Phishing Attacks by Demographic
Those who believe that no one falls for phishing anymore couldn’t be more wrong. Phishing is still on the rise, as shown by the 2016 Verizon’s Data Breach Investigations Report [PDF]. In fact, 30% of phishing emails are still opened soon after receipt and about 12% of targets even go on to click suspicious links or attachments. Moreover, “The median time for the first user of a phishing campaign to open the malicious email is 1 minute, 40 seconds. The median time to the first click on the attachment was 3 minutes, 45 seconds.”
See Infosec IQ in action
Phishers are still able to exploit the human factor to break the security chain; in the words of Janet Brumfield, the director of corporate communications for Verizon Enterprise Solutions, “cybercriminals are continuing to exploit human nature as they rely on familiar attack patterns such as phishing.” Phishing attacks are successful because they target basic human natural responses as the urge to open correspondence, especially when it reaches their work account or it’s believed to be coming from legitimate sources, colleagues or friends.
Attachments and link manipulation techniques in emails have been used in phishing schemes to fool or trick recipients into revealing personal identifiable information (PII); phishers have also setup phony Web sites (which often look identical to legitimate sites but may use a variation in spelling or a different domain) to target Internet consumers through click-on ads or pop-ups.
Phishing Attacks Becoming More Common
Phishing is a continuously growing threat today, and “the number of observed phishing attacks in Q1 2016 hit a 12-year high,” according to Tara Seals' US/North America News Reporter, Infosecurity Magazine. She noted that the Phishing Activity Trends Report [PDF] by the APWG (Anti-Phishing Working Group) documented “a 250% increase in phishing sites popping up between October 2015 and March 2016.” In addition, recent research has indicated that 93% of phishing emails are now ransomware. This increase is definitely a cause for concern.
Phishing has also spread beyond emails to include VoIP, i.e., vishing (over the telephone, voice phishing), and unsolicited text messages and instant messaging—i.e., smishing (SMS phishing). Phishers are, then, utilizing new attack vectors to exploit people through all electronic and digital channels. As Jason I. Hong, an associate professor at Carnegie Mellon University, points out, phishing variations and related attacks have grown to target not only individuals, but also social networking sites, and industries in healthcare, government/military, finance, retail and others.
Who Can Be a Target for Phishing?
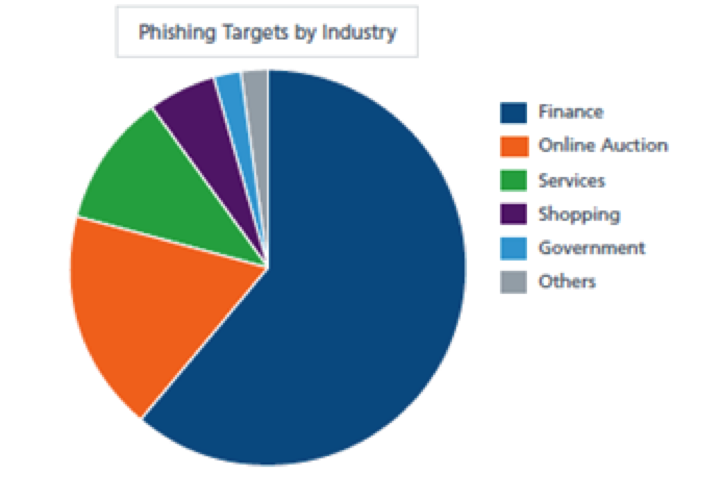
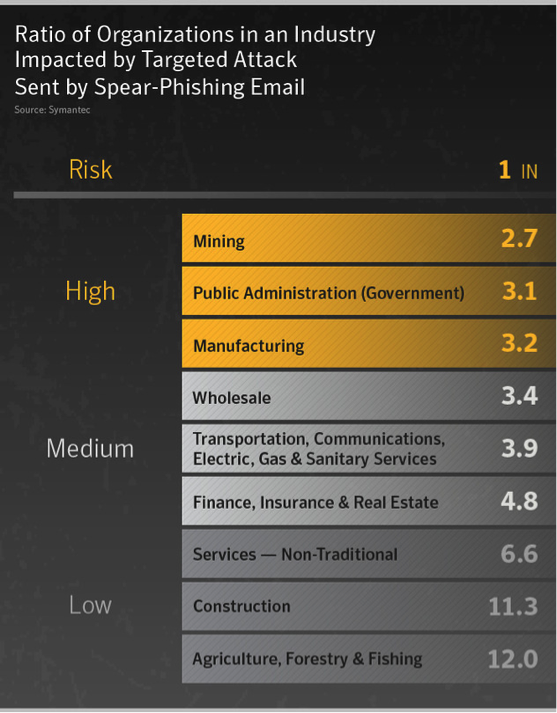
Any industry, any workplace, any work role can be targeted by phishing criminals; however there are fields that, for obvious reasons, are more at risk and where cybercriminals concentrate their efforts. A recent threat report on ‘Email Phishing by Industry’ in May of 2016 by Symantec noted that the finance, insurance, and real estate sectors witnessed the highest phishing rates lately, with 1 out of every 1,520 e-mails being affected. The agriculture, forestry, and fishing field is ranked second in the list of affected industries and, not surprisingly, public administration is the third in the ranking with 1 out of 2,625 e-mails being a phishing attempt. Companies with over 1,500 employees are the most likely targets, with 1 out of 1,638 e-mails being malicious.
