards 2007). The Alderman vs. Catteneo case had also highlighted the challenges involved in tracking down and pursuing lawbreaking avatars. It has come as no surprise to many observers that Linden Lab shut down and banned virtual gambling operators in Second Life because such activities were considered unlawful in certain legal jurisdictions if they were not licensed. A ban on unlicensed virtual banks in Second Life was put in place after the failure of Ginko Financial (Hutcheon 2007), a self-proclaimed virtual bank in Second Life which had more similarities with a Ponzi scheme than a real world banking institution.
The lack of governance and regulation in virtual worlds has highlighted severity of security incidents. The criminals are taking advantage of the lawlessness of virtual worlds to target unsuspecting virtual world users by executing various attacks like computer worm attack, phishing attacks and other malicious attacks.
The security threats can be classified into 2 different categories:
- In-world threats
- External threats
In-world threats:
Many of the threats that a user experiences in real world can also be experienced in virtual worlds. These threats may look slightly different than real world threats, but nevertheless, they exist.
-
Identity masking
Virtual worlds harbor fake characters that interact with real users using social engineering techniques to acquire items of value in-world. Users can create any number or kind of avatars. As a result, determining the true identity is almost impossible. In-world, when an unknown character/avatar presents an offer that seems too good to be true, that is likely the case.
-
Phishing
This technique is used to acquire sensitive customer information by fraudulent means, such as user id, passwords, credit card details, etc. phishers appear in-world and out-of-world. They communicate through chats or IM and direct users to provide their account credentials at a 3rd-party websites which appear legitimate, but actually are phishing sites or sites harboring malware. Once an account has been compromised, a cyber criminal can use its associated credit card for purchases.
-
Money Laundering
While this is not a threat in usual sense, users can become a part of money laundering. Avatars can trade currencies and goods in these virtual worlds and sell them in other markets for real money. If an avatar requests help while purchasing or selling in-world currencies, users should refuse and avoid being part of this scheme. This crime is difficult to trace.
-
Theft
Two kinds of theft can occur, including the theft of virtual assets for use in virtual world or their theft for conversion to real world currency. Virtual currencies and goods are not regulated hence more sophisticated syndicates focus on the later one.
Intellectual property infringement in virtual worlds can be largely attributed to lack of effective enforcement and dispute resolution mechanism.
-
Virtual rape
It is a simulated virtual crime. For example, In early text based virtual worlds, such as objects were known as "Voodoo dolls", and they have been used to perpetrate something that many would call it "virtual rape". The most famous case took place in LamdaMOO (text based multi-user environment). A voodoo doll was employed by one user to make it appear that several other users were participating in explicit acts in an extremely public part of the environment. In another example, scripted collars in SL that allow one user to take control of another user's avatar are regularly used. The code that makes these devices work, could be built into anything like a teacup of a tennis bracelet. In theory, these objects could be then given to unsuspecting avatar as virtual roofies. An attacker needs to combine skillful scripting and social engineering to pull of this trick.
-
Gangs
In some MMORPG, players or a group of players wait for a new player to come online. The gang kills the novice and the unsuspecting avatar with virtual weapons (Yes! They do exist, like a sword or a bazooka). When an avatar dies in virtual world, these assailants assume their assets.
- Threats due to Open Code
Some virtual world programming languages are open to allow players and 3rd part developers to participate and involve in modification and creation of some objects and design landscapes of virtual worlds. This makes virtual worlds unsafe and vulnerable to hacking.
One such example is the "grey goo" virus, which replicated the objects too many times, resulting in program crashing and strange account problems, such as disappearance of in-world currency. The grey goo incident resulted in player expulsions and code alterations making the replication algorithms less vulnerable to misuse.
Here is a snapshot of grey goo affecting virtual world:
 This is a LSL scripted code for grey goo: (source: http://www.gazirababeli.com/greygoo.php)
This is a LSL scripted code for grey goo: (source: http://www.gazirababeli.com/greygoo.php)
[javascript]
// =================================================
// Grey Goo Number Nine
// ====================
// (cc) 2006 Gazira Babeli - gazirababeli.com
// =================================================
// This work is licensed under a Creative Commons
// Attribution-NonCommercial-NoDerivs 2.5 License
// http://creativecommons.org/licenses/by-nc-nd/2.5/
// =================================================
//
// HOW TO: Drag/Copy/Add this script on a prim
//list GG = ["abe4de67-77e8-2fe2-c20d-118e7549b7b8", // super mario
"6a32f6a0-c5f0-a7f6-1911-ca43e804dda6", // warhol banana
"33d2a02e-f5a4-a5fa-4b6e-93acbdae770b"]; // kaspar doubt
string greygoo;
integer randGG;
integer i;
default
{
state_entry()
{
llSetStatus(STATUS_PHANTOM, TRUE);
llSetPrimitiveParams([PRIM_SIZE, <.09,.09,.09>]);
llSetTexture("f54a0c32-3cd1-d49a-5b4f-7b792bebc204", ALL_SIDES);
llSleep(9);
for (i=0; i<99; i++)
{
randGG = llFloor(llFrand((float)llGetListLength(GG)));
greygoo = llList2String(GG, randGG);
llParticleSystem([
PSYS_PART_FLAGS , 0
| PSYS_PART_BOUNCE_MASK
| PSYS_PART_FOLLOW_VELOCITY_MASK
| PSYS_PART_EMISSIVE_MASK,
PSYS_SRC_PATTERN, PSYS_SRC_PATTERN_EXPLODE,
PSYS_SRC_TEXTURE, greygoo,
PSYS_SRC_MAX_AGE, llFrand(9),
PSYS_PART_MAX_AGE, 99.0,
PSYS_SRC_BURST_PART_COUNT, 9999,
PSYS_SRC_BURST_RADIUS, llFrand(9.9),
PSYS_SRC_BURST_SPEED_MIN, .09,
PSYS_SRC_BURST_SPEED_MAX, 9.9,
PSYS_SRC_ACCEL, <0,0,-llFrand(9)>,
PSYS_PART_START_SCALE, <9.99,9.99,9.99>,
PSYS_SRC_OMEGA, <llFrand(9*2)-9,llFrand(9*2)-9,llFrand(9*2)-9>
]);
llSleep(.09);
llParticleSystem([]);
}
llDie();
}
}
[/javascript]
External threats:
-
Keyloggers and password stealers
In real online world, the use of keyloggers has diminished, but not so in virtual worlds. Many keyloggers, Trojans, and worms exist in virtual world which are targeted towards online gamers and residents of virtual world. They aim to capture user credentials and submit them to attacker via email or web requests. Because developers often update games and virtual worlds, phishers present a code update through a website URL or as an attached exe in email. This so-called update contains a malware instead.
