5 Commercial Threat-Hunting Platforms That Can Provide Great Value to Your Hunting Party
Introduction
Threat hunting is the process of proactively looking for anomalies within a company’s network or devices and discovering if they represent the trails left by stealthy attackers. This is usually done by having a team of threat hunters, the cybersecurity experts that excel in areas such as malware analysis, pattern recognition, data forensics and data analytics.
While there is no doubt that the hunter is the essential factor in finding threats, it is important to understand that the amount of data that must be collected and analyzed makes it impossible to have an effective process without the help of technology. Threat hunting is done in a continuous loop, where the hunter formulates a hypothesis (e.g. is one of our endpoints remotely controlled by an unknown agent?) and tries to prove it by finding behavior anomalies on the network or existing devices.
Become a certified threat hunter
While data collection and normalization were already done by SIEM solutions, threat-hunting platforms have advanced to the point where it is possible to combine machine-learning techniques and threat intelligence to automate a considerable part of the process, allowing experts to maximize their potential, making sure no threat remains undetected.
But which is the best solution for your company? Here are five well-known commercial threat-hunting platforms that will help you get the most out of your cyberthreat analysts.
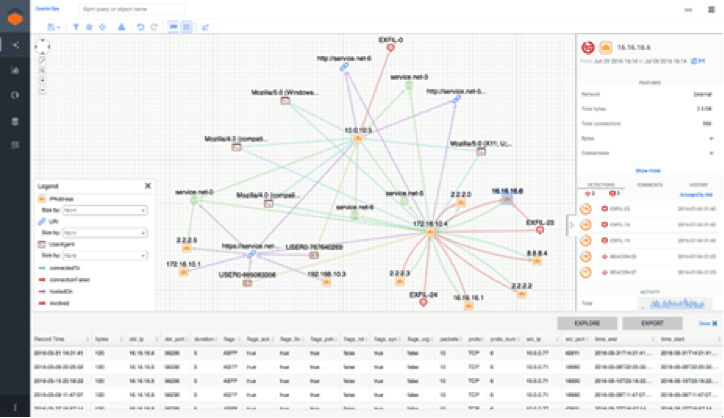
Sqrrl
One of the most mature threat-hunting platforms available, Sqrrl combines techniques such as link analysis, user and entity behavior analytics (UEBA), risk scoring and machine learning, creating an interactive visual chart that allows analysts to explore entities and their relationships. This makes it a simple yet powerful tool for hunters.
Sqrrl can collect data from an internal SIEM solution and outside sources, such as a threat intelligence feed. It does not install an agent on endpoints, but rather uses the data collected from existing endpoint protection solutions.
A strong point for the Sqrrl platform is its interactive visual chart. Hunters have a dashboard showing suspicious behaviors and their severity. It is important to note that the behaviors displayed here can be quite different from the ones that would, for instance, cause an alert on a SIEM solution.
For example, if an administrator logged into a server with valid credentials, there’s no cause for concern … right? Well, while that’s true for most cases, this could be considered an abnormal behavior if this specific user/administrator never logged into this server before. Sqrrl can flag these sorts of abnormalities and alert the hunters so they can launch an investigation. This sort of proactive instance should be considered mandatory for a good threat-hunting solution.
 Mantix4’s motto is “turning the hunted into the hunter.” This is done by using the M4 Cyber Threat Hunting Platform to accelerate the hunting process and actively defend against cyberthreats.
Mantix4’s motto is “turning the hunted into the hunter.” This is done by using the M4 Cyber Threat Hunting Platform to accelerate the hunting process and actively defend against cyberthreats.
As usual for threat-hunting solutions, M4 has two main components: sensors, deployed as needed at critical points throughout the network, and the analytics server, which is hosted in a secure data center run by Mantix4.
The M4 provides an interactive visual interface that is both simple to use and provides meaningful information for hunters. For instance, with a simple right-click on any element, it’s possible to start filtering for abnormal network activity.
