Reverse engineering
Reverse Engineering – LAB 3
Software: IDA Pro Free (v 5.0)
DLL Name: Test.dll
Story about DLL:
This DLL is reportedly scanning the system for running the process on the system and then send them to a hardcoded domain name. This DLL has also employed anti-analysis technique by checking the presence of known virtualization software's etc.
Steps:
- Load the malicious DLL into IDA Pro (Drag the file into IDAPro).
-
Accept defaults and Click on OK.

-
As soon as the DLL is loaded inside the IDA pro, we can see that IDA pro is showing that the flow started from DLLMain which is expected since it is the entry point of DLL.

-
Let's look into the imports of this DLL, which means that what code has been reused by this DLL to implement some functionality from DLLs existent on the system.
- Click on Imports tab OR Click on Views > Open SubViews > Imports

- As we can see this DLL is utilizing too many functions which implies that DLL is not packed. Among all the interesting imports, let's look string gethostbyname which is used commonly by malware to find the IP address associated with the FQDN name supplied. So, let's check what FQDN the code is trying to resolve.
-
Double Click on gethostbyname which show us that the function is declared in the .idata section of this dll.

-
Select the string gethostbyname and press X to see the cross references. With the help of cross-referenced technique, we can see all the areas from which the respective string/function is being referred to/by.

- We can see that gethostbyname is being referenced from in total 5 functions (multiple times from a couple of functions).
- Click on any function to see how IDA Pro navigate to that location.
-
From the above references, select the one highlighted below and press ok.

-
IDA pro will take you to the following code section.
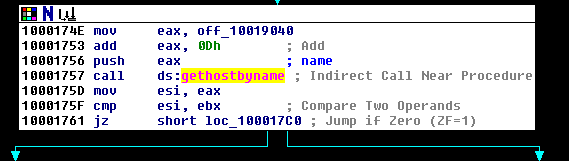
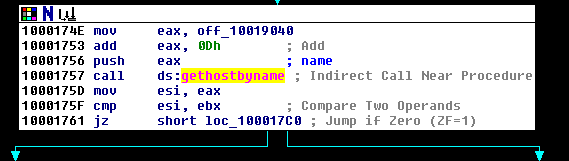
- We can see that gethostbyname is being called, but this function needs 1 parameter. That function parameter is pushed with statement Push eax. But what is in Eax? Let's backtrack, and we can see that initially string at off_10019040 is moved to eax. Let's look as to what is in off_10019040.
-
Double Click on off_10019040 and it will redirect to below declaration.

- We can see that the string it contains is [This is RDO]pics.practicalmalwareanalysisc.com.
- Now let's jump back to code from where we came by clicking on
 in the menu.
in the menu. -
Looking at the instructions below, we can infer that
- First, the string at off_10019040 is moved to eax
- Then eax is incremented by 0xD bytes, to point to pics.practicalmalwareanalysisc.com
- Then the function gethostbyname is called to retrieve IP address for the DNS name extracted above.
- Let's look at the strings present in the dll. Click on Strings tab in IDA pro.
-
We can see a lot of plain text strings in the dll which is an indication that the strings are not encoded inside dll.

- Above, we can see that the string [This is RDO]pics.practicalmalwareanalysisc.com which we find out earlier. Let's look at some other interesting strings
-
We could see a string to invoke command prompt inside dll which is unusual.

-
Double click on string listed above, and it will take you to section. Place the cursor on the command and press 'X' key to check cross-references.

- We can see that there is the only reference of cmd.exe. Click on the reference and press ok.
-
Ida pro will navigate to the below section

- This is a branch code which stems out from a comparison from above block.
- We can see that in the above block dword_1008E5C4 is compared with ebx.
- Following the previous approach, let's back track a little bit to see what is inside dword_1008E5C4.
- Click on dword_1008E5C4 and press 'X' key.

