Cybersecurity Policy and Threat Assessment for the Energy Sector
INTRODUCTION: A wake-up call
An HP Enterprise Security's 2014 Global Report on the Cost of Cyber Crime by the Ponemon Institute reveals some astounding aspects of the cyber-attacks on the energy utilities. First, these assets suffered the highest average annual losses from cybercrimes ($13, 2 million), closely followed by the losses caused by computer attacks against the finance sector ($12, 97 million). Second, the statistics apparently dwarfed the media, retail and health care cyber incidents, which had received much bigger coverage. Another chart reaffirms that cybercrime caused most damage in terms of monetary loss to the same "Utilities and Energy" industry:
Learn Incident Response
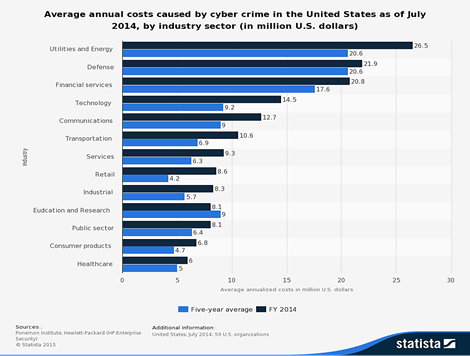
After looking at these numbers, it may seem unsurprising that people still remember the sophisticated cyber-attacks against Saudi Aramco and RasGas in 2012. Certainly, it was a vigorous wake-up call to the energy industry across the world: Even the biggest and wealthiest are not immune from cyber incidents. Moreover, in the summer of 2013, the Department of Homeland Security's ICS-CERT publicly reported a series of cyber-attacks against gas compression station operations. Despite advice to the contrary, those systems were Internet facing. In addition, at the Kaspersky Security Analyst Summit in 2014, the security researcher Jonathan Pollet, who specializes in ICS, managed to debug the control system of an amusement park ride, accessing it freely over the Internet without needing any credentials. What is even worse is the acknowledgement made by the ICS-CERT that such attacks are often difficult to analyze because logging and forensic data, which is supposed to be readily available in the ICS network, was partially or entirely non-existent.
On top of that, the surreptitious Dragonfly virus wreaked havoc on the energy businesses in the United States and Europe since 2011. Moreover, in 2014, the China-based hacker "Ugly Gorilla" allegedly infiltrated the network of a U.S. public utility company.
New cyber vulnerabilities in the energy infrastructure are discovered on a weekly basis which results in a vicious cycle where there is a constant struggle to patch up the newly emerging holes in the protective cloak.
The energy sector is up against two major cyber threats:
1) Vulnerabilities in the IT system employed for business and administrative purposes.
2) The operational technology (OT), that is, SCADA systems, specific software and other control technologies that are embedded into and operate power plants, transmission and distribution grids and pipelines.
Who Should Do the Drafting?
A survey performed by the IDC Energy Insights reports that half of all oil and gas companies do not have a documented, approved, and actionable information security policy in place. However, according to PwC, the world's second largest professional services network, "[e]nergy companies that embed security into strategic decision-making across the business are better able to recognize current and future security risks, navigate the threat landscape in pursuit of business opportunities, and allocate security resources more effectively…have a clear vision of how cyber security increases company's value [and] they'll able to clearly explain their cyber security strategy to all stakeholders: shareholders, investors, employees, regulators, and others."
Example—Chief Information Security Officers (CISOs)
Within the boundaries of an enterprise, information security policies are typically executed by Chief Information Security Officers (CISO). Founding their philosophy of work on the premise that an organization's data, network, users, customers have already been, or soon will be, compromised, CISOs can create a realistic, business-oriented security program that enables energy companies to quickly detect cyber-attacks and safeguard its most valuable information assets.


Comprehensive Vulnerability Assessment
Enterprise governance, risk, and compliance (eGRC) is an umbrella term having a threefold nature:
1) Gives account of the policies, procedures, and objectives by which an organization is governed.
2) The aims are pursued while avoiding or mitigating the negative effects.
3) Demonstrates adherence to laws, policies, regulations, industry standards, and contractual obligations:
The upstream segment of the oil and gas industry, more than any other part, has struggled throughout its history to cope with "silos" of segregated data and applications that do not maximize business value due to poor integration. "For example, to be truly effective in helping oil and gas companies manage governance, risk, and compliance, Environmental Health Sciences (EHS) applications must be integrated with a variety of other systems including Enterprise Resource Planning (ERP) systems, Enterprise Asset Management (EAM) applications, energy trading and risk management (ETRM) applications, supply chain management applications, and real-time data historians."
