SAP ABAP Platform Security
From the previous articles of SAP Security for CISO series (especially SAP Risks), you reviewed many examples of potential attacks on these systems. Now it is time to learn how these attacks can be conducted via vulnerabilities discovered in SAP systems.
First, let's look at patching process in SAP. When the vendor fixes vulnerabilities in its program components, it releases an SAP Security Note. It is a small patch with an instruction or just a piece of advice regarding important actions as when you have to change security parameters in your system and don't need to implement any patches. Sometimes an SAP Security note requires both implementations of a new patch and configuration of parameters. In most cases, it consists of a patch for one particular vulnerability, but we have noticed that patches provide corrections for multiple vulnerabilities in the recent updates. It means that the real number of security issues is even more than a number of patches.
Take a glance at the figures: 3662 patches were released for all SAP Products. More than 2500 of them are intended for SAP NetWeaver ABAP platform.
As you can see in the picture, most of the issues were found in ABAP engine, J2EE follows and then the others.
SAP NetWeaver ABAP platform Security
SAP NetWeaver ABAP is the main SAP Platform – it is like a framework on top of which SAP creates its business applications. Almost all business applications that are developed to automate different business processes of an organization (e.g. Enterprise Resource Planning or Supply Chain Management) are based on SAP NetWeaver ABAP Platform. By exploiting vulnerabilities in this platform itself, an attacker can get access to any business application, which sits on top of this platform. Access to the applications allows halting mission critical business processes, committing industrial espionage or fraud.
As illustrated, 2585 issues were patched in this platform. We carry out our annual research called "SAP security in figures." The picture provides some statistics such as information about different types of vulnerabilities.
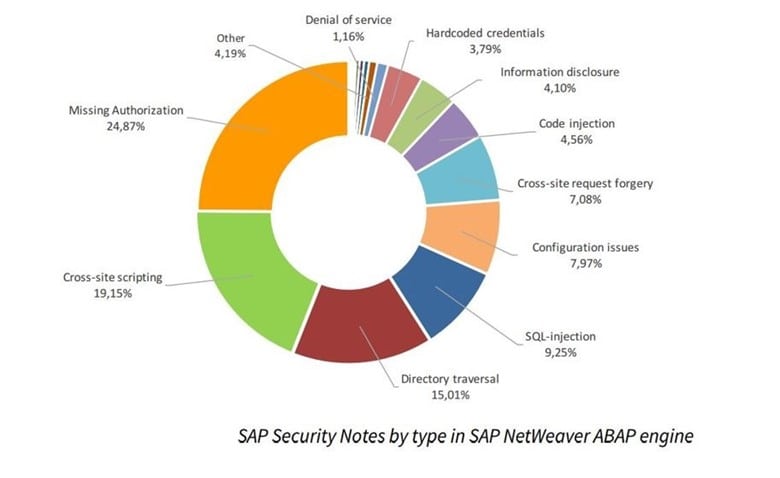
Missing or improper authorization checks are the most common types of flaws in the ABAP Platform, which were identified even in SAP developers' code. Taking into account the system's complexity, imagine how many of them you can find in the custom code. Because of that, there are many functions that can be caused by users who do not require such functionality to accomplish their work.

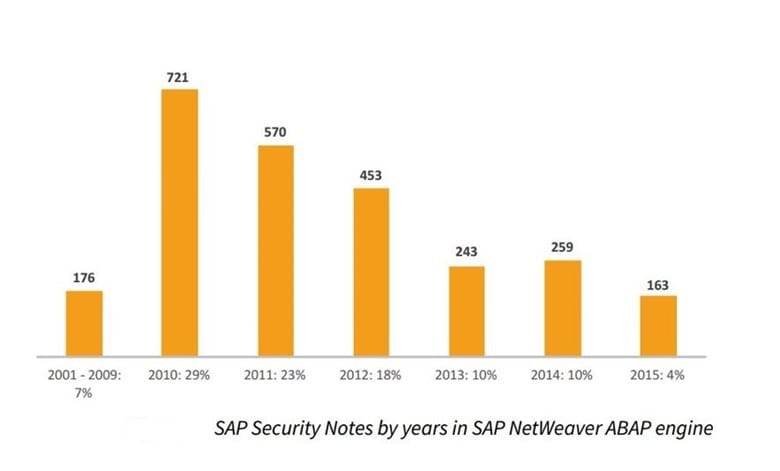
The upper graph of another statistics presents the number of vulnerabilities in SAP NetWeaver ABAP platform by years; the bottom graph shows the percent of vulnerabilities in ABAP platform in comparison with the number of vulnerabilities found on other platforms. Two trends together demonstrate that research interest is shifting from this old platform to the newer ones. However, it still leads to the number of fixed vulnerabilities.
SAP NetWeaver ABAP platform overview
Before we go deeper in SAP NetWeaver ABAP platform security, let's learn about its architecture and a standard procedure how the system works. In brief, a client uses an old fat client SAP GUI application to connect to SAP NetWeaver ABAP application server, particularly to Dispatcher service. Dispatcher service transfers requests to the main process called ABAP Work Process. It obtains necessary data from the database. In fact, there are numerous additional services for different functions, and all these services can be susceptible to hacks. For example, Gateway service is an alternative way to execute SAP functionality. It is like a remote API for running functions without any user interaction. Users can deploy "scripts" called RFC functions to execute actions in the SAP system.