- As we can see from above screenshot, there are 3 references of dword_1008E5C4. We can see there are 2 occurrences of cmp instruction and one of mov instruction. mov is more interesting, and it is moving some value (eax) in dword_1008E5C4. Click on mov references and click OK.
-
We will navigate to below section
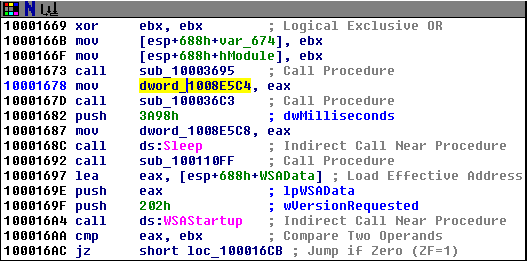
- We can notice that before instruction mov dword_1008E5C4, eax, we can see a call to function call sub_10003695. Which means that the function sub_10003695 is returning some value which is stored in eax and then moved to dword_1008E5C4. Let's see what the function sub_10003695 is doing.
-
Double click on function sub_10003695, and it will navigate to below function

- From the above code block, we can see that the code is checking the OS version and then comparing the value with 2. Post that byte is setup per comparison result and this value is returned from the code section to the previous section and then to invoke cmd.exe or command.exe.
-
Let's now look at the exports section of the dll. Click on Exports tab or views >open subviews > Exports. Below is the list of export section for this dll

-
Of all the export list, let's look at the PSLIST. Double click on PSLIST and flow will be redirected to below code block
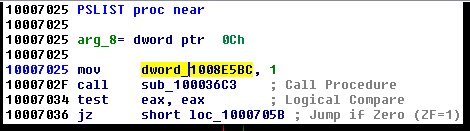
-
There is a call to sub_100036C3. Double click on sub_100036C3. Below is the code block for sub_100036C3.

-
The code above is getting the OS version and then comparing it. Based on the comparison a JMP instruction will take place. A JMP instruction is a non-conditional instruction which is used to jump to a specified location. And later value is returned in eax which is what is tested in PSLIST above.

- Navigate back to PSLIST block by following either navigation button as mentioned in step 15 or via Exports sections as mentioned in step 33.
-
After instruction in test eax, eax in PSLIST block, there is a conditional JMP instruction.

- Let's follow for JZ not equal to 0, and if we follow down the code, there are 2 more branches of code which stems from comparing jnz short loc_1000704E.
- In both the code branches, a function call is made i.e. call to sub_10006518, sub_1000664C.
- Both the function will point to the same place so let's look into one of the functions calls.
-
Let's look at sub_10006518. Double click on sub_10006518 and flow will be redirected to the following area
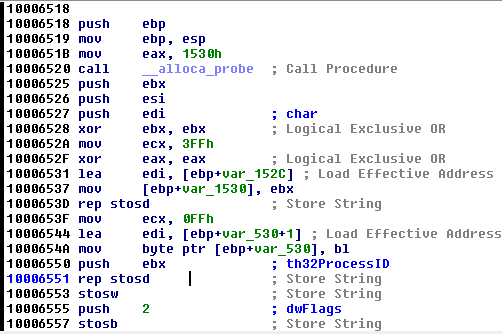
-
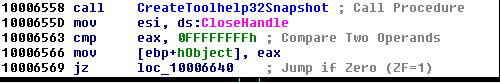
If we scroll down a bit, we can see a call to CreateToolhelp32Snapshot to take a snapshot of the specified process
-
And if we follow branches then, we can see a call to Process32First and Process32Next, which shows that dll is enumerating the Processes from the system and then sending it back over a socket to the above identified DNS name.


-
Let's find the 'IN' instruction in the dll. Click on Search > Sequence of bytes.

-
Fill in 'ED' opcode for IN instruction and check "Find all occurrences." Click Ok

-
Following is the occurrence of IN instruction in dll in text section
-
Double click on 'in' instruction (found in the previous step) and it will take us to below code (scroll down).

-
Let's look this code block from instruction at address 100061C7.start
- we can see that 544D55868h is moved to eax which is the magic number for VMxh.
- EBX is initialized to 0.
-
With move cx, 0Ah(10), it is detecting the version of VMware
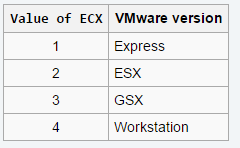
- VMware uses I/O port 5658h (VX) to communicate with VM. This value is moved to edx.
- Then with the IN instruction, the value of eax and edx is compared. If the code is running outside the VMware, then a privilege error occurs. Otherwise, ebx is copied with the magic number.
- Then with the cmp instruction, the value in ebx and the magic number is compared to check the whether the code is running inside VMware or not.





