Jus in Cyber Bello: How the Law of Armed Conflict Regulates Cyber Attacks Part II
Prohibition of Perfidy
 Article 37 of AP I - Prohibition of perfidy
Article 37 of AP I - Prohibition of perfidy

What should you learn next?
1. It is prohibited to kill, injure or capture an adversary by resorting to perfidy. Acts inviting the confidence of an adversary to lead him to believe that he is entitled to, or is obliged to accord, protection under the rules of international law applicable in armed conflict, with intent to betray that confidence, shall constitute perfidy. The following acts are examples of perfidy:
(a) The feigning of an intent to negotiate under a flag of truce or of a surrender;
(b) The feigning of an incapacitation by wounds or sickness;
(c) The feigning of civilian, non-combatant status; and
2. Ruses of war are not prohibited.
Without the prohibition of perfidy, certain humanitarian actions would not be possible and "quarter and succor would not be given, surrender would not be credible, and armistice would be meaningless."
Defining Cyber Perfidy
RULE 60 – Perfidy
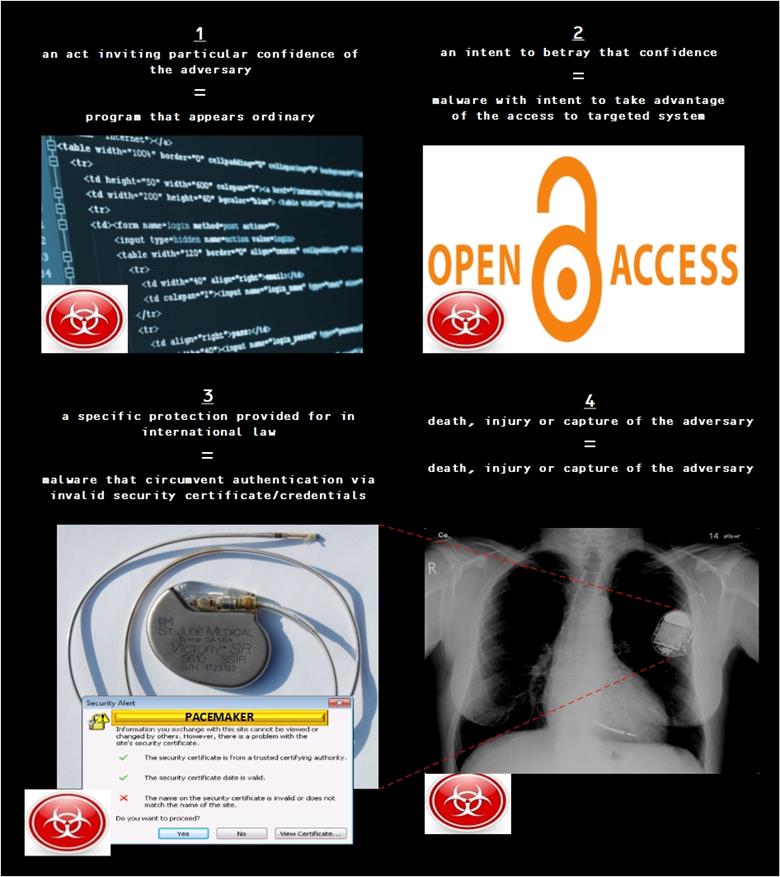
3. The prohibition has four elements: (1) an act inviting particular confidence of the adversary; (2) an intent to betray that confidence; (3) a specific protection provided for in international law; and (4) death or injury of the adversary.
Neil C. Rowe defines cyber perfidy as an act "whenever malicious software or hardware pretends to be ordinary software or hardware"—in other words, digital "acts inviting the confidence of an adversary […] with intent to betray that confidence" (2013, par. 7). Obviously, this definition is broad and, as the author realizes that himself, most of the cyber attacks today assume this form of compromising another system. Furthermore, impersonating a legitimate user of a computer device to gain access to it during cyber hostilities is also a conceivable alternative. At least as a rule established in theory, a computer-generated attack should not give the impression that is originating from the enemy's own IT infrastructure, as this would represent an equivalent of wearing the adversary's uniform.