Generally speaking, there is an increased need for business continuity plans and enterprise-level security efforts, which provide evaluation of the security vulnerabilities in single-point infrastructure assets, i.e., power plants, refineries and storage terminals, and even networked features (examples of the last kind are transmission lines, pipelines and cyber systems). While energy sector players should be working to address as many physical, cyber and human risks and vulnerability problems as possible, some assets, most notably those identified as critical and high priority, should receive additional attention. In trying to protect everything, many companies may leave their most important information assets vulnerable. Therefore, being familiar with both your threat landscape and critical corporate resources is a key precondition to setting up a robust and resilient cyber security strategy.
To be successful, a cyber-security plan should be both threat-based and asset-based. Sound security resource investments are contingent on informed cyber risk assessment, rather than fulfilling compliance requirements alone. In protecting their business, energy companies should consider the entire scope of security—cyber, physical, technical, non-technical, and human factor. Today's company assets—as well as company vulnerabilities—extend beyond a compound, or even a firewall. Particularly important in the energy sector are the interconnectedness between supply chain, service providers, strategic partners, employees and customers. Effective cyber security policy should take into account this complex net of relationships among different entities, all of which form a different segment of the energy business' ecosystem.
Considering Smart Grid technologies
With the smart instrumentation that continues to pervade the entire energy sector, the amount of data produced will only grow. As the Symantec researcher, Candid Wueest, warns: "[T]he increasing number of connected systems and centralized control for ICS (Industrial Control Systems) means that the risks of attacks in the future will increase. Energy and utility companies need to be aware of these risks and plan accordingly to protect their valuable information as well as there is or SCADA (Supervisory Control and Data Acquisition) networks."
Consequently, the fact that virtually all of the centralized control systems are made by the same company – Siemens (software as well, like in the Stuxnet case) – contributes in a way to the vulnerability factor. Another factor that should be taken into account is the explosion in the number of devices that can be plugged into the power grid. No matter whether those are really small home devices—for example, wind and solar collectors—the diameter of the potential attack surface is growing day by day. The chairwoman of the Federal Trade Commissions (FTC) confirms this trend by stating at a conference on the Internet of Things (2014) that today's number of smart sensors on the Internet 3.5 billion is expected to boom to trillions within the next 10 years or so.

As the smart systems become more integrated into corporate systems, it is a matter of great importance to transform this state-of-the-art but inherently insecure technology to a technology that has built-in security. By way of extension, Smart Grid technologies blend more and more with the traditional grid, and the level of security of former should match the one of the latter if one wants to avoid discrepancies among the security policies (which would be eventually the least of your problems). On the positive side, ICT capabilities brought about by the growth in mobile device market, cloud computing, Big Data analytics and Internet of Things offer innovative opportunities to transform the management, usage and distribution of data the way we know it from a couple of years ago.
Verifying and Updating Infrastructure Information
Many of the existing data in this industry is subject to verification and validation protocols. The Department of Energy (DOE) is ready to initiate discussions with market players and form expert groups in order to identify and implement workable solutions where verification procedures are deemed inadequate, including in processes related to the verification of cyber data. It is considered that verified data sets based on mutually agreed-upon levels of accuracy will be beneficial to the energy infrastructure in every possible way.
Participating in a training workshop can always be helpful. Sector partners are able to share at these events knowledge directly about immediate security fixes founded during system assessments, revealing common vulnerabilities. In addition, every respectful firm should periodically follow the annual reports of regulators in which there are published mitigations for all vulnerabilities identified throughout the year.

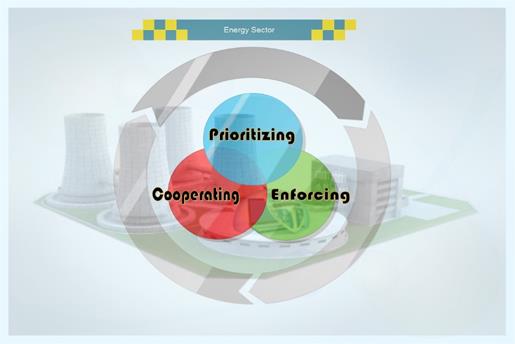
It seems that energy firms that want to introduce a successful cyber security policy should focus on three key aspects:
1. Prioritizing corporate resources by protecting those assets that have some worth to you and potentially to your adversaries.
2. Proactively enforcing cyber security best practices that will protect the business and, at the same time, will place the company in the forefront of the energy industry.
3. Effectively cooperating with energy policy makers and regulators, and participating in significant future cyber security initiatives in this sector.

