Automated Analysis with Inspeckage
Introduction:
In the previous article of this series, we discussed how to use AndBug to hook into classes and methods of a given Android application. In this article, we will discuss another useful utility called Inspeckage. Inspeckage is an Xposed module, which is useful for performing dynamic analysis of Android Applications. Be it a malware analysis or a penetration test, Inspeckage looks promising with its salient features. Inspeckage also comes with an inbuilt webserver, which can be used to perform everything using a simple and nice GUI.
Setting up Inspeckage:
Inspeckage setup is straight forward if you have already used Xposed Framework earlier.

What should you learn next?
- Download and install Xposed Framework on a rooted device.
-
Next, launch the Xposed application and it looks as shown in the following figure.
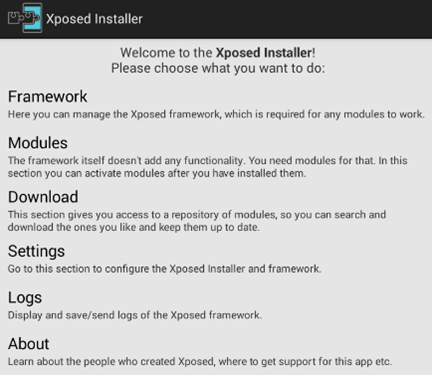
- Tap on Modules button and there should be nothing in here, as we didn't install any modules yet.
-
Now, we can simply download Inspeckage module from the link shown below and install it similar to any other application using adb.
http://repo.xposed.info/module/mobi.acpm.inspeckage
Another way is to use Xposed App's Download option and search for Inspeckage as shown below.
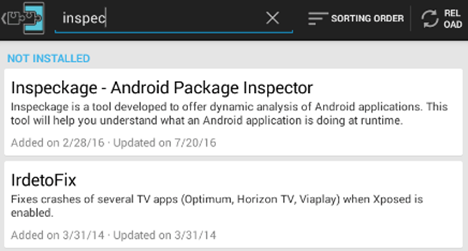
We can tap on the module, and we will be greeted with the following window.
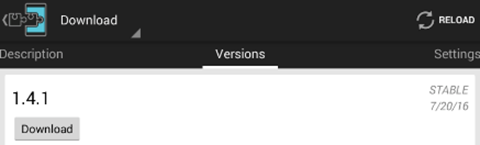
Click "Download" and "Install" button will appear if the download was successful. This is shown below.
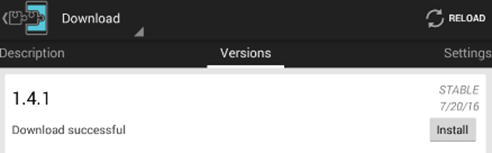
Clicking "Install" button, will install the application. You need to accept the permissions requested by Inspeckage during this process.

The above figure shows that Inspeckage is successfully installed.
-
Now, navigate to the Xposed app and click Modules once again and you should see a new module installed as shown in the figure below.
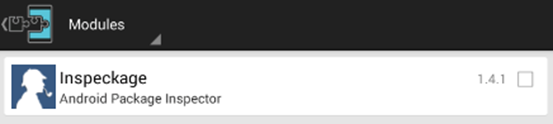
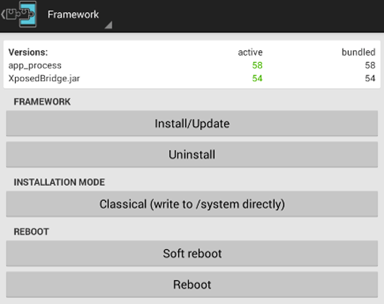
Check the checkbox on the right side of the above picture and perform a soft reboot for the changes to take effect. We can do it by navigating to Framework function in Xposed and tapping on Soft Reboot button. This is shown below.
Finally, we are there! After the reboot, tap on the Inspeckage module under Modules section of Xposed and you should see the following window. Here, we can see the list of applications installed on the device.
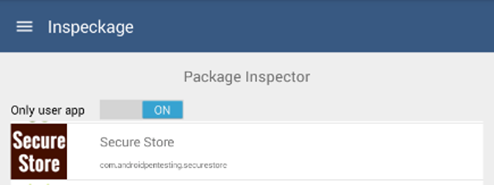
We can also choose the application to be analyzed. I chose an application called "Secure Store," which is an intentionally created vulnerable application by me.