RULE 60 – Perfidy
9. An example [of cyber perfidy] would be a situation in which the enemy commander is known to have a pacemaker. Malware that will disrupt the rhythm of the pacemaker and induce a heart attack is programmed to falsely authenticate itself as being generated by a legitimate medical source. The false authentication is accepted by the enemy's computer network and the malware attacks the pacemaker of the adversary commander, causing a heart attack [See the diagram below]. In this example, the confidence of the adverse party's computer system has been betrayed and, according to the majority of the Experts, the Rule has been violated.
Diagram 1
Example of Cyber Perfidy
Computer services whose modification would meet the requirements of cyber perfidy:
Nils Melzer enumerates examples of perfidy in cyberspace based on real-world such or on the cases envisaged in the provision itself:
"…belligerents can disguise the origin of their operations through the use of botnets or techniques like IP spoofing, camouflage combat troops or vehicles as medical transports by using internationally recognized protective signals, manipulate the enemy's reconnaissance data so as to wrongly make him believe that the opposing forces intend to surrender, or even send seemingly innocent civilian email attachments to individual recipients at a military headquarters, causing them to inadvertently infect the computer system with malware." (Melzer, 2011, p. 32)
Methods of tampering
A service then can be modified to:
In times of peace, these acts are criminal by virtue of domestic law; for example, the U.S. Federal Anti-Tampering Law (USC Title 18 Chapter 65, "Malicious Mischief") is in force when a consumer product is being manipulated. So these programs, according to Rowe, would qualify as "noncombatants" because they do not advance military objectives.
Considering Cyber Perfidy in the Context of Cyber War
Trust is the main casualty of perfidy, as when warring parties abuse the status of the Red Cross personnel. Consider now the impact of an insidious, illegal cyber operation that targets respected national hospitals, diminishing their reliability, in other words, becoming untrustworthy in the eyes of their patients.
In this connection, Rowe thinks that legitimate cyber combatants should in the first place openly announce their geographical locations – this would perhaps satisfy the rule that the belligerents need to carry their arms openly to distinguish themselves as in Art. 44 (3) of AP I – before hostilities to take place in order to avoid cyber perfidy committed by unauthorized entities claiming legitimate war status on false pretences.
Neil C. Rowe introduces many signs through which a digital forensic team can take its bearings of whether there was a cyber perfidy: comparison of bit patterns of software prior to and after the attack done via comparing hash codes. Every time new software is installed on a machine, hash codes are computed with the help of basic algorithms. Any change in the hash codes means that the software has been modified, too. The National Software Reference Library (NSRL), a U.S. government institution, stores hash codes on a vast number of software, and this treasure can be obtained for free. However, as you might have guessed, comparison of hash codes is a time-consuming process. Besides, a crafty rootkit appropriated enough credentials, virtually in control of a targeted operating system, may either disable checking software or instruct it to falsify the detection results.
Cyber Perfidy is Limited to Kill, Injury or Capture
There are elements in the Stuxnet case that might be interpreted as a cyber perfidy. The hidden target of the worm was the control equipment made by Siemens Corporation of centrifuges in an Iranian nuclear plant. Jus in bello aside, this global cyber infection was illegal in many countries because it violated end-user license agreements for Siemens and Windows OS.
In addition, on its way to this target, the Stuxnet worm had to spread over and infect first many civilian computers and networks, and then disguise as ordinary versions of programs. In finding its primal target, Stuxnet reprogramed systems so as to change the reading on all instruments, readouts, and dials to make everything look normal, and then would hide itself. Engineers could no longer tell whether the instruments display correct information.