Imagine that a server is connecting with an unusual destination, such as a country in which the company does not do any business. From here, a hunter can confirm if the connection is, however unusual, valid or a true symptom of an attack. Is it using a high port not present on other connections? Are there any other hosts from the network making similar interactions with this unknown destination? By responding these questions, the M4 helps the hunter separate a false positive from what may be the setup for a future attack or even an ongoing large campaign from an adversary.
One point that stands out about the M4 platform is that it can also be implemented using an “as-a-service” model that is not limited to the software side, as Mantix4 can also provide a team of experienced hunters to remotely work for any company. If you are in a hurry to start looking for advanced threats and short on skilled personnel, this can be a great differential.
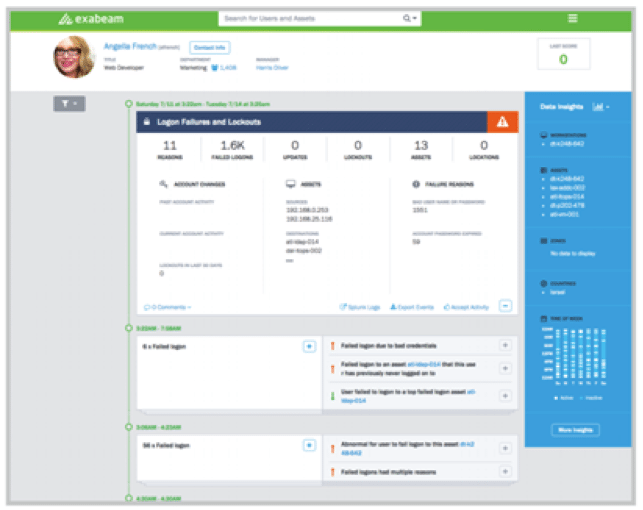
 Exabeam is mostly known for their UBA (User Behavior Analytics) solution, a tool that relies on machine learning to correlate events and identify the users that present risky behavior.
Exabeam is mostly known for their UBA (User Behavior Analytics) solution, a tool that relies on machine learning to correlate events and identify the users that present risky behavior.
Exabeam Threat Hunter complements this functionality by allowing analysts (hunters) to query the same data to match a specific set of criteria. In other words, it is possible for an analyst to drill down into a specific user session and confirm if it is an unusual, but valid, situation or an attack that bypassed conventional detection/prevention solutions.
Exabeam Threat Hunter is designed for cyberthreat analysts on all levels. While traditional threat queries make use the syntax of the SIEM solution, requiring a trained analyst with the right skills, Exabeam provides automatic incident timelines instead of logs and allows for rapid and proactive threat hunting. For instance, it’s possible to select an alert ID or IP address on the platform and create a complete timeline of events, showing how the security incident unfolded and providing a high level of situational awareness.
Most threat-hunting platforms are event-centric, meaning that during a hunt, the event is the stateful object (it never moves or changes) that is analyzed in the context of other events. After that, subjects such as people, programs and processes are taken into consideration and conclusions are drawn. This is where the Exabeam Threat Hunter distinguishes itself: since it focuses on user behavior, the user is the central/stateful object. Actions are analyzed based on the activities from other users, events, the TTPs (tools, techniques and processes) used by attackers, and other factors that help create a context for defining what may be an indicator of malicious activity. Once the user behavior is analyzed, it is scored and threat hunters can use this information for deciding cases where further analysis is required.
As with most good platforms, Exabeam Threat Hunter makes the process of finding a very specific answer that much easier. It’s just a matter of having someone capable of asking the right questions.