Information Collection and Sharing
A public-private partnership is another key precondition for workable cyber security. Energy corporations that want to uphold their competitiveness in the marketplace must seek out the right opportunities to collaborate with the government and notable non-governmental organizations. Prosperous corporations in the energy industry always implement security information sharing plan that includes government agencies, industry peers, cross-industry groups, etc. After all, information sharing is not a one-way street.
The energy industry in the USA has gathered a considerable amount of data to further a wide range of risk-vulnerability-consequence assessments. On the one hand, data is collected and utilized by owners, operators, trade consortiums, as well as by industry-specific entities, such as the American Gas Association, American Petroleum Institute and NERC. On the other hand, the government also collects energy sector data through various agencies at the State and local level.
In times of security crisis or an emergency, the most invaluable information sources originate from those trusted relationships between government and industry. Moreover, this partnership will improve the general in information flow, when needed, through information-sharing mechanisms (e.g., Homeland Security Information Network (HSIN)).
Consistent, contextualized, and integrated information, available in mobility
Avoiding mistakes and ultimately mitigating security risks can result from maintaining the company information in updated and contextualized form. Data integration through a single point of information concerning processes, operation and maintenance across various energy industry units, for instance, ensures that the asset information is current, retrievable and properly managed in its entirety. It is vital as well that this data can be accessed by authorized staff (especially field workers) at any time via mobile applications.
Collaboration tools
Technologies that enhance collaboration can speed up the decision-making in event of incidents or disasters, reduce the overall level of risk in operations, and foster standardization. In a business like energy production, expertise is needed across the globe. The industry have not been sparing investments in collaboration tools over the last few years in order experts from every distant point of the world can exchange knowledge about design, engineering and operations. For example, drilling can be very complex activity, and oil and gas companies would usually need 3D visualization and collaboration rooms that will facilitate the exchange of data, models and tools. When speaking about collaboration technologies, cloud and suchlike platforms represent a promising option in terms of mutual assistance.
Protection of Collected Data Energy Sector
Ensuring that your business data is adequately protected is per se a legal requirement. File-level of encryption, for instance, is one of the most effective approaches to guaranteeing safety without being at the expense of productivity.
Owners, operators, and other sector partners in the energy industry have reasonable expectations that all data and information that have been voluntarily shared with the U.S. Department of Homeland Security (DHS) or the Department of Energy (DOE) will be protected from release in accordance with norms set out by the Protected Critical Infrastructure Information (PCII) or other applicable classification procedures. In addition, this data should not be used for purposes not directly connected to the infrastructure protection and recovery. As far as the information sharing and protection in the State regulatory context is concerned, models such as National Association of Regulatory Utility Commissioners (NARUC) are of great importance.

Other Essential Elements:
Compliance
Keeping up with the IT security compliance is challenging for businesses conducting widespread and high-volume oil and gas operations. Administrators should rely on ultra-fast, automated systems to manage and configure everything ranging from computers and data centers to private cloud environments. A comparison between internal standards and international ones and industry best practices should be made.
Security Audits
Data and management audits should be mandatory, especially in cases when data is intended for regulatory and ratemaking usage. In complex organizations with stringent security requirements, audit policies can generate in no time remarkable volumes of security related events. Centralized database storage and consolidation of security logs, filtering and evaluation of events via reporting mechanisms and robust data analysis are things that can be helpful in those complex environments. Contemporary audit systems enable administrators with the option to implement audit policies that automatically save all server or various workstation events to a local security log. These systems also comes with features that allow for tight control over the personnel who can access the audit database.
Access Control
Finding the right balance between the need for fast and convenient access and maintaining a high level of security is not an easy task. Both regional and global market players have always been dependent on tons of email exchange, increasing usage of intranet websites and other collaborative means that facilitate production process, project making, and the management of the work output as a whole among far-flung partners and employees.
Network Access Protection
It is thought that the best access protection solution rests on the combination between device-level security and corporate governance policy compliance. Defining granular levels of access based on client identity, pre-access compliance and group policies is one way to approach the problem. Automatic control barriers should detect and weed out non-compliant devices, then start up remediation and update procedure for ensuring full compliance before network access is granted.
Respond & Recover
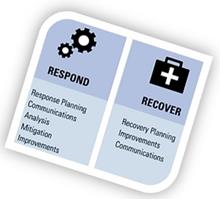
Security incidents happen even in the most secure systems. That is why it is important that there is a pre-deployed contingency plan and relief mechanisms that will help to bring the organization back to its feet. These recovery procedures not only help organizations to contain and eradicate a cyber-threat as quickly as possible, but they also serve as a record base from which the other companies in the sector can learn how to better protect themselves.
 While the industry desperately attempts to find a solution, more and more energy firms are resorting to the purchase of cyber insurance. So consider this option, too.
