Goodbye DIACAP, Hello DIARMF
When C&A becomes A&A, will you be ready?
Every few months, an elite group of DoD security experts, IT managers, and senior leadership gather to chart the future course for how Information Assurance will be conducted within the Defense Department. Very soon, this group will introduce sweeping changes to the Certification and Accreditation process, to the extent that personnel roles, job titles, and even the moniker C&A itself will change, evolving into new nomenclature and a new era for the Information Assurance community of practice within the DoD. After implementation, the use of DIACAP Certification and Accreditation processes will cease and DIARMF Assessment and Authorization will become the 'new normal' for information technology professionals and risk managers throughout the Defense Department.
The changes are an evolution of existing practices, but also a profound step forward that advances the practice of Information Assurance at DoD and reflects the growing importance of IA within the federal government. The shift also hails the emergence of cyber defense as an influential driver of Information Assurance policies and procedures government wide. Translation: IA is no longer just about checking off boxes for FISMA compliance. The increased threat landscape and looming budget scarcities demand a mature, efficient, and effective process which, when implemented correctly, DIARMF can deliver. The secret to success lies in being prepared for its imminent arrival and rapid deployment, and in sharpening the holistic approach of designing and building systems with IA baked in and not bolted on.
Defense Information Assurance Risk Management Framework (DIARMF)
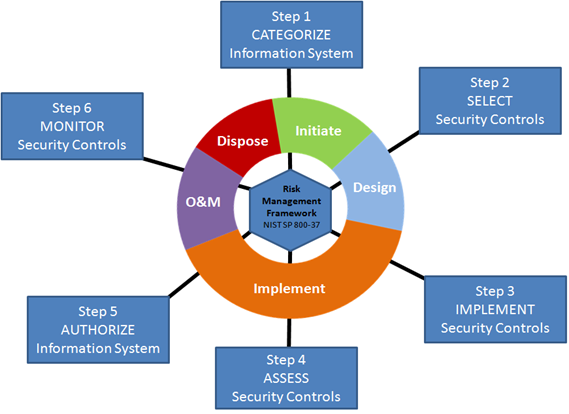
The six major steps of Risk Management Framework aligned with the five phases of a System Development Lifecycle (SDLC)
DIARMF represents DoD adoption of the NIST Risk Management Framework process, using security controls currently in practice at civilian federal agencies. The DoD implementation of RMF puts a different spin on the process however, so those familiar with civilian agency IA controls and practices will still need to adjust when undertaking a military grade Information Assurance endeavor.
The most profound change aesthetically is the process and role nomenclature. What has commonly been known for years as Certification and Accreditation (C&A) under DIACAP (and its predecessor DITSCAP) will now be called Assessment and Authorization (A&A), to better reflect alignment with corresponding steps in the Risk Management Framework process.
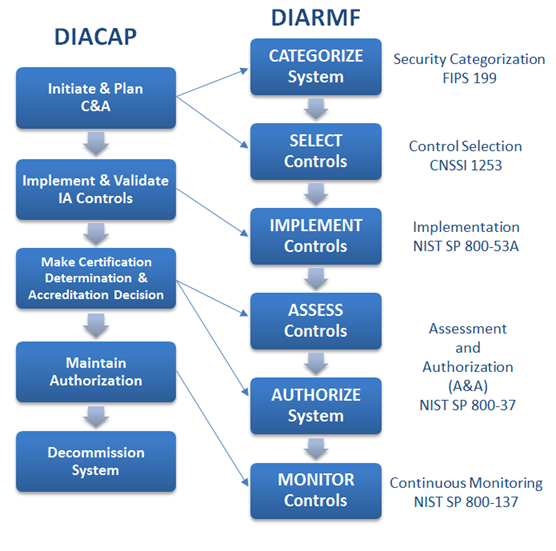
Comparison of DIACAP and DIARMF processes, with policy references
At a high level, the activities in a DIARMF A&A are the similar to those of a DIACAP C&A, with Assessment producing an endorsed checklist of compliance with selected security controls, and Authorization consisting of an acceptance (or rejection) of the residual risk outlined in the Assessment report. In detail however, there are specific activities and nuances that are unique to DIARMF, which represent the evolution and maturity of the Risk Management Framework process.
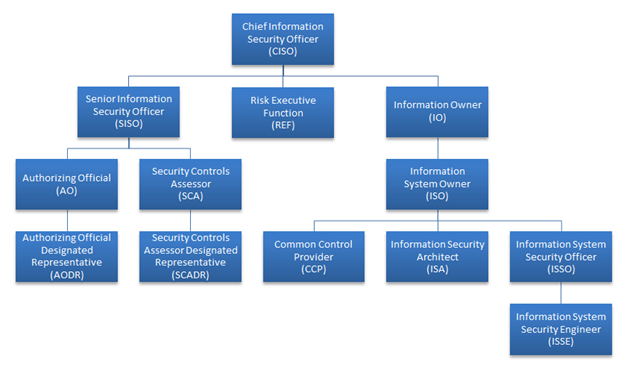
Sample DIARMF roles in a hierarchal view (estimated)
As for DIARMF roles, most changes will be designed to further convey alignment with RMF terminology, but an important new role that RMF adds to the mix is the Common Control Provider, which is part of how RMF addresses control inheritance. The CCP is someone who manages inherited controls for Authorized systems like enclave networks, server clusters, or virtualized computing environments. For example, if your system physically consists of just a few servers in rack space provided by a large DoD datacenter, then chances are resources like air/humidity controls and fire suppression are provided by the datacenter and are not part of your system, in which case those corresponding security controls will be marked up as 'Inherited' on your Assessment, pointing to the controls of the already Authorized datacenter. Inheritance is complicated affair however; some controls are inheritable and some are not, depending on the shakeout of control selection. Furthermore, an artifact requirement exists (in the form of a system specific Service Level Agreement) for the control inheritance to be considered valid during Assessment. Also, the possibility exists that the loss of Authorization on the host datacenter would cascade down to a loss of Authorization for the hosted system, creating an important dependency that all stakeholders in the system and its project/program should be aware of.