RULE 60 – Perfidy
10. The perfidy Rule does not extend to perfidious acts that result in damage or destruction of property.
Regardless of this case, there seems to be an obvious loophole left out on purpose by the lawmakers with respect to the principle of perfidy, because IHL proscribes only perfidious acts that lead to killing, injuring or capturing of an enemy. Consequently, cyber attacks limited to causation of physical or functional harm to infrastructure and data, or other similar forms of incapacitation or disruption, would not come under this ban even if they are furthered by resort to perfidious deception.
Ruses
Making a proper difference between what is permitted – ruses of war—and what is not – perfidy – is a matter of considerable importance.
Communication of misleading, incorrect information on tactical manoeuvres, rally point updates and current location of troops and forging adversary's intelligence database are a permissible ruse.
Direct Participation in Cyber Hostilities and Cyber Combatants
Article 51 AP I - Protection of the civilian population
2. The civilian population as such, as well as individual civilians, shall not be the object of attack
3. Civilians shall enjoy the protection […] unless and for such time as they take a direct part in hostilities.
Based on the conception that warfare is a territory reserved for certain groups of protagonists, others, as the civilian population, should normally not take direct part if they want to keep their legal protection. Hence, observing the involvement of these groups in hostilities is important.
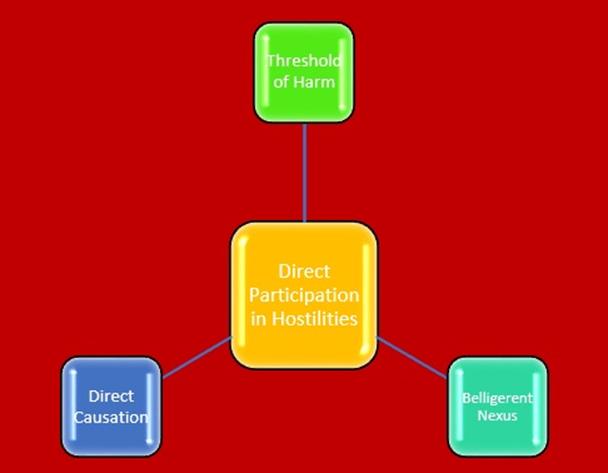
The ICRC has released prescriptive guidelines that set forth a three-pronged test for what constitutes a direct participation in hostilities.
Diagram 3
"Direct Participation in Hostilities" Test
Threshold of Harm
The act must adversely affect the military of the opposing party, that is, to cause harm of a military nature. For instance, "electronic interference with military computer networks could […] suffice, whether through computer network attacks […] or computer network exploitation" (Prescott, 2012, p.3). Alternatively, if the harm is not done to the military, it must be very likely to cause death, injury or destruction on protected persons or objects.
Furthermore, some scholars deem that this threshold of harm should take into account cyber attacks that terrorize civilians within the meaning of "inhumane treatment" set out by the International Criminal Court /ICC/ as "severe physical or mental suffering" if the act is of sufficient gravity to cause injury.
N.B.
While the scope of an armed attack excludes espionage and exploitation operations, the notion of hostilities is apparently broad enough to include them.
Direct Causation
Second, a direct causal link between the act and the consequences likely to result must exist. As to the timeframe matter, if "the execution of a hostile act does not require geographic displacement, as may be the case with computer network attacks [,] the duration of direct participation in hostilities will be restricted to the immediate execution of the act and preparatory measures forming an integral part of that attack (Prescott, 2012, p. 3)."
