Importance of security in mobile platforms
Introduction
In this period, security firms are publishing detailed reports on analysis conducted on principal cyber threats detected in 2012, the results proposed present a landscape dominated by explosion of menaces, especially for mobile and social media users.
Mobile technology has grown more than any other in the last few years and the IT industry, to respond customer's demands, has designed an impressive number of solutions and services specific for mobile platforms. Due the growing trend, many actors have been attracted by the possibility to exploit the mobile solutions for various purposes; let's think, for example, to cyber criminals or state-sponsored hackers that have started to research possible attack schemes against mobile platforms.
Another factor that must be considered when analyzing the rise of cyber threats against mobile platforms is the lack of awareness of users on the risks related to an improper use of mobile devices, in majority of case users don't apply mechanisms of defense to their mobiles, and often they totally ignore them; a customer's habit could cause serious damage (e.g. jailbreaking or downloading from third partyapp-store).
Mobiles are considered privileged targets for cyber criminals; according to the IDC, they are surpassing PCs as preferred devices used to access the Internet and the number of mobile users will increase by 91 million over the next four years.
Mobile devices accompany us in our movements, manage our communications and their use allows us the fruition of various services such as banking, payments and social networking; this consideration raises a series of questions under security perspective:
-
Is the wealth of information managed by mobile really secure?
-
Does the user know cyber threats and how to mitigate them?
-
Are the communication channels secure?
-
Does the user know the behavior of the app installed on the mobile and how they managed their data?
-
Mobile and workplace, how to combine business needs and private use of the devices?
This article provides the answers to the questions introduced.
Security in current mobile landscape
WebSense security firm has recently published an interesting analysis, the 2013 Threat Report, on principal cyber threats based on data collected by the Websense ThreatSeeker Network; the study confirmed the growth of sophisticated menaces that mainly targets mobile platforms and social media.
As announced, mobile security is a primary concerns for the IT sector; the rapid diffusion of malicious apps and wrong user's habits (e.g. jailbreaking and absence of defense systems) are the main sources of problems.
WebSense revealed that mobile users spend majority of time in Internet browsing (24,81 Minutes per Day) and in Social Networking (17,49 Minutes per Day), but also playing music and gaming have a meaningful relevance; this data is just statistics for security experts to give precious indications of which can be the channel that cyber criminals could explore to attack mobile platforms. If users who play games with their phone are at high risk for cyber crime, any attacker will exploit this attitude for hit them.
[caption id="" align="alignnone" width="584"]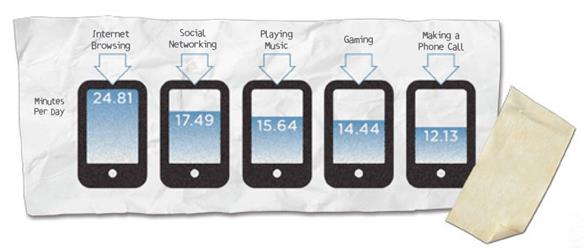 Figure 1 - WebSense Report - Mobile use[/caption]
Figure 1 - WebSense Report - Mobile use[/caption]
The following statements extracted from the report synthesizes the situation observed by WebSense:
"Legitimate apps were also a cause for concern; many proved less secure than expected. Consider a study by Philipps University and Leibniz University in Germany involving 13,500 free apps downloaded from Google Play. Researchers found that 8 percent of these apps were vulnerable to man-in-the-middle attacks, and approximately 40 percent enabled the researchers to "capture credentials for American Express, Diners Club, PayPal, bank accounts, Facebook, Twitter, Google, Yahoo, Microsoft Live ID, Box, WordPress, remote control servers, arbitrary email accounts, and IBM Sametime, among others.""
The document reported that malicious apps mainly need three permission requirements that are worth pointing out:
-
82% of malicious apps send, receive, read or write SMS messages. Very few legitimate apps require any SMS permissions.
-
12.5% of malicious apps required RECEIVE_WAP_PUSH permission, something legitimate apps rarely require.
-
10% of malicious apps asked for permission to install other apps—another rarity among legitimate apps.
Also, security company PandaLabs published their 2012 annual report on cyber threats. Last year, the company observed a sensible increase of attacks against mobile platforms, especially for Android systems. Android's popularity continues to grow and an increased amount of malware is targeting it; in January, Google had to remove several malicious apps from its Android Market; typically, cyber criminals repackage most popular games such as Angry Birds or Cut The Rope with malware and once published on the app store users downloaded the infected apps unaware that they were also installing a malware. Google declared that it had managed to reduce malicious app downloads by 40 percent.
