Fitting cyber attacks to jus ad bellum — Consequence-based approach Part II
The consequence-based duo tests
The focus of this contribution is placed on two tests which employ the consequence-based approach that, in turn, aims to categorize cyber attacks as a use/threat of force or an armed attack pursuant to UN Charter. Interestingly, such a method within the method reminds me ace little of the Russian matryoshka, where with each opening of a wooden doll the chance to snatch the final surprise is either getting bigger (while the dolls are decreasing in size) or vanishes thunderously at the end.

What should you learn next?
1. Pictet's approach
The author of the Commentary on the Geneva Conventions devised a test which relies on "scope, duration and intensity" factors in order to determine whether a use of force should be regarded as an armed attack. The evolvement of international instruments like the "Definition of aggression" resolution by U.N. General Assembly has been conducive to the application of Pictet's approach. Without providing a clear definition of armed attack, it gives examples of internationally accepted practices which are considered or bear some close resemblance to the term in question. Nonetheless, many of those pronouncements are inapplicable in the event of cyber attacks, but the test created by Jean Pictet may prove somehow fruitful (Graham, 2010).
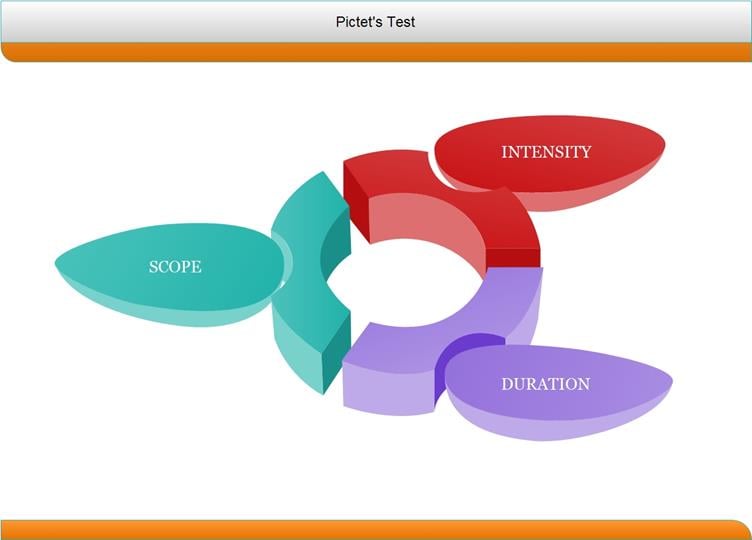
Let's put in a nutshell the constitutive parts of the test:
Scope feature stands for the breadth of the attack, which analyses the weapon from one side and the target from another. Key points of study concerning the weapon and target are accordingly the number used or attacked and their nature. The sum of these findings determines the scope of the attack (Wingfield, 1999).
Duration consists of quantitative and qualitative part and is probably the easiest component to evaluate. The quantitative one is related to either permanent or temporary effects ensuing from the attack. Consequently, if the effects are temporary, for the period they persist can be described in time values. As for the qualitative part, its purpose is to indicate for how long the attacked platform will be unavailable to the party (Wingfield, 1999).
Intensity, in the context of this test, can be presented as a spectrum. At the one side are activities that have no effect on the attacked state, and at the other side are those operations that affect 100% of the object under attack. With drawing close to the center, this "mission permissive/mission coercive" dichotomy is growing gradually in terms of complexity. At the same time, it should be noted that not always the destruction of the object leads to the worst consequences. Indeed, a continuous receiving of manipulated data. For instance, from a compromised satellite may actually be more deleterious. Thus, intensity factor which examines properly the balance of real damage caused is useful (Wingfield, 1999).
2. Schmitt's seven-factor scheme
The state practice concerning applying the notion of use of force to cyber attacks is vague and ambiguous. However, according to Michael Schmitt, one of the strongest advocates of applying the consequence theory to cyber attacks, there is a scheme of factors that may prove useful when evaluating whether a cyber attack constitutes a use of force. This approach is something like a compromise variant, preserving the status quo of the states' ability to make own assessment and choices based on them, but within the boundaries set out in the UN Charter. Schmitt claims that "the approach has generally withstood the test of time (Schmitt, 2011, p. 575). These factors are:
 Severity
Severity
Without a doubt it is the most important criterion. This factors looks at the intensity and scope of an attack. Assessment under 'severity' would take into account the number of casualties, size of the attacked zone, and the figures which reflect on the damage inflicted. The greater the total sum of these values is, the more likely is the cyber attack to be treated as an armed attack (Sklerov, 2009).
