An Examination of the Caesar Methodology, Ciphers, Vectors, and Block Chaining
Overview of the Last Article
In today's world, communications of all types and kinds are becoming of utmost importance. Whether it is from personal to professional, the use of the Smartphone and other wireless technologies is becoming an indispensable part of our lives. Just about any application can be accessed from the standpoint of remote connectivity; and because of this, the threats of Cyber based attacks pointed at this regime is becoming an increasing trend.
The hacker of today is obviously becoming very sophisticated towards the types of attacks that he or she can launch within a few seconds. As usual, these are very covert, such as Malware, Adware, and Spyware, which can disrupt these lines of communications without the end user even being aware of it.
Learn Applied Cryptography
The main of intention of these Cyber attackers is, of course, to gain access to the very personal and confidential information/data that we possess; whether it be a personal file or even a file that is used in the workplace. The worst part of it is that the Cyberattacker will take this even one step further and use this to launch Identity Theft attacks at a subsequent point in time.
True, there is no 100% magic solution to cure all of these threats and risks, but there is a tool out there which can help to alleviate much of this. It is known as "Cryptography." As it was reviewed in the last article, this is the "art" of scrambling a message while it is in transit and descrambling it once it arrives at its point of destination. This is just the simplistic view of it; it is much more complex when applied to everyday scenarios.
However, the basic objective is to keep a particular message in this scrambled state, so that even if it were intercepted by a third party, it would be rendered totally useless unless they had the appropriate keys to unlock and decipher at.
The last article also examined these topics
-
Message Scrambling and Descrambling
This examined in more detail about how messages are actually scrambled and descrambled, and a formal definition of Cryptography was provided.
-
Encryption and Decryption
The art of scrambling and descrambling a particular message is technically known as "Encryption" and "Decryption," respectively. Formal definitions of these were provided.
-
Ciphertexts
The scrambled state of a message is also technically known as a "Ciphertext." As it was eluded to before, the sending party must possess the keys to create the Ciphertext, and the receiving party must also possess the keys to descramble it. This is done via a special mathematical formula known as the "Encryption Algorithm" and the "Decryption Algorithm," respectively.
-
Symmetric and Asymmetric Key Systems
These are two types of Cryptographic Systems which are used in applications today; Symmetric Key Systems use only one specific key to scramble and descramble the message; this is called the "Private Key." Asymmetric Key Systems utilizes a pair of keys, called the "Public Key" in addition to the Private Key.
This article continues with the theme Cryptography, with a more in-depth review of Symmetric Key Systems. The topics which will be covered include the following
- The Caesar Methodology
- The Types of Cryptographic Attacks
- Polyalphabetic Encryption
- Block Ciphers
- Initialization Vectors
- Cipher Block Chaining.
Here is a link to a primer article
The Caesar Methodology
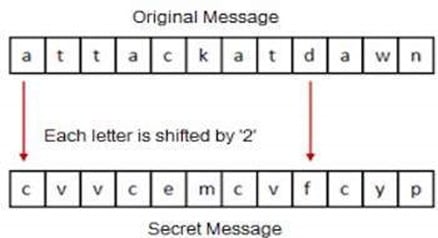
With the Caesar Methodology, each letter of the text or the written message is substituted with another letter of the alphabet that is sequenced by so many spaces or letters later in the alphabet. To make things simpler to understand, we can denote the specific sequencing as "k." So, four letters out into the alphabet, this would be represented mathematically as k=4.
Let us go back again to our example of "I Love You." If k=4, which represents the letter sequencing, the letter that would replace "I" in this plaintext message would be the letter "E." So, continuing in this fashion, the ciphertext would be translated as "E YOUA EIM." With the Caesar Cipher, a technique known as wraparound is possible. Meaning, once the last letter of the Ciphertext is reached in the alphabet (which would be the letter "Z"), it wraps around immediately to the start of the alphabet, with the letter "A."