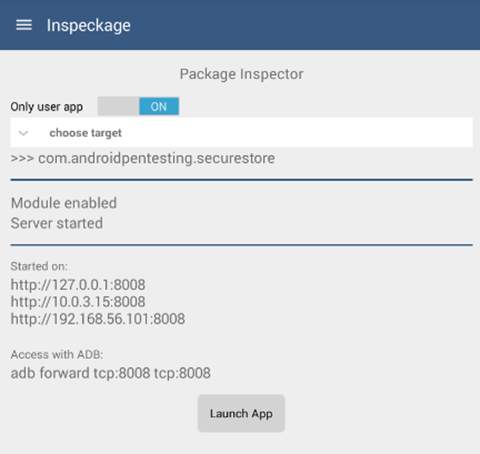
Click "Launch App" and navigate through the full functionality of the application. While running the target application, Inspeckage will monitor the calls being made by the application. We can also hook into the methods by specifying the class name and method name and then observe the arguments being passed and along with the return values. We will see how to do it later in this article.
Additionally, the above window also shows the address, which can be used to access the user interface. This is shown below.
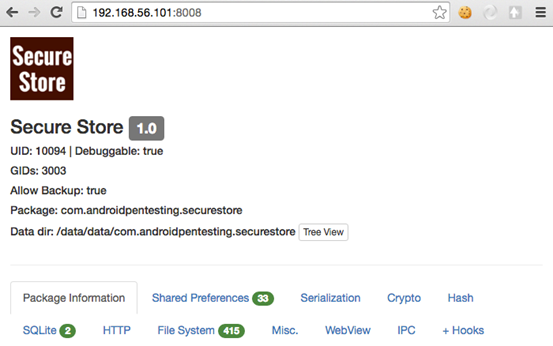
Accessing the user interface will greet us with the results having various sections as shown in the above figure. In the next sections of the article, let us discuss some of the sections that are flagged above.
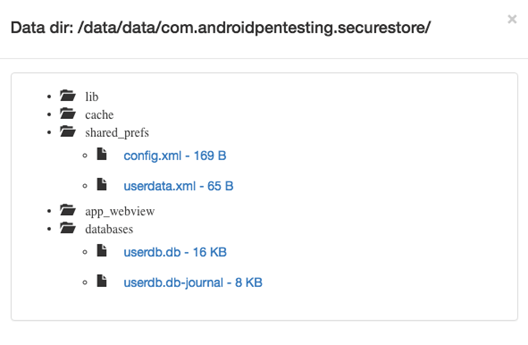
We can see the basic information about the app, which includes backup attribute, package name and data directory location. Interestingly, clicking "Tree View" button will give us a glance of what is available within the application's app directory. This is shown below.
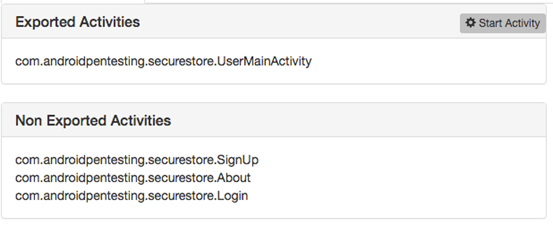
Next, clicking "Package information" section will show us a list of app components used by the application. In our case, we have one exported activity and three non-exported activities. We can also forcibly launch the activities using the "Start Activity" feature available there.
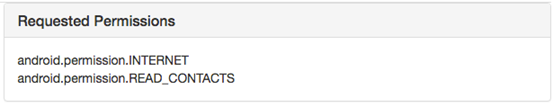
Additionally, we can also see the permissions being used by the application as shown in the figure below.
Next, let us move on to SQLite section. This section shows if there are any SQLite queries executed by the application as shown in the figure below.
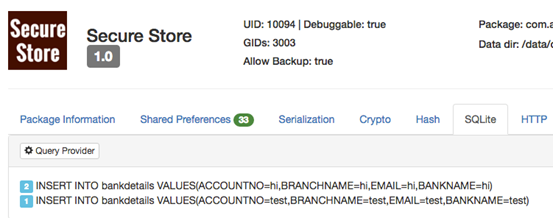
We can also query the content providers using "Query Provider" feature if any providers are available.
