Russia vs. the US: A Pretext to Discuss the Cyber “Cold War”
Introduction
Early 2016, the Director of National Intelligence James Clapper told Congress that the US intelligence agencies were aware of cyber-attacks against individuals and organizations involved in the 2016 presidential campaigns. This is just one of the numerous attacks suffered by the US Government over the years.
Let's consider the cyber-attacks against the Sony Pictures or the alleged intrusions of Russian hackers inside the US Government networks, including the Pentagon computers and several critical infrastructures in the country.

What should you learn next?
Russia, China, North Korea are the countries that most of all are threatening the dominance in the cyber space of the US.
Their governments are investing a significant effort in the developing of new cyber capabilities, like any other countries they are working to create a rich arsenal to conduct both sabotage and cyber espionage operations.
At the last Warsaw NATO summit, members of the alliance have officially recognized the cyberspace as a military operational domain. This means that the NATO alliance will respond with conventional weapons in case of a severe cyber-attack confirming that the Internet is a new battlefield.
A cyber-attack against the critical infrastructure of one of the NATO states can have real world consequence, for this reason, it is essential to improve the cyber defense of the members.
What will happen now?
Designating the cyberspace as an operational domain means that the NATO members will focus their efforts on improving cyber capabilities of its members, it is expected more focus on training and military planning.
Each member of the NATO is committed to improving its resilience to cyber-attacks and the ability to promptly respond to cyber-attacks, including in hybrid context
"Cyber-attacks present a clear challenge to the security of the Alliance and could be as harmful to modern societies as a conventional attack. We agreed in Wales that cyber defense is part of NATO's core task of collective defense. Now, in Warsaw, we reaffirm NATO's defensive mandate and recognize cyberspace as a domain of operations in which NATO must defend itself as effectively as it does in the air, on land, and at sea. This will improve NATO's ability to protect and conduct operations across these domains and maintain our freedom of action and decision, in all circumstances." states the Warsaw Summit Communiqué. "We continue to implement NATO's Enhanced Policy on Cyber Defence and strengthen NATO's cyber defense capabilities, benefiting from the latest cutting-edge technologies."
Cyber defense is a pillar of the cyber strategy of the alliance, but many experts are questioning about offensive cyber capabilities of Alliance. Almost every state is working to improve its offensive cyber capabilities too.
Some experts speculate that a similar decision could speed up the militarization of the cyberspace, for sure it will raise the debate on Information Warfare and the need for a new legal framework to address these questions.
Russian hackers target the Presidential Elections
In June 2015, experts from the security firm CrowdStrike were involved in the investigation of the cyber-attack suffered by the Democratic National Committee (DNS).
The researchers discovered not one, but two nation-state groups involved in the attack, the COZY BEAR, and the FANCY BEAR. According to the Washington Post, the Russian hackers managed to steal an entire database of opposition research on the presumptive Republican nominee for President Donald Trump.
Both hacker crews are well-known to the security experts; these ATPs are considered among the most active group of nation-state hackers that have been involved in numerous cyber espionage campaigns over the years. In 2015 US Government experts discovered that, COZY BEAR, a.k.a. CozyDuke, have breached the US State Department's email server and remained hidden at least for an entire year. The security breach forced the State Department shut down much of its unclassified email system to rid itself of the pervasive malware and made for an unfortunate backdrop for the Secretary of State, Hillary Clinton, embroiled a politically charged debate over her personal email server.
In April 2015, experts at Kaspersky Lab revealed the existence of the CozyDuke ATP that targeted several high-profile organizations in the second half of 2014. Security experts discovered many the similarities between the operations conducted by the CozyDuke and other campaigns managed by the APT groups such as CosmicDuke, MiniDuke, and OnionDuke.
The experts at Kaspersky haven't linked the CozyDuke to the Russian Government, but media agencies and many experts believe that the State Department and White House attacks were carried out by Russian hackers working for the Kremlin, which could also be the government behind these APTs.
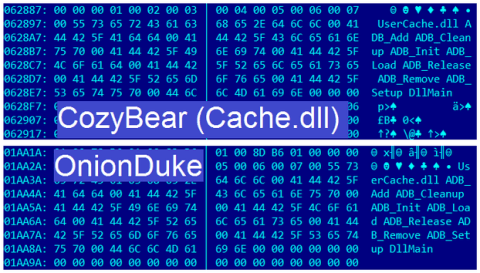
Figure 1 CozyBear code compared with OnionDuke code.