With the e-commerce market continuing to grow and gaining momentum and consumer confidence, there’s also been an upsurge in attacks, say researchers at Symantec Corp. “In the finance, insurance and real estate sectors, that ratio was one in 4.8”; a good percentage of the attacks were aimed at the ecommerce platforms for payments and retail engagements.
Source: Symantec
It’s not a surprise, then, that some countries are more susceptible to phishing than others. Analyzing the Global Phishing Susceptibility Map provided by OpenPhish with IntelliAct data, it’s clear how North America, Europe, Australia, and South Africa are regions and countries where users are more susceptible to phishing as more is done through the Internet. In a Q3 2015 report [PDF], however, according to Kaspersky Lab, the country with the largest number of users affected by phishing was Brazil (21.7%) followed by Japan (16.86%) and China (15.08%).
The OpenPhish site also provides an almost real time snapshot of the most targeted brands and sectors. Lately, for example, the most targeted URLs though phishing included Paypal with over 40% of attempts, Apple, Google, Dropbox, and more. As always the most targeted sector is that of payment services, followed by e-mail providers.
Phishing Attacks on Individuals
From phishing emails to malicious websites and domains to bogus phone calls and specific attempts of social engineering, all techniques and tactics have been used to manipulate people through the years; in many cases, victims have been exploited using a combination of techniques. Phishing attempts can be aimed at a mass audience (a variant of spam), directed at specific individuals or companies (spear-phishing), or targeted specifically at senior executives (whaling); attacks are increasingly pervasive and sophisticated.
The likelihood of computer and mobile users taking the bait and getting hooked in an individual phish scheme is quite significant. Intel Security (formerly McAfee) declared that 97% of people are unable to correctly identify phishing emails. A similar percentage holds true for those unable to distinguish legitimate URLs from illegitimate ones.
An interesting study titled “Enterprise Phishing Susceptibility Report” shows how phishers are able to use effective motivators to lure their victims into reacting to their malicious e-mails. According to the PhishMe study, the strongest motivator is a feeling of personal connection with the sender (23% average response rate), followed by the promise of a reward (21%), curiosity (18%), and urgency (16%). Gender doesn’t really play a role, as women had only a slightly higher average response rate (22%) than men (20%) in a “Package Delivery” benchmark simulation.
Phishing Attacks on Social Networks
Social networking sites are now a prime target of phishing; they are, in fact, a fantastic depository of information for hackers preparing spear-phishing or whaling campaigns. Detailed job descriptions, connections, friends, and previous employment info are normally widely available and can be used to craft specific and realistic baits. Phishing on social networks is as easy as gathering information from profiles, or it can be done by luring victims into revealing personal information or credentials. Scams like the Facebook Lottery Winning one (April, 2016) have already caused many victims. Phishers might use fake "social network" web site URL addresses with the intention to steal login and password details (or other personal information) and gain access to accounts.
