Reversing & Decrypting Database Credentials using Damn Vulnerable Thick Client App
Background
In the previous article, we have discussed injection attacks in Thick Client Applications specifically in DVTA. In this article, we will discuss how to decompile .NET applications to abuse the vulnerabilities exposed through the source code. To better understand this article, it is recommended to read the previous parts of this series if you haven't done yet.

FREE role-guided training plans
Let's begin.
There are multiple tools available for decompiling .NET applications. We are going to use dotPeek in this article. dotPeek can be downloaded from the following URL.
https://www.jetbrains.com/decompiler/download/
Launch dotPeek after downloading it. It should look as shown in the figure below.

dotPeek comes handy when you need to decompile the .NET assemblies into its equivalent c# source code. dotPeek has various other features apart from what we need in this article. You may explore its features from the following URL if you are interested.
https://www.jetbrains.com/decompiler/features/
Let us proceed to decompile DVTA application and explore if there is anything of our interest. dotPeek supports individual files as well as complete folders with .NET assemblies. Let us load individual files by navigating to File | Open. This looks as shown in the figure below.

Choose DVTA.exe file from DVTA application as shown in the figure below.

This will load DVTA.exe into Assembly Explorer as shown in the following figure.

If we click on any of the files shown under DVTA, dotPeek shows the decompiled code automatically as shown in the following figure.

IN DVTA, most of the database related code is written in DBAccess.dll. So, let us decompile DBAccess.dll using the same steps we used with DVTA.exe. Load DBAccess.dll and then choose DBAccessClass as shown in the figure below.

This will produce the code from DBAccessClass.cs file as shown in the figure below.

If you closely observe the above piece of code, there is a function called decryptPassword() inside which, the encrypted database password is being decrypted.
This logic is useful to write a new application that can decrypt the Database password in the same way as DVTA is decrypting it. In PART-1 of this series, we observed a configuration file inside DVTA directory, where we found encrypted database password, AES Key, and IV as shown in the figure below.

Now that we have the following details:
Encrypted Text: CTsvjZ0jQghXYWbSRcPxpQ==
AES KEY: J8gLXc454o5tW2HEF7HahcXPufj9v8k8
IV: fq20T0gMnXa6g0l4
Let us create a new application in C# using Visual Studio and decrypt the password using the information available.
-
Launch Visual Studio and create a new Windows Forms Application. In our case, it is named as aesdecrypt.

-
Now, add a button to the form as shown in the figure below.
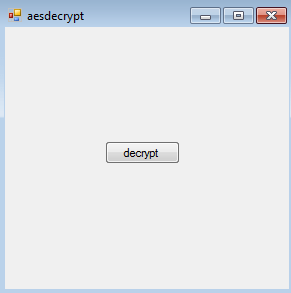
- Double click the above button, and we will land in .cs file where the code has to be written.
-
Make sure that you add the crypto reference System.Security.Cryptography as shown in the figure below.
-
As shown in the following figure, change the method name to decrypt for the button click event and write the code.

As you can see in the above figure, we used the same code taken from the decompiled code with some minor modifications. The original code takes the inputs from the configuration file, and they are hardcoded here. We are printing the decrypted password to the console using Console.WriteLine(). So, the decrypted password should be seen after running the application and clicking the button.
- Finally, run the application and click decrypt button.
-
Now, check Visual Studio output console and the following should be seen.
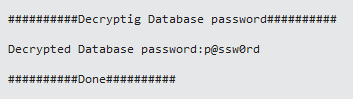
Nice, we have decrypted the password. We can use this decrypted password to login to the database as shown in PART-3 of this series.
Following is the complete source code we used in the above example.
using System.Collections.Generic;
using System.ComponentModel;
using System.Data;
using System.Drawing;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
using System.Windows.Forms;
using System.Security.Cryptography;
namespace aesdecrypt
{
public partial class aesdecrypt : Form
{
public aesdecrypt()
{
InitializeComponent();
}
private void decrypt(object sender, EventArgs e)
{
String key = "J8gLXc454o5tW2HEF7HahcXPufj9v8k8";
String IV = "fq20T0gMnXa6g0l4";
String encryptedtext = "CTsvjZ0jQghXYWbSRcPxpQ==";
byte[] encryptedBytes = Convert.FromBase64String(encryptedtext);
AesCryptoServiceProvider aes = new AesCryptoServiceProvider();
aes.BlockSize = 128;
aes.KeySize = 256;
aes.Key = System.Text.ASCIIEncoding.ASCII.GetBytes(key);
aes.IV = System.Text.ASCIIEncoding.ASCII.GetBytes(IV);
aes.Padding = PaddingMode.PKCS7;
aes.Mode = CipherMode.CBC;
ICryptoTransform crypto = aes.CreateDecryptor(aes.Key, aes.IV);
byte[] decryptedbytes = crypto.TransformFinalBlock(encryptedBytes, 0, encryptedBytes.Length);
String decryptedString = System.Text.ASCIIEncoding.ASCII.GetString(decryptedbytes);
Console.WriteLine("n");
Console.WriteLine("##########Decryptig Database password##########n");
Console.WriteLine("Decrypted Database password:" + decryptedString+"n");
Console.WriteLine("##########Done##########n");
}
}

What should you learn next?
}
Conclusion
In this article, we have discussed how .NET applications can be Reverse Engineered using dotPeek to view the source code and proceed further with the security assessment. We have also discussed how one can write his/her own application to decrypt the database credentials of DVTA using the decryption logic exposed in the application's source code. In the next article, we will discuss how to patch .NET applications to modify the application's logic.