While the industry desperately attempts to find a solution, more and more energy firms are resorting to the purchase of cyber insurance. So consider this option, too.
Conclusion
Today's infrastructure is heavily dependent on the power grid. Without a doubt, if you are "low on battery", it is not possible to provide just about anything that requires electricity. Moreover, due to the Internet, everything now is interconnected. Therefore, if a malicious actor has the capabilities to pull the plug on the entire country, it could have a devastating avalanche-like impact on much larger scale than even imagined. Under these circumstances, there is no surprise that the attacks against the energy sector rank very high in the hierarchy of cybersecurity incidents. All we can do is to fortify our defenses as good as we can. That would include creating a cybersecurity policy that will help us shake off easier the panic when the battle begins, and why not even prevent the whole thing before it has a chance to develop into something serious.
Reference List
Armerding, T. (2014). Energy sector a prime target for cyber attacks. Available at http://www.csoonline.com/article/2134407/fraud-prevention/energy-sector-a-prime-target-for-cyber-attacks.html (20/07/2015)
Assante, M. (2014). America's Critical Infrastructure Is Vulnerable To Cyber Attacks. Available at http://www.forbes.com/sites/realspin/2014/11/11/americas-critical-infrastructure-is-vulnerable-to-cyber-attacks/ (20/07/2015)
Bigliani, R. (2013). Reducing Risk in Oil and Gas Operations. Available at http://www.emc.com/collateral/analyst-reports/minimizing-operational-risk-in-oil-gas-industry.pdf (20/07/2015)
Bucci, S., Rosenzweig, P. and Inserra, D. (2013). A Congressional Guide: Seven Steps to U.S. Security, Prosperity, and Freedom in Cyberspace. Available at http://www.heritage.org/research/reports/2013/04/a-congressional-guide-seven-steps-to-us-security-prosperity-and-freedom-in-cyberspace (20/07/2015)
Eckert, S. (2014). Protecting Critical Infrastructure: The Role of the Private Sector. Available at https://www.ridgway.pitt.edu/Portals/1/pdfs/Publications/Eckert.pdf (20/07/2015)
Homeland Security (2013). NIPP 2013 Partnering for Critical Infrastructure Security and Resilience. Available at http://www.dhs.gov/sites/default/files/publications/NIPP%202013_Partnering%20for%20Critical%20Infrastructure%20Security%20and%20Resilience_508_0.pdf (20/07/2015)
Luke, R. (2015). Cyber Threat Has Oil And Gas Majors On Edge. Available at http://oilprice.com/Energy/Energy-General/Cyber-Threat-Has-Oil-And-Gas-Majors-On-Edge.html (20/07/2015)
Microsoft (2013). Security in Upstream Oil & Gas. Available at https://www.google.bg/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&ved=0CCQQFjAAahUKEwjVlvW-8OvGAhWMEywKHeMwCZU&url=http%3A%2F%2Fdownload.microsoft.com%2Fdownload%2F5%2F1%2F3%2F5136F8B4-5AB5-4E3E-96AF-611F84150AD7%2FSecurity%2520in%2520Upstream%2520Oil%2520%2520Gas%2520White%2520Paper.pdf&ei=mwyuVZXdFIynsAHj4aSoCQ&usg=AFQjCNE9sg3GvuN6k9sfBxeLl8KWvszxnA&cad=rj (20/07/2015)
National Institute of Standards and Technology (2014). Framework for Improving Critical Infrastructure Cybersecurity. Available at http://www.nist.gov/cyberframework/upload/cybersecurity-framework-021214-final.pdf (20/07/2015)
Perez, T., Segalis, B., Navetta, D. (2015). Energy cybersecurity – a critical concern for the nation. Available at http://www.dataprotectionreport.com/2015/04/energy-cybersecurity-a-critical-concern-for-the-nation/ (20/07/2015)
PWC (2013). Embedding cyber security into the energy ecosystem. Available at https://www.pwc.com/en_GX/gx/oil-gas-energy/publications/assets/pwc-embedding-cyber-security-into-the-energy-ecosystem-pdf.pdf (20/07/2015)
The White House Office of the Press Secretary (2013). Executive Order -- Improving Critical Infrastructure Cybersecurity. Available at https://www.whitehouse.gov/the-press-office/2013/02/12/executive-order-improving-critical-infrastructure-cybersecurity (20/07/2015)
Learn Incident Response
United States Department of Energy (2010). Energy Sector-Specific Plan. Available at http://energy.gov/sites/prod/files/oeprod/DocumentsandMedia/Energy_SSP_2010.pdf (20/07/2015)