Already in 2013, Kaspersky Security Network collected data showing that 35% of the cases in which their anti-phishing protections were triggered had to do with sites imitating social network pages. Fake Facebook pages accounted for approximately 20,000 incidents per day, while a total of 600 million attempts to access phishing sites were recorded. The way users were lured included messages from social network “friends” with compromised accounts, fake notifications, banners, and forums participation. Targets were all over the world with fake Facebook pages created in variety of languages including Turkish and Arabian in addition to German, French, English and more. In the first quarter of 2015, instead, the share of "social networking sites" attacked was 21.44%. As mentioned in the SC Magazine for IT security professionals, in fact, one in five phishing attempts is made through social media.
Phishers don’t just directly ask for info, but they can also exploit accidental disclosure. In workplaces, where social media are often used to communicate informally between colleagues, partners and clients, users might have a false perception that their communications are private, while it is hard to really control who has access to information (contacts, friends of friends, general public). Even a casual comment on something that happened during a meeting could lead to the unintentional disclosure of information that a malicious user could apply. According to the statistical portal Statista, in 2015 “76 percent of social media threats required end users to propagate them. Fake offerings were ranked second with 17 percent of attacks being attributed to them.” Fake applications and fake plugins accounted only for 2% and 1 % of the scams.
Phishing Attacks in the Financial Industry
For obvious reasons, one of the major targets for phishers is the financial industry. Since the motive behind malicious hackers is often monetary, it seems fitting that banks and other financial institutions are under attack through a wide array of tactics. According to the Anti-Phishing Working Group (APWG) Phishing Activity Trends Report Q1 2016, the financial world remains the second most-targeted service sector with 18.67% of attacks. There are many reports on financial clients being phished while involved in online payment services. Bank customers are popular targets, with a great deal of financial info (user account data and credit card number details) falling into to the wrong hands.
The JPMorgan Chase & Co banking phishing scam in July 2014 that involved a security breach is a prime example of a phisher’s attack on a financial institution. Often, the personal information seized has been used in direct strikes against individuals and businesses, as demonstrated by this incident, in which the accounts of 76 million customers and 7 million small businesses were compromised.
The increase of electronic payments and online transactions in the financial/banking sector has led to a surge of email fraud and sophisticated spoofed sites scams to steal customers’ money or identity, or both. Scammers are also making fraudulent payments. Financial service firms are now targeted 300% more often than any other sector, according to figures reported by the InternationalBanker site. “Last year, many banks were targeted by a sophisticated spam campaign that took advantage of email to trick consumers into installing the infamous banking Trojan, Dyreza, on their computers.” It seems approximately 100,000 machines were affected by this malware that spread in different ways throughout the globe. “In one example of Dyreza, attackers sent an email masquerading as a secure message from a bank. The attached Word document included the bank’s logo and address – including a ‘Secured by RSA’ logo – and what looked like an encrypted block of text. The page contained instructions to click on the "Enable Content" button to view the message, but instead of decrypting the text, it executed embedded macro script which downloaded and installed Dyreza.”
Phishing is a huge problem for businesses that rely on building customer trust for their growth. A Cloudmark study, in fact, reports that 42% of consumers are less likely to engage with a business after an email attack even if not directly affected. As reported by the FBI, a 270% increase in global losses was reported in the period January-August 2015. And InternationalBanker reports that “last year, the FBI reported that losses from one type of spear-phishing, Business Email Compromise (BEC) scams, alone totaled more than $1.2 billion.” That being said, it is important that financial institution really invest in technical and awareness countermeasures.
