Phishing on Social Networks - Gathering information
Phishing on Social Networks - Gathering information
Most people will remember the scandalizing 2015 new headlines when sensitive personal data (email addresses, names, contact information and credit card details) was stolen from the online cheating website, AshleyMadison.com. The hackers subsequently posted the personal details of the website’s, supposedly safely anonymous, users online. One of the luckier victims to ld The Guardian he had avoided being caught out by his nearest and dearest by using a fake email address and contact number (although his credit card was at risk) but others were not so fortunate – a number of suicides were reported. AshleyMadison.com it turns out, contrary to what it claimed and this claim is apparently what had initially incensed the attackers, was ultimately neither secure nor discreet.
ld The Guardian he had avoided being caught out by his nearest and dearest by using a fake email address and contact number (although his credit card was at risk) but others were not so fortunate – a number of suicides were reported. AshleyMadison.com it turns out, contrary to what it claimed and this claim is apparently what had initially incensed the attackers, was ultimately neither secure nor discreet.
CNN.com called the Ashley Madison debacle, “The utter end of privacy.” Visitors to the site could not have foreseen it would be hacked; had they known, they would all have used false identities.
See Infosec IQ in action
But there’s another, more sinister and more subtle, invasion of privacy on social media sites that many users seem airily unconcerned about: the use of social networking sites to gather information for phishing messages.
What is social networking phishing?
Phishing is a form of fraud in which the attacker tries to acquire personal information including, but not restricted to, login credentials or account information by masquerading as a reputable entity, through either a fake or stolen identity. It’s also, as described by Microsoft, a type of malicious online identity theft. The first effectively leads to the second. Users on social networking sites, and not only those frequented by adulterers, are fast becoming the easiest targets for phishers. Their strategies can broadly be grouped into two categories:
- The use of links to fake websites to steal your login and password details (or other personal information), and;
- The harvesting of seemingly unimportant personal details you unwittingly share with friends, colleagues and strangers.
Let’s look at these strategies in a bit more detail. How do they do it and why?
Strategy 1: Fake websites
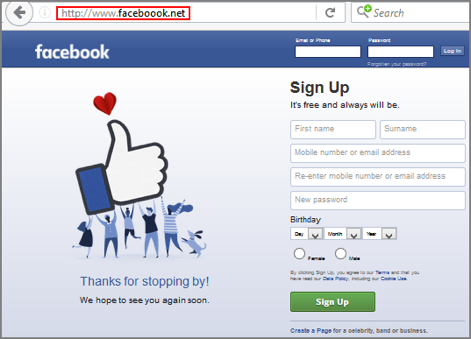
Phishers use fake web site addresses to lure victims into entering their credentials. Perhaps you’ve clicked on a link on a website and been presented with the following option:
 Do you ever check that the URL is actually the legitimate Facebook URL?
Do you ever check that the URL is actually the legitimate Facebook URL?
Once you enter your login details on this fake page, the phishers have access to your account.
Your details can now be sold to the highest bidder or used to lure someone else. For cyber criminals, a hijacked account has far more value than a fake account. People can easily match up your Facebook account and real name with your professional profile on a site like LinkedIn and so be more receptive to overtures from what appears to be someone they know. A hijacked account can be used to extort money from contacts in a hijacked account, scam you (they have your email address now and probably your telephone number too), collect information which can be used to launch malicious personal attacks, stalk victims and spread malware. People tend to follow people they think are who they say they are; it’s all based on trust.
 To add insult to injury, chances are pretty good your login details are the same username and password you use for your email, bank account and dating site accounts. It’s like Christmas for the phisher.
To add insult to injury, chances are pretty good your login details are the same username and password you use for your email, bank account and dating site accounts. It’s like Christmas for the phisher.
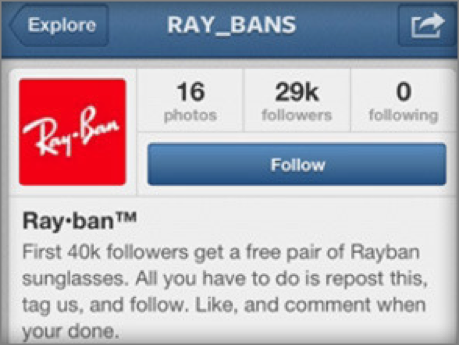
There are a myriad ways scammers try to get their victims to click on fake links: interesting sounding articles, promotional offers, images purporting to be of people you may know, etc. When you are directed to their website, generally you’re required to enter some information in order to view the image, claim your prize or read the article.
