AWS Cloud Security for Beginners — Part 1
Introduction to AWS cloud security
Cloud computing has gained enormous attention during the past few years, and a lot of companies are shifting their infrastructure into the cloud environments. With most of the cloud service providers, security comes as a part of their design. Nevertheless, people make mistakes and introduce misconfigurations and vulnerable applications into their cloud environments, leading to various attacks.
In this series of articles, we will discuss various problems related to Amazon Web Services (AWS) due to misconfigurations caused by human error.
Learn Cloud Security
Disclaimer: If you are running any automated scanners or performing attacks against the AWS environment, thus causing disruptions to users or any AWS services, you are completely responsible for your own actions. This series of articles is for educational purposes only.
Why Amazon Web Services?
Amazon Web Services is one of the most-used cloud service providers. The following is a figure showing public cloud adoption in 2017 and 2018.
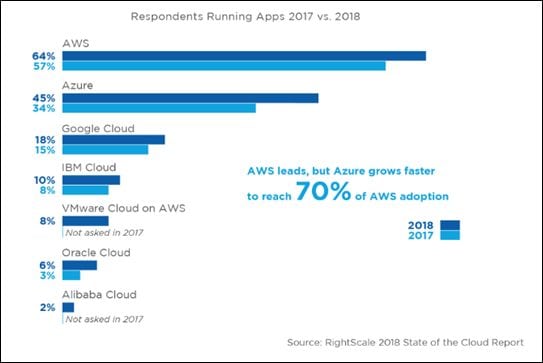
Source: https://www.rightscale.com/lp/state-of-the-cloud?campaign=7010g0000016JiA
With the massive adoption of AWS, its security is obviously a major focus for both administrators and attackers.
The Lab Setup
We will build our own lab setup so that we will be able to understand how the application/infrastructure is built before we look at things from an attacker's angle.
Prerequisites
The following are the prerequisites before proceeding.
AWS Free-Tier Account
As of writing this article, the AWS free-tier account is providing various amazing features for 12 months, free. The only catch is that you need to add your credit or debit card while registering an account.
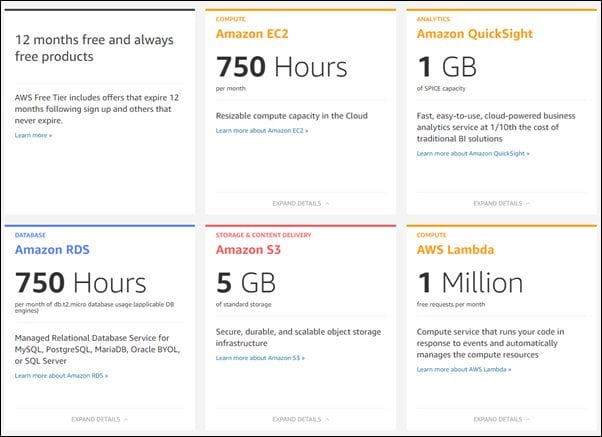
If you have an AWS account, you are good to go. If not, you can simply go and create an account here. After successfully logging in, you can explore various services offered by AWS as shown below.
Laptop with Windows/Linux/Mac OSX
We will use Ubuntu for all our labs in this series, but any other OS should just work fine.
Setting Up AWS CLI
Having AWS CLI set up on your workstation is useful when learning AWS and its security concepts. In fact, it helps you a lot during some of the labs we'll do in this series.
If you are running Ubuntu, you may simply run the following command to install AWS CLI.
sudo apt install awscli
If your installation is successful, you should be able to run awscli commands as shown below.
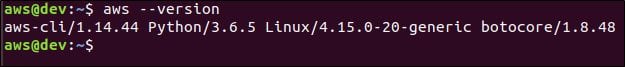
If you are not on Ubuntu, please refer to this for your platform-specific instructions.
Adding a User Profile to Your AWS CLI
Now we have AWS CLI set up on our workstation and we are ready to play. To start with, let's create a new IAM user and add that to AWS CLI so that we will be able to use AWS CLI to talk to our account.
An IAM user account can be set up in three different ways:
AWS management console
AWS CLI
AWS API
We will use the AWS management console for now, as it's the easiest way to get started.
Steps
Log into the AWS management console and navigate to Services | Security, Identity & Compliance | IAM

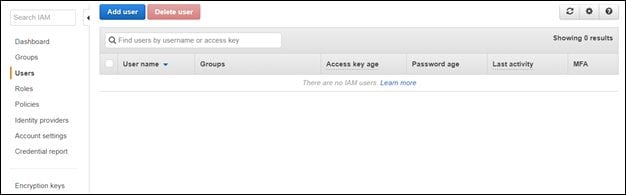
Next, in the left-hand pane click on users as shown below.

