IoT: Hacking a Smart Bulb with Bluetooth - Introduction
We will be learning how to hack a smart bulb using Bluetooth. Since the topic is vast and lengthy, I have decided to split it into two parts. In the first part, we will learn the basics and theory on Bluetooth, and in the second part, we will see the actual exploitation.
Let's start.

What should you learn next?
Our Aim – What we wish to do?
We have a mobile application which can be used for interacting with the smart bulb. However, we will be controlling the smart bulb using Bluetooth CSR v4.0 dongle (henceforth dongle) remotely. (CSR v4.0 dongle is the tool which can be used for interacting and communicating with the bulb). More on dongle later. In simple words - we will be controlling the bulb even though we are not the owner of it.
Theory on Bluetooth – We all know what Bluetooth is and we have been using it for a long time. What you know or may not know is – there are two types of Bluetooth Communication.
- Classic Bluetooth, i.e., Bluetooth 2.0
- Bluetooth Low energy, i.e., BLE 4.0
Classic Bluetooth and its specification were introduced as part of the Bluetooth 1.0. These specifications are handled by SIG (Bluetooth Special Interest Group) and all Bluetooth manufacturers, and service providers are a member of SIG.
BLE (Bluetooth Low Energy) is a wireless PAN. It was created by Nokia under the name of Wibree in 2006 and merged into Bluetooth standard in 2010. BLE has been designed especially for devices running on low power. Since IoT devices run on low power, they use BLE for communication. There are plenty of wireless protocols for IoT, but BLE is the simplest to design and implement.
BLE OS Support – BLE is supported and available for almost all the platforms. Major ones have been listed below –
- Mobile – Android, iOS, Windows, etc.
- Desktop/Laptop – Windows, Linux, and macOS.
Operating Frequency – 2.4 – 2.48 GHz ISM band.
BLE Stack – This is how a BLE Stack looks like

(Image Source - https://devzone.nordicsemi.com/tutorials/17/)
It consists of 3 layers –
- Host Layer
- Controller Layer
- Host Controller Interface(HCI) – Bounding both the layers
Thus, both the layers are bounded via HCI layer.
For this tutorial, we do not have to understand the functionalities of all the layers. We will go through what is needed (GATT, GAP, and ATT). Let's understand their functionalities –
- GAP – Stands for Generic Access Profile. It is responsible for the discovery aspect of BLE device. In simple word, your device should be discoverable to other devices and mobile application so we can connect to it. GAP does the work of making it discoverable.
- ATT – Stands for Attribute Protocol. In simple words – If we want to talk to Web Server, we use HTTP Protocol. Thus, HTTP is responsible for communication between Browser and Web Server. Similarly, in this case, how a mobile application and bulb should talk to each other is managed by ATT.
-
GATT – Stands for Generic Attribute Profile. In simple words – we use Browser to talk to Web Server. Thus, Browser is responsible for the entire exchange of user data. The Same role is played by GATT. It is responsible for exchanging data and profile information between mobile app and bulb. GATT comes into play once a connection is established between two devices. GATT makes use of services and characteristics.
To understand what they are let's have a look at the diagram shown below –
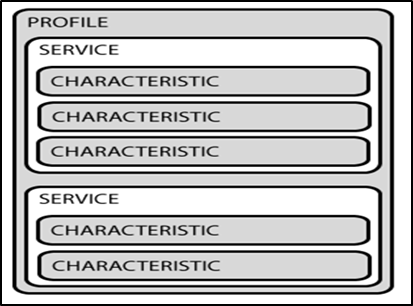
Let's understand the diagram –
Within Profile is Service and within Service are various Characteristics.
Thus,
- Profile - Collection of service.
- Service – Collection of characteristics
- Characteristics – Single Datapoint.
I have purposely not written the definition. Let's take this simple example –
Suppose you are a security consultant and you can do web and mobile pentesting. Listing your skills in the form shown below –
-
Web Application Pentesting
- Java Application Pentesting
- .Net application Pentesting
- PHP application Pentesting
-
Mobile Application Pentesting
- Android Application Pentesting
- iOS Application Pentesting
- Windows Application Pentesting
In the above example –
- Profile is – Security Consultant
- Service is – Web application Pentesting and Mobile Application Pentesting.
- Characteristics are – Java Application Pentesting, Net application Pentesting, Android application Pentesting, etc.
I hope the concept of Profile, Service, and Characteristic is clear now.
In BLE – There does not exist anything called Profile. It is just a collection of service, and you will not come across profile anytime while pentesting any BLE device.
List of services offered by Bluetooth SIG can be obtained here - https://www.bluetooth.com/specifications/gatt/services. If you open the link, you can see a list of services offered by Bluetooth SIG. All these services are predefined services offered by Bluetooth SIG and do have a look at "Assigned Number" column. Each service has some number assigned, and all the services start from "0x18**" series where 0x18 always remains constant.
Similarly, list of characteristics offered by Bluetooth SIG can be obtained here - https://www.bluetooth.com/specifications/gatt/characteristics. If you open the link, you will have a list of characteristics offered by Bluetooth SIG. All these characteristics are predefined and offered by Bluetooth SIG and do have a look at "Assigned Number" column. Each characteristic has some number assigned, and all the characteristics start from "0x2A**" series where 0x2A always remains constant.
Tools - There are many tools available for replaying the Bluetooth packets. Tools such as Ubertooth, Bluefruit, and Bluetooth CSR v4.0 dongle can be used. Ubertooth is used widely, but the cost of Ubertooth is around 120$. Cheapest tool available to us is a dongle, and it comes around 7-8$. In our blog, we will be using the dongle as discussed.
About Bluetooth CSR v4.0 Dongle – First, have a look at the dongle shown below –

As shown above, it is like a USB dongle which can be directly plugged into the laptop and is ready to use.
Setup – We have a smart bulb and an Android application. The bulb can be controlled using a mobile application. Thus, we can interact with the bulb using an Android Application.
Steps
for Exploitation –
-
Intercept the communication between the bulb and mobile device. The dongle is not capable of intercepting the communication between mobile and bulb, but we can intercept the communication on a mobile device using Bluetooth HCI Snoop log feature on the phone. It is present in developer options tab as shown –

Once it is enabled, it captures all the Bluetooth traffic of the phone.
- Transfer the Bluetooth log files to the computer.
- Analyze the traffic.
- Replay the packets using Bluetooth CSR.
Procedure – I am using Bluetooth CSR v4.0. So, I will be intercepting all the communication between the bulb and the mobile application using "Bluetooth HCI snoop log" feature present in the phone and transfer the log file to my computer for analyzing it using Wireshark. After analyzing the packets, replay attack will be made using CSR.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
That is it for this post guys. In the next post, we will be learning how to exploit a BLE connection using CSR.