We completed the review of the analysis of the major security companies with data provided by security firm F-Secure that has always been at the forefront of the study of computer threats. According to Mikko Hypponen, the mobile threat landscape continues to be focused on two platforms, Android, which accounted for 79% of all new malware variants identified in 2012 and Symbian, with 19% of the remaining new variants.
[caption id="" align="alignnone" width="425"]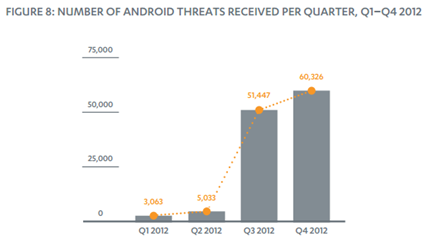 Figure 2 - Number of android threats received Per Quarter 2012 (F-Secure)[/caption]
Figure 2 - Number of android threats received Per Quarter 2012 (F-Secure)[/caption]
[caption id="" align="alignnone" width="295"]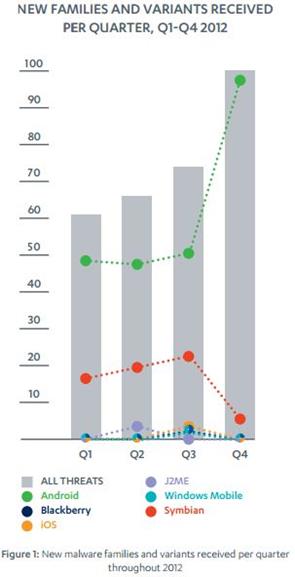 Figure 3 - F-Secure New malware families and variants received in 2012[/caption]
Figure 3 - F-Secure New malware families and variants received in 2012[/caption]
In Q2 2012, China officially surpassed the United States as the world's largest market for smartphone consumers. Android handsets accounted for 81% of that market and it's therefore probably not surprising that many of the new malware families detected last year were targeted specifically to Android users in mainland China.
[caption id="" align="alignnone" width="605"]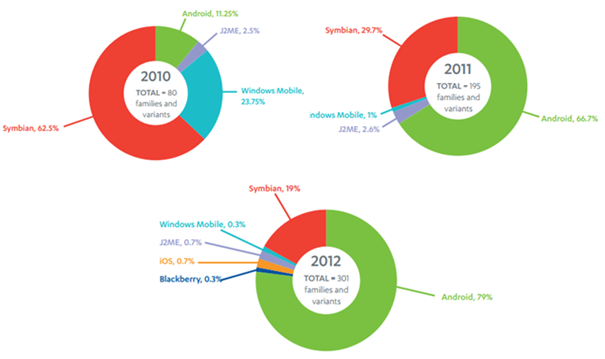 Figure 4 - F- Secure threat families and variants by PLatform,2010–2012[/caption]
Figure 4 - F- Secure threat families and variants by PLatform,2010–2012[/caption]
"Given its dominance, the Android platform has naturally become the main target for active malware development, with a total of 238 new, unique variants found on the platform during that period. The majority of these malware are distributed as trojanized apps, in which a legitimate program has been engineered to include a malicious component. Most of the new variants found are categorized as trojans or monitoring-tools, which are able to either compromise the user's data or track the user's movements and activities."
Mobile cyber threats, malware, risky apps and monitor tools
The principal statistics reveal that the most diffused OS for mobile today is Android, the system designed by Google is the fastest growing platform and due to this reason it has become most targeted by cyber criminals and hackers.
As said before, the F-secure firm revealed that Android OS accounted for 79% of all malware in 2012, up from 66.7% in 2011 and the 11.25% observed in 2010, meanwhile despite is Apple's IOS second world's most diffused OS it is one of the least compromised, with 0.7% of malware on its platform.
F-Secure highlighted an authentic explosion of Android's malware in Q4 2012, the period in fact accounted for a full 96% of attacks, the remaining malicious code hit only Symbian OS; the data appears not correlated to the OS market share.