In this Instagram example, “your done” is the first giveaway that this promotion is fake. Plus, the instructions are unnecessarily complicated.
[cquote id="1470254027965" post="35484"]
Strategy 2: Harvesting information
You receive a Facebook friend request from someone you think you know, perhaps someone who claims went to the same school as you although you don’t remember them, and you innocently accept the request; after all, it’s nice to have lots of friends and one doesn’t like to be rude.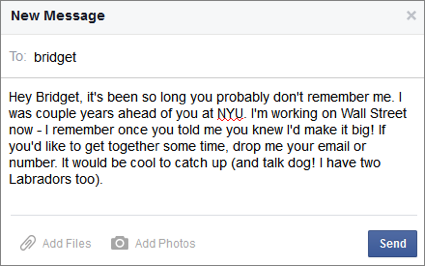
The scammer now has access to all the private information you share with your friends, family and work colleagues who have in one fell swoop become potential victims too.
What is this particular friend looking for? Your name, home town, relationship status, graduation class, favorite vet for your pets, photographs of your home and car, company you work for, your likes and dislikes and the name of the restaurant you visit on Fridays can all be used, chillingly, to produce a complete personal profile of you. They may even Inbox you for more information, perhaps ask for your phone number or email address to invite you to a reunion.
A simple example illustrates why this matters. The Guardian newspaper published an article about a 17-year-old Australian who, in 2012, posted a picture of a “large sum of cash” on her Facebook page that she had helped count at her grandmother’s home in Sydney. A few hours later, masked robbers broke in to the family’s home and demanded to know where the money was being kept, before making off with the cash and some personal property.
It is estimated that more than 600,000 Facebook accounts are compromised in some way every single day. That’s 219,000,000 a year.
Social networking scams are big bucks
According to a 2014 FBI Internet Crime Complaint Center report, 12% of fraud reports are tied to social media. Ominously, complaints have quadrupled over the past five years. “Criminals search dating web sites, chat rooms, and social media web sites for personally identifiable information, and use well-rehearsed scripts to attract potential victims. The criminals present convincing scenarios involving family tragedies, severe life circumstances, and other hardships in an attempt to solicit money.” The cost in dollars for the victims in 2014 was estimated at over $80 million.
https://www.fbi.gov/news/news_blog/2014-ic3-annual-report
It’s not just individuals that are targeted. In a 2015 study by the Ponemon Institute of Cyber Crime, phishing attacks cost an average large company nearly $4 million USD annually.
Who falls for these scams?
The problem is that many users are wary when asked to provide bank account or credit card details online but not so wary when entering personal details on social networking sites. And that’s the rub; a phisher is like an evil MacGyver and is able to use the most innocuous information to steal, stalk and scam victims. (*MacGyver was the hero of a TV series. Each episode he would save the day by making his escape or tricking the bad guys using random items. In one episode he made a parachute using a pair of shorts and some plastic bags.)
Social media scams are not as transparent as the notorious Nigerian 419 scams that few people with rudimentary spelling could take seriously. Interestingly, and according to an article in the NY Times, an email address in Nigeria for example could, by scaring off the savvier or more suspicious sorts, enable them to focus on the most gullible victims. In a similar fashion, victims on social media are gullible when it comes to the postings of “friends”.
Looking for Love
 Dating networking sites have their fair share of phishers. Victims are selected based on the information they upload to their profiles. According to the FBI’s Internet Crime Complaint Center, singles over 50 looking for love are the primary targets, probably because this demographic is lonely, wealthy and wants to believe love is waiting in the wings. In one case a victim lost $200,000. It is estimated that 1 in 10 dating profiles is fake. Badoo is the first dating site to introduce selfie photo verification in an attempt to weed the fakes out.
Dating networking sites have their fair share of phishers. Victims are selected based on the information they upload to their profiles. According to the FBI’s Internet Crime Complaint Center, singles over 50 looking for love are the primary targets, probably because this demographic is lonely, wealthy and wants to believe love is waiting in the wings. In one case a victim lost $200,000. It is estimated that 1 in 10 dating profiles is fake. Badoo is the first dating site to introduce selfie photo verification in an attempt to weed the fakes out.
