Security Barriers in the Adaptation of Cloud Technology
Cloud computing adoption continues accelerating; research by IDG found that 69% of enterprises have either applications or infrastructures running in the cloud. As organizations are adopting cloud systems, it's creating another security threat for the future.
As far as the security is concerned, many organizations don't trust or rely on cloud systems. They are afraid of storing their business data and information to a system or server that highly attracts hackers and other cyber criminals. Some concrete security assurance is required to gain trust for such organizations.
Learn Cloud Security
According to cloud security spotlight report, the majority of the organizations are highly concerned with the security risk associated with the adaptation of cloud systems. The research revealed that the security is the biggest factor holding back faster adaptation of cloud computing and certified cloud professionals.
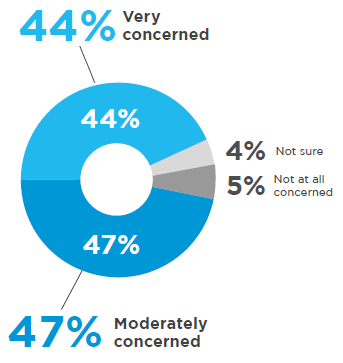
Around 44% of the organizations are highly concerned and 47% are moderately concerned with the security assurance of their data stored in clouds.
As cyber criminals are actively working to breach many organizations, cloud computing has also come under consideration for them. Cloud systems are sometimes dedicated that provide complete dedicated storage to a specific organization. If any breach occurs, only that organization will suffer. But, private clouds are highly expensive and out of budget for small organizations. For that, small businesses prefer public clouds that provide services to multiple small organizations. The biggest threat lies are, if any breach occurs, then multiple organization will suffer. Furthermore, providing security to such cloud is typically tough.

This graph shows that most organizations prefer private cloud because of its dedication towards the single organization. As the majority of enterprises haven't experienced any security breach from the cloud systems, it is motivating others to adapt it.
Research by Spotlight reveals that the security barriers are slowly eliminating as compared to traditional IT technologies and data storage services. The share of organizations that see a higher risk of security breaches in the cloud compared to traditional IT environments is shrinking to 21% compared to last year's 28%.
What is the critical data stored in the cloud that is creating security barriers?
Email is the most common corporate information stored in the cloud. Around 44% of the data stored on the cloud is email. While personal information like name, contact numbers and others covers 31% of the storage on average. Moreover, critical data like sales and marketing, payroll data, property information, healthcare information and other confidential data have also been saved to cloud a system that covers a relatively huge storage.

Cloud Apps Vs On-premise Apps
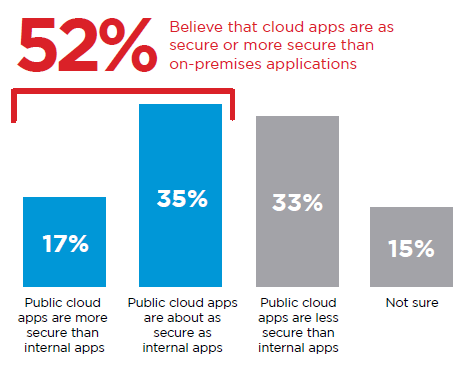
Security as a Service (SaaS) is gradually evolving and improving because of continuous investing, controls and end-user awareness. The majority of the surveyed organizations believe that cloud apps are as secure as or more secure than on-premises applications. The cyber world has already witnessed critical breaches in on-premise apps that cost organizations in millions of dollars and loss of trust too.
What security flaws are threatening Public Clouds?
Identity theft and access control are the emerging and increasing threat concern for public cloud and solution providers. Unauthorized access through misuse of employee credentials and improper access controls is the biggest threat to public cloud security. Around 58% of the security breach occurs due to unauthorized access. Out of which 44% are due to the hijacking of accounts and 39% due to insecure interface/API.

These are the most critical security flaws that are threatening public clouds. A single breach can cause critical data loss to multiple organizations at once. The good news is that all these risks can be addressed by using security controls, including multi-factor authentication, Identity and Access Management (IAM), Cloud Access Security Brokers (CASB), IP range restrictions and access auditing.
What are the Cloud Security Concerns?
There are many security concerns associated with the cloud systems. Cloud systems are responsible for providing complete security to the company's information as well as accessibility and availability. Organizations rely on their data, a single breach, data loss, or data theft can cost them in millions and also the loss of customer reputation as well.
To overcome such risk, cloud system should be protected well enough from both the sides, client and server side. Organization's security concerns are different as per their requirement and nature of work. Around 49% of the organizations are concerned about the data leakage they need complete surety from the cloud provider about this risk. While other risks are also in consideration, that involves data privacy, confidentiality, legal and regulatory compliance.

What are the biggest cloud security headaches?
As the cloud is a new and rapidly growing environment, that is often incompatible with existing security technologies and solutions; there is a need for a new holistic security model to cover both on-premise and cloud environments. It is the main challenge that makes the organization to rethink before adopting cloud system. Whether it is compatible with their existing system or not is the main reason.
The major headaches in the cloud security achievement are the verifying security policies, visibility into infrastructure security and compliance. The statistics below shows the occurrence of issues occurred while adopting the cloud systems.

Cloud Application Security:
Although, cloud security controls include multi-factor authentication, encryption, intrusion detection and prevention, and other security solution provided by the cloud provider. But, organizations still don't feel safe and implement additional security mechanism at their end.
A majority of organizations are taking proactive measures to protect their business applications as well as cloud applications. No doubt the cloud applications have been developed while considering all the threats and are required to assure the information security. But, still static and dynamic testing, monitoring, bug bounty programs have been introduced to make it trustworthy and ideal for organizations to adopt cloud services.
Given the downside, organizations that are planning to adopt cloud systems are required to assess their data's confidentiality before choosing the cloud services. Don't go for the cheap services; consider the applications and security features that your cloud provider is offering you. No doubt cloud systems are highly secure services as compared to traditional storage services that cause billions of data leakage in the past few years. But, still, organization side security should also be considered to make it full proof, as the attackers are not going to stop to hunt for organization's critical data.
Learn Cloud Security
Reference:
https://pages.cloudpassage.com/rs/857-FXQ-213/images/cloud-security-survey-report-2016.pdf