[caption id="" align="alignnone" width="477"]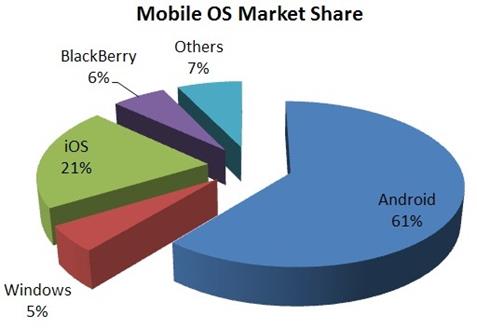 Figure 5 - Mobile OS Market Share[/caption]
Figure 5 - Mobile OS Market Share[/caption]
Sean Sullivan, security advisor at F-Secure Labs declared:
"Malware in general has a parasitic relationship with its host," "As old Symbian handsets continue to be replaced by those with other operating systems, especially Android, Symbian malware dies off and will probably go extinct in 2013."
Researchers at F-Secure found that 66% of malware detected were trojans, and the Android version most compromised are the ones before Jelly Bean (ver. 4.2); this version in fact was known for the introduction of security features that have reduced the infection rate. The study demonstrated that malware has become more sophisticated and financially motivated malicious code is increased in sensible way due the diffusion of more transactional services.
[caption id="" align="alignnone" width="373"]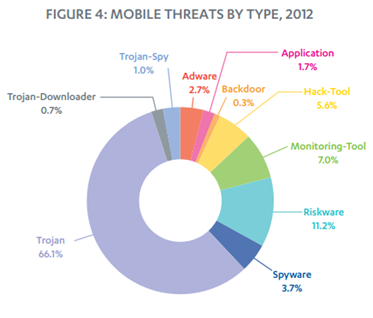 Figure 6 - Mobile Threats by Type, 2012 (F-Secure)[/caption]
Figure 6 - Mobile Threats by Type, 2012 (F-Secure)[/caption]
Another component of great interest are the applications executed on mobile devices by users. In the last few months, the number of categories of apps have increased; these applications are used at work and during leisure time and are characterized by technologic architecture, final use and configurations, all those components concur to enlarge surface of exposure to cyber threats.
McAfee has conducted an interesting analysis on "sophisticated and complex risky apps containing multi-faceted scams, black market crimes, drive-by downloads and near-field communication threats", identifying new methods used by attackers to steal sensitive and personal information and realize complex cyber frauds.
[caption id="" align="alignnone" width="523"]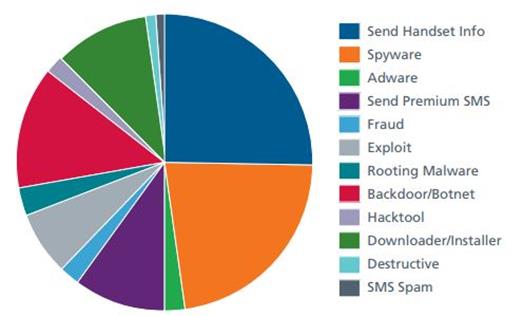 Figure 7 - Mobile Malware Cyber Threat - McAfee[/caption]
Figure 7 - Mobile Malware Cyber Threat - McAfee[/caption]
"Cybercriminals are exhibiting greater levels of determination and sophistication leading to more destructive, multi-faceted hacks that are harder to spot, and thus warrant a greater degree of security and vigilance. Our goal in releasing this report is to help consumers understand the risks they face and learn ways they can stay safe and compute with confidence on all of their devices." said Luis Blando, vice president of mobile product development at McAfee.
Following the key findings proposed by the McAfee study:
-
Unlike the email and website-based infections typical of PCs, mobile malware is distributed primarily through infected apps today.
-
3 percent of malware-infected apps in our overall mobile app zoo came from the Google Play store.
-
Within the fairly conservative McAfee user community, 75 percent of malware-infected apps were downloaded from Google Play.
-
Crooked app stores use black hat search engine optimization (SEO).
-
Based on the experience of McAfee users, typical consumers have at least a 1 in 6 chance of downloading apps that include malware or suspicious URLs.
-
Almost 1/4 of the risky apps that contain malware also contain suspicious URLs.
-
40 percent of malware families misbehave in more than one way, showing the sophistication and determination of the criminals.23 percent of mobile spyware joins a botnet or opens a backdoor, increasing the risk of data loss or device abuse.
Risky apps are the primary channel used by cybercriminals to spread malicious code, hacker tools and links to compromised websites. Using risky apps, cyber criminals are able to compromise a user's mobile device, installing malicious code designed to steal sensitive information or implement any other fraud scheme.
As we will see shortly, phishing on mobile is increasing in a meaningful way due the diffusion of risky apps that contain infected URLs lead to sites with drive-by downloads and around 25% of the risky apps that contain malware also contain suspicious URLs.
