Database Security
Database security is one of the most important topics that have been discussed among security personnel. The growing number of incidents proves that it's something that should be taken care of immediately. Database security should provide controlled and protected access to the members and also should preserve the overall quality of the data. We must understand the issues and challenges related to database security and should be able to provide a solution. The threat to database depends on various factors like network security, physical security, encryption, authentication, etc. The data sensitivity differs for different organizations. There may be customer data, financial records, and many other types of valuable information within its database. It's very important to protect such data from internal and external attacks. There should be periodic audits to check the vulnerabilities and flaws that exist in the database. Some flaws arise through neglecting the security factor at the time of design or through using an expired version of the application without proper update. It's very important to understand the structure of the database and identify potential threats at the beginning stage. The three main points that should be considered when securing a database are the following:
- Protecting data from unauthorized access.
- Preventing unauthorized disclosure.
- Recovering from hardware or software errors.
So, in every case related to database security the main points to consider are access control, application access, vulnerability management, and auditing. Let's discuss these topics in detail. Since almost all databases are connected to the Internet in one or another, we need to understand the complexity of the structure. The following diagram shows how a database is normally used:
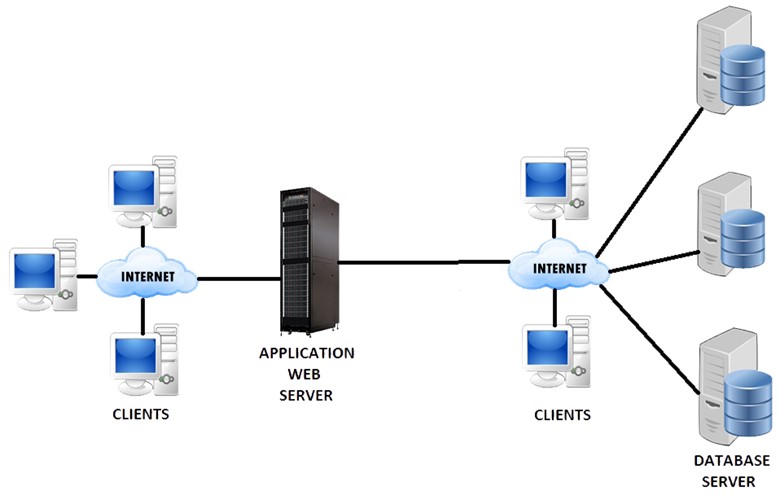
Figure 1 : Database Environment
Authentication
The first step in accessing a database is logging in to the database server after the authentication process. If the authentication process in not configured properly, it becomes easy for the attacker to gain access in to the database. If the database consists of high-priority data, multiple-level authentications should be implemented to maximize the security level. Even if a normal username/password authentication is implemented, we must make sure that the strength of the keywords used is high. The following are a few tips to increase the password strength:
- The number of characters in a password should be between 8 to 20 characters.
- It should not be related to your username, email address, server name, or phone number. Those kinds of passwords are very easy to guess.
- Repetition of passwords for multiples accounts should be avoided.
- A mixture of numbers, characters and symbols will increase the password strength.
There are many types of software available that help us to check the password strength. Make use of one such software to ensure maximum strength.
Access Control
The best way to secure the data is by limiting its access. We should implement authorization and authentication to each and every user accessing the data. The common way to do this is by assigning usernames and passwords to each user to log in to the database. Also, privileges should be set for different users, depending on the requirement by classification of sensitive data. Let's explain this with the help of an example. Consider a college database. Students should be given login access to their individual accounts and also permission to read the contents of the database assigned to them. Teachers and other officials should have the permission to write in the database when required. This is the basic step involved in securing a database. Even if an attacker manages to login to the database using a student's account, the access will be limited. In this process, identifying each user and assigning them processing and data access needs is the key point. Access control can be mainly implemented in four levels, as shown below:
- Discretionary access control (DAC): In this level, access is given to user, depending on the identity and privileges considering some pre-defined discretionary policies. In this method, users can grant permission on data to other users. Due to this feature, it's used in most companies. User can add or remove permission when needed.
- Content-based access control: In this, access is granted based on the contents. In an organization, there may be different projects running at the same time, so the users related to each projects are only given access to data related to their projects.
- Fine-grained access control: This gives access control at multiple levels. We could see this in Oracle virtual database, for example.
- Mandatory access control (MAC): This model is based on users and classification of data objects. The classification is based on different classes, called access classes. An access class contains various security levels. These could be used to give read or write permission to required class when needed.