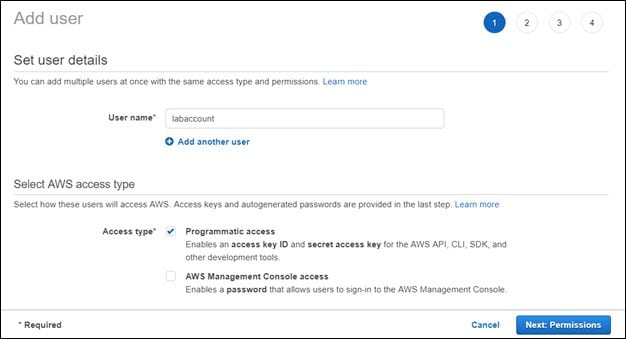
Next, click Add user and enter a username of your choice. We entered labaccount as the username in this case.

Next, click the Next: Permissions button and choose Attach existing policies directly as shown below.
Search for AmazonS3 and check AmazonS3FullAccess for this user. Essentially, we are creating a user account just to perform S3-specific operations only.
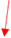

Click the Next: Review button and review all the details.
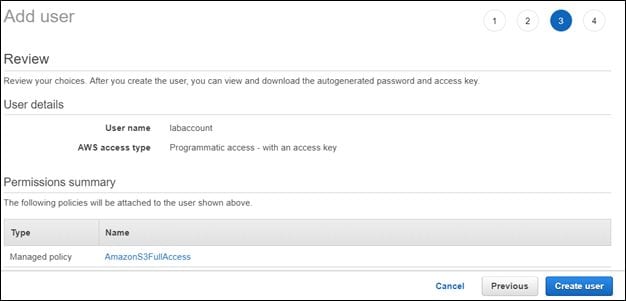
Finally, click the Create user button to get the Access key ID and Secret access key of your user account.
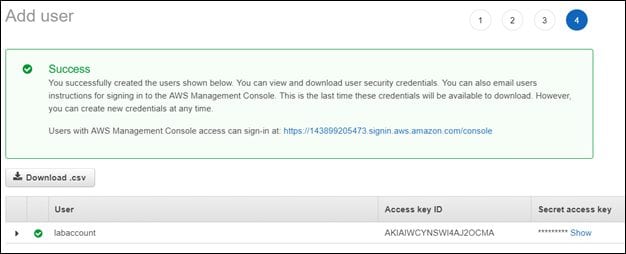
Clicking Show will reveal your secret access key.
If we want to edit the permissions and add some more, such as AdministratorAccess, we can do that as shown below.

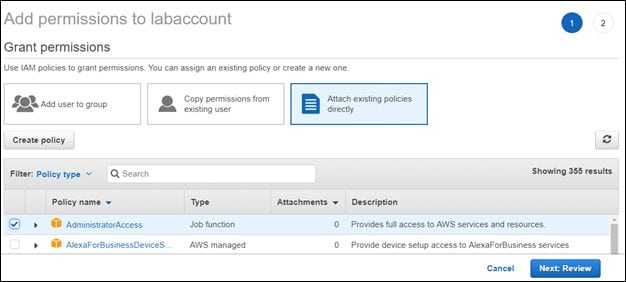
Review and save the changes by clicking the Next: Review button.
Now switch back to your terminal and type the following command:
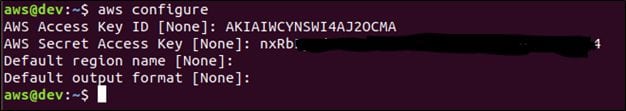
aws configure
You will be prompted to enter the Access key ID and secret access key that we created earlier. Enter the relevant details and press enter. This looks as shown below.
The configured credentials will be available on the machine under the .aws directory. So anyone who has access to this machine with appropriate privileges can access the .aws directory as well as the credentials.
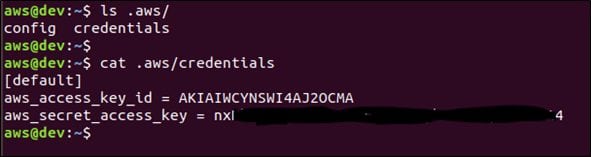
This can be used in post exploitation if this host is compromised.
With the current setup, we are good to go! Now we can get started on learning various AWS services and their security concepts.
Learn Cloud Security
Conclusion
In this article, we discussed why AWS is chosen to learn cloud security, set up a free-tier account, and configured AWS CLI. In the next article, we will discuss S3 buckets and the security concepts associated with them.