A well know example of a password stealer Trojan is TSPY_ONLINEGA.KB. This Trojan collects users' information and credentials from the Chinese MMORPG Zhengtu. It drops a DLL component in the WindirSystem32 folder and installs into a newly created Windir uninstall folder. The other variants of TSPY_ONLINEGA and TSPY_LINEAGE, which steal user information for the Lineage II game, are some most widely reported Trojans.
-
Spoofing
There are many spoofed sites that resemble the official game or virtual world sites, users should be aware of such sites.
For example, www.world0fwarcraft.net and www.wor1dofwarcraft.com (note the number '0' in the first link and the number '1' in the second link) which at glance appear to be legitimate World of Warcraft sites are actually malicious hosted sites.
-
3rd party sites
Users can purchase third party objects to improve virtual world experience. Some of the sites may not be legitimate (including the ones providing currency exchange for in-world dollars). Without in-world experience, determining a legitimate third party site from a fraud one is difficult. Hence new users (also called as "noobs" in virtual worlds) should wait until they gain some in-world experience which will allow them to assess the status of 3rd party vendors.
-
Extensions and Plug-ins
Attackers have started using social engineering techniques to trick users into installing malicious plug-ins under the pretext of providing extra and improved functionality in MMORPGs and virtual worlds.
Other threats:
-
Cyberstalking:
Cyberstalking describes a relatively new form of stalking behavior where technology is used as the medium of harassment. –Firstmonday.org
The term corporate cyberstalking is often used to describe incidents that involve organizations like government departments and companies. Corporate cyberstalking can be put into various categories like:
-
Cyberbullying:
According to 'The National Crime Prevention Council', cyberbullying is: "When the internet, cell phones or other devices are used to send or post text or images intended to hurt or embarrass another person".
Examples of what constitutes cyberbullying include communications that seek to intimidate, control, put down, manipulate, humiliate or falsely discredit the recipient. These actions are deliberate, repeated and hostile behavior whose intention is to harm the victim.
Conclusion:
Security threats have so far created disturbances, disruptions and chaos within virtual worlds. Practitioners are especially concerned with securing virtual worlds to ensure that disruptions and chaos do not spill over into the real world. Another security concern relates to the extent to which real life legal systems extend into virtual worlds. Increasingly we are seeing the real life legal system being used to settle disputes in virtual worlds. For instance, the dispute over the theft a prized virtual sword has led to the murder of a user in real life in China in 2005. The murderer was subsequently sentenced to life imprisonment (BBC 2005). In the USA, the breakdown of a virtual relationship between two users in Second Life had led to the attempted kidnapping of a user in real life (ABC 2008). A dispute over intellectual property theft in virtual worlds has led to legal proceedings in a real life court (Davis 2007). Hence, security threats that originate from virtual worlds may appear "virtual" for now but they tend to have a real impact on virtual world users and stakeholders. This is not surprising given the large number of virtual world users who spend a substantial part of their lives immersed in virtual worlds, living an extension of their real life in the synthetic environments of virtual worlds.

FREE role-guided training plans
References:
- http://virtuallyblind.com/2007/04/24/open-roundtable-allegations-of-virtual-rape-bring-belgian-police-to-second-life/
- http://www.vtoreality.com/2007/how-exactly-does-virtual-rape-even-occur-in-second-life/909/
- http://en.wikipedia.org/wiki/Cyberbullying
- http://ro.ecu.edu.au/cgi/viewcontent.cgi?article=1044&context=ism
- http://www.trendmicro.com/cloud-content/us/pdfs/security-intelligence/white-papers/wp_virtual_worlds_white_paper_10_31_08.pdf
- http://www.virtual-communities.net/mediawiki/images/9/98/Lee.pdf
- http://virtualnavigator.wordpress.com/2011/02/28/redzone-second-life-ip-address-detection-tool-runs-afoul-of-new-sl-policy-eu-data-privacy-law/
- http://www.nis-summer-school.eu/nis09/presentations/02_barlte.pdf
- http://www.eecs.harvard.edu/~cat/papers/vetr.pdf
- http://wiki.secondlife.com/wiki/Category:Safety_and_security
- http://www.iacpsocialmedia.org/Portals/1/documents/External/NW3CArticle.pdf
- http://www.wired.com/culture/lifestyle/commentary/sexdrive/2007/05/sexdrive_0504
- http://en.wikipedia.org/wiki/Cyberstalking
- http://en.wikipedia.org/wiki/Cyberbullying
- http://firstmonday.org/ojs/index.php/fm/article/view/1002/923
-




