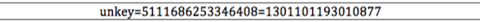PoS Malware: All You Need to Know
Introduction to POS malware
PoS malware continues to be a serious threat to several industries, from retail to the hotel industry. Respect our previous post, the number of attacks increased such as the number of strains of malware specifically designed to compromise PoS systems.
Security firms have investigated several incidents in the last twelve months involving payment card data and payment systems, and in many cases, the attackers used malicious code that targeted the point-of-sale devices. PoS malware is a very effective weapon in the arsenal of cyber criminals; these codes could steal sensitive information stored in the magnetic stripe the payment cards and most recent variant implement sophisticated evasion techniques and exfiltration methods

Become a certified reverse engineer!
In the previous post, we introduced the following Point-of-sale malware analyzing the featured implemented by cyber criminals.
- Sophisticated method to find card data.
- Self-update ability to execute new code.
- Effective measures to protect its code from analysis.
- The malware belongs to the "scrapers" family.
- Implementation of the Luhn formula to verify card validity.
- Use a Keylogger module.
- Efficient memory scraping process.
- Custom packer and new anti-debugging mechanisms.
- Implements the ability to harvest user input.
- To obtain persistence, it uses a registry entry with the name "Java. Update Manager".
- Disables the warning messages used by the OS.
- Implementation of the Luhn formula to verify card validity.
- Infects Mass Transit Systems.
- Allows remote control of victims.
- Implements functionalities of RAM scrapping and keylogging features.
- Allows loading of additional payloads through "File Upload" option for lateral movement inside the local network.
I anticipate you that much novelty appeared in the threat landscape in the last year, below the list of threats that presented the most interesting features:
- Ability to update and alter its capabilities remotely.
- Implements reconnaissance and hacking abilities.
- Use a keylogger module.
- It can capture and exfiltrate track one and two from payment cards by scanning processes.
- Phishing emails as an attack vector
- Malicious Macros
- MalumPoS disguises itself as "the "NVIDIA Display Driver
- Scalable
- Ram Scraper
- Written .Net
- Ram Scraper
- Spread through a botnet
- It has been around since at least 2011
- Cherry Picker is a memory scraper malware that uses QueryWorkingSet API
- The threat includes a cleaner module to remove all traces of the infection
- The malware experts took three weeks to reverse engineer one of the three kernel modules
- The ModPOS is a project to run a large-scale operation
- Pro PoS integrates a polymorphic engine that allows the threat to generate a different signature for each malware sample
- The Pro PoS support TOR to hide its C&C servers
- Memory scraper that iterates through running processes
- Known as "Cerebrus" in the underground
Punkey malware
The Punkey malware was spotted by the researchers at Trustwave during a law enforcement investigation a few weeks after the discovery of the NewPosThings PoS malware. The crooks used the Punkey malware to compromise payment systems of some organizations.
The investigators discovered three different strains of Punkey a circumstance that lead the researchers to believe that the malware was used by different criminal crews that tailored it for specific targets in the retail industry.
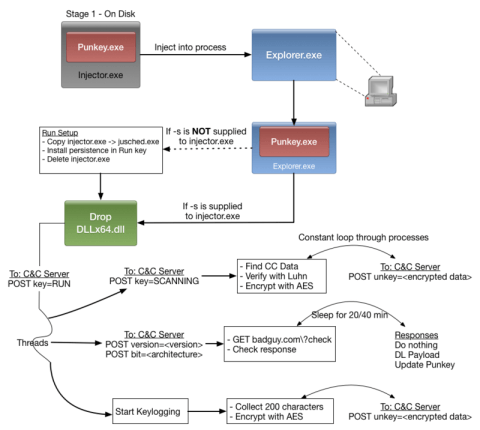
Figure 1 – Punkey (Trustwave)
Punkey implements common features of other PoS malware, but experts were surprised by its ability to update and alter its capabilities remotely.
"A second thread has spawned that handles downloading arbitrary payloads from the C&C server, as well as, checking for updates to Punkey itself. This gives Punkey the ability to run additional tools on the system such as executing additional reconnaissance tools or performing privilege escalation. This is a rare feature for POS malware." reads a blog post published by Trustwave SpiderLabs blog.
