Skype Forensics

Skype is an application that enables voice and video calls, instant messaging, file transfers, and screen sharing between users. Millions of people download and use Skype everyday for voice and video calling, messaging, sharing and low-cost local and international calls.
Learn Digital Forensics
If you have a Microphone and Speakers, you can use Skype to call people that have Skype. Skype also has an Internet connection box, so that you can convert your regular telephone to use the internet for your telephone service.
As forensics perspective it can give us a lot of information which can be present as evidence in court of law.
Need of Computer Forensics in today's world:
In this high-tech world variety of computer crimes that take place. There are various computer crimes took place on small scale as well as large scale. The loss caused is dependent upon the sensitivity of the computer data or the information for which the crime has been committed. So the computer forensics has become a vital part in the corporate world. There can be theft of the data from an organization in which case the organization may sustain heavy losses. For this purpose computer forensics are used as they help in tracking the criminal.
There are many tools that can be used in combination with the computer forensics to find out the geographical information and the hide outs of the criminals. The IP address plays an important role to find out the geographical position of the terrorists. The security personnel deploy the effective measures using the computer forensics. The Intrusion Detecting Systems are used for that purpose.
So In this article we are going to perform forensics analysis of Skype application.
Show Time: First we will start from the Skype's file location
- Linux: ~/.Skype/SKYPE-USER/
- Windows XP and previous: C:Documents and SettingsWINDOWS-USERApplication DataSkypeSKYPE-USER
- Windows Vista and later: C:UsersWINDOWS-USERAppDataRoamingSkypeSKYPE-USER
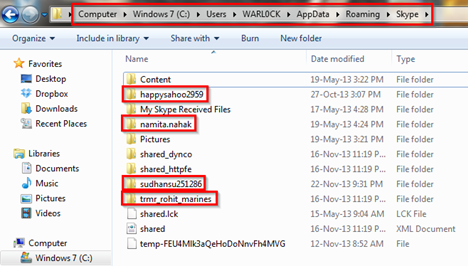
We are in the Skype directory and we can see the four red box marked directories are: happysahoo2959, namita.nahak, sudhanshu251286, trmr_rohit_marines. These four directories are users directory who are using Skype in this system. As shown in the below figure:
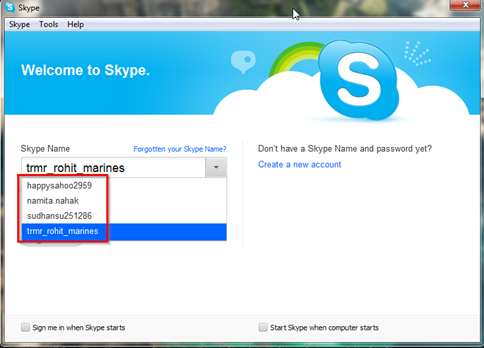
As can we see in the below figure there is a XML file named shared. It is a configuration type file so first we will analyze this XML file.
We can open this file directly through any browser otherwise here we are using Notepad++ for opening shared.xml file and it will look like this shown in below figure
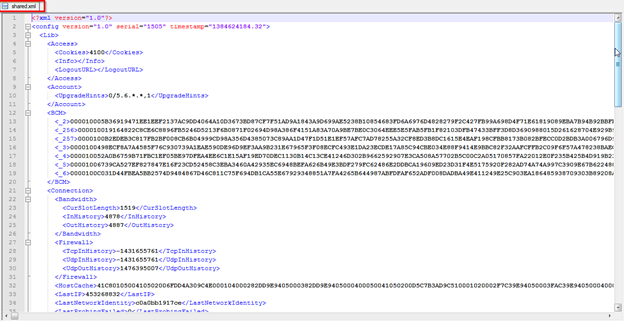
First thing what we will see in this file the timestamp which is showing a value 1384624184.32. This is a Unix style timestamp so we will convert it to readable format. Here we are using online conversion tools and see what we get after conversion.
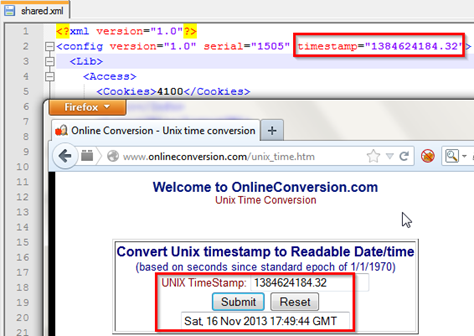
We can see in above figure the output is Saturday 16th November, 2012 17:49:44 GMT.