Application Access
Users always log in to the database directly. They use an application or software to access the database. With the help of a security matrix, we can solve this problem. This tool helps in identifying the application and assigns the permission accordingly. The security matrix also provides a visual description of the database management, relation between each class and a detailed report on the current status. For each program, the permission is defined in the matrix which provides access as per the requirement.
Database Threats
According to research, databases are among the most compromised assets. Databases are the heart of any organization, so it's very important to protect these at any cost. When an attacker gains access to database they can damage it of expose it and can disturb the entire functioning of that organization. The following are the few threats that have been affecting database form a very long period of time:
- Excessive and unused privileges: Often users get privileges that exceed their needs. These over-granted permissions to a particular user can lead to various problems. If this worker leaves on bad terms, he can use these privileges to steal high sensitive data. This happens because of not properly assigning privilege control mechanisms.
- Privilege abuse: Users may sometimes misuse their privilege for unauthorized activities. This can be for various purposes. It's not advised to use their privilege for non-authorized works.
- SQL injection: These attacks are carried out by inserting malicious statements into the fields of a web application. This may give attacker access to the entire database.
- Malware: Malwares are sent to a user's email account as a part of phishing technique by the hacker. The user, without knowing, may click on the link that compromises the user. Through this user, the attacker finds its way into the database.
- Poor auditing records: Automated system recording should be a part of every database. It may cause various problems if proper records are not made. Most of the companies have audit systems that are provided by the database vendors. This software often doesn't meet the requirement for every company.
- Storage media exposure: People spend a lot of effort in protecting a live object. At times they forget to secure the backup, which is as important as the live system. An attacker can easily get access to an unencrypted backup and could use it for compromising the company, so it's very important to protect the backup data files and also to keep a track on high-priority users.
- Denial of service: This is a general type of attack, in which the access to network devices or data is denied. In a database, DOS is usually carried out by overloading the server with queries and requests that use a large amount of resources. This makes the server non-responsive, finally resulting in the failure of the database. DOS is a serious threat that should be taken care of. Every system is vulnerable to such attacks.
Database Auditing
With the help of periodic monitoring, the attacks on the database can be minimized to an extent. Auditing helps us to find the flaws and vulnerabilities in the existing structure and fix them with a proper solution. Database auditing consists of various levels, as listed below:
- Access and authentication auditing: This includes the log of users who use the database. It shows the time, content, and methods used by the users to access the data.
- User and administrator auditing: Activities performed by the user and the administrator are analyzed and reported in this auditing method.
- Security activity monitoring: This keeps track of the entire activity list and reports any kind of unauthorized or suspicious activities carried out in the database.
- Vulnerability and threat auditing: Vulnerabilities are normal in any system. It's our duty to identify and fix those flaws at the right time. In this auditing process, vulnerabilities are detected and fixed. It also identifies the users who try to exploit such vulnerabilities.
- Change in auditing: First set a basic structure for the auditing process. Then, depending on the requirements, the auditing polices should be changed and those changes should be tracked properly to avoid any confusion.
How to Carry Out Database Auditing?
- Identifying the data: This is not as simple as it sounds. To identify the data that actually needs to be secured is very important. A database might contain various types of data with different priority levels. It might also contain data, like public records, that needs no protection. Classifying these types of data would make the entire process very simple.
- Basic Auditing with In-built features: Nowadays every database server has default auditing features. The first thing is to run an audit with the help of those tools. Their login triggers as a default feature in many servers, which helps us to control and monitor login details. Using these tools, we cannot perform custom audit works that includes complex work. For this type of purpose. Third-party software is used to carry out auditing works.
- Use of Third-Party Auditing Software and Network Devices: These are extreme-end auditing tools that can be customized to meet the user's requirements. They have a lot of features and dig in deep to create maximum output. There are network devices available in the market that provide protection as well as monitoring services. The main advantage of these devices is that, since they are installed separately from the server, the performance of the server won't be affected.
Data Encryption
Encryption is one of the areas to which more attention should be given. Encrypting the data is very important in securing a database. In a real-time situation, we need to take care of two types of data. The first one is encryption for data at rest and the second one is data in transit with strong authentication control. For data at rest, there are various encryption algorithms available which cannot be easily reversed by unauthorized users. The algorithms are of different levels depending on the encryption technique. Some of the algorithms used in servers are DES, Triple DES, DESX, 128-bit AES, 192-bit AES, 256-bit AES, etc. The algorithms are selected according to the priority of each situation. There is no perfect algorithm that could be used for every condition. The data in transit should also be protected by every means. Secured shell traffic should be used to transmit data that should be protected. Usually the data are sent through a network as clear text. This type of data could be easily captured with the help of sniffers. In order to avoid such activity, the data are sent through SSH, which uses an encrypted path.