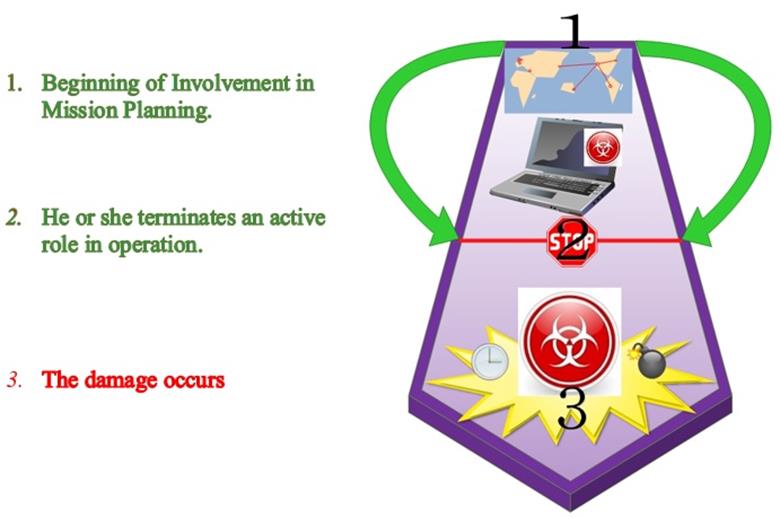
The majority of the International Group of Experts (IGE) behind the Tallinn Manual seems to prolong the temporal factor a bit more, calculating that "the duration of an individual's direct participation extends from the beginning of his involvement in mission planning [how to emplace a Trojan malware, for example] to the point when he or she terminates an active role in operation…the period of direct participation may not necessarily correspond with the point at which the damage occurs (RULE 35(8) – Tallinn Manual)."
Diagram 3
Duration of Direct Participation in Cyber Hostilities (Tallinn Manual)
Belligerent Nexus
Third, there is a required threshold of harm directly caused to the detriment of another party that the act must be designed to reach.
In the light of the ever increasing cyber occurrence of cybercrime, telling apart cyber belligerents and cybercriminals could be challenging.
The Rule 29(iii) of HPCR Manual on International Law Applicable to Air and Missile Warfare elaborated when cyber attacks amount to direct participation as "[e]ngaging in electronic warfare or computer network attacks targeting military objectives, combatants or civilians directly participating in hostilities, or which is intended to cause death or injury to civilians or damage destruction of civilian objects."
The Status of Cyber Warriors
Combatants
According to the Hague Conventions, sole members of regular armed forces to a state are entitled to participate and use force against the enemy. Unless for violation of LOAC, they should not be prosecuted for their wartime actions. This is the so-called combatant immunity. If they fall captive, combatants are given a prisoner-of-war privilege as well (Art.44 AdditionalProtocol I).
RULE 26 – Members of the Armed Forces1. The notion of combatancy is limited to international armed conflict;2. […] a combatant who conducts cyber operations that violate domestic criminal law may not be prosecuted for such actions so long as they are carried out in compliance with the law of armed conflict. Combatant immunity is a customary international law principle recognized in Article 43(2) of Additional Protocol I.
Under IHL, the armed forces of a state comprise all ranks of organized armed forces, groups and units under command of staff officers responsible to the state for the conduct of their subordinates. Given the modernity of cyber operations, they are generally implemented by highly specialized personnel. Provided they are members of armed forces, their status, rights and duties coincide with those of traditional combatants.
Combatants must conform strictly to the law of war at all times, but the inability to follow it does not deprive them of "combatant" status. However, Article 44 (3) of AP I stipulates that "soldiers" should wear a uniform or carry their arms openly in preparation or during engagement to identify themselves and failing to do so may lead to stripping of their combatant privilege with a tribunal's verdict.
It is rather unclear whether cyber-combatants should satisfy the requirement to wear "…a fixed distinctive sign recognizable at a distance Art. 1(2) of 1907 Hague Convention)." The International Group of Experts did not determine whether this rule should or can be fulfilled in cyber warfare.
Responsible countries, on the other hand, might lay the matter to heart or out of good faith decide to ensure their operations in cyberspace are by all means lawful. For those who decide to respect the letter of the law, labelling their cyber attacks with some sort of encrypted signature sounds probably reasonable. This signature or label should be hidden from casual inspection, perhaps with the help of a decryption key known to the attacker or neutral entity and which will prove who the source of the attack is.
Civilian immunity and combatant privilege are foundation stones at the heart of LOAC.
Armed forces are often in need of know-how for additional operational capabilities, a.k.a. non-military duties, delivered with the help of civilians and civilian experts.