The same counts also if there is more harm inflicted on 'critical national interests'. Consequently, because physical existence is at stake and this is the most valuable need among the all human needs. Therefore, 'severe' armed attacks are banned because they endanger in the utmost degree this supreme human need (Schmitt, 1999).
"Only if a foreseeable consequence is to cause physical injury or property damage and even then, only if the severity of those foreseeable consequences resembles the consequences that are associated with armed coercion" is the situation when a cyber attacks is justified according to the former General Counsel of the CIA Daniel Silver (2002, p. 89). He infers as well that the main factor that should determine existence of a cyber attack is the severity of the damage caused.
 Immediacy
Immediacy
This factor corresponds to 'duration' from the Pictet's test and is also important because it indicates how long after the impact takes place the consequences emerge. The nature of cyber attacks frequently prepossesses in favour of swift emergence of attack effects, which decreases the chances for peaceful solution accordingly. By contrast, computer malware such as logic and time bombs raises serious concerns because they can stay dormant for a long time before being activated (Schmitt, 2011). Additionally, 'immediacy' as well engages in finding of what time is necessary for the effects to abate (Sklerov, 2009).
 Directness
Directness
This index accentuates on the harm caused and the chain of logical events that leads to the causation of a cyber attack. While the immediacy criterion keeps track on the temporal issue, the directness is more interested in assessing the line of the events that would eventually lead from the act to the results:
"If the attack was the proximate cause of the harm, it strengthens the argument that the cyberattack was an armed attack. If the harm was caused in full or in part by other parallel attacks, the weaker argument that the cyberattack was an armed attack." (Sklerov, 2009, p. 69)
For example, an economic embargo may produce its final consequences much later than it has started. On the other hand, the armed actions usually cause the results directly after the conflict has begun. For instance, the result from air raid bombardment causes a wave of explosions that directly cause death/injury to people and damage/destruction of tangible objects (Schmitt, 2011). Negative consequences, which have more certain character, meaning that their occurrence is highly probable, are under the prohibition of use of force (Schmitt, 1999).
 Invasiveness
Invasiveness
A quantity which determines the depth of penetration in secured system. Greater penetration leads to higher value of invasiveness, which, in turn, trails the path to higher degree of use of force.
If we use again the example above, the economic embargo may have a little penetration, like in the case when the economic ties with another state are simply severed, but in the armed incursion there is always a breach in another state's territory. While in the first case there is no "use of force" action, in the second situation surely the use of force is a fact (Schmitt, 2011). Sovereignty, authority and prestige of a victim state may be impaired significantly in the event of unauthorized armed attacks that break in another's country territory (Schmitt, 1999).
Notwithstanding, owing to the borderless terrain of cyberspace, invasiveness criterion is hardly applicable. Indeed, one should apply this factor carefully in the event of cyber attack. The computer means often are used in the modern high-tech cyber exploitation and, as it has already been discussed in previous writings, the cyber exploitation seldom rises to a use of force even though it is highly invasive. Thus, actions of spying on the other governments' computer systems are not regarded as a use of force (Schmitt, 2011).
 Measurability
Measurability
Simply said, it is a calculator of consequences in quantitative values — if the number of this factor is at the upper diapason, then the state's interest is more likely to be undermined. In practice, the consequences of armed attack are easier to be gathered and evaluated, while the consequences of other kinds of coercion are difficult to measure. Thus, the international community, institutions, and laws are more willing to pursue the more evidential case (Schmitt, 1999).
And here comes again the economic embargo example. Although it may cause significant suffering, the international law excludes it from the use of force. Conversely, an armed attack which inflicts the slightest harm qualifies undoubtedly. This is so because the correct measurement is difficult in the first scenario while in the second one the result is usually clear (Schmitt, 2011). Speculative damages certainly make a weak case that a cyber attack is in fact tantamount to a kinetic armed attack (Sklerov, 2009).