Phishing Attacks in the Healthcare Industry
The healthcare sector is also prone to phishing attacks. The healthcare industry is expected to be a target because of the valuable data contained within EHRs that can be used by phishers to commit several types of fraudulent activities or identity theft. In fact, many of the hospitals’ IT systems and medical records are being targeted by phishers who try to gain access to patient data, launch ransomware attacks demanding money, or make clinics’ electronic health records (EHRs) inaccessible, thereby compromising the patients’ care.
Healthcare phishing attacks often have large-scale consequences. A security breach that potentially led to information being disclosed for 1,300 patients—including names, addresses, credit card numbers and Social Security numbers, according to Becker Hospital Review—happened at Auburn, Ind.-based DeKalb Health in 2014. Around the same period, there was another incident at the Franciscan Health System of Tacoma, Washington, which was hacked in a phishing scheme; it affected potentially 12,000 patients, according to Health IT Security. More recently, the Wyoming Medical Center was attacked through a phishing scam that started with an employee opening a phishing e-mail. The account was hacked and new e-mails were sent to other employees until the hacker gained control of the e-mail system for 15 minutes and had access to the protected health information (PHI) of 3,184 patients.
Equally troublesome, an IBM study, the 2015 Cyber Security Intelligence Index report, actually found, “Healthcare moved into the top spot of the rankings as the most-attacked industry in 2015, replacing financial services. […] Five of the eight largest healthcare security breaches since the beginning of 2010 took place during the first six months of 2015. In fact, over 100 million healthcare records were compromised in 2015.”
Phishing Attacks in the Retail Industry
According to the APWG Phishing Activity Trends Report Q1 2016, the retail industry is actually the most-targeted industry service sector, with 42.71% of attacks. The rise is possibly due to the surge in attacks through cloud-based companies or SAAS (software as a service) companies. Attacks are on the rise, especially during the holiday shopping seasons. Once again, for hackers looking for financial reward, targeting e-commerce customers is an obvious choice. Sending e-mails posing like Amazon customer service, an internet carrier, or any highly-used multinational operation can quickly fool any customers into clicking on malicious links and disclosing personal account information.
Employees are also possible targets. A phishing incident was detected this last tax season: a tax-related data breach incurred by Sprouts Farmers Market that confirmed an email scam resulted in the retailer inadvertently disclosing its employees’ 2015 W-2 earnings statements. Sprouts has been working with the FBI and the IRS to investigate the crime but, in the meantime, the scam has affected many of the thousands of employees that work for the company.
In other case, back in January 2016, an Austrian aircraft industry supplier FACC was the victim of a $54M cyber fraud believed that might have been perpetrated through e-mail spoofing and business e-mail compromise.
Phishing Attacks in the Government and Military
It's not surprising that the government is a target of phishing, too; there is lots of evidence of data leaks – some from intentional culprits, while others were not. In spite of that, the top cause of government-related data breaches was phishing attacks, which has led to an increased focus on data security. The U.S. government now also has a dedicated phishing website to report suspicious email.
Sophisticated phishing schemes against U.S. government and military institutions initiated by spear-phishing have been intensifying; some are high-profile attacks, even involving foreign governments and militants. For example, the Hacker News site reports attacks by the Syrian Electronic Army (SEA) Hackers, known for advance phishing attacks and the use of Trojans against military, diplomats, and government officials.
But phishing schemes have also been at the center of infamous data collection campaigns by malicious hackers. The US Joint Chiefs of Staff systems were hacked through spear-phishing e-mails sent to military personnel from a bank. As a result, 4,000 DoD personnel credentials were compromised and the e-mail system was unusable for approximately 10 days, said a U.S. official familiar with the hacking attempt.
Conclusion
User mistakes aid most phishing attacks, as communicated in Verizon’s annual Data Breach Investigations Report (DBIR) for 2016, and Symantec's 2015 Internet Security Threat Report (ISTR) confirms that overall Internet security threats are on the rise. Both security vendor reports on cybercrime tell how counter-phishing measures are essential to help protect both individuals and companies against those scams. Increasing the use of web content filtering can reduce some phishing. The implementation of appropriate protections at the network level may help in resolving security weaknesses and make direct penetration more difficult for the attackers. That said, internet content filtering (ICF) or even sandboxing solutions, however, might not be sufficient to protect against advanced threats in email. So, it is equally as important to implement the organizations’ security policies and effectively train employees to react with caution to any e-mails, even when they look legitimate.