Another important thing in this file is the HostCache tag. Hostcache is the IP node of the skype. The IP starts after 0400050041050200 it means D5C7B3AD9C51 is the IP address.
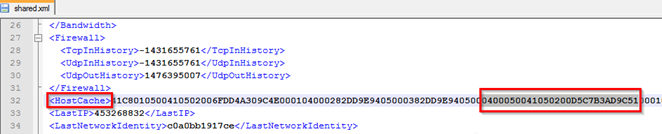
Now what we will do we convert this Hexadecimal value D5C7B3AD9C51 to decimal numbers for revealing the IP and port number. For this we are using here online conversion tool. So first I take D5 and convert it.
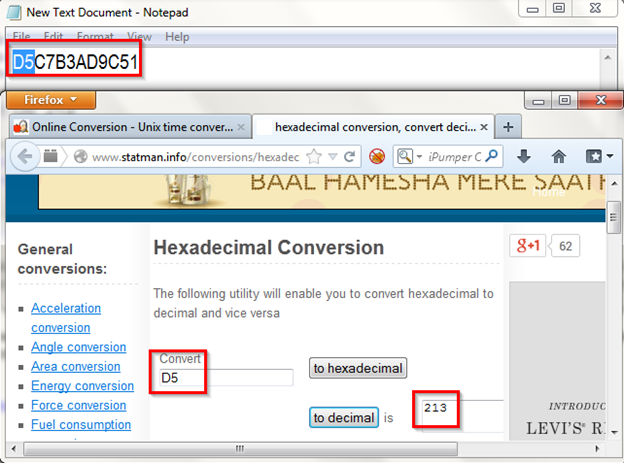
After converting in decimal value what can see the decimal value is 213 , now by this way we can get the whole IP address and Port number.
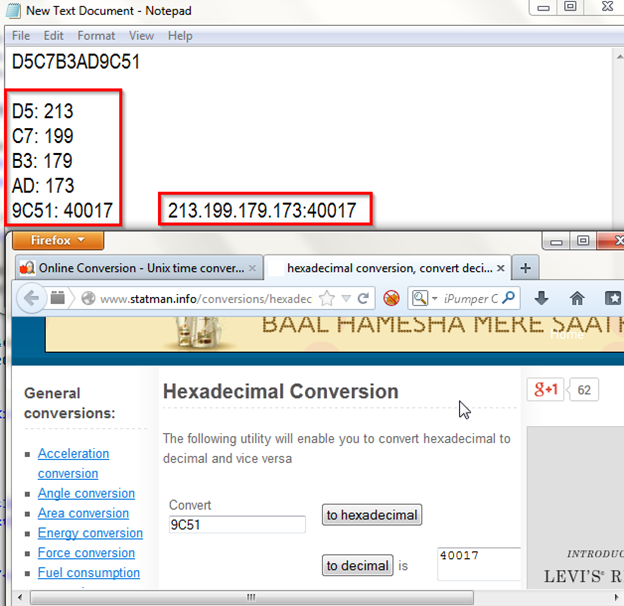
As can be seen in above figure after converting the whole value into decimal we get this 213.199.179.173:40017
Next in UI version tag we will get the current skype version 5.6.59.110 which is used by the users. Under the Language tag we can see the language used by the user which is en simply it means english.
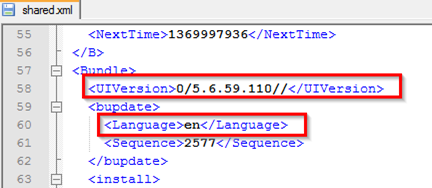
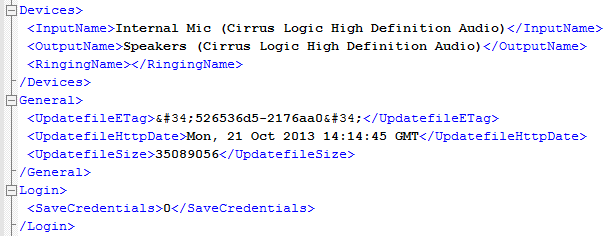
Another information like Devices used in the system speakers and Mic can be seen under Devices tag.
