Chaining Web Proxies to overcome limitations
This article shows a practical example of what is proxy chaining in a web proxy tool and how proxy chaining can be used to overcome limitations of web proxy tools
Introduction:

Earn two pentesting certifications at once!
Enroll in one boot camp to earn both your Certified Ethical Hacker (CEH) and CompTIA PenTest+ certifications — backed with an Exam Pass Guarantee.
Web proxies are tools used to modify the request/response to web servers to perform penetration testing of web applications. There's a whole lot of web proxy tools (such as Burp, Paros, ZAP, etc…) available out there. All the popular and major proxies work seamlessly and very efficiently. But often, we may face certain issues with them in order to perform a particular function as they may not support it or may be limited due to a bug. In that scenario, we can combine two proxies with each other to get around this limitation present in both or either of two. Every proxy has a feature called 'Proxy Chain' where we can chain two proxies and overcome the limitations. This article shows a practical example we faced with some of the popular proxies and how we overcame their respective limitations/bugs.
The issue:
While doing one assessment, we faced one issue of our ZAP proxy, when it was throwing the response '401 Unauthorized' while we were trying to fuzz one application. The application was using NTLM authentication, where the client needs to send the domain name, username and user-password's hash combination to the server, in order to entertain the requests. NTLM is a windows challenge/response authentication protocol.
For more info on NTLM: http://msdn.microsoft.com/en-us/library/windows/desktop/aa378749%28v=vs.85%29.aspx.
So, we were not able to fuzz the parameters as it was sending back '401 Unauthorized' response. We don't know for what reason despite us providing the windows credentials to ZAP [Fig-1].
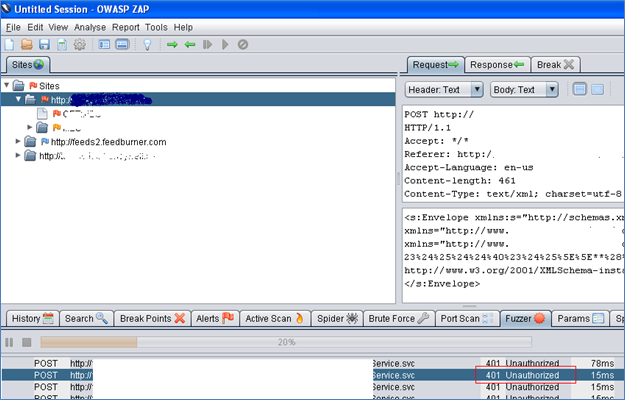
Fig-1
So we had no other option except trying other similar web proxies. We tried WebScarab and provided Windows authentication by going Tools-> Credentials [Fig-2]
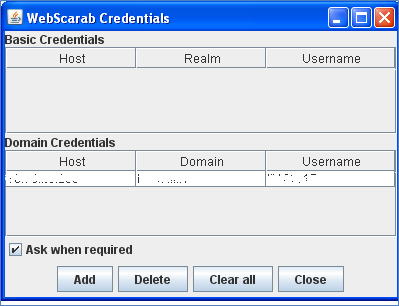
Fig-2
When we again try to capture the request response, it was working fine. Then we wanted to fuzz the parameters in one of the URLs. We need to right click on any of the requests on Summary tab and select Use as a fuzz template to send it to Fuzz tab.Bad luck again; though Webscarab was working fine with windows authentication, in the Fuzzing tab, the parameters were not appearing [Fig-3].
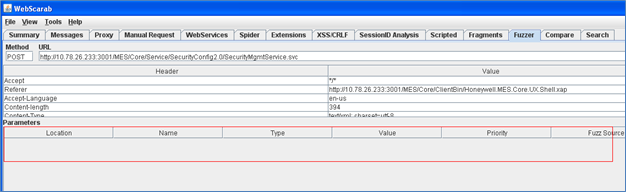
Fig-3
Now the scenarios were:
-
ZAP was sending an unauthorized error while fuzzing, even thought we had supplied the windows credentials
-
Webscarab was having issues as the parameters to be fuzzed were not being displayed
A bizarre situation indeed!