Contractors and Civilian Employees
Common practice for states is to employ private contractors and civilians to perform a variety of functions usually within the ambit of the regular military personnel. A scenario already known from the practice is the CIA having to employ civilians to pilot drones for targeting killing, or hiring private contractors in conflict zones such as Iraq and Afghanistan. Today, this tendency is even more ubiquitous because of the rapid advance of information technologies.
It might be beneficial for governments to assign the creation of a secret and sizable zero day virus for attacking other states to civilians, because states may not possess the expertise and it is easier for a government to deny any involvement. For that reason, among other things "it is not a coincidence that the creation of "Stuxnet" seems to have been assigned to several nongovernmental subjects, each of which was assigned to develop only a 'piece' of the malware, without being aware of the range of the overall project."
As a result, contractors and civilian employees entrusted with the conduct of cyber operations remain civilians as long as they assume activities not equal to direct participation in hostilities. They are even entitled to the prisoner-of-war status in the event of capture if they are formally instructed to accompany a belligerent state's armed forces in an international conflict.
RULE 34 – Persons as Lawful Objects of Attack
7. The International Group of Experts agreed that individual contractors are civilians who may only be targeted based on their direct participation in the hostilities (Rule 35).
8. Other civilian government employees are civilians who are targetable only for such time as they directly participate in hostilities.
More to this line of analysis, if they are expressly authorized to take part in the hostilities, these private contractors/civilians become, de facto, irregular cyber combatants, and as such, they forfeit their civilian status but gain, in addition to the prisoner-of-war privilege, combatant status.
Levée en Masse
"Levée en masse" refers to residents inhabiting a given territory who spontaneously and in unorganized fashion recourse to use of force in attempt at repelling an approaching enemy and provided that they carry their arms openly and respect laws and customs of war. They are entitled to prisoner-of-war status and combatant privilege.
Transferred to online affairs, it may at first seem incomprehensible how this group will exist there. Indeed, cyber warfare procures an ideal opportunity for levée en masse to flourish; one word is enough—"hacktivism"—non-hierarchical, spontaneous, collective but unorganized at the same time cyber defense action driven by hacktivists in great numbers.
RULE 27 (5) – Levee en Masse
5. According to a majority of the Experts, the concept of levee en masse is to be understood in a narrow sense, requiring the physical invasion of national territory.
The Crimea crisis provides us with a first-hand experience of how the IHL institute of levée en masse can be transferred to Internet. In unorganized and spontaneous minor DDoS attacks against what they undoubtedly consider an occupier, allegedly Ukrainian hacktivists succeeded in bringing down several Russians websites belonging to the government, the Foreign Ministry and the central bank.
As to the requirement to "carry their arms openly", theoretically speaking, we can consider it fulfilled when there are no acts of cyber perfidy, i.e., feigning of protected or non-combatant status.
Members of Organized Armed Groups
These are members of non-state belligerents and they do not qualify as civilians. Persons who initiate cyber attacks on behalf of a non-state organized armed group on a continuous basis ("[…] the preparation, execution, or command of acts or operations amounting to direct participation in hostilities" (Melzer, 2009, p. 38)) and reach the threshold of direct participation in hostilities lose their civilian status, because they become members of this group, and may become an object of attack even if they do not participate actively in the hostilities at that particular moment.
 RULE 26 (5) – Members of the Armed Forces
RULE 26 (5) – Members of the Armed Forces
[…] Such organized armed groups are assimilated to the armed forces and as a group must, pursuant to Article 4A(2) of Geneva Convention III and customary international law, fulfil four conditions:
a) being commanded by a person responsible for his subordinates;
b) wearing a distinctive emblem or attire that is recognizable at a distance;
c) carrying arms openly; and
d) conducting operations in accordance with the law of armed conflict.
Irregular forces that meet these conditions and belong to a party to the conflict qualify as combatants and are entitled to combatant immunity and prisoner of war status.
