Windows Systems and Artifacts in Digital Forensics: Part III: Prefetch Files
1. Introduction
In this article, I'm going to focus on prefetch files, specifically, their characteristics, structure, points of interest in terms of forensic importance, uses, configuration, forensic value and metadata.
For part one of the series, which discusses the Windows Registry, please visit: https://resources.infosecinstitute.com/windows-systems-and-artifacts-in-digital-forensics-part-i-registry/
Learn Digital Forensics
For part two of the series, which discusses event logs, deleted data, computer sleep and the erasure of artifacts in Windows, please visit: https://resources.infosecinstitute.com/windows-systems-and-artifacts-in-digital-forensics-part-ii/
Windows Prefetch files first appeared in Windows XP, and their purpose is to boost the startup process of launched applications.
- They include the name of the executable which they accelerate, Unicode itemizations of the DLLs that the executable requires to function, timestamps which pinpoint when the application was last launched, and a counter that keeps track of the times that the executable has been launched, inter alia.
Figure one reveals the four most important elements of a prefetch file in terms of forensic significance.
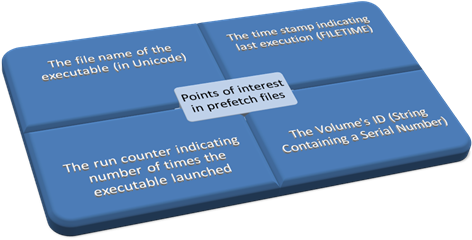
Prefetch files can reveal that an application was actually installed and launched by the suspect at some point in time. Even if prefetch files unveil the presence of a wiping application like "Evidence Eliminator," (a program with the purpose of thoroughly removing selections of data from the hard drive) and nothing else. That's because the actual evidence was destroyed by the wiping application. The mere presence of a wiping application can itself become as incriminatory as the files that were destroyed with it.
2. Basics of Prefetch files
Prefetch filenames have the following naming convention:
{exename}-{hash}.pf
Exename is the name of the executable, hash is an eight character hexadecimal hash of the path from which the executable was launched, and .pf is the file extension. Note that a dash separates the exename from the hash and that the filename ought to be made up of only uppercase characters with the exception of the file extension.
Furthermore, when an application is started from three separate locations on the drive three distinct prefetch files will be created, each corresponding to one of the locations from which the application was run. Prefetching also exists in Windows Vista, where it has been enhanced by SuperFetch, ReadyBoost and ReadyBoot. SuperFetch logs usage scenarios and places resources into the memory before they are requested/ ReadyBoost is a disk cache which boosts processes by utilizing any type of portable flash mass storage system as a cache which enables the OS to service random disk reads with enhanced performance. ReadyBoost's caching doesn't only relate to the page file or system DLLs, but to the whole disk content. In a test case ReadyBoost increased the speed of an operation from 11.7 to 2 seconds. Although simply increasing the main memory from 512MB to 1 GB diminished the length of the operation to 0.8 seconds (without any reliance on ReadyBoost).
Prefetching takes place when the OS (Windows Cache Manager, in particular) is monitoring components of data that is extracted from the hard drive into the RAM. The monitoring takes place on 3 occassions. First, it begins on every system startup and lasts for two minutes of the boot process. Second, it also takes place following the completion of the startup of all Win32 services and lasts for sixty seconds. Finally, it occurs each time an application is launched and lasts for the first 10 seconds of its execution. Subsequently, the Cache Manager, along with the Task Scheduler writes the data into .pf files. These files speed up the system by making themselves promptly available before there is any actual demand for them from the user. Hence, the prefetcher acts as an allocator of data from the hard drive into the main memory before any actual request for it has been made.
Note that SSD drives have Prefetch turned off by default.
3. Prefetching configuration in the Registry
Picture one below reveals the values of prefetching that can be configured in the registry. As it can be seen in the picture, the path to the configuration parameters of Prefetcher is HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerMemory ManagementPrefetchParameters. To configure the Prefetcher, one has to change the value of EnablePrefetcher to one of the values mentioned below and to configure Superfetch, one has to do the same with EnableSuperfetch:
3: Enables Prefetcher/Superfetch for application startup and Boot
2: Enables Boot prefetching
1: Enables Prefetcher/Superfetch for application startup
It can be deduced that cyber-criminals can disable their prefetch and get rid of prefetch files, effortlessly, to remove traces of illegal activity, such as opening an application filled with child pornography on a regular basis, or accessing copyrighted material without the relevant permissions. The only cost is the worsening of the performance of the system.