Now we will move to user's directory here we selected trmr_rohit_marines directory for further analysis.

As can be seen in above figure we are under trmr_rohit_marines directory. In this directory we can some files and folders there. Inside the user directory are mostly chat, call, and voicemail logs, all split across multiple files and combining data from multiple sessions and dates. The first folder is chatsync which contains history in dat format. Under this folder each file contains one or more chats between SKYPE-USER and one other user, the timestamp showing the time the last chat ended. The full chat history between those two users may be spread out over several *.dat files.
bistats.db, dc.db, griffin.db, keyval.db these files are skype metadata. config.xml contains the current configuration and contact list for the account holder. config.lck contains account creation date, If SKYPE-USER's account was created on this computer, this will be the account creation date. Main.db is the main file which has juicy information.
First analysis we will start from the config.xml file, let us open this file. We can see another timestamp here under LastSync tag. So convert it in readable format as we did previously.
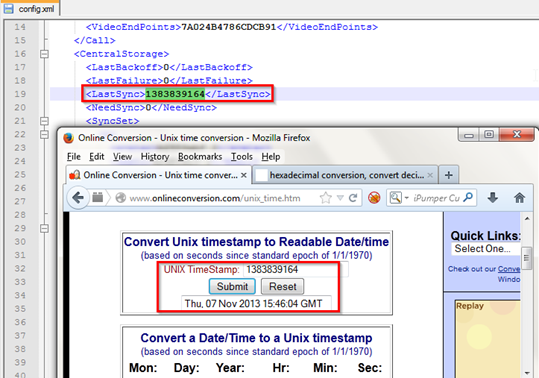
We have the output shown in above figure which is Thursday, 7 November, 2013 15:46:04 GMT.
Now just scroll the file for looking another information and see what we found under U tag the whole contact list of the user.

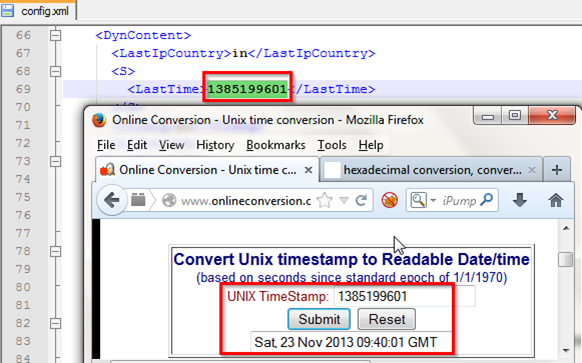
Another information like Last Ip Country, LastTime all we can see here.
Now we will move on to the main.db file which has important information. For opening the .db file we need SQLite Administrator tool we can download this tool from here http://sqliteadmin.orbmu2k.de/.
Now Goto Database and select Open and choose the main.db file from its location.
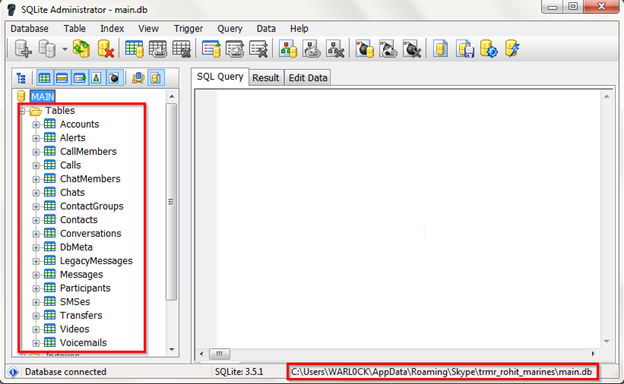
We can see here the whole table in main.db file.
We will review some of the tables which contained sensitive data. For displaying the table data result in right pane side of the SQLite Administrator first select the Result tab then right click and select Show Memo and we are done. 