 Presumptive Legitimacy
Presumptive Legitimacy
It is an unwritten rule that any use of violence is deemed illegitimate without any concrete provision to explicitly proclaim this for a fact. On the contrary, the other forms of coercion which are not explicitly forbidden are legitimate (Schmitt, 1999). The economic embargo is not considered a use of force and it is not banned at least by this provision. From this point, we can notice that if the act conducted via computer tools is not prohibited, then is presumptively legitimate (Schmitt, 2011). Furthermore, from the international community's point of view, "the less a cyberattack looks like accepted state practice, the stronger the argument that it is an illegal use of force or an armed attack (Sklerov, 2009, p. 69)."
 Responsibility
Responsibility
His original scheme has only six factors, but in 2011 Schmitt adds "responsibility" as a seventh indicator. This factor manifests when a state is responsible for a given cyber attack. The assessment is based on the degree of involvement. If a state is considerably implicated in a cyber attack, then it is more likely this act to be categorized as a use of force (Schmitt, 2011). Except for the involvement condition, however, a state must be recognized as a culprit with relation to a cyber attack that is duly attributed as well.
Functioning of Schmitt's seven-factor scheme
Michael Schmitt explains briefly the purpose and benefits of this consequence scheme:
These consequence commonalities can serve as ties between a cyber attack and the prevailing instrument-based prescriptive shorthand. By this scheme, one measures the consequences of a cyber attack against the commonalities to ascertain whether they more closely approximate consequences from a particular sort characterizing armed force or whether they are better placed outside the use of force boundary. This technique allows the force box to expand to fill lacunae (Schmitt, 1999).
The Schmitt's seven-factor scheme actually works by assessing the reasonably predictable consequences of a cyber attack and gauge them to the average results of an armed attack. If the former is similar to the latter, then the expansion of the use of force would be just. If they are not, then the act is beyond the ban on the use of force and if it is yet illegal should be prosecuted with the help of other legal mechanisms (Schmitt, 1999).
Empirical application of Schmitt's seven-factor scheme
On the ground, Schmitt's approach is being applied by the Pentagon's officials, even though not against an actual cyber attack. The case in question had begun the summer of 2006 when the Pentagon lost its communication network in Central and North USA. Later on, the connection with the South U.S. central was lost, too. The reason for both telecommunication disruptions was an accidental miscalculation of the digging work on construction sites made by construction crew personnel. As a result, the communications were cut off for more than 36 hours. However, after applying comprehensively the Schmitt's analytical scheme at the moment of the event, the Pentagon cyber division established that this incident is most probably not a cyber attack (Remus, 2011).
Final thought on the two tests
To conclude with a few words, the reviewed tests are direct application of the consequence-based methodology and as such they carry almost the same pros and cons innate to the approach in question. With this being so, it should be yet noted that each approach such as the Pictet's three-features criteria and Schmitt's seven-factor scheme is always likely to have a contribution on its own in filling gaps in theory and practice.
Reference List
Graham, D. (2010). Cyber threats and the law of war. Journal of National Security Law and Policy, 4, 87-104.
Schmitt, M. (1999). Computer network attack and use of force in international law. Columbia Journal of Transnational Law, 37, 885-937.
Schmitt, M. (2011). Cyber operations and the jus ad bellum revisited. Villanova Law Review, 56, 569-606.
Silver, D.B. (2002). Computer network attack as a use f force under Article 2(4) of the United Nations Charter. International Law Studies, 73.
Sklerov, M. (2009). Solving the dilemma of state responses to cyberattacks: A justification for the use of active for the use of active defences against states who neglect their duty to prevent. (Master's Thesis, The Judge Advocate General's School, USA)
Resmus, T. (2011). Cyber attacks and international law of armed conflicts: A 'jus ad bellum' perspective. Journal of International Commercial Law and Technology, 7.

What should you learn next?
Wingfield, T. (1999). Legal Aspects of Offensive Information Operations in Space. Retreived on 02/07/2013 from http://www.au.af.mil/au/awc/awcgate/dod-io-legal/wingfield.pdf




