Rootkits: User Mode
In this article, we will learn about what rootkits are and how they operate. The focus will be on two types of Rootkits exploits: User Mode & Kernel Mode, what are the various ways in which rootkits exploit in both modes. In this part we will learn about the 'Rootkit Category: User-Mode' only.
What are Rootkits?
Rootkits are collection of tools that are used to provide backdoor access for Trojan horses by modifying important system files. A common misconception about rootkit is that they provide root access to the malicious user. Instead, rootkits actually depend on that attacker/malicious user already has already exploited the target and gained root access into the system .Once the attacker has root access to the system, rootkits will make sure that the attacker access on the target remains.
Rootkit Categories
Rootkits are mainly classified into two major categories as follows:
Let's learn about both of these categories in more detail:
User Mode
Rootkits that fall into this category will operate at user level in an operating system. As stated earlier rootkits helps attackers to keep their control over the target by providing a backdoor channel, User Mode Rootkit tends to change the important applications at user level thus hiding itself as well as providing backdoor access User Mode rootkits are variable for both Linux and Windows:
Linux User Mode Rootkit
There are several Linux user mode rootkits available today for example:
- To gain remote access to a machine, login services like 'login','sshd','inetd' etc. are all modified by the to include a backdoor password. Attacker just has to access these services and provide backdoor password to instantly got root access. Please note that attacker already has exploited the system by changing the legitimate services with malicious ones and with this technique, it is only connecting again to get root access.
- Another to reach level is to perform privilege escalation attack. Attackers modify the commands such as 'chsh','su','passwd' in such a way that when the attacker uses these commands with the backdoor password , attacker will instantly get elevated to root level.
-
Another way the attacker user User Mode rootkit is to hide their presence which further fall under four categories:
- Process Hiding: Various commands which shows information about process running on the machine like 'ps','pidof','top' is altered so that the attacker process is not listed among other running process. Also command 'killall' is usually changed so that attacker process cannot be killed and command 'crontab' is changed so that malicious process run at a specific time without any modification of cron configuration.
- Network hiding: Commands like 'netstat' are also altered so as to show no information about port attackers processes are listening to. Also command 'ifconfig' is altered so that to mit any indication of 'promisc' mode activity.
- File Hiding: Attackers hide their presence by modifying the command like 'ls' and 'find' so that attackers files cannot be found. Also command 'du' is modifies to hide attacker file from disk usage collection.
- Event Hiding: 'syslogd' is modified so that attackers events do not even get logged I the target machine.
Windows User Mode Rootkit
Rootkits hooked in Windows through the process known as DLL injection, so before we jump to know how rootkits hook themselves in windows, we should be aware of the process of the DLL injection, so spare a few to learn about how DLL injection happens:
DLL injection in Windows
DLL's are usually being utilized by programs such as exe for any global functionality i.e. DLL's code are being shared by multiple programs at one time. DLL injection means that a legitimate process gets its required function/code from a malicious DLL, which is injected by the attacker. The requesting program will dutifully accept whatever instructions come from the DLL. The injection process covers following steps:
- First, the space required for DLL code to be in victim process, a call to 'VirtualAllocEx' is being made. VirtualAllocEx is a Microsoft API that is developed for this purpose. After allocating the space, now the space for DLL parameters is being allocated using the same 'VirtualAllocEx' call. Please note that for now only the space is being allocated to the DLL and its parameters into the victim process.
- After allocating the process for DLL and its parameters, second step is to write the code of DLL into the victim process. To achieve this 'WriteProcessMemory' API is being used which is used to write to the memory location of a running process. Until now space and code of the DLL is being placed into the victim process.
- Last step is to execute the above-allocated DLL code, a thread is being created in the victim process to run the DLL code. For this API call is being made to the 'CreateRemoteThread' that will run the code of DLL into the victim process.
-
After getting the desired code to be executed, attacker can even free up the resource like DLL space by using the 'VirtualFreeEx' function.
- Example of DLL injection:Now since we have understood the DL injection, let's have some more clarity with the help of an example. The diagram below will show a rootkit that creates some malicious DLLs and then hook the DLL into a legitimate process. Below is the complete process
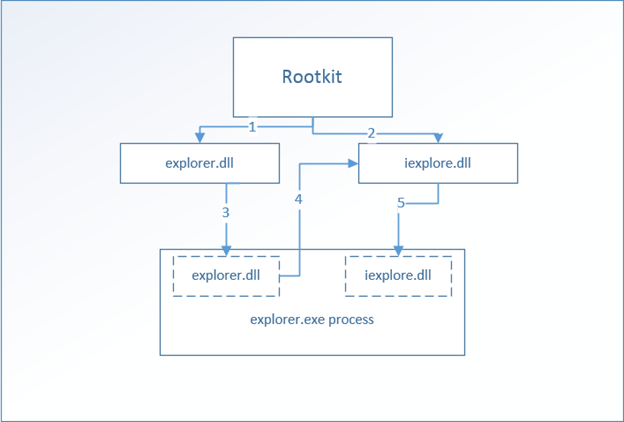
- IN Step 1 & 2, the rootkit will create two malicious DLLs named explorer.DLL and iexplore.dll. Please note that Windows requires explorer.exe (for Windows GUI) and iexplore.exe (for Internet explorer) and not he respective files with DLL extension. A system admin without this knowledge will ignore these DLL files to be legitimate.
- IN step 3, with the help API calls 'VirtualAllocEx' space is being created for the malicious DLLs and then code of the explorer.DLL is being written to the legitimate process explorer.exe. The purpose of this explorer.DLL is just to place the code of iexplore.DLL into the explorer.exe.
- IN step 4, explorer.DLL grabs the code inside iexplore.DLL
- IN Step 5, explorer.DLL writes the code of iexplore.DLL into explore.exe with API call 'WriteProcessMemory'.
- So now, whenever the explorer.exe will open malicious code inside iexplore.DLL is executed.
Best Practices against User Mode Rootkit
This section states the best practices with the User-Mode Rootkit:
- For key system files, cryptographic hashes must be obtained. Also use tools like File Integrity monitor must be deployed to check for any unauthorized change to the key system files.
- To prevent Windows DLL injection, restrict the DEBUG right in the system. This can be set under secpol.msc >Local Policies > User Rights Management.

- Keep the system patched with the latest updates from vendors.
- If system is infected with this rootkit, then reinstalling the system with reformatted drove is the best choice.
- To disallow another attack, patch the systems and change all the previous set admin passswords.
In this article, we have seen how User Mode rootkit can exploit the User Space. In the next article, we will dig down a level deep and see how Kernel Mode exploit performs their nefarious deeds.






