PHP Lab: Review the code and spot the vulnerability
Introduction and background
An application has been developed in PHP, and the source code of the login page is given for source code review to ensure that no serious vulnerabilities are left in the application.
Please note that the following setting is enabled in the php.ini file.
Learn Secure Coding
register_globals = On
The application can be accessed from the following URL.
http://192.168.56.101/webapps/globals/index.php
Source code can be accessed from
http://192.168.56.101/webapps/globals/source/
Review the application and its code. Report if any vulnerabilities are identified.
Let's begin:
Before diving into code analysis, let us understand how the application behaves.
When the following link is opened,
http://192.168.56.101/webapps/globals/index.php
It shows a login page where we need to enter the password.
If the user enters a wrong password, the following message will be shown.
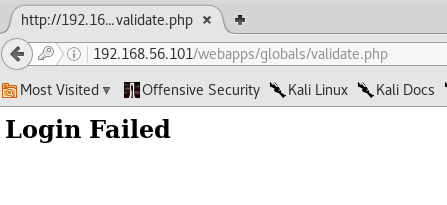
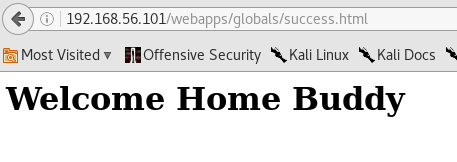
If the correct password is entered, the user will be greeted with the following message.
Note: p@ssw0rd is the correct password to log in.
Now, let us check the source code of this application and see what's happening. Let's begin with index.php.
index.php
<html>
<head>
</head>
<body>
<form action="validate.php" method="post">
<h2>Enter your password to authenticate</h2>
<label for="password">Your Password</label>
<input type="password" name="password"/>
<br /><br />
<input type="submit" value="Login"/>
</form>
</body>
</html>
The user is asked to enter his password on this page. When he enters the password, it will be passed to validate.php as a post parameter for further validation.
Let us check validate.php
validate.php
$db_file = dirname(__FILE__) . '/db.txt';
$data = file_get_contents($db_file);
$data = rtrim($data);
$password = $_POST['password'];
if ($password === $data) {
echo 'inside';
$authorized = true;
}
if ($authorized) {
header("Location:success.html");
}
else{
echo "<h2>Login Failed</h2>";
}
?>
This code reads the password from a db.txt file, which is shown later. The code, highlighted in red, validates the entered password and redirects the user to success.html if the password validation succeeds.
The key point to note here is the variable $authorized is not initialized, and security decision is made based on the value of it. As this variable is not initialized as false and register_globals is set to On, it is possible for an attacker to define the value of $authorized through a GET parameter. If an attacker defines this value as true, he can be authenticated without a valid password and will be landed on the success.html page.
success.html
<body>
<h1>Welcome Home Buddy</h1>
</body>
</html>
db.txt
Let us verify how this can be done.
Since the application is sending data in POST, it is a good idea to use a proxy tool such as Burp. In kali Linux, burp comes pre-installed. Following are the steps to configure and use it.
1. Launch Burp Suite on your Kali Linux by typing the command "burp suite" in a terminal.
You should see a screen as shown below.

Click Next and the following screen will be shown.

Click "Start Burp" and you should see the following while Burp loads.

Once done, you should see Burp Suite up and running. Now, navigate to Alerts tab and make sure that your Burp shows the following message.

This means Burp is running on your localhost port 8080.
2. Next, configure Ice Weasel in Kali Linux to route all the browser traffic through Burp proxy.
To do this, navigate to Edit > Preferences > Advanced > Network > Settings and enter configure 127.0.0.1:8080 as shown in the preceding figure.
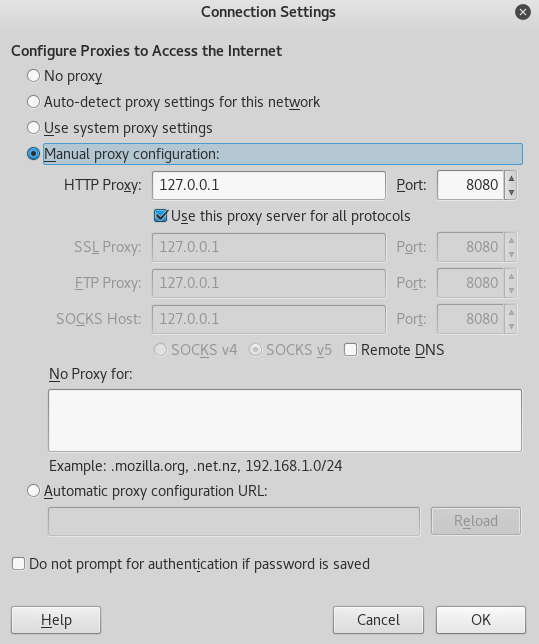
Finally click OK to save the settings.
3.
Now, launch the following URL in your browser
http://192.168.56.101/webapps/globals/
Enter an incorrect password "p@ssw0rd" and click Login.
Make sure you turn "Intercept On" before clicking "Login." Burp will intercept the request.
The request looks as shown below.

As we can see in the above figure, a POST request is made to validate the .php page.
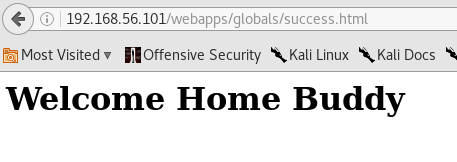
As mentioned earlier, modify this request by adding authorized=true as a GET parameter and click forward button.
Modified request looks as highlighted below.

Once we click forward, the user will be redirected to success.html even though he did not enter a correct password. This is shown below.
Learn Secure Coding
This lab clearly shows the security impact that can be caused due to the register_globals setting in the php.ini file. It is recommended to turn off register_globals and always initialize variables within your PHP scripts.