Buzzwords you may hear bandied about
- Social engineering – A malicious assault tactic that involves tricking people into breaking normal security procedures, often relying on greed, an appeal to vanity or kindness, or threat of authority and intimidation. This type of phishing is associated with the Trojan horse of Greek mythology and its main purpose is information gathering by creating an illusion of reality. Wikipedia provides a nice example: an individual walks into a building and posts an official-looking announcement to the company bulletin that says the number for the help desk has changed. So, when employees call for help the individual asks them for their passwords and IDs thereby gaining the ability to access the company's private information.
- Pretexting – A fake, but seemingly legitimate, scenario is created aimed at gaining access to a victim’s privileged data, e.g. requiring their personal details in order to confirm their identity before they can claim a prize or pretending to be the human resource department of their previous company who need to update their records. This tactic relies on a reasonable pretext; clearly one cannot claim a prize without providing personal details.
- Doxing – Private information, gained in a phishing attack, is leaked on social media, making victims vulnerable to other scams, like stalking, harassing and stolen identities. This psychological tactic is usually exclusively malicious, designed to intimidate victims for little reason other than so-called fun.
- Pharming – A victim is lured to a spoofed website and invited to log in using their Facebook or email account. The victim’s login details are hijacked and their information used to access other accounts including their email address. The success of this tactic relies on the trust victims have in the impenetrability of their basic internet software, like their browsers, online email and social media accounts.
- Spear phishing - An e-mail spoofing fraud attempt that targets a specific organization or individual, seeking unauthorized access to confidential data. Charles Harvey Eccleston, a former federal agent was recently found guilty of spear phishing. He was convicted of offering to sell information on more than 5,000 Energy Department officials’ email accounts to a foreign embassy in Manila.
Hot phishing targets for 2016
Phishers are relentless in their quest for information and despite social media security initiatives, phishers keep finding new ways to strip their victims.
- Dating: Targeting social media like dating networking sites is on the rise. According to the FBI’s Internet Crime Complaint Center, singles over 50 looking for love are the primary targets, probably because this demographic is lonely, wealthy and wanting to believe love is waiting in the wings. Losses of hundreds of thousands of dollars are not uncommon. Victims are selected based on the information they upload to their profiles. It is estimated that 1 in 10 dating profiles is fake.
- Freelancers: Security software solutions provider Bitdefender says LinkedIn is becoming the social media site of choice for work-at-home scams. Freelancers are vulnerable to nefarious information gatherers as they often provide a lot of information about themselves onto networking sites in an effort to pique potential clients’ interest.
- Facebook videos: Malicious links in Facebook videos will be more common this year. A two-year study showed videos such as “beheading and murder” account for almost 1% of social media scams.
- Companies: According to CNBC, impersonating companies rather than individuals is on the rise. Someone tweets at a company because they may be upset about an issue. A fake account on Twitter replies directly to that person, and asks them to log in to a fake website. The victim then exposes their personal information to hackers.
- Streaming video: Variety.com reports pirates are posting links to copyright-infringing movie streams and downloads in the comments section on Facebook pages. Some 62% of the piracy comments that were analyzed impersonated free streaming channels to acquire non-authorized credit card payments.
How does it affect businesses?
 Identity theft in the form of company account takeovers can cause said company great embarrassment. It happened to Burger King when its Twitter account was taken over purportedly by McDonalds. Jeep suffered similar embarrassment when its takeover by Cadillac was announced in a tweet.
Identity theft in the form of company account takeovers can cause said company great embarrassment. It happened to Burger King when its Twitter account was taken over purportedly by McDonalds. Jeep suffered similar embarrassment when its takeover by Cadillac was announced in a tweet.
But the theft of employees’ identities can also have a direct impact on their employers.
While most corporations and even small businesses employ stringent security measures including anti-virus software and external and internal firewalls, they often neglect to take the vulnerable human element into account. Staff can compromise security out of hours simply by providing sensitive information about their employer online, for instance, by uploading a resume or their portfolio on a site like LinkedIn. In fact, the biggest risks to businesses from social media usage may be from accidental disclosure. The most innocent of social tweets may put an employer at risk, e.g. “Have to work over the weekend. Serious problems with the network.”