Thus, if the wraparound technique were needed to finish the encryption of the plain text message, with k=4, the letter "A" in the plaintext message would become the letter "D," and so on. The value of the "k" serves as the key in the Caesar Cipher since it specifies how the plaintext should be encrypted into the ciphertext.
With the Caesar Cipher, some 25 different combinations or key values can be used. An improvement over the Caesar Cipher came with a newer technique known as monoalphabetic cipher. What distinguishes this from the Caesar Cipher is that, although one letter can still be replaced with one another, there is no exact mathematical sequencing that is required.
Rather, the letters in the plaintext can be substituted at random to create the ciphertext. Again, for example, the plaintext message of "I Love You" can be written at will and at random as "UYO VOLI E." With the monoalphabetic cipher, there are more pairings of letters which are possible. For example, there are 10 ^26 possibilities of letter pairings versus only 25 letter pairings available with the Caesar Cipher.
Thus, is a hacker were to attempt a brute force attack on a monoalphabetic cipher (which is just the sheer guessing of the ciphertext for any type of pattern to decipher the plaintext), it would take a much longer time to crack the Caesar Cipher.
The Types of Cryptographic Attacks

However, with both of these Cryptographic methods just described, there are three types of attacks in which they are vulnerable to, and are detailed as follows:
-
Ciphertext-only Attack
With this type of attack, only the cipher text is known to the attacker. However, if this particular individual is well trained in statistics, then he or she can use the various statistical techniques to break the ciphertext back into the plaintext.
-
Known Plaintext Attack
This occurs when the hacker knows some aspect of either of the letter pairings; thus, they can consequently crack the ciphertext back into the plaintext.
-
Chosen-Plaintext Attack
With this type of attack, the hacker can intercept the natural plaintext message that is being transmitted across the network medium. From this, he or she can then reverse engineer it back into its ciphertext form, in an attempt to figure out the specific encryption scheme.
Polyalphabetic Encryption
Over time, improvements were made to both the Caesar Cipher and the Monoalphabetic Cipher. The next step up from these two techniques was another technique known as "Polyalphabetic Encryption." With this, multiple types of Caesar Ciphers are used, but these Ciphers are used in a specific sequence, which repeats itself again when the overall Cipher has reached its logical end the first time to finish the completion of the encryption of the plain text message.
This means that the "Wraparound Technique" is also prevalent in this type of scenario. Let us illustrate this example again with "I Love You." Building upon the example used previously, suppose that two types of Caesar Ciphers are being utilized, such as where k=1, and k=2 (k denotes the actual Caesar Cipher or the sequential spacing of the number of letters later in the alphabet).
The overall Cipher Algorithm utilized is C1 (k=1), C2 (k=2), where "C" denotes the Caesar Cipher. Thus, with the example of using "I Love You," using the Polyalphabetic Algorithm, it would be encrypted as J ORYF BPX. To understand this further, the first letter in the plaintext is C1, so "I" is represented as "J," the second letter of the plaintext is C2, so "C" is represented as "O," and so on.
The logical end of the Cipher Algorithm is C2 once again, and when it reaches the logical end of the first iteration, it then wraps around again as C1 (k=1), C2 (k=2) the second time around, then the third time around, until the plaintext message has been fully encrypted.
So, in our illustration of "I Love You," there were a total of three iterations of C1 (k=1), C2 (k=2), etc. to encrypt the plaintext fully. Over the years, a more modern form of encryption was developed, known as the "Block Cipher." With this method, the plaintext message is put together in one long stream, and from this, it is then broken up into blocks of text of equal value.
Block Ciphers
Block Ciphers utilize a method known as "Transposition," to encrypt the plaintext message. Let us illustrate this again with our example that we have used before, but this time, let us assume a block of three characters, mathematically represented as 3 Bits, or where k=3.
Note that an extra character is added at the end, which is the letter "X." This was added so that a complete plaintext block can be formed. As a rule of thumb, if the total number of characters in the plaintext is not divisible by the block size permutation (in this instance, where k=3), then it can be safely assumed that extra characters will be needed to the plaintext for the last block of plaintext to be considered as complete. This specific technique is known as "Padding." It should be noted that the most widely used block is where k=8 Bits long.
