Tracking Attackers with a Honeypot - Part 2 (Kippo)
Introduction
Unauthorized access to servers occurs on a daily basis. Attackers are constantly searching the Internet for servers that they can use for malicious activity. An easy target for an attacker is a server on which an administrator has set up a service which allows users to control the server remotely but has a weak password set. An attacker aiming to find such a server will scan network ranges, probe the service's specific TCP port and try to connect to the service. Whenever a service is found, the attacker will try to authenticate to the service by guessing user credentials. This process is often automated by a program called a scanner, which can do a dictionary attack or brute force attack on the service. After a successful login attempt, the attacker can use its credentials to login to the server and install his malware.
Learn Incident Response
To study the activities of attackers on a compromised server, one can setup a honeypot server. A honeypot could, for instance, emulate a remote login service and will log all interactions with an attacker. Honeypots are often deployed within particular IP ranges to attract attackers looking for vulnerable targets in specific networks.
FILL OUT THE FORM BELOW TO DOWNLOAD THE CODE ASSOCIATED WITH THIS ARTICLE
[download]
Secure Shell Honeypot (Kippo)
A common way to provide remote shell access on an operating system is using the Secure Shell network protocol. By using the SSH protocol one can perform a secure remote login over an insecure network to access a remote shell. In order to login to the remote shell, the user has to successfully authenticate itself to the SSH server. An attacker can authenticate itself by getting the password from a dictionary attack or brute force attack.
In order to study the activities performed by attackers after they compromised a system with an SSH server, we can use a Kippo honeypot. Kippo is a medium interaction SSH honeypot designed to log all brute force attacks and, most importantly, the entire shell interaction performed by the attacker. It has a fake filesystem, simulating a Debian Linux server, and that is what the attacker sees on login. They can navigate around, but can't do any real damage.
Kippo allows an attacking entity to attempt a login to the system, believing it is entering into a legitimate SSH session with the server. Upon successful guessing of the password, the attacker is then moved into a fake system with which they can interact. In this fake system, all interactions with the shell are monitored and recorded. The system also allows the use of wget and other commands commonly used to fetch or download files, and manipulate it on the "compromised host" as well as a base set of utilities. It saves the files downloaded with wget for later investigation.
In essence, through effective mimicry it is able to allow an attacker to log in and interact with what they think is a real, compromised host. Kippo is independent from the operating systems as it is implemented in Python.
The main objective of the implementation is to bring to the attacker the impression of navigating the real system. IT security can give a view on the basis of the command given by him - for what purpose it was hacked, which data the attacker was trying to get, and what techniques were used. Undoubtedly, it is also a source of learning how the administrator in the near future should strengthen the system.
Some interesting features that Kippo provides:
-
Fake filesystem with the ability to add/remove files. A full fake filesystem resembling a Debian 5.0 installation is included.
-
Possibility of adding fake file contents so the attacker can 'cat' files such as /etc/passwd. Only minimal file contents are included.
-
Session logs stored in an UML compatible format for easy replay with original timings.
-
Stores all the files that were downloaded during the SSH session (simulating wget and curl commands) for later inspection.
-
Stores information about the attacker's behavior in the operating system (commands that were invoked) in a format allowing to replay it in a screen-cast form.
-
Simulates finishing of the SSH session – the honeypot does not really stop the connection but provides another shell-like environment for gathering additional data about the attacker's behavior, i.e exit doesn't really exit, etc.
Once you navigate into Kippo's directory in honeydrive, you will see:
![]()
Most notable directories and files of Kippo are:
-
Data - Directory for miscellaneous data files, such as the password database.
-
fs.pickle - File in the Python pickle format containing the virtual file system.
-
dl - This is a default directory where Kippo will store all malware and exploits downloaded by hacker using the wget command.
-
kippo.cfg - Kippo's configuration file.
-
honeyfs - This directory includes some files which will be presented to attacker.
-
Txtcmds - Directory for creating simple commands that only output text.
-
log - Default directory to log attacker's interaction with the shell and where log files are saved.
