Phishing Attacks in the Financial Industry
Phishing Attacks in the Financial Industry
Phishing Targets by Industry:
- Financial Phishing
- Government and Military Phishing
- Healthcare Phishing
- Retail Phishing
- Phishing Individuals
Phishing simulations & training
In a September 2011 presentation to the House Financial Services Committee, Subcommittee on Financial Institutions and Consumer Credit, Gordon M. Snow, Assistant Director of the Cyber Division of the Federal Bureau of Investigation, identified phishing as the primary vector used for cyber-attacks in the financial industry. Mr. Snow pointed to the size and the nature of the financial industry as the primary reasons for targeting by cyber-criminals.
At the time of his presentation, Mr. Snow reported that the FBI, with cyber squads in 56 cities across the U.S., was investigating over 400 cases in which hackers had attempted to steal, cumulatively, over $255 million, and had been successful in actually pilfering over $85 million. And while that is an enormous sum, it is likely only a small fraction of the actual total attempts and losses. The FBI only tackles larger cases as a general rule, so these figures do not include smaller losses.
The scale of a single breach can be staggering, as demonstrated by the July 2014 attack on JP Morgan Chase & Co. In this attack, phishers snagged information on 76 million households and 7 million small businesses. Chase officials reported no financial losses to any of their clients’ accounts or to Chase’s own operating, general, or any other in-house accounts, so the concern is that the personal information seized will be used in direct attacks against these individuals and businesses.
In the wake of this enormous breach, Chase IT security sent a fake phishing email to their employees in order to determine how well-attuned staff were to potential threats. 20% of the recipients reportedly took the bait. The results of that experiment seem consistent with industry estimates, which attributed 30% of breaches in 2015 to employee error.
Because of the anonymous and seemingly enormous number of parties, initiating phishing schemes against millions of clients and tens of thousands of employees, maintaining a solid defense is a daunting task for banks and other large financial institutions. In a recent interview, when asked about cybersecurity, John Stumpf, Wells Fargo CEO, stated that “It is the only expense where I ask if it’s enough.”
True total losses are difficult to measure, as many cases go unreported. There are laws which require businesses to notify customers in the event that a client’s personal information has been stolen. However, institutions will often choose not to report a loss to operating or other general accounts that do not contain personal information of clients, as such losses can be devastating to reputations. People are generally unlikely to do business with a financial institution that has a known history of security lapses. In a 2014 survey by Javelin Strategy and Research of over 5,000 adults in the U.S, 24% of respondents said that they would leave a financial institution after a security breach.
Larger businesses may be able to shrug off these events, but a cyber-attack could very well mean the end for smaller firms who are unable to absorb the financial loss. The U.S. House of Representatives Small Business subcommittee on health and technology reports that 60% of small businesses will fail after a cyber-attack.
Why Phish Financial Institutions?
One of America’s most prolific bank robbers of the early 20th century, Willie Sutton, was once asked why he robbed banks. Willie replied, “Because that’s where the money is”. Today, phishers target banks and other financial institutions because, among other reasons, that’s where the money is.
Willie Sutton also once stated in an interview that he carried either a pistol or Thompson submachine gun (both supposedly unloaded, as he did not want to hurt anybody), because “You can’t rob a bank on charm and personality”. Times have changed. Charm and personality, along with wit, technical know-how, and deceit are exactly how phishers now target banks and other financial institutions.
There are unlimited targets today. Banks, credit, payment services, investment firms, and other financial services are everywhere. Most every business and individual use one or more of these entities to conduct business, providing unlimited pathways for cyber criminals, either through the financial firm’s website or internal systems.
How are Financial Companies Phished?
Phishers have a wide array of tactics, which they may use to attack financial institutions. These attacks may be launched with a deceptive email to either a customer or employee of the firm, and may either be random or selectively targeted (known as spear phishing).
Phishers may randomly spam individuals en masse with a false alert from a large institution, warning of a problem with their account. The email may direct the recipient to provide their account and password, or other information, or to log in through a fake website, or download a malicious file used to gather that information from the user’s personal device.
Emails with overly generous offerings, such as a bonus for opening an account, guaranteed loans at low rates, or other irresistible enticements may also be used to entice readers to submit personal information, visit a website, or download a file.