Securing a Database
It is a never-ending process that involves a set of steps that should be carried out periodically to ensure maximum security to the database.
- The first and foremost step is to find the database to be analyzed and secured.
- Next step is to classify the system or data according to the requirement. A database consists of data with different priority levels, so it should be classified properly before starting the process.
- Scanning the database for vulnerabilities, misconfigurations, and changes is done in this step. This helps to plan a strategy for securing the database.
- Next step is to prioritize the information based on the previous step. The vulnerabilities that need an immediate fix should be of high priority.
- Find the suitable fix for the vulnerabilities, run patches to update the existing system to fix the vulnerabilities.
- Auditing should be done after the fix to confirm the process. This will also point out if any further changes are to be made. Repeat the entire cycle on periodic basis to ensure maximum security to the database.
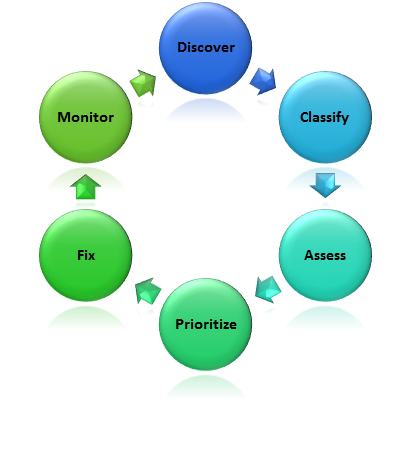
Figure 2: Database security Cycle
Monitoring and Blocking
- Live alerting and Blocking: All the database activities, such as login, access logout, etc., should be monitored to prevent data leaks and unauthorized access. When such activities are detected in a server. there should be alerts and warnings. If again accessed, the user should be blocked from accessing the database. The database traffic should be constantly monitored to identify irregular activities that may lead to problems such as a DOS attack.
- Check unusual access activity: Each user profile should be monitored thoroughly. Any attempt to access high-priority data should trigger a warning or be blocked immediately. This might help us from preventing attacks from injections, malware, etc.
- Filtering web request: To avoid an injection attack, it's very important to block all malicious web requests. Also, a web application firewall should also be established to check requests from web applications. All the HTTP parameters in the request should be inspected. The presence of brackets or special characters in the request is a sign of an attack.
- Local database monitoring: The users having the highest priority, such as system administrators, should be carefully monitored. They can be compromised by a phishing attack, which may lead to the database.
- Response timing: DOS attacks overload the server, making it non-responsive to requests and queries. Response time monitors should be implemented to check the response delay and other factors. Any clue for such delay should be carefully observed, because this could bring down the entire server.
- Implement connection controls: The load on the server should be controlled by limiting connection rates, query rates, etc.
Conclusion
The need for securing data has increased over time. We live in a world where information is given top priority. The right information in the wrong hands can do worse harm than ever imagined. Databases are being targeted by attackers from all over the world. All organizations and companies have made database security a part of their plan. More awareness should be spread about the importance of data security. There are various products in the market that meet our security requirements. We have to analyze it and choose the right one for our environment. Ignoring this could even cause the total breakdown of an organization. Companies have to set strong security policies that include database security.

What should you learn next?
Securing a database is not a simple task and cannot be completed with a few hours of work. It requires constant planning, dedication and, above all, its set of steps should be repeated over a period to ensure maximum efficiency.
Reference
- https://en.wikipedia.org/wiki/Database_security
- http://docs.oracle.com/cd/B19306_01/server.102/b14220/security.htm
- https://www.oracle.com/database/security/index.html
- https://msdn.microsoft.com/en-IN/library/ms345262.aspx
- https://www.sans.org/reading-room/whitepapers/analyst/making-database-security-security-priority-34835
- http://www.zdnet.com/article/the-top-ten-most-common-database-security-vulnerabilities/
- https://www.techopedia.com/definition/29841/database-security
- http://www.academia.edu/6866589/Introduction_to_Database_Security_Issues_Types_of_Security_Database
- http://www.slideshare.net/null0x00/database-security-issues
- https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2014/july/top-10-common-database-security-issues/
- http://www.collegelib.com/t-database-security-issues-and-challenges.html