-
start.sh - This is a shell script to start Kippo.
-
utils - Contains various Kippo utilities, from which most notable is playlog.py, which allows you to replay the attacker's shell session.
Kippo File System
Kippo stores its file system in a pickle file.
Pickle is the standard mechanism for object serialization. Pickle uses a simple stack-based virtual machine that records the instructions used to reconstruct the object. A pickle file is kind of like a partial memory dump that allows you to easily write objects to the hard disk in binary format. You can then easily read the object into memory at a later point.
Every time a new user connects to the honeypot, Kippo loads the file system into memory. The attacker can do whatever they want to the file system, but when the next person logs in, Kippo loads the pristine file system pickle file. That way everyone starts fresh.
Working
Kippo is absolutely simple to get started in HoneyDrive. To start Kippo, open a terminal and navigate to /honeydrive/kippo/ and run start.sh. That's it. You are now running an SSH honeypot.
![]()
For testing, we use the BackTrack machine. Open the terminal on the machine and type the following command to login on our honeypot server:
![]()
After entering the command it shows the warning that the system can't identify the authenticity of the host. Press yes, after entering the password, we are in. The default password for Kippo is 123456.
As you see in the above result, the attacker will be able to log in to our server, but only to the fake file system. From here, he can do all interactions like creating and deleting files or folders.
To add a new fake user into the Kippo SSH honeypot, an attacker cannot simply use the useradd command within the honeypot. However, the useradd command provides a more interesting feature. It tries to collect all the personal essential information about the attacker.
![]()
Alternative root passwords
In the file "/honeydrive/kippo/data/userdb.txt" you can set the username/password "allowed" to get access to the fake system. You could set the password to whatever you want to allow the hacker get access to.
![]()
To add a new user, we have to append new username and password combination into the data/userdb.txt file. Similarly, if a successful login is done by attacker, an attacker has to launch a passwd command and the new password will be appended to the file directly.
![]()
Below is the updated userdb.txt file of Kippo honeypot.
![]()
Hostname
The default Kippo hostname is svr03. If you want to use some real name ex. banking- server, edit the kippo.cfg file and change the hostname. Go to your Kippo directory and edit file kippo.cfg. Find the following line and change hostname as per your convenience.
![]()
When the attacker tries to connect via SSH on your server, he will be presented with the hostname Banking-Server.
Change OS name:
To change the OS name go to the Kippo directory and edit file /etc/issue. Change the OS name as per your liking.
![]()
There are some great ways to monitor Kippo with custom made scripts. To see graphical statistics from Kippo we can use Kippo-graph. Kippo-graph is a full featured script to visualize statistics from a Kippo honeypot. We can view Kippo stats via web browser by visiting http://localhost/kippo-graph.
![]()
Above, you see the start screen for Kippo-Graph. Kippo-Graphs follows incredibly detailed information. Kippo-Graph currently shows following charts:
-
Top 10 passwords attempted
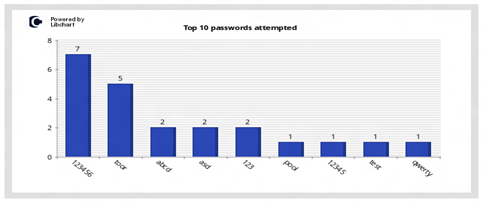
This vertical bar chart displays the top 10 password that attackers try when attacking the system.
-
Top 10 usernames attempted

This vertical bar chart displays the top 10 usernames that attackers try when attacking the system.
-
Top 10 username-password combinations (bar chart & pie chart)
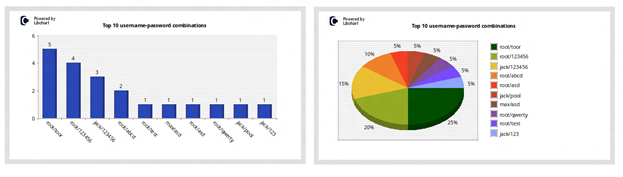
These bars display the top 10 username and password combinations that attackers try when attacking the system.
