Battling with Cyber Warriors- Exploit Kits
Introduction
In today's environment of highly interconnected system necessities, bringing down a system may cause a catastrophic damage to an individual in many ways. Hackers are frequent in the market, making exploit kits that can bring down the whole system. Even a novice in hacking technology can use these exploit kits to wipe the enemy out from the globe.

FREE role-guided training plans
Most organizations fail to update in response to the latest threats in the market and, due to a competitive environment that requires product innovation and reduction of administrative cost, such releases in exploit kits remain undetected in an organizational perspective. Doing much research on these exploit kits requires funding for the information security domain that is cost-prohibitive and impracticable for most organizations. An organization must plan to maintain an operational resilience and protect their valuable assets effectively. The development and distribution of exploit kits is a never-ending process and managing these exploit kits is not a trivial task for any organization.
An exploit kit is a malware toolkit that is used to exploit the vulnerabilities of a system. It is a platform that distributes malware including bots, spyware, backdoors, or other payloads to the victim's machine.
The main purpose of an exploit kit is that it automates the exploitation of client-side vulnerabilities, mostly targeting browsers. It also targets various programs that can be accessed by a browser. Most exploit kits target zero-day vulnerabilities or exploits for which patches are out in the market. For instance, the Black Hole exploit kit targets vulnerabilities in browsers such as Internet Explorer, Firefox, Google Chrome, and Safari and vulnerabilities in Java, Adobe Reader, and Adobe Flash Player.
A key characteristic of an exploit kit is the simplicity with which it can be used by anyone; a user need not be an IT or security expert. The main benefit of exploit kits is that the attacker doesn't need to know how to create exploits. Through the use of an exploit kit, specific vulnerabilities can be exploited without any expertise. It also provides a user-friendly interface that can be used to track the infection statistics and it also provides a remote mechanism to control the exploited system.
Types of Exploit Kits
An exploit kit is a launching platform used to deliver payload, which includes bots, backdoors, spyware, or any other type of malware. Exploit kits are not bounded by geographical limits and can be remotely controlled from one location while exploiting vulnerabilities at another location. This provides a great advantage to the attacker, since it will be very difficult to trace the source of attack and carry out further legal actions.
Black Hole Exploit Kit
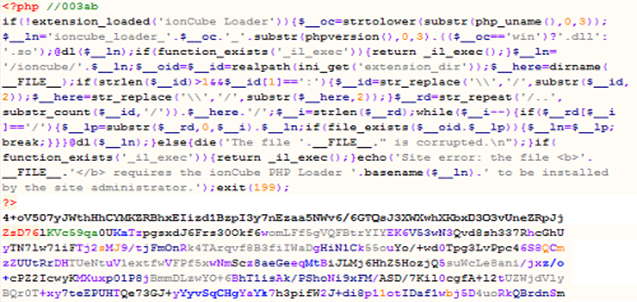
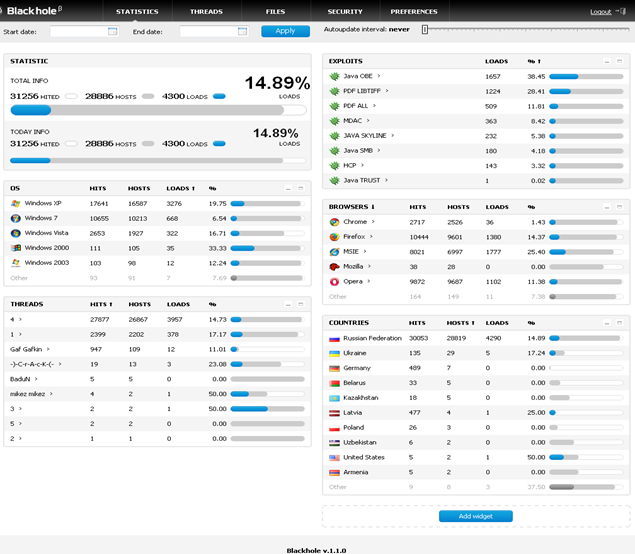
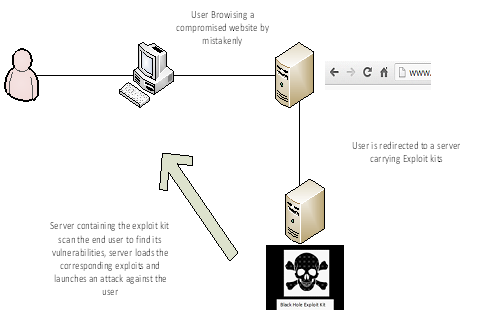
Black Hole loads malicious contents into victim's computers and is one of the major web threats that exist today. It is of Russian origin and can be customized into different levels that can be used to exploit various levels of vulnerabilities. The working of the Black Hole exploit kit is as follows. A victim browses on a malicious payload-injected website, which further redirects to a server that hosts the malicious exploit kit. After that, the exploit kit scans the system and detects the vulnerabilities. Then the particularly crafted payload is injected into the system that will be exploited. This kit's versions vary from v1.0.0 to v1.2.2 and contain PHP scripts running on a web server; it uses MySQL as a back end. These scripts are encrypted using an ionCube encoder that makes the code undetectable (ionCube encoders are tools to protect the software that is written in php from viewing and changing code; once the codes are encoded via ion cube then there is no other solution to decode the codes).