The malicious code also implements reconnaissance and hacking abilities; these features are not common for PoS malware.
"This traffic is AES encrypted, base64 encoded, then URL encoded. After reversing the process, the data sent looks like this (no, it's NOT a valid payment card number):"
"This is where the naming fun comes into play! The combination of P(OST)unkey and calling the malware author a punk was just too sweet to pass up." continues the post.
Data transferred by the Punkey PoS malware to C&C servers includes payment card numbers and data collected by the Keylogger module.
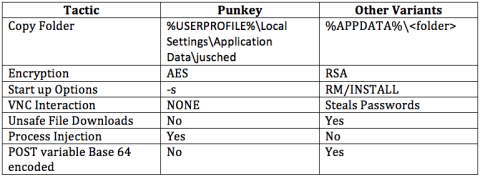
In the following table are listed the principal differences between tactics implemented by the Punkey and other PoS malware.
Figure 2 - Punkey Tactics
It is interesting to note the use of a Keylogger module and process injection mechanism that make this new threat an excellent weapon in the hand of cyber criminals.
NitlovePoS
NitlovePoS is a strain of PoS malware discovered by the experts at FireEye in May 2015; it can capture and exfiltrate track one and two from payment cards by scanning processes of the infected PoS machines.
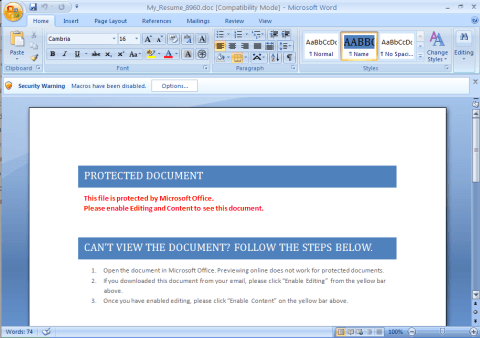
The experts at FireEye discovered a spam campaign spreading the malware; the malicious emails have subjects like "Any Jobs?", "Any openings?", "Internship," "Internship questions," "Internships?", "Job Posting,""Job questions,""My Resume" ,"Openings. The emails include an attachment named "CV_[4 numbers].doc" or "My_Resume_[4 numbers].doc", that embeds a malicious macro that once enabled trigger the infection process.
Figure 3 - Spam email
When the victim opens the document, it is displayed with instructions to enable the micro to view the document that claims to be protected. Once enabled, the "malicious macro will download and execute a malicious executable from 80.242.123.155/exe/dro.exe."
"To trick the recipient into enabling the malicious macro, the document claims to be a 'protected document,'" said FireEye researchers.
The threat actors behind the campaign have updated the payload several times to improve their efficiency.
"We focused on the "pos.exe" malware and suspected that it maybe targeted Point of Sale machines,"We speculate that once the attackers have identified a potentially interesting host form among their victims, they can then instruct the victim to download the POS malware. While we have observed many downloads of the various EXE's [hosted] on that server, we have only observed three downloads of "pos.exe"." added FireEye researchers.
The malware adds an entry to the registry key to gain persistence of the infected system.
"NitlovePOS expects to be run with the "-" sign as an argument; otherwise, it won't perform any malicious actions. This technique can help bypass some methods of detection, particularly those that leverage automation."
"If the right argument is provided, NitlovePOS will decode itself in memory and start searching for payment card data," "If it is not successful, NitlovePOS will sleep for five minutes and restart the searching effort."
Malumpos
A few weeks after the discovery of the NitlovePoS, the security experts at Trend Micro have spotted a new strain of the MalumPoS malware that was reconfigured to compromise PoS systems based on the Oracle® MICROS® platform.
Trend Micro was the first security firm to detect MalumPoS in the wild; the new variant was developed to target this Oracle platform that is widely used (330,000 customer installations worldwide) in various industries, including the hospitality, food and beverage, and retail industries.
Most of these platforms are located in the United States, the MalumPoS belong to the family of PoS RAM scrapers, it means that the malicious code steals customer credit card data directly from the RAM memory of the infected systems.
The researchers al Trend Micro explained that the MalumPoS was designed to be configurable, it has a modular structure that makes the threat scalable. The threat actors can change or add other processes or configure new targets.