Civilians
In the context of IHL, the concept of civilians is drafted by giving an account of who is not:
This includes members of armed forces of either a state or non-state party (militia) to an armed conflict, or the levée en masse. Civilians are granted protection against military attack and other dangers surrounding military operations so long as they do not take part in the hostilities.
 RULE 32 – Prohibition on Attacking Civilians
RULE 32 – Prohibition on Attacking Civilians
The civilian population as such, as well as individual civilians, shall not be the object of cyber attack.
1. This rule is based on the principle of distinction, set forth in Rule 31. It has been codified in Article 51(2) of Additional Protocol I and Article 13(2) of Additional Protocol II and is undoubtedly reflective of customary international law in both international and non-international armed conflict.
This category in a cyber war scenario would probably include all hackers that are neither having state services, nor belong to an organized armed group.
Cyber civilians would lose their status and protection if they decide to unleash malware, resulting in taking direct part in hostilities for the time their participation lasts. "Contrary to combatants, however, they do not benefit from immunity from prosecution for lawful acts of war (so-called "combatant privilege") and, therefore, can be punished by their captor for any violation of national law," states Melzer (2011, p. 35). Nonetheless, captured civilians that participated directly in hostilities are always entitled to humane treatment and fair trial.
RULE 29 – Civilians
Civilians are not prohibited from directly participating in cyber operations amounting to hostilities but forfeit their protection from attacks for such time as they so participate.
1. […]no rule of treaty or customary international law prohibits civilians from directly participating in hostilities during either international or non-international armed conflict […] they lose their protection from attack (Rule 32) when doing so (Rule 35).
Taking part in hostilities, knowingly or not, especially in an interconnected medium, can be a very alarming trend. Many civilians that recklessly take up the cyber war as a vocation perhaps do not realize the worst case scenario –for the duration of their participation, they become legitimate targets and can be prosecuted ex post facto. In the context of cyber warfare, their attacks would be almost impossible to differentiate from other cyber hostilities.
Unambiguous examples of cyber activities conducted by civilians that qualify as direct participation in hostilities, according to the Tallinn Manual, are: cyber attacks related to an armed conflict and facilitating such (e.g., detecting vulnerabilities in a targeted system), collecting data on enemy military activities through cyber means, and launching DDoS attacks (RULE 35(5) – Tallinn Manual).
Practicalities:
A Civilian Who Provides Maintenance or Technical Support for a Person Engaged in Cyber Hostilities
Such an act would most likely not meet the threshold of direct participation in hostilities.
A Civilian Programmer Who Writes a Malware Code, but Does Not Personally Execute It
The ICRC Guidance apparently suggests that a person who devises a mechanism for infliction of destruction and is not engaged in the process beyond the construction part is not participating directly in hostilities:
[…] individual conduct that merely builds up or maintains the capacity of a party to harm its adversary . . . is excluded from the concept of direct participation in hostilities . . . . [Examples of non-DPH] include scientific research and design, as well as production and transport of weapons and equipment." (Melzer, 2009, p. 57)
The IGE, however, is divided whether this would meet the threshold if the civilian programmer havs enough information to know that his creation will be used for military cyber attacks.
Legitimate Cyber Targets
As far as who may lawfully be targeted, legitimate targets are combatants, members of organized armed groups, levée en masse, and civilians directly participating in hostilities, whereas regular civilians, medical and religious members and hors de combat individuals (wounded, sick, captured, and surrendered) must be spared and protected. When in doubt, any person must be presumed to be a civilian.
RULE 34 – Persons as Lawful Objects of Attack
The following persons may be made the object of cyber attacks:
a. members of the armed forces;
b. members of organized armed groups;
c. civilians taking a direct part in hostilities; and
d. in an international armed conflict, participants in a levee en masse.