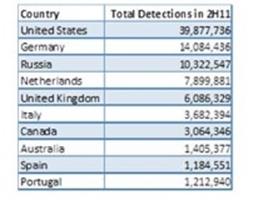

It has different confi
The Black Hole exploit kit targets various client vulnerabilities, including Java, Adobe Flash Player, Adobe Reader, etc. It has an add-on for antivirus scanning and has different license types including rental, three-month license, half-year license, annual license, etc.
Crime Pack Exploit Kit
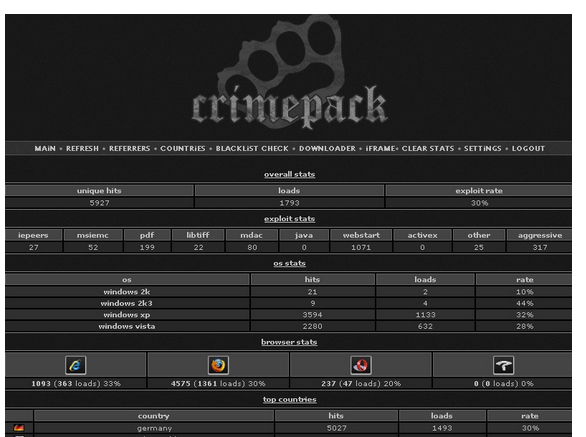
Crimepack was the most popular exploit kit that was available in the market. Whenever news of Crimepack exploit releases were out, more users were seen to be downloading it. Crimepack primarily targeted German and South American websites. The cost of this pack was around $400 and around 14 exploit kits were made available inside crime pack. All of the following vulnerabilities are now fixed and security measures have been enforced to detect Crimepack exploits.
White Hole Exploit Kit
The White Hole exploit kit has similar code as the Black Hole kit; it provides cybercriminals with one more tool with which to infect computers with malware over the web. The kit is different from Black Hole in that it does not use JavaScript for code obfuscation. It has the ability to evade antivirus detection, to prevent Google safe browsing from detecting, and to load up to 20 malicious files at once. White Hole is being used to distribute a variant of a rootkit called ZeroAccess, whose purpose is to install additional malware.
White Hole kits use the drive-by download attack pattern that doesn't require any user interaction, making them one of the most efficient ways to distribute malware. Users generally get redirected to drive-by download attack pages when visiting compromised websites. To prevent these types of attacks, disable browser plug-ins that are not frequently used and enable click-to-play for plug-in based content in browsers.
Phoenix Exploit Kit
The Phoenix exploit kit is a commercial crimeware tool that detects vulnerabilities on a system and exploits vulnerabilities by injecting malicious software. This malicious code can be used to compromise the security of all data on the computer. This exploit uses the infection method by injecting malicious code into legitimate websites. It installs a number of different malwares, including variants of the PWS: Win32/Zbot family. Like most other exploit kits, Phoenix exploits vulnerabilities in Java, Adobe Flash Player, Adobe Reader, and Internet Explorer.
The Phoenix exploit kit continues to be one of the most popular drive-by download packs used by cyber criminals. These attacks are very dangerous and effective because the infection process is completely transparent to the victims.
Neutrino Exploit Kit
Neutrino has a simple control panel and includes features that evade antivirus and IPS systems when exploited successfully. It downloads a ransomware variant that typically locks computers until users pay a certain amount of money or ransom. It has various features such as capturing system information, traffic filtering, encryption of stolen information, etc.
Styx Exploit Kit
Styx redirects users from legitimate websites to malicious websites hosting exploit files that search for vulnerable applications installed in the system. This page has an iframe that contains a malicious link with obfuscated code. The JScript on the malicious page references the iframe using a unique ID, decrypts the malicious code, and loads malicious web pages that have particular payloads for corresponding vulnerabilities. Then a downloader that delivers additional malware from remote server is added as final payload.
Eleonore Exploit Kit
This is a malware package that contains a collection of exploits used to compromise web pages. When the compromised web pages are viewed via vulnerable systems, the exploit payload is run. The attacker gains access to Internet web servers and installs the exploit by modifying web pages, which are then served to the public. The malware pack also contains functionality for the tracking and management of compromised computers.
Incognito Exploit Kit
The Incognito Web-based exploit kit is located in the cloud and provides services for underground communities. The kit uses JavaScript code to perform drive-by downloads. The two most common versions of this exploit kit are Incognito and Incognito 2.0. This kit most often exploits the vulnerability of Java and Adobe. It applies new multi-layered obfuscation techniques on a regular basis. The Incognito exploit kit can be recognized based on typical URL-path patterns in which its top-level domains and hostnames vary accordingly.
CK Exploit Kit
The Chinese-origin CK exploit kit uses a tiny encryption algorithm (TEA) that incorporates a base-64 encoding algorithm. Exploit code generated by the CK kit was identified by file, variable, and function names based on the strings CK and CKWM. The CK kit is a descendant of the Net Boom NB exploit kit produced in late 2010.