Here is the list of other services and ports that are usually open for remote connections. The port number depends on application server instance number with values from 00 to 99. For example, the role of Message Server is a load balancing. Imagine you need to serve thousands of users, so you install different application servers, and each of them has its own Dispatcher process. To transparently use one or another application server, there is SAP Message Server, which transfers requests from a user to the application server. Needless to say that with an access to the Message Server a perpetrator can control the data flow from a user to the application server. Message Server HTTP is just a web interface with statistics, but if it is not configured properly, an attacker can obtain all application server configuration parameters. ICM service is intended to enable access to SAP functionality by a web browser. IGS is an old service that provides some statistical information. If being misconfigured, it can be used by malicious actors to exfiltrate critical data. Enqueue server provides administers locks on objects during SAP transactions. The locks are requested by applications to ensure the consistency of the SAP system. Server failure in the absence of high availability protection leads to the total loss of the stored locks, with such consequences as an automatic rollback of transactions. MMC and Host control services exist for the administrative purposes. They represent SOAP interfaces that can execute a bunch of administrative commands, some of which don't require authentication if misconfigured.
Therefore, there are services installed by default, with vulnerabilities and misconfigurations, usually left unattended by administrators who rarely take care of their security.
SAP NetWeaver ABAP platform vulnerabilities
SAP NetWeaver ABAP application server is the oldest and most vulnerable SAP platform. Researchers presented dozens of reports describing the security of each of provided services. I will highlight the most important reports so far.
In 2007, a researcher from Argentinian company Cybsec published information about a vulnerability in SAP Gateway service that allows bypassing security restrictions and executing any OS command on SAP Server. This issue still affects different systems.
In 2011, a research called "Scrubbing SAP clean with SOAP" revealed multiple ways to obtain critical information from SAP using MMC service. Later on, we presented more attacks with such results as reading configuration files from the server using MMC Service.
In 2012, there was a worth mentioning talk describing SAP Solution Manager security as a topic to watch. Solution manager is like a management console to all SAP Systems. By gaining unauthorized access to it, an attacker reaches all systems in the landscape. It occurs due to RFC and other connections between SAP Systems, which usually store credentials to access a satellite system. You will find more on that in the next chapters. "Top 10 most interesting SAP vulnerabilities and attacks" is an informative presentation where I collected some compelling and curious attacks on SAP Systems to prove that SAP Security is much more than just segregation of duties.
Finally, if you want to get an overview of real attacks and learn more technical details about them, I recommend looking at the presentation from the RSA conference 2013 titled "If I Want A Perfect Cyberweapon, I'll Target ERP." For you to know how to perform an SAP Security assessment manually, there is the "Practical SAP Pentesting" workshop available on our website.
Remote attacks on SAP NetWeaver ABAP
There is still a myth that SAP Systems are only available internally. In fact, a wide range of services is not only open for connections from the corporate network but also accessible from the Internet.
What about the most considerable vulnerabilities, which can be exploited remotely? Almost every SAP Client uses SAP Router application to download updates from the vendor as well as to provide remote access for SAP support team to the systems in case of emergency. It means that access to SAP Router service is available via the Internet, and every potential vulnerability can be used by attackers to break into every company that has SAP Router installed and doesn't implement updates in time. Our researchers successfully identified critical remote command execution vulnerabilities in SAP Router service. By the time of our research, 85% of SAP Routers were not updated! This vulnerability can be used to infect the system with stealth agent, a "backdoor" which can stay undetected and modify any updates uploaded into SAP systems. It makes this vulnerability one of the most dangerous issues identified in SAP, but bear in mind it is only one of 3600+ issues.
Every year situation is changing, and researchers are looking for different areas, which seemed to be secure earlier. The year 2014 was known for the multiple denials of service vulnerabilities in different SAP Services. Previously, system availability and sabotage attacks used to be underestimated areas. While a single denial of service vulnerability in a standard application is not a big deal, it can cause serious trouble for such systems as ERP or Core Banking system. That is why researchers identified multiple DoS issues in SAP applications.
Another area we focus on is reverse engineering of SAP proprietary protocols and identifying different remote command execution issues. Vulnerabilities in protocols of such services as SAP Dispatcher, SAP Message Server, and SAP Router were presented in 2014 – 2015. 2014 was a year of Crypto vulnerabilities in general; most of them (e.g. FREAK, BEAST, and VENOM) affect SAP Systems as well.
Last but not least, the most significant trend is the industry-focused research. We spent five years on analyzing specific challenges of different verticals like Oil and Gas, Retail, Manufacturing, and now present a paper with a detailed consideration of security risks for every particular industry type.
Securing SAP NetWeaver ABAP platform
Now let's shortly discuss defensive measures (a detailed Defense article will come later). There are two main areas: Infrastructure security (network, OS, and DB) and Application security.
As for Infrastructure, no matter how properly you secure your application if you have a default password for OS. I hope everybody realizes it and there is no need to discuss all details of Infrastructure Protection, which you can get from industry guidelines such as NIST and SANS.

What should you learn next?
Speaking of the latter, there are three areas in SAP security. First, you should care about vulnerability management (deal with SAP Security notes) and secure configuration (default passwords, unnecessary services, etc.), then check your custom code for vulnerabilities and backdoors and, finally, review access control and SoD issues so that no users will be able to execute more that they are required to do. The SAP NetWeaver ABAP Platform Vulnerability Assessment Guide developed by the EAS-SEC organization with the help of ERPScan team is a great source of information to start secure configuration of SAP NetWeaver ABAP application server.