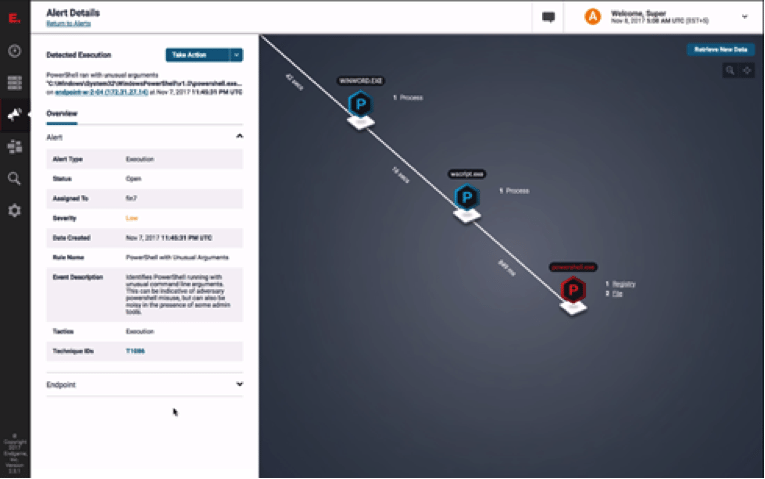
![]() This is another platform that focus on automating the hunt. As part of an endpoint protection platform, Endgame Hunt focuses on stopping advanced attacks and all their components before any damage can occurs.
This is another platform that focus on automating the hunt. As part of an endpoint protection platform, Endgame Hunt focuses on stopping advanced attacks and all their components before any damage can occurs.
Contrary to other solutions, such as Infocyte HUNT, this platform requires the installation of an agent on all endpoints. This allows Endgame to stop processes, delete files and even restrict access to an endpoint as needed. In other words, hunters using this solution are not only able to perform a deep investigation, but if a threat is discovered, they can completely stop it.
It is important to understand that Endgame can also act as a traditional anti-malware solution, detecting and stopping low-level threats on the spot. This however, has nothing to do with the hunting process, as attacks are stopped at this level never get to the Endgame HUNT console, which is reserved for alerting on situations that bypassed traditional security solutions and would be unknown even on an SIEM.
For example, Endgame is able to detect the execution of a PowerShell with “unusual” arguments. If this abnormal activity was executed with a valid/authorized user account, it is up to the hunters to investigate and confirm if it was just a false positive, or compromised credentials used by an adversary.
Endgame features many interesting functionalities, such as being able to perform a complete system memory inspection, identifying in-memory attacks including memory modification, memory injection and hidden modules. This allows analysts to perform instant malicious thread suspension, containing the threat without any loss of system stability.
While Endgame is a great platform for hunting advanced threats on endpoints, it is limited to, you guessed it, protecting endpoints. This excludes some very important aspects of a good threat-hunting process, such as network behavior analysis. So if you are looking for a more complete platform, other solutions such as Sqrrl or Infocyte HUNT will probably better suit your needs.