"He can, for example, configure MalumPoS to include Radiant or NCR Counterpoint PoS systems to its target list." states the post.
The researchers highlighted the following characteristics of the MalumPoS malware:
- NVIDIA disguise: Once installed in a system, MalumPoS disguises itself as "the "NVIDIA Display Driver" or, as seen below, stylized to be displayed as "NVIDIA Display Driv3r." Although typical NVIDIA components play no important parts in PoS systems, their familiarity to regular users may make the malware seem harmless.
- Targeted systems: Aside from Oracle MICROS, MalumPoS also targets Oracle Forms, Shift4 systems, and those accessed via Internet Explorer. Looking at the user base of these listed platforms, we can see that a major chunk is from the US.
- Selective credit card scraping: MalumPoS uses regular expressions to sift through PoS data and locate pertinent credit card information. We have seen an older PoS threat called Rdasrv demonstrate the same behavior. In the case of MalumPoS, it selectively looks for any data on the following cards: Visa, MasterCard, American Express, Discover, and Diner's Club.
Trend Micro published a detailed analysis of MalumPoS malware that includes IoC indicators and YARA rules that could be used to detect the presence of the malware.
New GamaPoS Malware
GamaPoS is the name of another PoS malware spotted this summer by Trend Micro, when its experts discovered that the malware was distributed by a large botnet known as Andromeda, which has been around since 2011.
"We discovered GamaPoS, a new breed of point-of-sale (PoS) threat currently spreading across the United States and Canada through the Andromeda botnet ." states Trend Micro in a blog post.
The GamaPoS malware most infected Windows systems in the US (85%) and Canada (2%), the malicious code hit PoS systems in some industries, including home health care, online retail, and consumer electronics.
The researchers at TrendMicro discovered that the malware is written in.Net, an unusual choice for the development of a RAM scraping PoS malware.
The experts noticed that hackers have chosen to spread the malware through a botnet instead by stealing or guessing remote access credentials in response to countermeasures implemented by many retailers. Many organizations, in fact, have improved the security of their systems protecting internal resources from remote attacks.
Bad actors have used a botnet to infect machines worldwide, including machines inside the trusted internal networks of target organizations.
The infection starts with spam messages containing malicious emails purporting to include PCI DSS (Payment Card Industry Data Security Standard) compliance documents or software updates necessary to protect systems from the recently discovered MalumPos malware. The attachments contain malicious macros that install the backdoor on the infected PC that is used to serve the GamaPoS.
"This means that it launches a spam campaign to distribute Andromeda backdoors, infects systems with PoSmalware, and hopes to catch target PoS systems out of sheer volume. Rough estimates show us that GamaPOS may have only hit 3.8% of those affected by Andromeda." continues the post.
The experts also discovered that threat actors used the backdoor to download tools that can be used to make lateral movements within the targeted network.
GamaPoS targets a range of cards, including Visa and Discover, their users are exposed to the risk of hack.
"While the evaluated example does not do Luhn validation, GamaPoS does manually filter the data by evaluating the first few numbers of the scraped data.
- 4 (length=12) – Visa
- 56 to 59 (length=14) – Maestro and other ATM/debit cards
- 6011 (length=12) – Discover Card
- 65 (length=14) – Discover
Finally, it would attempt to upload the collected data via the command-and-control server that has been selected during initial execution." states the post.
Cherry Picker
A spike in the number of sophisticated point-of-sale (PoS) malware was observed by security experts at the end of 2015.
In November 2015, security researchers from Trustwave have analyzed an insidious point-of-sale (PoS) malware dubbed Cherry Picker that threat has been around since at least 2011. The malware remained under the radar due to the implementation of sophisticated evasion techniques.
"Cherry Picker's use of configuration files, encryption, obfuscation, and command line arguments have allowed the malware to remain under the radar of many security companies and AV's," Trustwave researchers said. "The introduction of new way to parse memory and find CHD, a sophisticated file infector, and a targeted cleaner program have allowed this malware family to go largely unnoticed in the security community."
Cherry Picker Pos malware was detected for the first time in 2011 by experts at Trustwave, one of the samples analyzed by Trustwave was composed of two components, a command line interface (sr.exe), and the searcher.dll that is a code which is directly injected into targeted processes bysr.exe.