As we can see, even with the simple example from above, Block Ciphers are a very powerful tool for Symmetric Key Cryptographic systems. After all, it goes through a set number of iterations of scrambling to come up with a rather well-protected Ciphertext. However, despite these strong advantages of Block Ciphers, it does suffer from one kind of inherent weakness.
If a hacker discovers it, it can cause rather detrimental damage, with irrevocable results. This vulnerability is that the two blocks of data can contain the exact same data. For example, as it was illustrated, the Ciphertext Block was formulated as OLI YEV XUO. However, of course, it is possible that the Ciphertext Block can contain two or more exact blocks of the same data.
Initialization Vectors
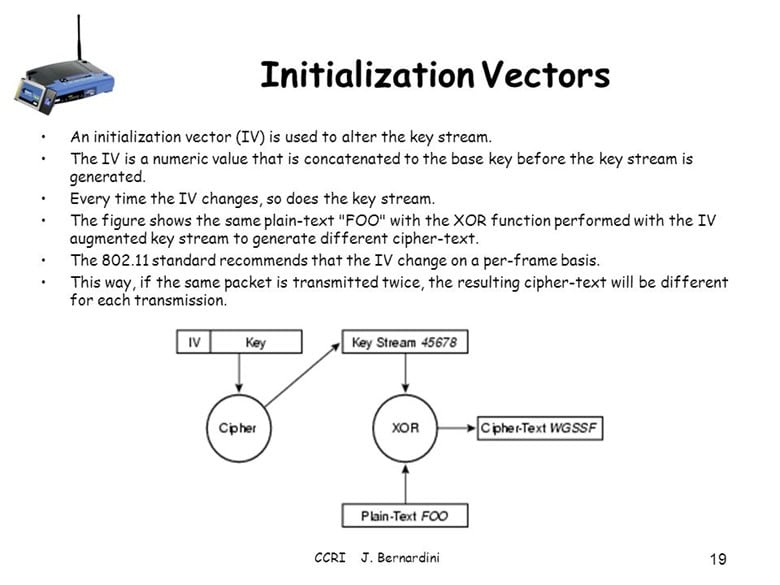
To alleviate this Security vulnerability which is inherent in the use of Block Ciphers, Initialization Vectors (also known as "IVs") are used. Although it may sound complex, it is just the technique of creating some further scrambling or randomness within the ciphertext block itself. However, it should be noted that it is not the Initialization Vectors itself which does not promote the usage of ciphertext blocks.
Cipher Block Chaining
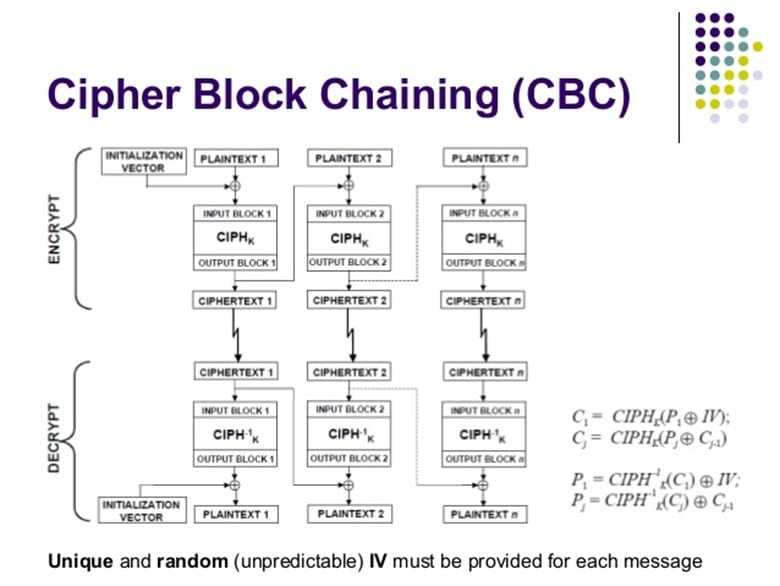
Rather, the Initialization Vectors are part of a much larger process known specifically as "Cipher Block Chaining," or "CBC" for short. From within this methodology, multiple loops of encryption are created to totally further scramble the ciphertext. Here is how this process works
- The Initialization Vector is created first.