Exploit Kits in Action
1. Regulating Web Traffic
The Black Hole exploit kit works mainly by controlling user web traffic with various techniques. This includes compromising legitimate websites and injecting malicious code into them. After that, when these pages are browsed by the victim, the malicious code silently loads content from the exploit site.
Different techniques that control web traffic are:
- Compromised Website
This technique of controlling web traffic is carried out by compromising legitimate websites or servers and injecting it with malicious code. This malicious code then loads contents from exploit sites. Mostly the web pages are compromised with malicious JavaScript or simple HTML iframe elements. These scripts are generally encrypted or hidden in various ways in order to avoid detection.
- Phishing Email
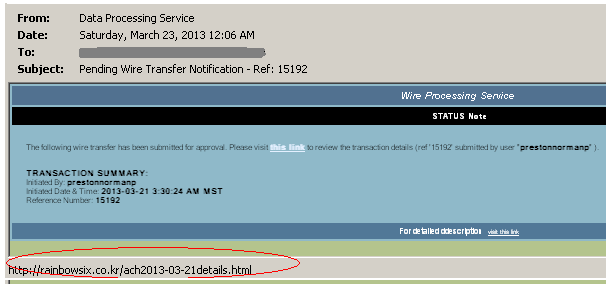
Another technique used for controlling web traffic is sending phishing emails. These emails includes malicious URLs that lead to malicious websites. They usually load simple JavaScript content that navigates to the Black Hole exploit site. Phishing emails may also use techniques that include HTML contents or social engineering methods.
There were a lot of mailing campaigns related to the Black Hole exploit kit that claimed that this mail was from LinkedIn or Facebook. Actually, these mails were spoofed and acted as initiators for the Black Hole exploit kit.

2. Landing Page
After controlling the web traffic, the user's browser loads the codes served from the malicious sites. Then it captures the parameters from the URL, which in turn allows correlating page requests to specific users or groups for redirecting victim. The exploit kit can the find the details of the operating system, browser name and version, and versions of Java, Adobe Reader, and Flash. Using these details, it loads various exploit kits as required.
Components Used for Exploitation
Various exploit kits contain components to exploit:
It is used with embedded Jscript to exploit vulnerabilities.
- Flash
Uses two Flash files; the first file prepare the corresponding JavaScript functions and calls the second file. The second Flash file contains another Flash file as a hex string that is hidden and is actually used for exploit the vulnerabilities.
- Java
Java is the predominant means through which users are affected by the Black Hole exploit kit. The Java contents are loaded via JAR files and Java vulnerabilities are most affected by Black Hole.
Payload
The purpose of Black Hole is to infect victims with malicious payloads; this will vary depending on the licensing. The payloads will be delivered from URLs with the following formats:
[removed]/w.php?f=b6863&e=0
[removed]/w.php?f=19&e=1
The "e" parameter in the query string is used to track the exact vulnerability and can be used to deliver the corresponding payload. This allows the attackers to measure which exploits are most effective for typical combinations of browser and its versions on different operating systems.
Each payload is different from others in the sense that it is packed with custom encryption tools designed to bypass AV detection.
The most prevalent payloads include fake AV (scareware), Zeus, TDSS rootkit, ZeroAccess rootkit, ransomware, etc.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Recommendations and Mitigations
- Ensure that OS and other application programs are up to date.
- Generate user awareness session periodically.
- Ensure that all the latest patches are applied and validated either manually or by using an auto-update mechanism.
- Use a good antivirus system like Symantec Endpoint Protection and keep it up to date.
- Avoid using pirated software.
- Don't click on suspicious links and avoid emails from unknown senders.
- Have a general sense of security and current trends.
- A host-based intrusion prevention system (HIPS) with known algorithms can prevent the Black Hole exploit kit attacks to a point.
References
- https://sophosnews.files.wordpress.com/2012/03/blackhole_paper_mar2012.pdf
- https://community.mcafee.com/community/security/top_threats/blog
- https://resources.infosecinstitute.com/cyber-weapon-of-mass-destruction-the-blackhole-exploit-kit/
- http://nakedsecurity.sophos.com/exploring-the-blackhole-exploit-kit/
- http://blog.malwarebytes.org/intelligence/2013/02/tools-of-the-trade-exploit-kits/
- http://krebsonsecurity.com/2010/08/crimepack-packed-with-hard-lessons/