The most substantial difference between NIST RMF and DoD enhanced DIARMF lies in the area of security control selection. To address the diverse and specialized nature of DoD systems, DIARMF employs a significantly more complex formula for selection criteria. Where NIST RMF categorizes systems using a one-dimensional scale of High/Moderate/Low based on mission impact of the system, DIARMF starts with a matrix of High/Moderate/Low impact splayed against the Confidentiality/Integrity/Availability of the data, then applies overlays for specialized characteristics like medical, industrial control, or weapons systems. An overlay can add or even subtract controls from the selection, and can also modify the variables (password length, key size, etc.) within the control statement itself. This shakes out to easily over a hundred different possible control sets that can be attributed to systems. DoD intends to tame this to a small degree by filtering out some unlikely combinations and by issuing a control selection calculator tool, but the complexity of control selection will nonetheless be a memorable feature of the DIARMF process.
When contrasting DIARMF to its predecessor DIACAP, the obvious standout is the security controls themselves. DIACAP practitioners will find the NIST library more substantial in quantity, yet more granular and specific within the scope of each control. For example, where DIACAP might fit an entire password policy into one control, the NIST control set in DIARMF will have a primary control for the password policy enforcement and individual control enhancements for each element (length, complexity, history, etc.) of the policy. Required control enhancements will be determined in the control selection process, and the variables within them (like the number of characters in a password length requirement or the number of unique passwords to be saved and enforced via history) will be dynamic, varying according to the impact ratings and overlays applied during the control selection process. There is actually a sub-committee at DoD dedicated solely to determining these variables and the formulas that generate them. Technical folks will find the text of NIST control descriptions and validation procedures more clear and concise, since they were written by their technical peers and contain less of the FISMA influenced legal bent often attributed to the DIACAP controls. NIST intends to revise the SP 800-53 control library every 18 months, based on threat analysis, attack trends, and other input provided by the National Security Agency, the Defense Information Security Agency, various federal and commercial CERT teams, and the newly formed US Cyber Command at DoD.
Equally profound within DIARMF is the increased requirements for Continuous Monitoring activities. Each control (and control enhancement) will be attributed with a refresh rate (daily, weekly, monthly, yearly) and requisite updates on the status of each control will be packaged into a standardized XML format and uploaded into the CyberScope system where analysis, risk management, and correlation activities will be performed on the aggregate data. The XML format will be a variant of the SCAP protocol currently in use for the Federal Desktop Core Configuration (FDCC) standard, also pioneered by NIST. CyberScope is akin to a giant federal-wide SEIM system, where high-level incident management teams can quickly pull queries or drill down into system details to add analysis on system defenses and vulnerabilities to the available intelligence on an attack. CyberScope data will also be used to track trends, make risk management decisions, and determine where help is needed to improve security posture.
It's easy to fall for the misconception that the first frame of data in Continuous Monitoring is identical to assessment, but this is a pitfall to avoid. For starters, Assessment artifacts are sent to the eMASS workflow management system, while Continuous Monitoring data is sent to the CyberScope aggregator. Assessment involves more attestation of the control with a primary focus on the goalpost of Authorization, whereas Continuous Monitoring is more akin to a raw feed of the data behind the control.
Being prepared for DIARMF is a process in itself: Risk managers and C&A practitioners can (and should) start early by reading the available policy documents now, and by reading the revised/reissued policy documents as they are released. Diligence should also be given to the local scene, as various services and major commands will be revising and re-issuing their own policies and procedures, which will contain valuable details as to how they expect the job to be done. Shortly after DIARMF is formally announced is when its implementation will begin, and folks should follow up with a training course designed to update their skills from DIACAP.
The shift within DoD from DIACAP C&A to DIARMF A&A is a profound change, and the rise of Continuous Monitoring will double the stakes in terms of cost and effort. Practitioners of the traditionally civilian agency NIST standards will be in high demand because of their knowledge of the SP 800-53 control set and SP 800-53A control validation procedures, whereas DIACAP practitioners are only an upgrade course away from being spooled up on the new controls and processes. It's impossible to understate how all Information Assurance practitioners must be prepared for the profound and swift changes that lie ahead.
-=Len
"The dogmas of the quiet past are inadequate to the stormy present. The occasion is piled high with difficulty, and we must rise with the occasion. As our case is new, so we must think anew and act anew."
Abraham Lincoln, 1862