- Through a mathematical process known as "XOR" (which stands for eXclusive OR; this is used quite frequently to determine if the bits of two strings of data match up or not), the first created Initialization Vector is XOR'd with the first block of ciphertext data.
- The first chunk of data which has been XOR'd is further broken by another layer of encryption.
- This process is then continued until all of the blocks of ciphertext have been XOR'd and enveloped with another layer of encryption.
Thus, this is how Cipher Block Chaining gets its title. For instance, steps 1-4 a detailed up above creates the first loop or chain, the second loop or chain is then next initiated, and so on, until the ciphertext has been fully analyzed and encrypted by this particular methodology.
Conclusions
Overall, this article has examined some of the more traditional methods of encrypting as well as decrypting information and data which is transit from the point of origin to the point of destination.
Although they may have served their purposes in the past, in today's technological driven world, these methods are simply not sophisticated enough to thwart off the mindset of the Cyber attacker of today.
The Cryptographic methodologies as detailed in this article have their own set of security vulnerabilities, which can be taken advantage of in literally just a matter of seconds. In fact, these specific methodologies fall under the realm of Symmetric Key Cryptography, which is not a secure system to use.
One of the primary reasons for this is that only one pair of Private Keys are used, and if these were to be intercepted, any confidential or proprietary information could be deciphered very quickly.
We continue with the theme of Cryptography into our next article, with an exhaustive examination of Public and Private Keys which are used in an Asymmetric Key Cryptography system.
Sources
http://www.nku.edu/~christensen/092HNR304%20section%202%20caesar%20ciphers.pdf
http://disp.ee.ntu.edu.tw/meeting/%E6%94%BF%E9%8C%A6/Cryptography/Cryptography.pdf
https://www.apprendre-en-ligne.net/crypto/bibliotheque/PDF/Kwang.pdf
http://esatjournals.net/ijret/2013v02/i09/IJRET20130209049.pdf
https://see.stanford.edu/materials/icspmcs106a/26-strings-and-ciphers.pdf
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.402.8295&rep=rep1&type=pdf
http://www.umich.edu/~umich/fm-34-40-2/ch10.pdf
https://www.math.stonybrook.edu/~rtanase/files/Vigenere.pdf
http://www.aaai.org/Papers/FLAIRS/2006/Flairs06-087.pdf
http://www.aaai.org/Papers/FLAIRS/2006/Flairs06-087.pdf
https://engineering.purdue.edu/kak/compsec/NewLectures/Lecture3.pdf
http://www.utdallas.edu/~muratk/courses/crypto07_files/modes.pdf
https://www.cosic.esat.kuleuven.be/ecrypt/courses/albena11/slides/LRK-basics.pdf
http://www.cs.columbia.edu/techreports/cucs-010-04.pdf
http://e-collection.library.ethz.ch/eserv/eth:38650/eth-38650-02.pdf
http://csrc.nist.gov/groups/ST/toolkit/documents/Examples/TDES_CBC.pdf
https://cseweb.ucsd.edu/~mihir/papers/cbc.pdf
http://gauss.ececs.uc.edu/Courses/c653/lectures/PDF/block.pdf
https://www.blackhat.com/presentations/bh-usa-06/BH-US-06-Eng.pdf
https://www.emsec.rub.de/media/crypto/attachments/files/2011/03/hudde.pdf
http://web.cs.ucdavis.edu/~rogaway/papers/modes.pdf
Learn Applied Cryptography
http://luca-giuzzi.unibs.it/corsi/Support/papers-cryptography/sp800-38a.pdf