"Most malware on a web page still needs to be "accepted" by the user, giving consumers the chance to back out. However, we saw our first mobile drive-by downloads in 2012 and expect more in 2013."
The study by McAfee states that the average user has a one in six chance of downloading a risky app, nearly 25 percent of the risky apps that contain malware also contain suspicious URLs, and 40 percent of malware families misbehave in more than one way, various are the cases in which the infected apps were housed directly in the Google Play.
The evolution of mobile threats is, in many aspects, similar to desktop environments; in the underground market it is possible to acquire various exploits that allow to criminals to recruit machines for botnet architectures or to organize prolific scam, typically premium SMS's and click fraud. Fortunately, these exploit kits are not popular, but their use is increasing in concerning way. The casuistry is wide, from spam distribution to the sale of malicious code for data theft or for stealing of banking credentials, many agents present a multi-feature profile that allows the implementation of these features in a single flexible malware.
The mobile malware black market is still in an embryonic stage because cybercriminals mostly use to them to directly attack mobile platforms instead to sell exploit toolkits and mobile malware.
According Group-IB security, there are meaningful differences between mobile malware for cybercrime and for cyber warfare, key properties for cybercrime are:
-
Using of well-known brands, including graphical design of famous applications or legal entities (financial institutions, e-commerce, stock/e-trading applications, applications for social networking and etc.);
-
the need to send an SMS or dialphone calls to other numbers (sometimes it is doing silently after mobile malware will be installed on the system);
-
65% of installations – only on "jailbroken" devices, 20% – through low verification of applications, 15% – through wireless channels (NFC, WPAN networks).
The market oriented to cyber warfare is focused on the offer of malware for cyber espionage and intelligence. The means of malware planting and its functional are quite similar to that one used by cybercriminals.
The key properties of mobile malware for cyber warfare are:
-
The payload is targeted on information stealing including contact lists, text messages, calls history, information about compromised device (IMEI, Device IDs, external IP and etc.);
-
Some of the specific mobile malware is targeted on mobile calls recordings including Skype conversations.
-
Additionally, modern smartphones are used for cyber espionage with special tools, used as traditional penetration testing tools.
Mobile environments provide a new opportunities for the hacker; cybercriminals use them for monetization through special underground partnership programs, the principal idea of which is to distribute malicious code on the huge range of smartphones based on popular OS's through landing pages or mobile traffic (iOS, Windows Mobile, Google Android and etc.), and then to ask for paid SMS or it does it silently on specially crafted paid number from grey SMS billings providers in different countries.
Mobile phishing
As described previously, emails are considerable as a primary vector for cyber-attacks against mobile devices, principal security firms revealed that phishing activities in the last few years have increased exponentially, targeting every sector from industry to government agencies. RSA's October Online Fraud Report 2012 described an impressive increase in phishing attacks, up 19% over the second half of 2011. The total loss for various organizations sums up to $2.1 billion over the last 18 months; these are extraordinary figures that gives an idea of the amplitude of phenomena.
2013 has started with an apparent reversal of the trend that is actually symptomatic of a dangerous phenomenon, to an apparent slowing of phishing activities on desktop PCs is paid with an increase of offensives that are targeting mobile platforms.
An increasing number of web sites are expressly designed to circumvent mobile users, targeting e-banking and e-commerce services, Trend Micro security firm observed that in 2012, 75% of mobile phishing URLs were rogue versions of popular financial and banking sites, meanwhile only a small percentages (4%) were related to sites try to trick online shoppers and social network users (2%).
The methods of attacks are unchanged with respect normal phishing. Users are misled and hijacked on spoofed versions of legitimate sites to trick them into disclosing sensitive information such as banking credentials, account details and other personal information that could be used in successive APT attacks. Most targeted users are PayPal customers followed by other financial institutions clients such as Absa Internet Banking, Barclays and Wells Fargo.
