Windows Cryptography API
Microsoft Windows provides a sleek API for cryptographic purposes. It is a generic interface for accessing cryptographic services provided by Microsoft Windows operating system.
CryptoAPI is meant to be used by developers of Windows-based applications that may alter users to form and exchange documents and alternative information in a very secure setting, particularly over nonsecure media like the net. Developers ought to be aware of the C and C++ programming languages and also the Windows programming.
Learn Applied Cryptography
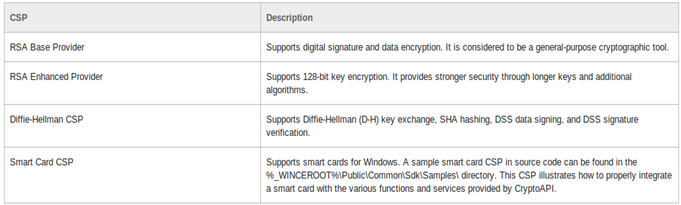
It consists of basic classes and methods that can be used in your C/C++ program to encrypt and decrypt data. WinCrypt API basically consists of providers. Providers are simply algorithms that are provided by the API .
First, let's understand about a little bit about cryptography.
Cryptography is the science of writing secret code; the first documented use of cryptography in writing dates back to circa 1900 B.C., when an associate degree Egyptian scribe used non-standard hieroglyphs in associate degree inscription. Some experts argue that cryptography appeared ad lib once writing was invented, with applications ranging from diplomatic missives to war-time battle plans. It is no surprise, then, that new varieties of cryptography arrived shortly after the widespread development of computer communications. In knowledge and telecommunications, cryptography is critical once communication is made over any untrusted medium, which includes reference to any network, particularly the Internet.
Within the context of any application-to-application communication, there is a square measure of some specific security needs, including:
Authentication: the process of proving one's identity. (The primary varieties of host-to-host authentication on the Internet nowadays is square measure name-based or address-based, each is notoriously weak.)
Privacy/confidentiality: ensuring that no one can scan the message except the intended receiver.
Integrity: assuring the receiver that the received message has not been altered in any approach from the first.
Non-repudiation: a mechanism to prove that the sender sent this message.
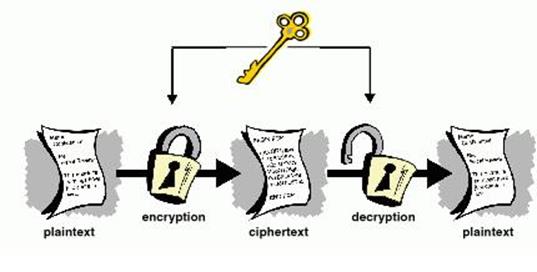
Cryptography, then, not only protects knowledge from thieving or alteration, but also may be used for user authentication. There are, in general, three styles of cryptographic schemes generally wont to accomplish these goals: secret key (or symmetric) cryptography, public-key (or asymmetric) cryptography, and hash functions, each of that is described below. In all cases, the initial unencrypted knowledge is brought up as plaintext, then encrypted into ciphertext, which can in turn (usually) be decrypted into usable plaintext.
In many of the descriptions below, two communication parties are brought up as Alice and Bob; this is often the common terminology within the crypto field and literature to make it easier to identify the communication parties. If there is a third or fourth party to the communication, they'll be brought up as Carol and Dave. Mallory is a malicious party, Eve is an associate degree auditor, and River is a trusty third party.
The three sorts of algorithms which will be discussed are:
- Secret Key Cryptography (SKC): Uses a single key for both cryptography and decoding.
- Public Key Cryptography (PKC): Uses one key for cryptography and another for decoding.
- Hash Functions: Uses a mathematical transformation to irreversibly "encrypt" info.
Using CryptAPI
We will be discussing the following Algorithms using CryptAPI:
- MD5 hash algorithm
- RSA encryption algorithm
MD5 Hash Algorithm
The MD5 algorithm is a scientific cryptographic algorithm that takes associate input of variable length and produces a message digest that's 128 bits long. The digest is typically additionally called the "hash" or "fingerprint" of the input. MD5 is employed in many situations where a probably long message needs to be processed and/or compared quickly. The foremost common application is the creation and verification of digital signatures.
MD5 was designed by well-known researcher Ronald Rivest in 1991. In 2004, some serious flaws were found in MD5. The complete implications of those flaws has nonetheless to be determined.
All the definitions related to API are provided in the wincrypt.h Windows header file.
We will be starting by initializing the variables related to providers, which in this case is:
[plain]
HCRYPTPROV hCryptProv;
HCRYPTHASH hHash;
CString &Cmd5Capi::GetDigest(void)
{
}
[/plain]
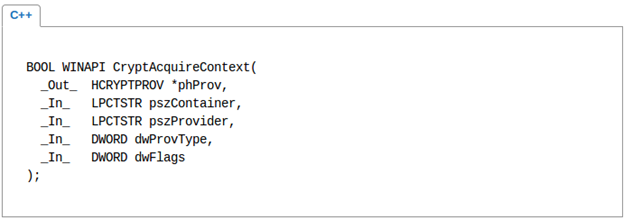
We need to initialize the provider service by using the following function. The prototype of the function goes like this:
Proceeding that, we need to set the hash stream in order to get the hash of the data we need. For that purpose, CryptCreateHash function can be used:
[plain]
CryptCreateHash(hCryptProv, CALG_MD5,0, 0, &hHash);
Further, to get the hash and verify the return code:
[plain]
if(CryptGetHashParam(hHash, HP_HASHVAL, bHash, &dwHashLen, 0))
{
// Make a string version of the numeric digest value
csDigest.Empty();
CString tmp;
for (int i = 0; i<16; i++)
{
tmp.Format("%02x", bHash[i]);
csDigest+=tmp;
}
else csDigest=_T("Error getting hash param");
RSA is the most commonly used encryption algorithm. It is a type of asymmetric algorithm. It uses public and private key. The following mathematical axiom defines the algorithm:
m = D sk (E pk (m))
m = cd mod n AND c = me mod n <=>
The RSA algorithm supports CBC mode, which means the data to be encrypted will be divided into blocks and then encrypted. In our example, we will be encrypting the data in CBC mode.
[plain]
CryptAcquireContext(&hProv, NULL, MS_DEF_PROV, PROV_RSA_FULL, 0);
CryptAcquireContext(&hProv, NULL, MS_DEF_PROV, PROV_RSA_FULL, CRYPT_NEWKEYSET);
As said earlier, we need a key to encrypt data, so for that purpose we will generate a key.
[plain]
CryptImportKey(hProv, pbBlob, cbBlob, 0, 0, &hSessionKey);
The handle will be stored in hProv. To generated a key out of that handle, the following function can be used.
[plain]
CryptGenKey(hProv, CALG_RC4, CRYPT_EXPORTABLE, &hSessionKey);
And the following function can be used to encrypt:
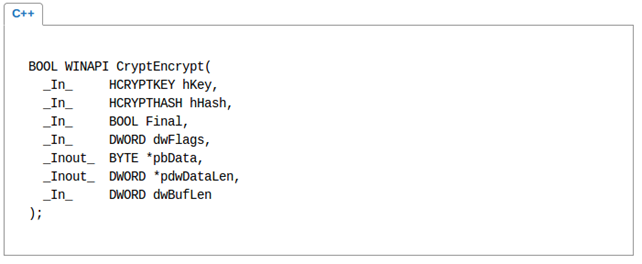
Learn Applied Cryptography
[plain]
CryptEncrypt(hSessionKey, 0, TRUE, 0, cipherBlock, &length, length)



