Computer Forensics: Multimedia and Content Forensics
Introduction
Probably one of the most exciting and relevant fields in the computing world today is forensics. Much like its criminal namesake, computer forensics is the practice of collecting, analyzing, and reporting on digital data so that is both legal and admissible in court. It is an evidence-based process that can be used for the detection and prevention of a cybercrime or any incident that involves the misuse of data. But instead of blood spatters or DNA swabs, computer forensics relies on evidence in the form of emails, files, online documents, and digital fingerprints. Just as physical components in the real world can lead investigators to criminals, virtual trails can be followed to reveal the movements and intentions of hackers. In this way, computer forensics allows the extension of law enforcement into the digital spheres, also known as the place where people spend most of their time. This modern shift has allowed law enforcement to address Internet crimes as robustly as real-world crimes and to use digital evidence as a legitimate means for enforcing cyber laws and prosecuting those who abuse them.
Despite the legitimacy of the field, the term computer forensics is not entirely straightforward in its definition of how an electronic device was used in a crime. Was the computer a tool used to commit a crime in the real world? Or was the computer just the means used to create the digital landscape where the crime could take place? In either case, forensic investigators must extract probative facts from the computers involved and use them to piece together a logical scenario.
Learn Digital Forensics
What Is Multimedia Forensics?
When applied to the field of multimedia, digital forensics faces some new challenges. Because multimedia is content that uses a mix of various forms, such as text, audio, and images, it has become an actively changing form of investigation in the digital world. And, thanks to the wide adoption of mobile devices, high bandwidth, and cheaper storage, online users now generate crazy amounts of multimedia content, all of which they are free to store and share via the Internet. This growth has pushed digital multimedia into the forefront of human activity and made it an integral part of everyday life. As such, this varied content must also be secured from illegal use through the forensic process.
While this approach to digital safety sounds feasible enough, it’s important to remember the sheer amount of data being handled in this situation. In fact, the amount of data is so massive, it has surpassed the ability of forensic experts to effectively process and analyze it. Plus, there are also the challenges of limited time, numerous formats, short innovation cycles, and the highly dynamic environment to consider. Tools are therefore needed to support the investigative process through increased management, protection, interpretation, and visualization. The multimedia community has developed some excellent solutions to this problem, including knowledge extraction, automatic categorization, and indexing. But there are still challenges and constraints involved, and most experts agree the time is right to tailor and adapt multimedia forensics to modern demands.
What Are Some Different Types of Multimedia and Content Forensics?
Watermarking is a technique used in multimedia forensics to identify the original source and user authentication for a particular image. This forensic (or digital) watermark is a code of characters embedded in a digital document, image, video, or computer program that offers the details investigators need to find out more about the images they encounter. This insight can protect the interest of content creators against illegal use and make it easier for copyright holders to locate individuals who violate this ownership. Further, a forensic watermark can alert an honest user in the event that they inadvertently receive an illegitimate document or program. Moreover, these marks can be repeated at random locations within the content, which can make them somewhat difficult to predict and remove.
Digital signatures are the equivalent or handwritten ones except that they appear in electronic form. These signatures encrypt the contents of a document, allowing applications to detect if it has been tampered with in some way. From a legal perspective, this allows the creator to prove that a document existed at a certain date and time. This can be useful in situations where the exact moment of a cybercrime needs to be nailed down within a larger forensic investigation.
What Are the Two Approaches to Multimedia Authentication?
Internet content comes in a lot of different varieties, so the forensic approaches developed to analyze them must also vary in scope and sequence. The goal is to analyze the images, audio, and video of multimedia content in order to produce some kind of forensic evidence. Image forensics focuses specifically on still images by looking at the authenticity and integrity of data, a tactic that is particularly useful in forgery detection. By reconstructing the history of the image itself—a process known as image ballistics—investigators can match metadata and file structure with a known device, such as a digital camera’s make and model. Multimedia security divides its efforts between two main approaches: active and passive.