One of the current phishing scams, which targets Chase customers, offers $50 for merely taking a two-minute survey. Any takers of the offer are directed to an official looking site, complete with a bogus customer-satisfaction survey. Once the survey is completed, the user is asked to provide their Chase account number, password, and answer to security question, so that the $50 can be deposited.
Employees of a firm may receive an email, appearing to be from a legitimate customer or fellow employee of the firm. The employee, like the customer, may be directed to provide account information, download a malicious file, or take other actions which can provide the phishers with the information needed to compromise an account.
Over a two-year period, from 2013-2015, an Eastern European gang stole over $1 billion from 100+ banks in nearly 30 countries. The gang used a very sophisticated Trojan horse, which would be embedded in an attachment to an email sent to bank employees. The malicious software enabled the thieves to use screen grabs in order to monitor how money was moved internally, and then repeated those steps themselves in some cases. In other cases, the group would direct an ATM to dispense cash, and merely have it picked up by a courier.
Three Steps for Preventing Financial Phishing
Education and Training
Because phishers are typically more computer savvy than the average user/customer or employee of a financial institution, they have a decided advantage in the game. To mitigate this advantage, businesses need to take the initiative in educating and training their staff and clients.
InfoSec Institute offers self-paced tutorials, available to all InfoSec account holders, including those with free membership plans. A quick overview of phishing to help learners recognize suspicious emails, and what to do in the event a suspect email is received is covered in the coursework.
Financial institutions and IT professionals seeking higher-level security courses, including those pertaining to phishing, can also find advanced courses at InfoSec Institute. You may view InfoSec’s tutorials and sign up for a free account here.
Testing and Evaluation
To understand what initiatives a financial firm may need to undertake, so as to train and inform its clients and staff, or to determine how effective a phishing educational program may have been, testing and evaluation should be conducted. InfoSec’s Security IQ provides an ideal mechanism to perform just such an assessment.
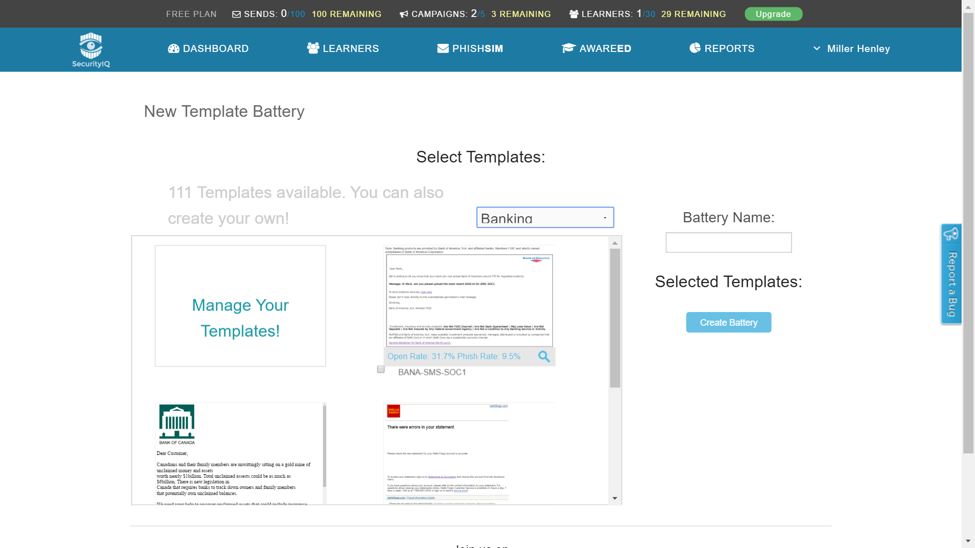
Using InfoSec’s PhishSim tools, IT security team members and management can create emails similar to those which may be used by phishers, and then dispatch the emails to customers and staff to determine how they might respond to a real phisher. To create a faux phishing email, users may either develop their own email from scratch, or modify one of dozens of existing templates in the PhishSim library.
With a large collection of existing templates, cloning and then modifying an existing one is probably the quickest and easiest way for a user to start a phish testing campaign. Below is a sample of some of the existing email templates for banking (just one of many sectors available), found in InfoSec’s online library, which may be edited as needed.