While CrowdStrike was making headlines with its breaking news, PaloAlto Networks was releasing its own report on FANCY BEAR, a.k.a. Sofacy APT, another well-known espionage group, believed to be Russian. According to the experts from PaloAlto Networks, the attacker used spear phishing emails with weaponized attachments. The messages were sent by compromised server belonging to the Ministry of Foreign Affairs in an unidentified country. PaloAlto experts analyzed the malicious code used by the threat actor and noticed that FANCY BEAR hackers are using the source code from another popular malware, the infamous Carberp Trojan. Once the malware infected the victim's machine, it beacons to "google.com" to mask beacons to a C2 server hosted at 191.101.31.6.
A cyber-attack against a political party is not a novelty, in the past other nation-state, attackers targeted politicians and organizations involved in the elections.
In 2008, Chinese hackers compromised the computer networks of the Senators Barrack Obama and John McCain and later, in 2012, the hackers targeted the campaign networks of Obama as well as Mitt Romney.
Trump is considered a politician welcome to Russian authorities, Trump's fascination with Russia is not a mystery. Trump has made it no secret that he may be willing to rehabilitate the Putin's reputation on the world stage often saying,
"Wouldn't it be nice if actually we could get along with Russia." at many of his rallies.
Regardless of the political implications and fallout of the DNC breach, there is little doubt that Russian espionage actors most likely now have a comprehensive playbook on the DNC's strategy in defeating Trump in the November elections. How they use that playbook remains to be seen and many other questions about the breach remain unanswered.
Both COZY BEAR and FANCY BEAR APT groups are well coordinated, funded, and highly skilled actors.
Were both groups acting alone, or are they operating in a coordinated effort on behalf of a single entity?
It is not easy to answer the question. Anyway, it is a known that intelligence agencies rely on multiple nation-state actors that are given overlapping objectives without any knowledge of each other. Adopting such kind of strategy make hard for security experts to attribute the attack to a specific entity.
Is the DNC hack linked to the attacks against Russian State computer networks?
While US security experts blame Russian nation-state hacker for the recent attacks, the Federal Security Service (FSB) announced the discovery of spyware in state computer networks.
The news was first reported the Reuters agency, on Saturday, June 30, networks belonging to at least 20 Russian organizations were infected with malware as part of a coordinated attack.
"Russia's intelligence service said on Saturday that the computer networks of 20 organizations, including state agencies and defense companies, have been infected with spyware in what it described as a targeted and coordinated attack." reported the blog post published by the Reuters.
The Russian Intelligence hasn't provided further details about the cyber-attack against government networks. Russian Government experts have found many similarities to other cyber-attacks suffered by Russian organizations and other entities worldwide. At the time I was writing the Russian authorities haven't provided information about who is behind the attacks.
"Information technology resources of government agencies, scientific and military institutions, defense industry companies and other entities involved in crucial infrastructure have been infected," reads the announcement published by the FSB on its website.
Security experts believe that the attacks have been launched by state-sponsored hackers because the type of targets and the complexity of the attack.
Experts are already speaking of Cyberwar
The recent cyber-attacks on the Presidential Election are raising concerns in IT security industry. The hacks of the Democratic National Committee and presidential candidate Hillary Clinton's campaign and the malware-based attacks that hit the Russian government networks demonstrate the intense activity in the cyberspace.
Government worldwide are aware of potential risks for their infrastructure, the activities of nation-state actors are reaching a peak as never before, and the situation is likely to get much worse.
Kenneth Geers, a senior research scientist with security firm Comodo, speaking at the BlackHat 2016 USA security conference explained that the cyberwar is a real and present danger.
"There is no question cyberwar exists," he says. "Whether it rises to the level of weapons of mass disruption is another question. We don't have a decisive answer yet."
I have always considered the term 'cyberwar,' less appropriate than 'Information Warfare', but it probably gives the common people a better idea of the risks related to the exposure to a cyber-attack and about the dispute with the government in the cyberspace.
Geers is a notorious cyber security expert with a deep knowledge of the Information Warfare; he has been working with the NATO, monitoring cyber dispute in the Ukraine.
A cyber-attack on a critical infrastructure with a malware like Stuxnet could be considered as an act of war.
The attack against the Estonia in 2007, when the country systems were hit by a huge distributed denial of service attack, is probably one of the most clamorous cyber-attack recognized as an act of war,
The Estonia case raises another problem when approaching information warfare, the "attribution" of the attack. Although the attack has been linked to the Russian government, the source was not officially confirmed.
Returning to the present day, something of similar happened across the last years in the Crimea, where cyber armies linked to the Kremlin targeted the critical infrastructure of the area such as communications.
The tension in the real world between Russia and Crimea had a corresponding conflict in cyberspace. Security experts observed numerous cyber-attacks on both sides during the revolution in Kiev, and the cyber offensives have had an escalation after the approval of the Russian parliament for military use in the Crimea. The decision of the Russian government has triggered a series of events in cyber space as state-sponsored cyber units, groups of hacktivists, and cyber criminals started their campaigns against the enemies.