Now we will check some of the table which contained some information data. Here we selected CallMembers table and the tab info under this table are as follows:
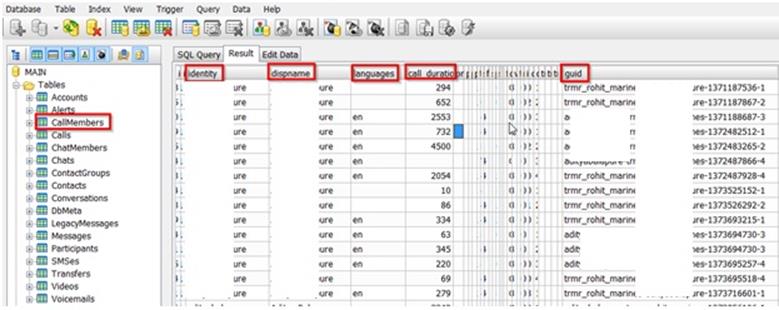
Screenshot blured
Next we selected here Calls table and the tab info under this table are as follows:
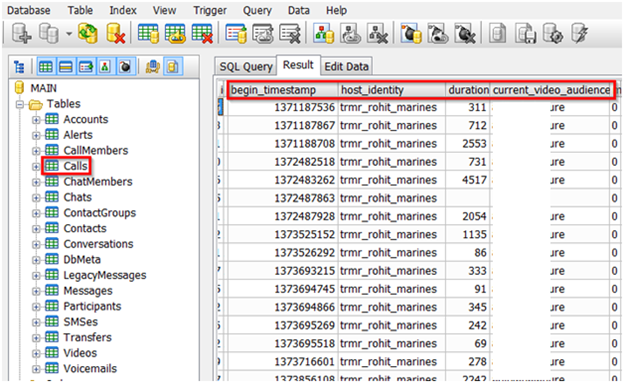
Screenshot blured
Next we moved on to the Messages table the tab info under this table are as follows:
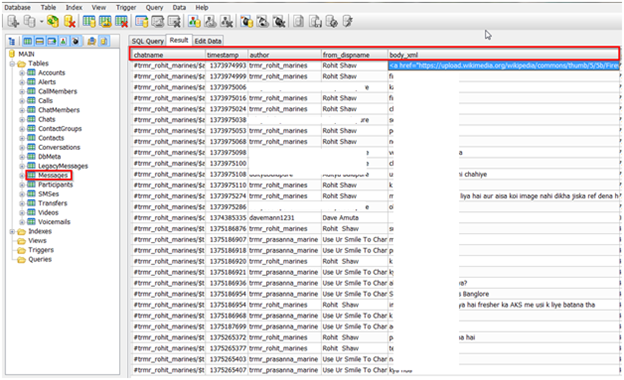
Screenshot blured
Another important Table is Transfers table which contains the information of data transfer. So here we selected Transfers table and the tab info under this table are as follows:
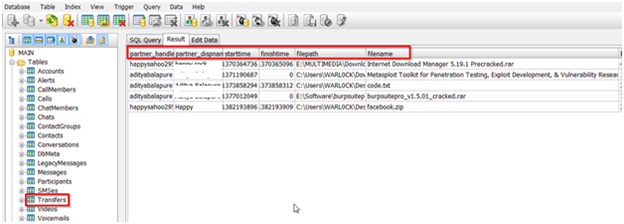
Screenshot blured
Now we are done with the main.db file analysis and we will move on to the chatsync folder. We already described about this folder so we are going to use here a small tool named Skype Chatsync Reader which can be downloaded from here http://itsecuritylab.eu/index.php/tag/read-skype-chatsync-files/.
We can see in below figure the usage of the tool is very easy we have to just put the user's profile directory name in Own ID field as we gave here trmr_rohit_marines and then in Read chatsync filed just give the whole path of chatsync folder. After that we can see the whole chat history here.
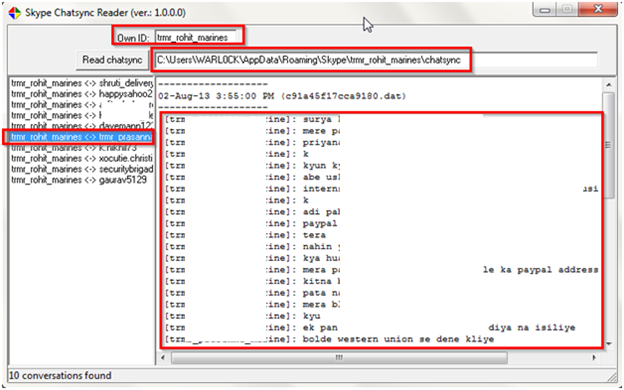
Screenshot blured
References:
http://my.opera.com/wpost/blog/skype-forensics
Learn Digital Forensics
http://stephanietan.boldersecurity.com/2011/04/analyzing-skype-chat-and-call-logs.html