[caption id="" align="alignnone" width="355"]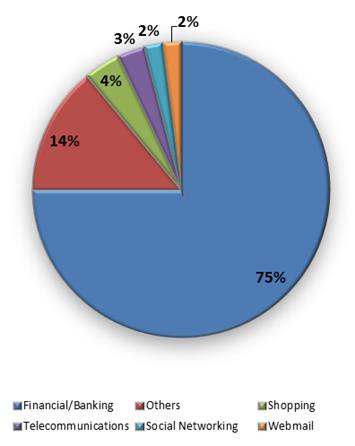 Figure 8 - Services hit by Mobile Phishing[/caption]
Figure 8 - Services hit by Mobile Phishing[/caption]
[caption id="" align="alignnone" width="395"] Figure 9 - Mobile Phishing Sites (Trend Micro)[/caption]
Figure 9 - Mobile Phishing Sites (Trend Micro)[/caption]
Cybercrime, governments … surveillance and cyber espionage exploiting mobile
The rapid diffusion of mobile devices, especially in the workplace, has transformed them in a primary target for cybercrime and government cyber espionage. Authoritarian regimes and democratic governments are investing to monitor mobile communication and to exploit the most popular platforms.
Recent events such as the cyber espionage campaign «Red October» discovered by Kaspersky Lab team have demonstrated the elevated interest on mobile devices.
The operation Red October was conducted to acquire sensible information from diplomatic, governmental and scientific research organizations in many countries, mostly of them of Eastern Europe, former USSR members and countries in Central Asia.
Differently from other cyber espionage campaigns discovered in the past, Red October has targeted various devices such as enterprise network equipment and mobile devices (Windows Mobile, iPhone, Nokia).
The campaign is not an isolated event, as mentioned by WikiLeaks in the Spyfiles relation, many private companies provide products for monitoring and espionage such as architectures for large-scale monitoring of Internet and spyware and other kinds of tools for targeted and invasive surveillance. The surveillance business is a billionaire affair that is sustained by a growing demand of governments and private businesses.
Another example of the high interest manifested by governments in the exploiting of mobile platforms has been provided by US Defense Intelligence Agency that published on 12th of December 2012 a solicitation (TES2013)titled "Technical Exploitation Support", the request is related to support for developing of technology aimed at exploiting digital media and hardware, with specific references for exploitation of mobile devices.
[caption id="" align="alignnone" width="443"] Figure 10 - US Defense Intelligence Agency solicitation[/caption]
Figure 10 - US Defense Intelligence Agency solicitation[/caption]
The solicitation aimed to the definition of new exploit methods not generally available on the commercial market and look with great interest to the mobile sector. The U.S. government is trying to develop new capabilities to acquire information of interest from mobile devices, such as cell phones and tablets on account of their extraordinary rise in the market.
Mobile devices are a mine of information to spy on individuals, communications, social habits, movements; all is traceable and U.S. wants to do it… and they are not the only ones.
Conclusion
Rapid diffusion of mobiles are alimenting the interest of ill-intentioned, cyber criminals and state-sponsored hackers are in fact intensifying their attacks against mobile platforms. Security in mobile devices must be considered a fundamental requirement. Mobile devices represent a technological appendix to our persons, and due this reason, it needs a high level of protection.
The correct approach must follow parallel paths; on the manufacturer's side, it is crucial that the mobile and application installed are designed considering all the possible cyber threats and evaluating with care the surface of exposure. On the other side, a user must be aware of the potentiality of their devices and the risks connected to cyber-attacks.
The year 2013 presents itself full of challenges in mobile security, Android users will have to face a growing number of cyber threats of increasing complexity. The principal cyber threats will be originated by cyber-crooks wanting to steal sensitive information and intellectual property, but also cyber-espionage activities of governments and private actors have to be considered.
Among the main threats that will grow exponentially there are malware for scam purpose and phishing activities.
The figure presented portend an explosion of offensives against mobile platforms and its services, in particular for payment and social networking services. It is important to identify principal cyber threats and implement all necessary countermeasures to their containment, but majority of mobile devices are managed by common people that total ignore security issues so it is desirable that specific awareness campaigns be conducted by law enforcement and private businesses. The security concept is materialized in the knowledge of any individual!
Keep update installed apps, do not download software from third part app stores, avoid jailbreaking operations and of course, avoid clicking on links contained in unsolicited emails.
References
http://www.websense.com/content/websense-2013-threat-report.aspx
http://press.pandasecurity.com/wp-content/uploads/2013/02/PandaLabs-Annual-Report-2012.pdf
http://www.f-secure.com/static/doc/labs_global/Research/Threat_Report_H2_2012.pdf
http://www.f-secure.com/static/doc/labs_global/Research/Threat_Report_H2_2012.pdf
http://www.mcafee.com/us/resources/reports/rp-mobile-security-consumer-trends.pdf
http://www.f-secure.com/static/doc/labs_global/Research/Mobile%20Threat%20Report%20Q4%202012.pdf

11 courses, 8+ hours of training