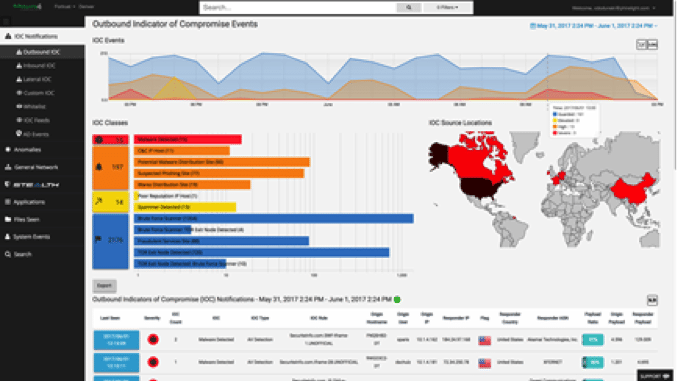
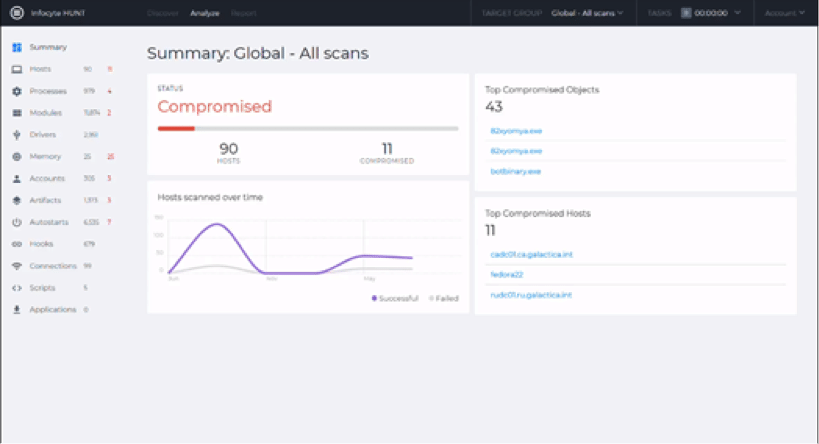
 Infocyte HUNT is an agentless threat-hunting solution. Well, not completely “agentless,” as a central console installs agents on all endpoints. The good news is they only last for about one to three minutes before being dissolved, reducing the impact on analyzed hosts to this very short time period.
Infocyte HUNT is an agentless threat-hunting solution. Well, not completely “agentless,” as a central console installs agents on all endpoints. The good news is they only last for about one to three minutes before being dissolved, reducing the impact on analyzed hosts to this very short time period.
The central HUNT console is also responsible for tasks such as creating dashboards and reports, but the Infocyte platform’s key functionalities rely on cloud components: the File Intelligence Services, which uses multiple intelligence sources (e.g. AV vendors, third-party threat intelligence providers and file reputation services) for aggregating information and data about files and the Digital Forensic Analytics Services, responsible for analyzing unknown or suspicious samples, including aspects such as injected memory, executables, scripts and modules.
Using these combined resources, HUNT is able to spot advanced threats other solutions might miss. For example, a browser executable file — even with a valid hash and no malware detection from standard anti-malware software — can have a bitcoin miner module. While this would have escaped most endpoint protection software, HUNT is able to flag it as abnormal.
The HUNTER platform adopts an approach that is aligned with the central pillar of threat hunting: it assumes that endpoints are already compromised and tries to confirm this hypothesis. Is a host providing remote access? If so, is this remote access allowed? Is there any sign of malware infection? No? Let’s check for avoidance techniques and persistent mechanisms.
According to its vendor, Infocyte HUNTER was developed to be independent, minimally invasive and simple. It is mostly used by information security professionals responsible for tasks such as incident response and vulnerability assessment. In theory, this solution does not require a highly-specialized set of cybersecurity skills, so junior staff can be easily assigned to the simpler hunting tasks and more experienced team members can focus on investigations.
Conclusion
For the last several years, threat hunting has been gaining momentum. And as more and more organizations realize the practical value of enhancing their security teams’ ability to quickly uncover and handle advanced attacks, finding the best platform to get the most out of hunting becomes an essential task.
There should be no mistake: The most important part of an effective threat-hunting process is having an experienced team of hunters, but that’s quite different from saying a threat-hunting solution is not relevant.
In a traditional cybersecurity approach, technical solutions are first deployed and then the security team works to make the most of them. As threat hunting creates a paradigm shift, the idea is now to have a good team of cyberthreat hunters and deploy a platform that will enable you to get the most out of their abilities and experience.
Become a certified threat hunter
While technology advances at incredible speed, it will still take (hopefully) a couple decades before artificial intelligence can outsmart a specialist in areas requiring critical thinking or intuition. Right now, the best approach is understanding that a threat-hunting platform, especially those based on machine learning and advanced algorithms, can have exceptional value in matters such as detecting IOCs or network abnormalities. Provided there is a good network baseline, a proper mix of advanced tools and a team of experts can give any company an effective hunting process.