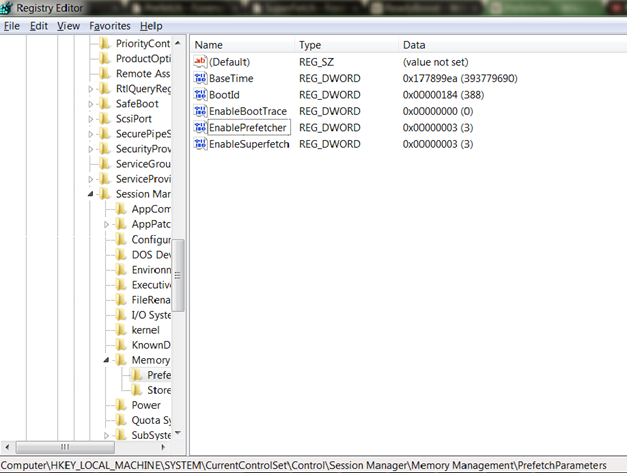
Picture one: Configuration of Prefetcher and Superfetch in the Registry Editor (Windows 7)
Superfetch files begin with the 'Ag' prefix and end with the '.db' extension. The data that is written into Superfetch files is collected by Sysmain.dll, situated in %SystemRoot%/System32, and is a part of the Service Host process (Svchost.exe) which is situated in the same directory. The '.db' files can be found in the %SystemRoot%/Prefetch (usually C:WindowsPrefetch) directory, along with the other prefetch files.
Windows XP, Vista and Windows 7 perform application prefetching by default while Windows 2003 and 2008 are capable of performing prefetching though the feature is turned off by default. Also, every version of Windows, following Windows XP, does boot prefetching.
4. Structure of Prefetch files and metadata
The metadata that prefetch files consist of is of particular relevance to forensic analysts. In Windows XP, the 64-bit time stamp indicating when the executable was last launched has an offset 0x78 within the file, and the counter that pinpoints the number of times the executable has been launched is a 4-byte DWORD value situated at offset 0x90 or 144 bytes. On the other hand, the offset of the last run time stamp is 0x80 in the binary contents of the particular prefetch file, and the "number of times opened" counter is situated at offset 0x98 in Windows Vista and Windows 7 systems.
It's also possible to dig up more data from the metadata of a prefetch file. Inside the prefetch file, there's data revealing the volume from which the executable was started, and strings that show the path to the modules which the executable required to start.
Figure two reveals some key information about the structure of prefetch files:
Table one describes some preliminary characteristics of prefetch files:
Table 1: characteristics

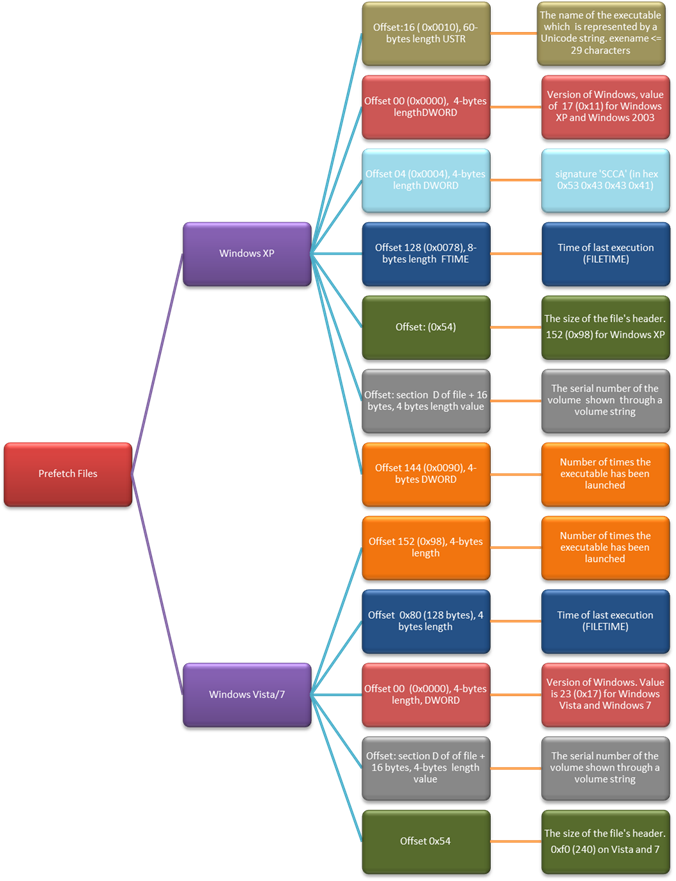
Figure 2 is based on information gathered from David Koepi (http://davidkoepi.wordpress.com/2013/09/29/prefetch-forensic/ and two Forensics Wiki pages( http://www.forensicswiki.org/wiki/Windows_Prefetch_File_Format and http://www.forensicswiki.org/wiki/Prefetch.)