-
Success ratio
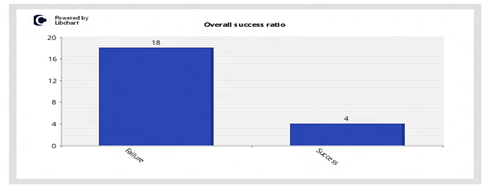
This vertical bar chart displays the overall attack success ratio for the particular honeypot system.
-
Successes per day
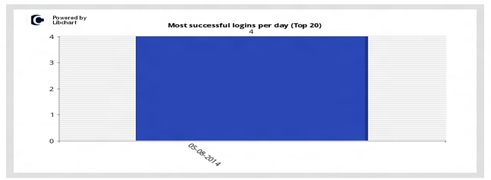
This vertical bar chart displays the most successful break-ins per day (Top 20) for the particular honeypot system. The numbers indicate how many times correct credentials were given by attackers.
-
Number of connections per unique IP (bar chart & pie chart)
![]()
These charts displays the top 10 unique IPs ordered by the number of overall connections to the system.
-
Successful logins from same IP (Top 20)
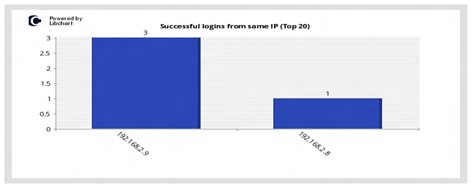
This vertical bar chart displays the number of successful logins from the same IP address (Top 20). The numbers indicate how many times the particular source opened a successful session.
-
Most probes per day (Top 20)
The vertical bar chart visualizes the top 20 busiest days of real human activity, by counting the number of input to the system.
-
Probes per day/week
This displays the most probes per day/week (Top 20) against the honeypot system.
-
Top 10 SSH clients
![]()
This displays the top 10 SSH clients used by attackers during their hacking attempts.
-
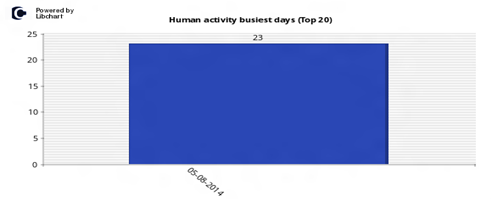
Human activity busiest days (Top 20)
This chart visualizes the top 20 busiest days of real human activity, by counting the number of input to the system.
-
Human activity per day/week
These charts visualize real human activity per day/per week, by counting the number of input to the system for each day of operation.
-
Top 10 input (overall)
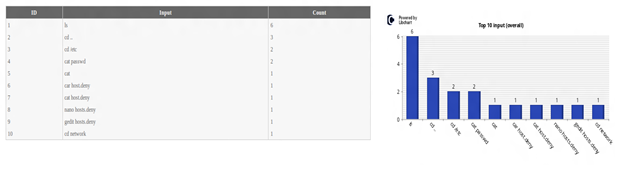
This table and chart displays the top 10 commands (overall) entered by attacker in the honeypot system.
-
Top 10 successful input
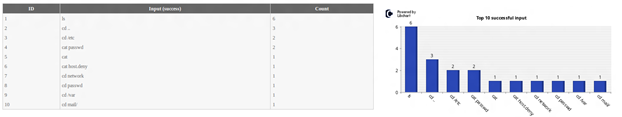
The table and chart displays the top 10 successful commands entered by attacker in the honeypot system.
-
Top 10 failed input
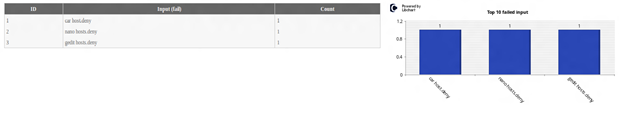
The table and chart displays the top 10 failed commands entered by attacker in the honeypot system.
-
wget commands

The above table displays the latest "wget" commands entered by attackers in the honeypot system.