The next section that is flagged is "Shared Preferences". Inspeckage shows both read and write calls separately. The following figure shows that the application is storing "auth token" in the userdata.xml file using Shared Preferences.
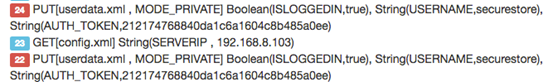
Later, the app is also reading the token stored earlier. This is shown in the figure below as entry 27.

Next, let's navigate to WebView section. Inspeckage also identified that the target application is using WebView addJavaScriptInterface, which acts as a bridge to interact with Java using JavaScript and vice-versa.
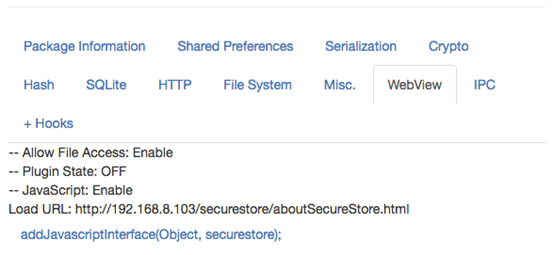
If the app's API level is targeted to less than 17, this remote code execution vulnerability can be exploited.
Adding hooks:
Let's move on to +Hooks tab. This section is an interesting section as we can add hooks to specific methods and monitor what is going when that specific method is run.
Let's add hooks to two different methods in our app and observe how Inspeckage handles it.
Case 1:
We can get the class names and method names by reversing the application. "isUserAlreadyLoggedIn" is a method that appeared interesting while exploring this application's source. Let us add a hook as shown in the figure below.
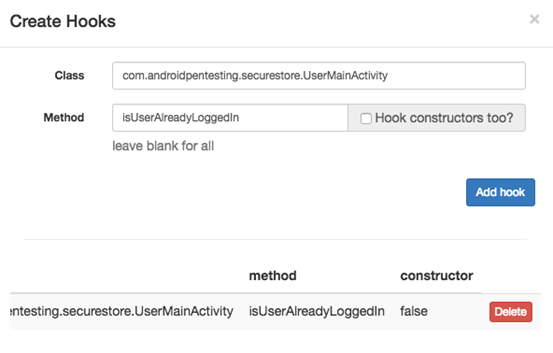
We specified the class name and method name. If you wish to hook the constructors too, you can do it.
Run the application now and if the application invokes this method, you should see the arguments and return value as shown in the figure below.
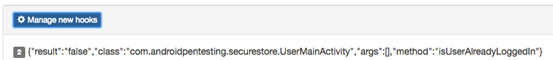
As you can see, the method has returned "false" and it has no arguments.
Case 2:
Now, let's have a look at an example with method arguments. Let's delete the existing hook and add a new one as shown below (you can also have more than one hook at the same time). "isLoggedIn" is the method name this time and please note that the class name is also different.
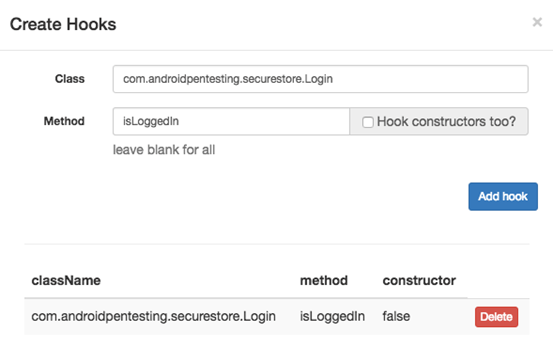
Once done, we need run through the application once again, and we should see the arguments as well as return values.
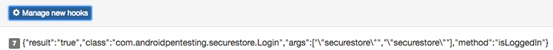
The above figure shows the arguments that are passed to the hooked method. We can also notice that there is a return value "true."
Similarly, Inspeckage can spot issues under other sections if the app has features triggering those calls.

What should you learn next?
Conclusion:
Inspeckage module, without a doubt, is a very useful tool for dynamic analysis of Android Applications. If you are analyzing malware or conducting a penetration test, Inspeckage is a very good choice to speed up your work. Being an Xposed module, the way Inspeckage performs the checks is definitely powerful and reliable as it has full control over the device and the target app it is analyzing.