From phone numbers to employee titles, from employee blogs to Friday afternoon comments on social media about the week at work, these can all help a hacker to create a vulnerable profile of a company. It is these little crumbs of information that can have even wider security implications than employees opening email attachments from people they don’t know.
Security awareness programs like Infosec IQ’s PhishSim phishing simulator are increasingly being used by companies to educate staff and identify phishing loopholes.
Threats to companies include:
- Reputation damage from employee gossip
- Copyright infringements
- Unauthorized sharing of company information
- Enabling of phishing attacks using hijacked staff accounts
- Privacy infringements
Be safe
- Spelling errors are telltale signs of a phishing scam, e.g. Facebook spelled with only one “o”.
- Never click on links in suspicious messages.
- Never click on an unverified link, video or file.
- When leaving a secure site, check the address of the site to which you are redirected.
- Use reputable security software.
- Limit the information available in your profile, e.g. your address.
- Don’t save your login information when using a shared computer.
- If it’s too good to be true, like an offer for a free laptop, it probably is; don’t follow the link.
- Don't accept 'friend' requests from people you don't know.
- When asked for information to update your account or to re-enter your login details, check the URL.
- If you receive an unusual message from someone you know, contact them outside of the social networking site to check their story.
- Don’t be intimidated. Banks and the revenue service never ever ask for your personal information via social media.
- Don’t respond to invitations to connect unless you know the person or company.
Summary
The chilling reality is that some phishing tactics - for instance those where websites harvest information on social websites - to identify users’ website preferences, or to store account and personal details - are seemingly benign but may have, if the information gathered is hacked as in the Ashley Madison case, damaging consequences.
https://securityiq.infosecinstitute.com/?utm_source=resources&utm_medium=infosec%20network&utm_campaign=infosec%20iq%20pricing&utm_content=hyperlink has published a number of videos on social engineering and phishing. You can sign up for a free account to browse their resources and test how phishing savvy you really are.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Sources consulted:
- http://www.makeuseof.com/tag/phishing-techniques-scammers/
- http://www.forbes.com/sites/lisabrownlee/2015/10/07/security-simulated-phishing-attacks-yield-37-percent-return-on-investment/#32cc9bad2642
- http://www.ponemon.org/blog/2015-cost-of-cyber-crime-united-states
- http://www.techlicious.com/tip/avoiding-social-media-scams-on-facebook-twitter/
- https://www.fbi.gov/news/news_blog/2014-ic3-annual-report
- https://blog.kaspersky.com/1-in-5-phishing-attacks-targets-facebook/5180/
- https://www.theguardian.com/technology/2016/feb/28/what-happened-after-ashley-madison-was-hacked
- https://www.theguardian.com/technology/2016/feb/28/what-happened-after-ashley-madison-was-hacked
- https://www.cybercrimeinvestigators.com/videos/videodetail/id/24/offset/10/itemcountpage/setitemcount
- http://www.lavasoft.com/mylavasoft/company/blog/how-social-networking-security-awareness-saved-a-company%E2%80%99s-reputation
- https://en.wikipedia.org/wiki/Social_engineering_%28security%29
- http://www.nytimes.com/2014/01/05/magazine/who-made-that-nigerian-scam.html?_r=0
- http://www.huffingtonpost.com/james-parsons/facebooks-war-continues-against-fake-profiles-and-bots_b_6914282.html
- http://www.theguardian.com/money/2015/nov/07/social-media-scammers-twitter-instagram-facebook
- http://www.tripwire.com/state-of-security/security-awareness/internet-scams-its-no-longer-merely-emotional-part-2/
- https://netguide.co.nz/story/biggest-social-media-security-threats-2015/
- http://www.cnbc.com/2015/10/23/hackers-turn-to-social-media-to-phish-for-credentials.html
- http://variety.com/2016/digital/news/how-pirates-hijack-movie-studios-ad-campaigns-on-facebook-guest-column-1201747816/
- https://uofa.younglife.org/Graphics%20and%20Clip%20Art/Forms/AllItems.aspx (fish in a bucket)
- http://www.federaltimes.com/story/government/cybersecurity/2016/04/13/eccleston-sentenced-spear-phishing/82983260/