Conclusion
The overall dependence on information technology for the conduct of warfare is growing drastically and in proportion grows the necessity of applying existent norms, such as jus in bello, to the newly formed institute of cyber warfare. Documents such as the Tallinn Manual are a step in the right direction. Some scholars support the idea for a multilateral treaty that will regulate whether the means and methods used in cyber hostilities are compatible with the extant IHL norms. Regardless of the official form, the focus should be placed on the protection of civilians and critical national infrastructure, not the great military superiority that new cyber armaments can offer. Any other course might carry serious consequences for all of humanity.
Reference List
Clayton, M. (2014). Massive cyberattacks slam official sites in Russia, Ukraine. Retrieved on 07/04/2014 from http://www.csmonitor.com/World/Security-Watch/Cyber-Conflict-Monitor/2014/0318/Massive-cyberattacks-slam-official-sites-in-Russia-Ukraine
DeLuca. C. D. (2013). The Need for International Laws of War to Include Cyber Attacks Involving State and Non-State Actors. Retrieved on 02/07/2013 from http://digitalcommons.pace.edu/pilronline/34/
Dörmann, K. (2004). The applicability of the additional protocols to computer network attacks: an ICRC approach. In Bystrom, K. (Ed.), International Expert Conference on computer network attacks and the applicability of international humanitarian law: Proceeding of the Confrence. Stockholm: National Defence College.
Franceschi-Bicchierai, L. (2013). Expert: Stuxnet Virus Infected Russian Nuclear Plant. Retrieved on 07/04/2014 from http://mashable.com/2013/11/12/stuxnet-russian-nuclear-plant/
Graham, D. (2010). Cyber threats and the law of war. Journal of National Security Law and Policy, 4, 87-104.
Hague Convention 1907. Convention (IV) respecting the Laws and Customs of War on Land and its annex: Regulations concerning the Laws and Customs of War on Land. The Hague, 18 October 1907. Retrieved on 07/04/2014 from http://www.icrc.org/applic/ihl/ihl.nsf/INTRO/195
Hampson, F. (2011). Military Necessity. Retrieved on 07/04/2014 from http://www.crimesofwar.org/a-z-guide/military-necessity/
Hathaway, O., Crootof, R., Levitz, P., Nix, H., Nowlan, A., Perdue, W., Spiegel, J. (2012). The Law of Cyber-Attack. California Law Review, 100 (4), 817-886.
Heneghan, T. (2011). NSA Virus "Stuxnet" Hacked Fukushima Before HAARP-Caused Earthquake. Retrieved on 07/04/2014 from http://humansarefree.com/2011/03/nsa-virus-stuxnet-hacked-fukushima.html
International Committee of the Red Cross (ICRC) (2008). How is the Term "Armed Conflict" Defined in International Humanitarian Law? Retrieved on 07/04/2013 from http://www.icrc.org/eng/assets/files/other/opinion-paper-armed-conflict.pdf#page=3&zoom=auto,0,822
ICRC (1977). Protocol Additional to the Geneva Conventions of 12 August 1949, and relating to the Protection of Victims of International Armed Conflicts (Protocol I). Retrieved on 17/02/2013 from http://www.icrc.org/IHL.nsf/FULL/470
ICRC (1977). Protocol Additional to the Geneva Conventions of 12 August 1949, and relating to the Protection of Victims of Non-International Armed Conflicts (Protocol II). Retrieved on 17/02/2013 from http://www.icrc.org/ihl.nsf/full/475?opendocument
International Court of Justice (1996). The legality of the threat or use of nuclear weapons. Retrieved from http://www.icjcij.org/docket/index.php?sum=498&code=unan&p1=3&p2=4&case=95&k=e1&p3=5
International Criminal Court (2002) Elements of Crimes. Retrieved on 07/04/2014 from http://www1.umn.edu/humanrts/instree/iccelementsofcrimes.html