5. Other points of interest in prefetch files
Besides the obvious importance of prefetch files, answering when a certain activity has occurred (via the last execution time), what activity has taken place, how frequently it was performed (via the counter that shows the number of times the executable has ran which increments by one on each launch) prefetch files may reveal obfuscated directories. For instance, let's say a prefeteched executable has been executed fifty times (notepad.exe). By examining the prefetch file, one can see the file path of the files that triggered this execution, (let's say you stumble upon list6.txt) which is situated in a TrueCrypt volume. As TrueCrypt enables users to conceal directories, it's vital to examine the paths enumerated in the prefetch files, as these may be a door towards a data source that would have not been otherwise identified. If the examiner didn't look at the paths, they may have never identified the obfuscated directory with the C:WindowsSystem32Neohiddencreditcardslist6.txt path hidden with TrueCrypt. Because the System32 directory is filled with programs that are in use by the OS, and an ordinary person would have never checked its contents.
Additionally, the full directory path enumerated in the prefetch file reveals the user accounts under the Users directory (for Windows Vista/7) and the Documents and Settings directory for Windows XP. An examination may unveil that there was a temporary account created with the purpose of performing criminal activity by pinpointing applications that were launched at some point in the past. It could be by an unauthorized or abnormal user, which would be an answer to the "who" question of an investigation.
Furthermore, by examining the full paths enumerated in the prefetch files, one may see whether the program, application or file was launched from an external storage device as the entry would differ from the entry of an application accessed from the hard drive. Thereafter, the last execution time may be utilized for coordination with the USBStor registry key and if the time stamps match the USBStor registry key entry can be examined to get the serial number of the external storage device and this will aid in solving the "what" and "why" questions surrounding an investigation.
When cyber criminals infiltrate a system and modify the timestamps of an application, they could be unaware of the data that prefetch files contain. If the cyber criminal alter the SIA and FNA time stamps in the Master File Table to hinder the examination. The entries in the prefetch files would remain unchanged and will pinpoint the real time stamps. In that way, examiners may thoroughly avoid the cybercriminal's time stomping attempts. The Master File Table (MFT) is a file that the NFTS file system contains. The MFT has no less than one entry per file on the NFTS file system volume, it even has an entry for itself. These entries include data about each file such as the file's size, permissions, contents and time and date stamps. The metadata is kept in one of two places:
Thus, it's no wonder why time stomping efforts aimed at the MFT is important. It's an enormously large collection of valuable metadata. The prefetch files need to be examined to determine if there were possible time stomping attempts.
6. Summary and Conclusion
To put it in a nutshell, prefetch files are designed to boost the speed of the system. In computers, the saying "speed kills" must be transformed into a negation, which becomes something like "the absence of speed kills." Prefetching can be disabled and enabled as much as one wants, and each time the contents of prefetch files reset. Besides their primary purpose, prefetch files are useful for forensic examiners because they can prove that an application was installed and started on a particular machine. They can pinpoint the time when it was opened and how many times it was opened. They can reveal from which volume it ran and which modules the application loaded. Furthermore, prefetch files may also reveal any hidden or obfuscated directories, temporary, unauthorized or any other abnormal accounts. They may expose any external storage devices and they can pinpoint if there was time stomping.
Therefore, prefetch files help examiners answer the "who", "what", "why", "when," and "where" questions that surround any digital or non-digital investigation. That certainly means that their analysis is of utmost importance.
Figure three reveals the questions asked whenever a crime has to be investigated. That highlights the importance of prefetch files for solving cyber crimes, as a source of answers to these questions.
Learn Digital Forensics
References:
- Forensics Wiki, 'Prefetch', 21 Oct 2013. Available at: http://www.forensicswiki.org/wiki/Prefetch
- Forensics Wiki, 'SuperFetch', 3 Sept 2013. Available at: http://www.forensicswiki.org/wiki/SuperFetch
- Ryanmy, 'Misinformation and The Prefetch Flag', 25 May 2005. Available at: http://blogs.msdn.com/b/ryanmy/archive/2005/05/25/421882.aspx
- Wikipedia, 'ReadyBoost', 17 Oct 2013. Available at: http://en.wikipedia.org/wiki/ReadyBoost
- Wikipedia, 'Prefetcher', 13 Oct 2013. Available at: http://en.wikipedia.org/wiki/Prefetcher
- Forensics Wiki, 'Windows Prefetch File Format', 21 Oct 2013. Available at: http://www.forensicswiki.org/wiki/Windows_Prefetch_File_Format
- David Koepi, 'Prefetch Forensic', 29 Sept 2013. Available at: http://davidkoepi.wordpress.com/2013/09/29/prefetch-forensic/
- Mark Wade, 'Decoding Prefetch Files for Forensic Purposes, Part 1', 12 Aug 2010. Available at: http://www.dfinews.com/articles/2010/12/decoding-prefetch-files-forensic-purposes-part-1
- Windows Dev Center, 'Master File Table', 10 Dec 2013. Available at: http://msdn.microsoft.com/en-us/library/windows/desktop/aa365230(v=vs.85).aspx
- Cory Altheide and Harlan Carvey, "Digital Forensics with Open Source Tools", 2011
- John Sammons, "The Basics of Digital Forensics", 2012