Ukraine's mobile phone infrastructure was under attack, the offensive against the Ukraine's mobile phone infrastructure originated in Crimea and is interfering with the phones of members of the parliament.
"I confirm that an IP-telephonic attack is under way on the mobile phones of members of Ukrainian parliament for the second day in a row," declared Valentyn Nalivaichenk, the head of Ukraine's SBU security service during a press conference, according to the Reuters agency.
Ukraine's telecommunications system has come under attack. The attackers used equipment installed within Ukrtelecom networks in the Crimea region under the control of Russian forces. This circumstance has raised tension between the two countries, and although the majority of the Crimean population is pro-Russian, the sabotage was interpreted by the government of Kiev as an intolerable act of war.
A cyber-attack could have a severe impact on the population and in the worst scenario, it can cause the loss of human lives. In December 2015 hackers shut down three power plants in Ukraine, plunging more than 200,000 citizens into darkness.
The effects of a cyber-attack today could be much more severe compared to the ones observed in Estonia in 2007 because we live in a society that heavily depends on technology.
"Today's tanks, planes and ships are really just rolling, flying and floating computers," Geers says. "If you're a tank commander and the enemy launches a zero-day attack against an application you depend on, you may not win on the battlefield that day."
Back to the US elections hack, Geers doesn't exclude a possible involvement of Russian state-sponsored hackers.
"Could the US elections be hacked by the Russians, just as Ukraine's was?" "Absolutely, says Geers." reported The Guardian that reported the Geers declaration.
"But they could probably change the election more easily by doing influence operations in the runup to the election," he adds. "Maybe doxxing is the best way to do that. You're embarrassing the hell out of somebody. Lives are ruined."
We have no time; cyber security is a top priority for any government to avoid severe incidents in the next future.
Considering an electoral system as "critical infrastructure."
The recent cyber-attacks against the Democratic campaign computer systems in the alleged attempt to manipulate the 2016 Presidential election is urging a reaction of the US Government.
According to a source close to the NYT, the US intelligence agencies have told the White House that they have "high confidence" that Russian state-sponsored hackers launched the attacks.
The White House avoided publicly blaming the Kremlin for the attacks, but experts speculate that the US intelligence is preparing a cyber counteroffensive.
Speaking at the Aspen Security Forum the CIA director John O. Brennan explained that the attempt to interfere with Presidential elections is a new level of malicious activity, far different from the cyber espionage operations that almost every government conduct every day.
"When it is determined who is responsible for this," Mr. Brennan said, avoiding to point out the Russia, there "will be discussions at the highest levels of government about what the right course of action will be. Obviously, interference in the U.S. election process is a very, very serious matter."
At the same event, Lisa O. Monaco, homeland security adviser, admitted that the US Government might soon have to consider whether the electoral system as "critical infrastructure," to be protected.
"I think it's a serious question," she said, especially if there is "coercion, destruction, manipulation of data." Ms. Monaco noted that whenever the United States thinks about retaliation, "the danger of escalation and misinterpretation is such that we have to be responsible for it." But she also said that if an event were serious enough, "we have to be very clear we will respond."
The Russia is one of the most dangerous and persistent cyber adversaries, in response to the Democratic National Committee hack, two senior administration officials speaking on the condition of anonymity told the NYT that the US Government could hack back on the F.S.B. and the G.R.U.
Both intelligence agencies are suspected to be involved in the DNC attack.
Conclusion
The events raised the debate about the effective value of attribution and its accuracy.
There is no doubt that the DNC hack is likely going to be one of many cyber-attacks in the coming months as we approach the elections later this year in November.
Whoever is behind the attack, the DNC hack demonstrates the potential influence of hackers on the politic of one of the most important governments of the world.
Once again, an attack from the immaterial cyberspace could have a severe impact on the event in the real world.
References
http://securityaffairs.co/wordpress/49255/cyber-warfare-2/nato-warsaw-summit-2016.html
https://www.crowdstrike.com/blog/bears-midst-intrusion-democratic-national-committee/
http://securityaffairs.co/wordpress/49843/intelligence/russian-intelligence.html
http://securityaffairs.co/wordpress/49705/intelligence/dnc-hack.html
http://securityaffairs.co/wordpress/48428/cyber-crime/russian-hackers-spy-us-politics.html
http://securityaffairs.co/wordpress/47455/intelligence/hackers-target-presidential-contenders.html

What should you learn next?
http://securityaffairs.co/wordpress/50059/cyber-warfare-2/cyberwar-cyberspace.html