Proxy chaining:
We are going to use something already available in the tools and we can use it effectively to overcome some of the limitations of individual tools. The proxy chain works as follows:
-
The client (browser) will forward the request to Proxy1 (ZAP)
-
Proxy1 will in turn forward it to Proxy2 (Webscarab)
-
Proxy2 will pass it to the server
So, the requirements for performing this action are:
-
The client (browser) will run on the same port as Proxy1 (ZAP), say 8880
-
We shall use Proxy chaining option in Prox1 (ZAP) to forward this request to Proxy2 (Webscarab)
-
We shall configure the same port no. (say 8008) in Proxy1 (ZAP), on which Proxy2 (Webscarab) is running
-
The Proxy2 (Webscarab) will automatically forward the request to the server
Now, the overall scenarios are similar to Fig-4:
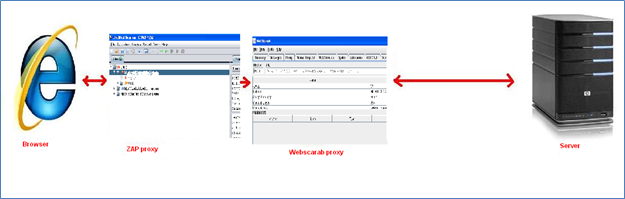
Fig-4
Setting proxy chain option in ZAP:
In ZAP, go to Tools-> Options-> Connection-> Use an outgoing proxy server and specify the address as 127.0.0.1 and port as 8008 [Fig-5].
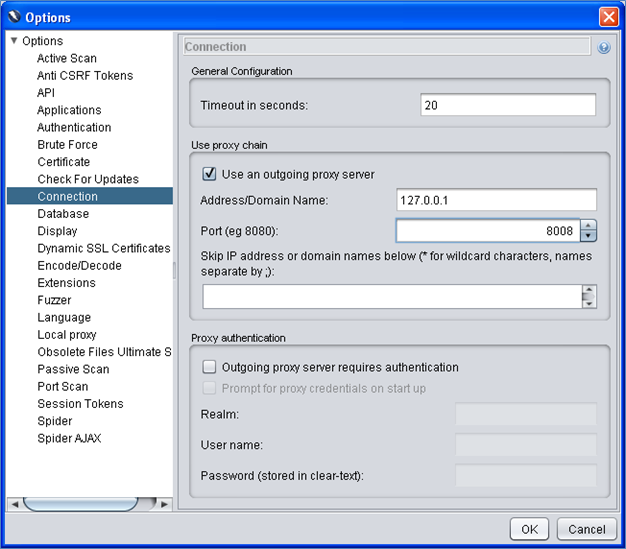
Fig-5
Port 8008 is where the next proxy (Webscarab runs). We need not specify it in Webscarab as it runs at this port by default.
Try to access the URL in the browser. The browser will forward the request to ZAP on port 8880, ZAP will in turn pass it to Webscarab, which is running at port 8008. Webscarab passes this to the server. The chain is now complete.
Let's see how this responds when we again try to fuzz it in ZAP. Nice, we can now successfully fuzz the parameters without getting the '401 Unauthorized' response! We now get 200 OK responses [Fig-6].
Conclusion:
We saw how we can use proxy chaining to use features of both the proxies, subsequently solving individual tool issues.
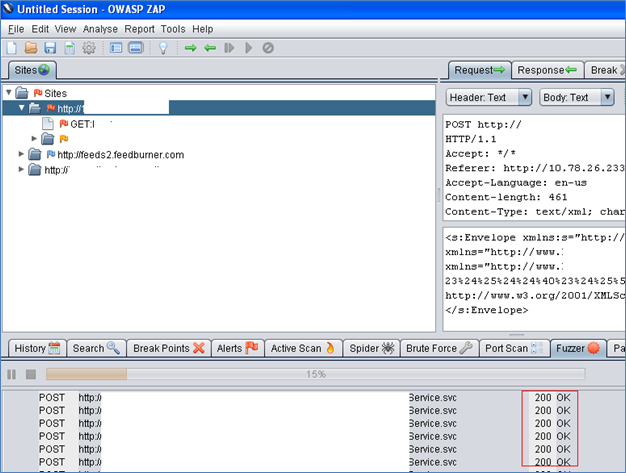
Fig-6
I filed a bug with the vendor and I'm waiting to see their response as to if it's an issue at our end or a bug with their software: http://code.google.com/p/zaproxy/issues/detail?id=554
References:
http://en.wikipedia.org/wiki/NTLM
https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project

What should you learn next?
https://www.owasp.org/index.php/Category:OWASP_WebScarab_Project