Cherry Picker is a memory scraper malware that uses a file infector for persistence.
The threat includes a cleaner module that allows it to remove all traces of the infection from the system.
The latest version of the Cherry Picker PoS malware uses a set of API called QueryWorkingSet to scrape the memory and gather card data. The stolen data are then written into a file and sent back to the control servers.
"Once the data is exfiltrated, the cleaning process begins. The malware developers created a targeted cleaner tool designed to restore the infected system to a clean state. The threat relies on the popular remote control software TeamViewer to overwrite and remove files, logs and registry entries." reported SecurityWeek.
The researchers observed that systems infected by Cherry Picker ware also infected by other threats such as the AutoIt PoS malware and the Rdasrv that is one of the earliest PoS RAM scrapers.
Trustwave researchers spotted three different strains of the Cherry Picker PoS malware, a circumstance that confirms the evolution of the threat in the criminal ecosystem.
The malware authors improved the mechanism for persistence; earlier versions used a registry entry, in more recent instances, it uses an updated version of sr.exe, srf.exe, which has been used to install the malware and inject a DLL into processes.
The Cherry Picker PoS, differently from similar threats focuses only on the process that manages card data; this process is reported in the configuration file.
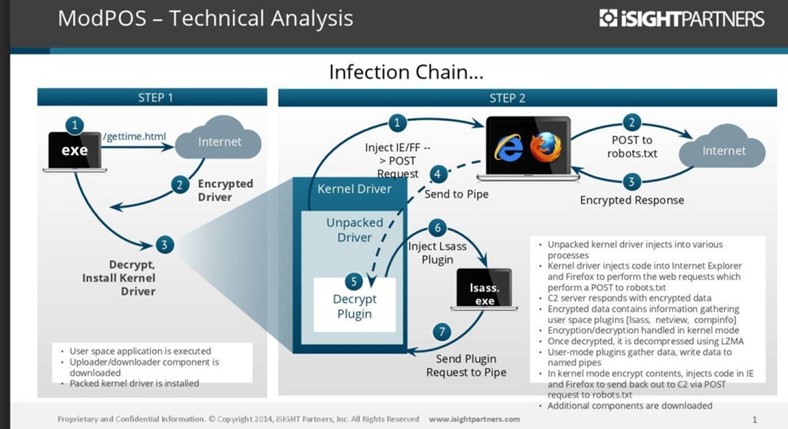
ModPos
Always in November, data belonging to millions of US bank cards were gathered by a new POS malware called ModPOS. The threat was found in some unnamed companies, including big retail companies.
The available information about the attackers are not a lot, but it's known that they have been operating since 2013. It is an organized criminal syndicate that remained under the radar for years.
"This is POS [point-of-sale] malware on steroids," "We have been examining POS malware forever, for at least the last eight years and we have never seen the level of sophistication in terms of development …[engineers say] it is the most sophisticated framework they have ever put their hands on." Said iSight Partners senior director Steve Ward.
The malware experts took three weeks to reverse engineer one of the three kernel modules of the malware. To give you an idea of the complexity of the threat, the same malware experts that analyzed ModPos only needed 30 minutes for the reverse engineering of the code Cheery Picker POS malware.
Steve Ward was impressed by the "incredibly talented" authors of the malware and even commented that they did an "amazing job", because their understanding of the security around POS was huge, "It is hard not to be impressed," Ward said.
Another point of strength is the encryption used to protect traffic data, it is a 128 and 256-bit encryption, and a new private key was needed per customer.
Figure 4 - ModPoS malware
Ward confirmed that the authors spent a huge amount of money and time on each packed kernel driver module, which acts as a rootkit, and it is difficult to detect and to reverse engineer.
The ModPOS is a project to run a large-scale operation that can get a return on their investment.
After the discovery of the ModPOS, the attackers will need to change part of the base code to re-gain the obfuscation they achieved with previous variants. These changes will be harder to implement and needs a significant monetary investment.