-
Executed scripts

The above table displays the latest executed scripts by attackers in the honeypot system.
-
Number of connections per unique IP (Top 10) + Country Codes (bar chart & pie chart)
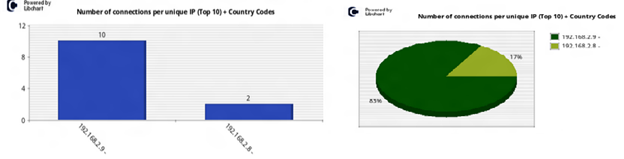
These bar and pie chart visualizes the top 10 IPs ordered by the number of connections to the system. Notice the two-letter country code to after each IP get a quick view of the locations where the attacks are coming from.
-
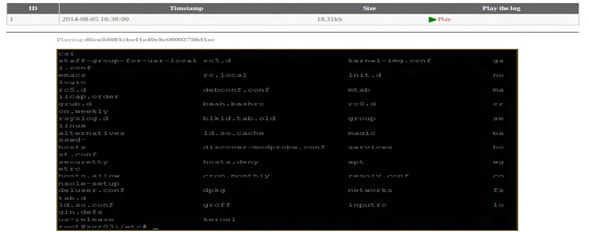
Replay input by attackers captured by the honeypot system
-
Geolocation information gathered from the top 10 IPs probing the system
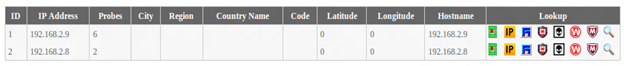
The table displays the top 10 IP addresses connected to the honeypot system.
-
IP activity gathered from the honeypot system
![]()
-
Graph – Gallery
![]()
In this table, you can see all the images in this single page with the help of fancy box.
Kippo-Malware in HoneyDrive is a Python script that will download all malicious files stored as URLs in a Kippo SSH honeypot database. This is useful in situations where you have lost your files or something happened to your server but you still have your DB intact. The script also supports HTTP proxy usage to cover your IP address from malicious servers and custom User-Agent values.
![]()
Pipal is a tool for quickly and easily analyzing password trends across many passwords.
Pipal is a password analysis tool that gives relevant statistics of passwords given a password dump. We can use this tool to analyze passwords gathered by Kippo.
Pipal is completely self contained and requires no gems installing.
![]()
Recognition Kippo
The biggest disadvantage of the honeypot is that it simulates the system, but does not provide the full environment. An example that may overlook the administrator command is ./ where the normal system behavior looks like this:
![]()
A virtual shell behaves like this:
![]()
Advantages of using Kippo
Kippo first of all gives a little time response to an intrusion attempt and reconnaissance with whom we are dealing. A skilled person probably detects the honeypot, but this would deter script kiddies and inexperienced hackers. Incredible added value is the log analysis linking wget, where the administrator can be a real exciting treasure trove of knowledge to the script. In addition, Kippo stores information about an attacker's behavior in the operating system in a format allowing replaying it in a screen-cast form.
Conclusion
Kippo seems to be a nice and easy to configure SSH honeypot. Kippo will help you learn greatly how someone is trying to attack your network, what information they know or are using to try and gain access, and possibly what their intentions are.
Kippo is great at some things and not great at others. It is great at being easy to set up and at emulating a real SSH session. Another thing that is phenomenal is its ability to play back an attacker's actions including all of their typos. Kippo is vulnerable to some DOS attacks, as there are no limits on how many people can connect to it, or how many files they can download.
Learn Incident Response
Reference
- https://www.digitalocean.com/community/tutorials/how-to-install-kippo-an-ssh-honeypot-on-an-ubuntu-cloud-server
- http://blog.donovanhubbard.com/2013/10/customizing-kippo-ssh-honeypot.html
- http://edgis-security.org/
- http://www.unixmen.com/kippo-ssh-honeypot-monitor-brute-force-attacks-debian-7-ubuntu-13-10/
- http://www.delaat.net/rp/2011-2012/p26/report.pdf
- http://bruteforce.gr/



