Detecting Data Breaches with Honeywords
Introduction
Data breaches and security issues related to information leakage are a subject that has been making headlines in recent times. When a data breach happens, cybercriminals obtain information associated with a person or a large group of people. Data exposed by crooks is considered sensitive and often corresponds to personal emails, usernames, and password representations (generally, hash keys), when there is adequate security protection of user's information.
Often, cybercriminals obtain the password representation easily, and the cracking schema is commonly known: trying to guess the password behind the cryptographic hash through some documented techniques within the password cracking landscape, for instance, using rainbow tables and brute-force attacks. For this reason, the username-password authentication method is considered poor since that criminals can easily access the user's secret password.

FREE role-guided training plans
Honeywords can be highlighted at this point. Initially described by Ari Juels of RSA Labs and MIT Professor Ronald L. Rivest, that refer the following: "We propose a simple method for improving the security of hashed passwords: the maintenance of additional "honeywords" (false passwords) associated with each user's account" [1].
The Meaning of Honeywords
The term honeywords is very similar to a honeypot, where fake servers are created to fool cybercriminals, and cause them to attack the wrong server. Typically, this mechanism is used to help system administrators to detect more widespread security artifacts inside a network or a system.
According to the authors, with the use of honeywords
an adversary who steals a file of hashed passwords and inverts the hash function cannot tell if he has found the password or a honeyword [1].
Therefore, if an attacker obtains a fake password (honeyword) during the cracking process and tries to authenticate the false password into the system, the attempt will be flagged as an unlawful activity, and an alarm will be triggered to an IT department as a consequence. Within this context, there is also a secondary server named "honeychecker" with the capacity to distinguish the user password from honeywords. According to the authors, this system should be isolated from the primary system.
How to Improve System's Security Using Honeywords
A honeyword is composed by a fake password derived from the user's password. Consider the example presented in Figure 1 below.
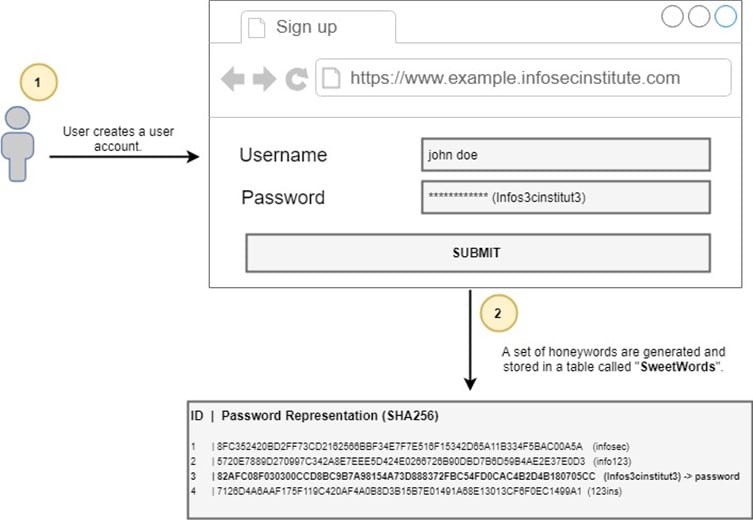
Figure 1: Honeywords are generated during a user's registry.
When a registry happens, e.g., in a website, the user can define his personal password as "Infos3cinstitut3" with the respective SHA256 cryptographic hash associated:
82AFC08F030300CCD8BC9B7A98154A73D888372FBC54FD0CAC4B2D4B180705CC (see label 1 highlighted above).
After submitting the password, the system derives several false passwords (honeywords) which are recorded, for instance, in the same table together with the original password (presented by label 2 in Figure 1). Honeywords are entirely invisible to users because they are generated and stored by the system.
This implementation also requires building a verifier called "honeychecker," allowing thus to validate true authentications and potentially malicious login attempts produced by cybercriminals during the process of password cracking.
The auxiliary checker is typically represented as an oracle, and it's not part of the main system. Figure 2 below shows a diagram which describes the general operation of a common honeychecker.
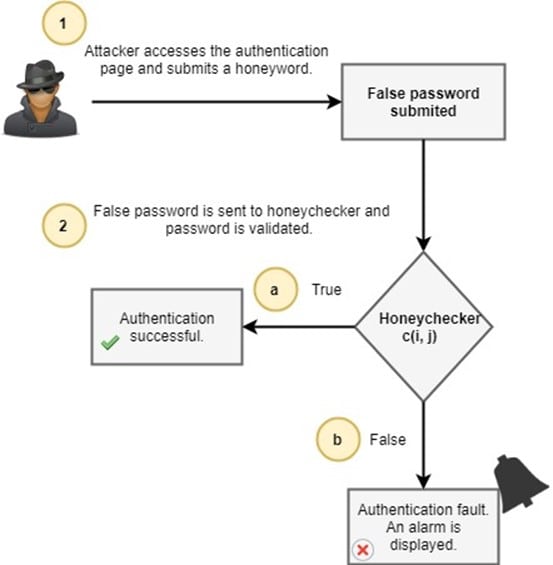
Figure 2: Validating honeywords via a honeychecker.
Weaker passwords are broken faster than strong passwords because they have a smaller size and a weak complexity. For example, according to the group of honeywords defined in Figure 1, the infosec honeyword is quickly broken compared to the original password picked by the user (Infos3cInstitut3). The last is effectively more complex and constituted by a mix of letters, numbers, and capitalized letters.
An authentication attempt is carried out on the target system whenever an attacker breaks a password. However, during the validation of the password, the honeychecker should mark the authentication attempt as "illegitimate" for the user john doe if he to try a login with a false password (highlighted with b in Figure 2). Here, a potential data breach also should be flagged and addressed to the IT team thereby enhancing security skills and processes against data breaches.
Benefits of Using Honeywords
It's clear that the use of honeywords isn't going to prevent cybercriminals from stealing password databases and cracking them. Nonetheless, the use of honeywords can improve the security of the system, and their users.
Some benefits are enumerated as follows:
- When a false login attempt occurs via a honeyword, a data breach can be earlier detected by IT operators.
- A user account can be automatically locked down when a honeyword is used.
- Honeychecker runs separated from the computer systems running a website and compromising the honeychecker does not compromise the website (and vice-versa).
- Two systems may be placed in different administrative domains (website and honeychecker), running distinct operating systems and platforms.
- And the last, a well-succeeded password cracking does not give the attacker confidence that he can log in successfully and undetected.
Conclusion
Honeywords aren't meant to replace the good password security practices. Nevertheless, as numerous breaches continue the rise, this kind of mechanisms can offer another type of business solution to detect data breaches more efficiently and quickly. Remember that no password security system is foolproof. The major problem with this poor authentication method are the people. They are, in fact, the most vulnerable endpoint.
Sources
[1] http://people.csail.mit.edu/rivest/pubs/JR13.pdf

FREE role-guided training plans
[2] https://seguranca-informatica.pt/palavras-passe-e-honey-words