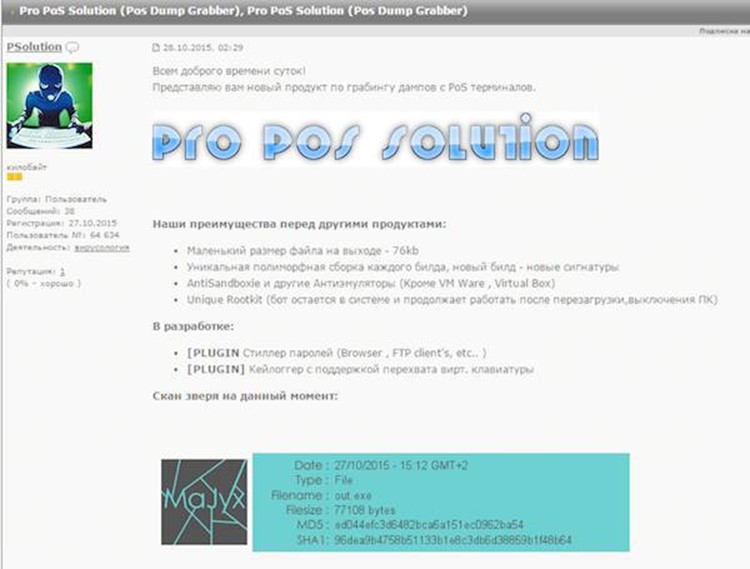
Pro PoS
It was Christmas time when researchers from the threat intelligence firm InfoArmor discovered a new PoS malware dubbed Pro PoS that is available for sale in the underground forums. The authors of the Pro PoS malware are hackers from Eastern Europe that designed their malicious code malware to infect the principal operating systems used by the companies in the retail industry, including newer operating systems.
Figure 5 - Pro PoS malware
According to the threat intelligence firm InfoArmor, cyber criminals were already using the Pro PoS Solution to target PoS systems used by retailers and SMBs in the US and Canada.
Pro PoS is a tiny malware, just 76KB, that acts as a rootkit and implements mechanisms to avoid antivirus detection. The experts at InfoArmor explained that Pro PoS integrates a polymorphic engine that allows the threat to generate a different signature for each malware sample.
On November 27, experts at InfoArmor noticed a significant increase in the Pro PoS Solution price that was offered at $2,600 for a six-month license.
The Pro PoS support TOR to hide its Command and Control (C&C) servers.
In the last 2/3 years, we have seen a significant increase in the number of POS malware, their diffusion is becoming even more worrying. We read about many high-profile breaches that involved high-complex malware targeting payment systems worldwide.
CenterPOS
Early 2016 experts at FireEye disclosed a new PoS malware dubbed CenterPOS, This fairly new malware was discovered in September 2015 in a folder that contained other POS malware, including NewPoSThings, two Alina variants known as "Spark" and "Joker," and the infamous BlackPOS malware.
Figure 6 - Center PoS
The sample analyzed by FireEye is identified with an internal version number 1.7 and contains a "memory scraper that iterates through running processes in order to extract payment card information. The payment card information is transferred to a command and control (CnC) server via HTTP POST":
The experts discovered many samples of the malware version 1.7 that were associated with different CC locations:
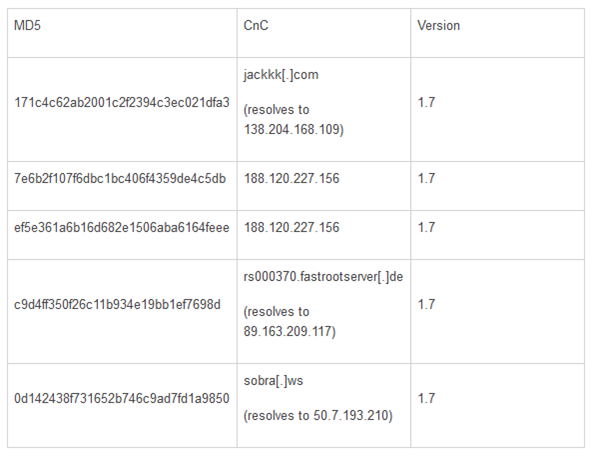
The analysis of a live CnC server allowed FireEye to discover that in the underground the malware is known as "Cerebrus" (don't confuse it with the RAT also known as Cerebrus).