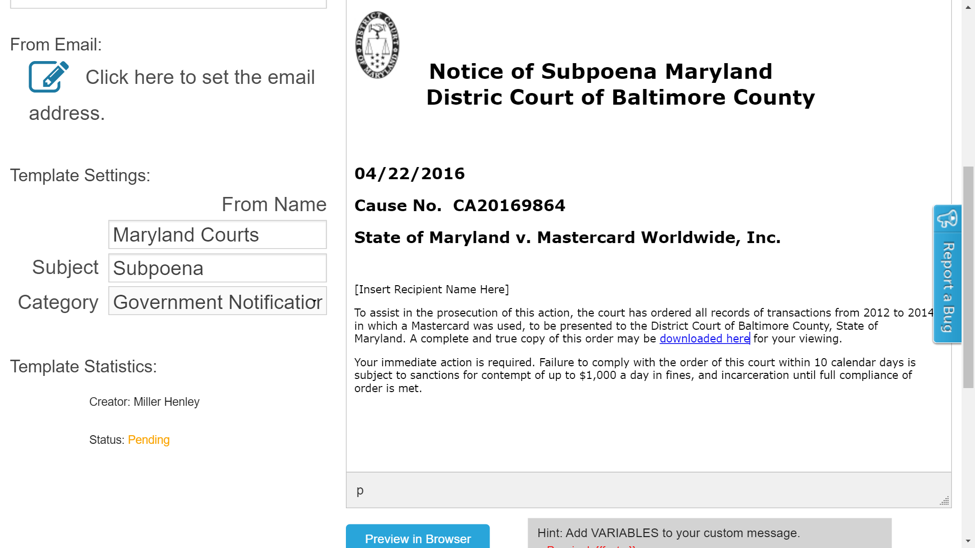
Here, is a template created to mimic one of the most recent and successful phishing scams, where CEOs are sent fake court subpoenas requiring the submission of account information. In one case, Verisign reported that over 1,800 CEOs clicked on the email.
After creating an email for testing, users may send these simulated emails directly from PhishSim. Email addresses of those being tested may be directly imported, and unique campaigns with different simulated phishing emails and recipient lists may be managed within PhishSim by means of the Campaigns management feature.
Reporting
Any organization, large or small, having any association with financial institutions, which consequently includes most every company, needs to have reporting procedures in place. Procedures should instruct employees and customers on how to immediately act upon receiving a phishing email and to whom to report the email to.
[cta id="1470254541654" post="35732"]
Not only must businesses have procedures for clients and staff to report suspected phishing events internally, but businesses also must engage externally to help stymie the crime. Working with both law enforcement and industry associations devoted to combatting cybercrime, businesses can help to protect the community at large, and as a result themselves.
Although it may seem in vain in many cases to report a phishing attempt, as the senders frequently change email accounts and formats, making for a seemingly endless and futile game of whack-a-mole: it helps. The FBI, the Department of Homeland Security, Interpol and other agencies maintain databases containing different types of scams attempted, suspects’ names, and other information to share with other law enforcement agencies, and some private organizations, from around the world for use in investigations and prevention initiatives. And while many cases will be unsolvable, some will be successfully prosecuted. Even without successful prosecution though, the sender’s account can often be quickly shut down, if the culprit is listed in one of these databases, and the malicious email or file cataloged for use in spam and malware detection.
Conclusion
Phishing in the financial industry is real, serious, and ubiquitous. IT security professionals must remain vigilant in monitoring, training, testing, and reporting. Failure to thwart phishing activities could cost an IT worker his or her job, jeopardize a firm’s reputation and financial standing, or even lead to the shuttering of a business.
InfoSec can assist with training of staff to counter phishing and other cyber threats. Since our founding in 1998, over 15,000 IT professionals have received instruction on a host of cyber security areas and our programs have consistently received industry awards and recognition.
InfoSec’s PhishSim tool, tutorials, and advanced training combine to provide IT security specialists with a complete system for combating the ever-present threat of phishers. It takes only seconds to create a free InfoSec account, and minutes to create and run a PhishSim test. To get started, click here to create your account (if you haven’t already) and run your first PhishSim test.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.