Active image authentication is a technique that uses a known authentication code embedded in the image or sent with it for assessing its integrity on the receiving end. This approach requires a watermark or a digital signature to be created precisely when the image is recorded or sent, which limits its ability to handle specially equipped digital devices. However, the overwhelming majority of images on the internet today do not have a digital watermark or signature, which has forced this authentication method to consider additional techniques.
Passive image authentication is a method that uses only the image itself for assessing its integrity, without any peripheral information, such as a signature or watermark from the sender. This technique works well in the absence of these identifying features. It works on the assumption that digital forgeries may disturb the underlying property or quality of an image, even though no visual clue has been left behind.
What Are Some Common Digital Fingerprints?
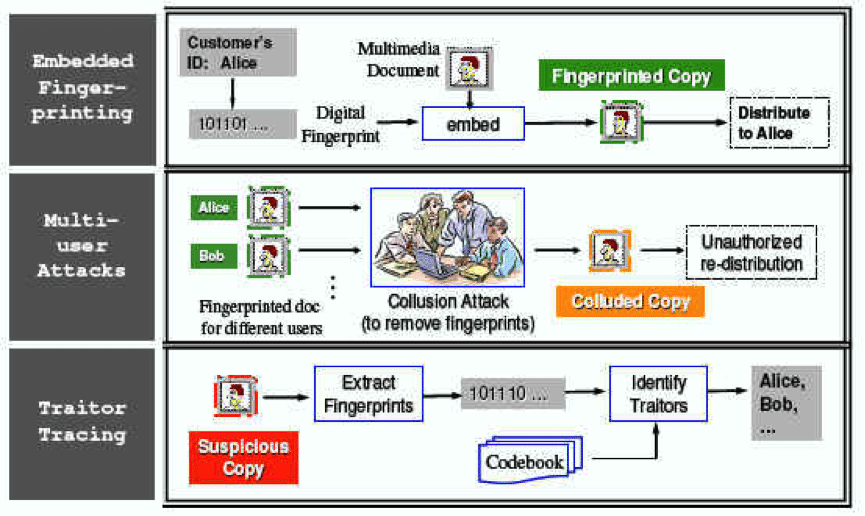
Although cryptographic tools and access control ensure the safe delivery of multimedia over networks, this protection ends as soon as the content is delivered and safely decrypted. Digital fingerprinting has emerged to address this post-delivery dilemma by identifying users who have legitimate access to the plaintext but use it for unauthorized purposes. This process allows investigators to trace the illegal usage of multimedia through unique identifying information, known as a “fingerprint,” embedded in the content before distribution.
Although these prints are technically coded strings of binary digits generated by mathematical algorithms, they are as unique as the analog fingerprints of a person. In the multimedia world, this technology can identify a piece of media like a song or video clip as being originally itself, complete with its own unique features. As a forensic tool, this process enables sites like YouTube to scan files and match the digital fingerprints they find against a database of copyrighted material to see if any intellectual property is being violated. But this is not the only way digital fingerprinting can be utilized. In a more traditional way, a user’s personal computer could also be equated to a digital fingerprint with the ability to trace online activity. Both concepts rely on the notion of a unique identifier—but with completely disparate functionalities.
As an emerging forensic tool, digital fingerprinting is still in something of a fledgling state, with one powerful adversary known as the multi-user collusion attack. This threat occurs when a group of hackers work together to remove any trace of these identifying fingerprints. Through the connectedness of the internet, malicious actors with differently marked versions of the same content can come together to mount attacks against these fingerprints. And hackers can also produce a new untraceable version of the content just by reducing the identifying nature of their own. This is a cost-effective way to remove identifying features and it poses a major threat to multimedia fingerprinting.
Learn Digital Forensics
Conclusion
The more images and videos continue to flood the internet, entertaining and educating the world at large, the more critical it becomes to find protection through forensic investigations. As online multimedia content continues to grow, it will become increasingly important for users and creators to understand the legal boundaries of the virtual world and how they will be protected through vigilance and knowledge.