Besides the version 1.7, a version 2.0 was found, and it's very similar with 1.7 with the difference that in version 2.0 it is used a config file to store the information related to the CC server.
"The malware contains two modes for scraping memory and looking for credit card information, a "smart scan" mode and a "normal scan" mode. The "normal scan" mode will act nearly the same as v1.7."
The CenterPOS scans all processes searching for those that meets the following criteria:
- The process is not the current running process.
- The process name is not on the ignore list.
- The process name is not "system," "system idle process," or "idle."
- The process file version info does not contain "Microsoft," "Apple Inc," "Adobe Systems," "Intel Corporation," "VMware," "Mozilla," or "host process for windows services."
- The process full path's SHA-256 hash is not in the SHA-256 blacklist.
If a process meets the criteria "the malware will search all memory regions within the process searching for credit card data with regular expressions in the regular expression list."
Moving on to the "smart scan", this scan is initiated with a normal scan, and "any process that has a regular expression match will be added to the "smart scan" list. After the first pass, the malware will only search the processes that are in the "smart scan" list."
"After each iteration of scanning all process memory, the malware takes any data that matches and encrypts it using TripleDES with the key found in the configuration file."
The malware sends information to the CC server about the "hacked" system including the current settings, always after a performed scan. The collected info includes all system users, logged in users, sessions, process list, and current settings list. The info is sent by a separate HTTP POST request.
"The malware primarily sends data to the CnC server, but can also receive commands and in addition to processing commands, the malware also accepts commands to update its current settings."
The next table includes data related the variants of the CenterPOS version 2.0 found by FireEye:
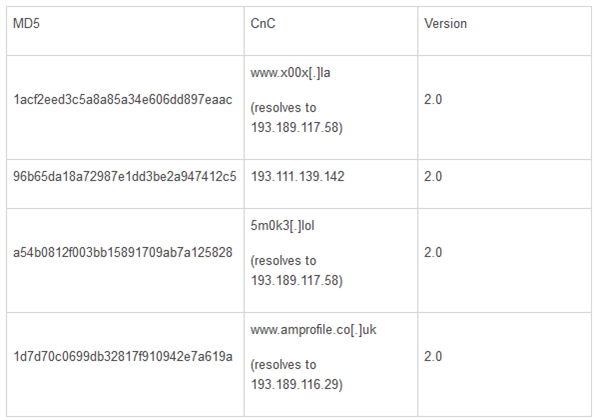
CenterPOS or Cerebrus as will likely continue to evolve; their authors will include more functionalities in future versions.
Operation Black Atlas
During the holiday season, the experts at Trend Micro uncovered a large-scale operation dubbed Operation Black Atlas, about notorious BlackPOS PoS malware that is the threat primarily used in these attacks.
BlackPOS, also known as Kaptoxa, is the malicious code used by crooks behind the Target breach in 2013 and other cyber attacks on retail accounts in 2014.
Threat actors behind the operation have developed a set of hacking tools used in their operations.
"Operation Black Atlas has been around since September 2015, just in time to plant its seeds before the holiday season. Its targets include businesses in the healthcare, retail, and more industries which rely on card payment systems." reads a blog post published by Trend Micro. "The operation is run by technically sophisticated cyber criminals who are knowledgeable in a variety of penetration testing tools and possess a wide network of connections to PoS malware in the underground market."
Threat actors behind the Black Atlas operation used some popular PoS malware, including Alina, NewPOSThings, a Kronos backdoor, and, of course, the BlackPOS threat.
The bad actors have stolen user login credentials, email accounts, and other sensitive information from victims. The experts also discovered a live video feed of closed-circuit television (CCTV) cameras in a gasoline station, evidence that crooks are collecting whatever information is available.
"Similar to GamaPoS, the Black Atlas operators employed a "shotgun" approach to infiltrate networks as opposed to zeroing in on specific targets. They basically checked available ports on the Internet to see if they can get in, ending up with multiple targets around the world." continues the post.