Johnson, R. (2012). 'I Count The Bodies And Watch The Funerals' — A Drone Pilot Speaks Out. Retrieved on 07/04/2014 from http://www.businessinsider.com/a-drone-bomber-pilot-speaks-out-for-the-first-time-on-what-his-job-is-really-like-2012-6
Kanuck, S. (2010). Sovereign Discourse on Cyber Conflict Under International Law. Retrieved on 07/04/2014 from https://www.law.upenn.edu/live/files/1345-sean-kanuck-reading-keynote
Kelly, M. (2013). Associated Press Twitter account hacked, tweet about White House attack 'untrue'. Retrieved on 07/04/2014 from http://venturebeat.com/2013/04/23/ap-twitter-hacked/
Kodar, E. (2010). Applying The Law of Armed Conflict to Cyber Attacks: From The Martens Clause to Additional Protocol I. Retrieved on 02/07/2013 from http://www.ksk.edu.ee/wp-content/uploads/2012/12/KVUOA_Toimetised_15_5_Kodar.pdf
Korns, S. and Kastenberg, E. (2009). Georgia's Cyber Left Hook. Retrieved on 07/04/2014 from http://www.army.mil/article/19351/Georgia__039_s_Cyber_Left_Hook/
Melzer, N. (2009). Direct Participation in Hostilities. Retrieved on 07/04/2014 from http://www.icrc.org/eng/assets/files/other/icrc-002-0990.pdf
Melzer, N. (2011). Cyberwarfare and International Law. Retrieved on 02/07/2013 from http://www.unidir.org/files/publications/pdfs/cyberwarfare-and-international-law-382.pdf
O'Donnell, B. T. & Kraska, J. C. (2003). Humanitarian Law: Developing International Rules for the Digital Battlefield. Journal of Conflict and Security Law, 8(1), 133–55.
Ophardt, J. A. (2010). Cyber Warfare and the Crime of Aggression: the Need for Individual Accountability on Tomorrow's Battlefield, Duke L. & Tech. Rev, 003.
Prescott, J. M. (2012). Direct Participation in Cyber Hostilities: Terms of Reference for Like-Minded States? Retrieved on 07/04/2014 from http://www.ccdcoe.org/publications/2012proceedings/4_3_Prescott_DirectParticipationInCyberHostilities.pdf
Rowe, N.C. (2013). Cyber Perfidy. Retrieved on 07/04/2014 from http://faculty.nps.edu/ncrowe/cyberperfidy.htm
RT (2013). Stuxnet goes out of control: Chevron infected by anti-Iranian virus, others could be next. Retrieved on 07/04/2014 from http://rt.com/usa/stuxnet-chevron-cyber-virus-348/
Schmitt, M. (2011). Cyber operations and the jus ad bellum revisited. Villanova Law Review, 56, 569-606.
Schmitt, M. (2012). "Attack" as a Term of Art in International Law: The Cyber Operations Context. Retrieved on 07/04/2014 from http://www.ccdcoe.org/publications/2012proceedings/5_2_Schmitt_AttackAsATermOfArt.pdf
Shackelford, S. J. (2009). From Nuclear War to Net War: Analogizing Cyber Attacks in International Law. Retrieved on 02/07/2013 from http://papers.ssrn.com/sol3/papers.cfm?abstract_id=1396375
The International Group of Experts at the Invitation of The NATO Cooperative Cyber Defence Centre of Excellence (2012). The Tallinn Manual on the International Law Applicable to Cyber Warfare. Retrieve on 17/02/2013 from http://www.ccdcoe.org/249.html
United Nations (1945). United Nations Charter. Retrieved from http://www.un.org/en/documents/charter/
Wortham, A. (2012). Should Cyber Exploitation Ever Constitute a Demonstration of Hostile Intent That May Violate UN Charter Provisions Prohibiting the Threat or Use of Force? Federal Communications Law Journal, 64(3), 644-650.
Photos:
- The image used in "Visual Illustration of How Ar. 51 (4) of AP I Apply to Cyber Attack" Diagram is provided by the U.S. Army for Fotopedia http://www.fotopedia.com/items/flickr-8008867397
- Pacemaker images used in Example of Cyber Perfidy Diagram are provided by Steven Fruitsmaak for Wikipedia, and Wikipedia Commons