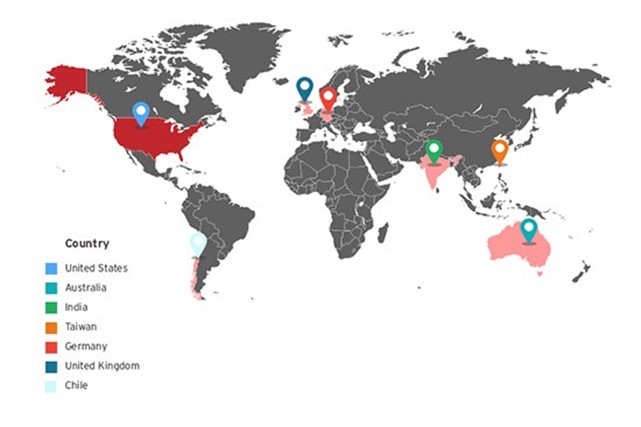
The experts at Trend Micro observed that Black Atlas operators used the botnet Gorynych or Diamond Fox in a number of installations.
In the following image has reported the distribution of Gorynych targets in Operation Black Atlas.
Figure 7 -Black Atlas operation
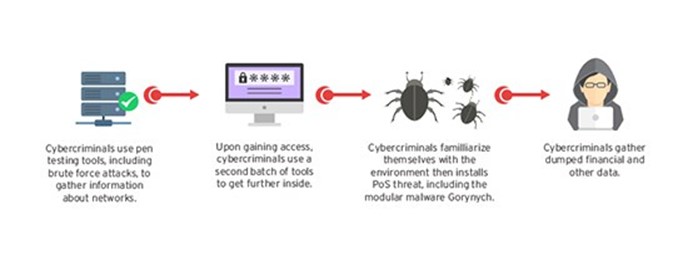
The Operation Black Atlas targeted numerous healthcare organizations in the US; threat actors use to run an initial intelligence gathering or reconnaissance activity to identify the best systems to compromise then they used the tools to run the attack (i.e. Brute force or dictionary attack).
"Networks with weak password practices are likely to fall victim to this initial penetration testing stage. Many of these tools are easily downloaded from various sites on the Internet. The cybercriminals will then create a test plan based on the initial probe, and then use a second set of tools to execute the said plan."
Figure 8 - Black Atlas operation (Trend Micro)
In the attack stage, the crooks utilized remote access tools to steal more information and move laterally within the network, one inside they inject the PoS threats.
Trend Micro announced it will provide further details about the Black Atlas Operation.
Conclusions
The number of data breaches is growing at a fast pace, the retail industry is among the most affected sectors, but the threats presented have a significant impact on many other industries.
Security experts sustain that the measures adopted in the retail industry to prevent cyber attacks are not adequate.
PoS systems are a privileged target of cyber criminals; this means that criminal organizations will continue in investing in the development of new malicious codes that implement sophisticated evasion techniques.
Many POS malware were spotted in the last years; their proliferation is the result of a huge demand in the criminal underground.
I have no doubts, in the incoming months, we will assist with an increased in the number of incidents involving POS malware.
References
http://securityaffairs.co/wordpress/36113/cyber-crime/punkey-pos-malware.html
https://www.trustwave.com/Resources/SpiderLabs-Blog/New-POS-Malware-Emerges---Punkey/
http://securityaffairs.co/wordpress/37201/cyber-crime/nitlovepos-new-pos-malware.html
https://www.fireeye.com/blog/threat-research/2015/05/nitlovepos_another.html
http://securityaffairs.co/wordpress/37612/cyber-crime/malumpos-pos-malware.html
http://securityaffairs.co/wordpress/44051/cyber-crime/centerpos-pos-malware.html
http://securityaffairs.co/wordpress/38643/cyber-crime/gamapos-pos-malware.html
http://securityaffairs.co/wordpress/41928/malware/cherry-picker-pos-malware.html
http://securityaffairs.co/wordpress/42220/cyber-crime/modpos-pos-malware.html
http://securityaffairs.co/wordpress/42464/cyber-crime/operation-black-atlas.html
https://infoarmor.com/wp-content/uploads/2015/12/Pro-POS-Solution-FINAL.pdf
http://securityaffairs.co/wordpress/42404/cyber-crime/pro-pos-malware.html
https://www.fireeye.com/blog/threat-research/2016/01/centerpos_an_evolvi.html