Such was the case with Chase IT security, for example, which, in response to the breach that affected it, has trained its staff to spot such scams with encouraging results. They used solutions like a phishing simulator that “sent a fake phishing email to their employees in order to determine how well-attuned staff were to potential threats,” said Darren Dalasta, InfoSec Institute. The use of a simulation like InfoSec’s PhishSim tool, for example, can determine how they might respond to a real phisher.
For the most part, the best strategy for combating phishing is to train people to recognize phishing attempts; this can be done with mock simulated phishing scenarios (as with Infosec IQ) that can help to progress toward reducing user click rates and measure the ability to detect phishing emails. In addition to establishing best security practices and policies as well as implementing technical and non-technical countermeasures, awareness is the best tool companies have at their disposal to counteract phishing attempts.
References
Ashford, W. (2016, March 24). Phishing attack at US retailer underlines need for proactive security. Retrieved from http://www.computerweekly.com/news/450279834/Phishing-attack-at-US-retailer-underlines-need-for-proactive-security
Brumfield, J. (2016, April 27). Verizon’s 2016 Data Breach Investigations Report finds cybercriminals are exploiting human nature. Retrieved from http://news.verizonenterprise.com/2016/04/2016-verizon-dbir-report-security/
Demidova, N. (2014, June 11). Social network frauds. Retrieved from https://securelist.com/analysis/publications/63855/social-network-frauds/
Peterson, P., Lord, N., et al. (2016, May 18). Phishing Attack Prevention: How to Identify & Avoid Phishing Scams. Retrieved from https://digitalguardian.com/blog/phishing-attack-prevention-how-identify-avoid-phishing-scams
Green, A. (2014, September 11). Do Certain Traits Make People Vulnerable to Phishing? Retrieved from https://blog.varonis.com/certain-traits-make-people-vulnerable-phishing/
Heimerl, J. L. (2012, November 16). Incident Response: Are You Ready for a Phishing Attack? Retrieved from http://www.securityweek.com/incident-response-are-you-ready-phishing-attack
Hong, J. I. (2012). The State of Phishing Attacks. Communications of the ACM, Vol. 55 No. 1, Pages 74-81. DOI: 10.1145/2063176.2063197. Retrieved from http://cacm.acm.org/magazines/2012/1/144811-the-state-of-phishing-attacks/fulltext
Hussain, F. (2015, August 7). Spear Phishing Attack at Pentagon’s Network, Breached 4000 Military Accounts. Retrieved from https://www.hackread.com/pentagons-network-hacked-with-phishing-attack/
IT Secure. (n.d.). Verizon Report Indicates Cyberthieves Are Keying in on Human Nature. Retrieved from https://www.itsecureservices.com/verizon-report-indicates-cyberthieves-are-keying-in-on-human-nature/
King, R. (2014, April 8). Mining, Manufacturing at Highest Risk for Spear Phishing: Symantec. Retrieved from http://blogs.wsj.com/cio/2014/04/08/mining-manufacturing-at-highest-risk-for-spear-phishing-symantec/
McAfee, Inc. (2015, May 12). 97% Of People Globally Unable to Correctly Identify Phishing Emails. Retrieved from http://newsroom.mcafee.com/press-release/97-people-globally-unable-correctly-identify-phishing-emails
McDowell, M. (2009, October 22). Security Tip (ST04-014) – Avoiding Social Engineering and Phishing Attacks. Retrieved from https://www.us-cert.gov/ncas/tips/ST04-014
Seals, T. (2016, June 6). Phishing Activity Hits a 12-Year High. Retrieved from http://www.infosecurity-magazine.com/news/phishing-activity-hits-a-12-year/
Symantec Corporation. (n.d.). Symantec Phishing Readiness. Retrieved from https://www.symantec.com/services/cyber-security-services/cyber-skills-development/phishing-readiness

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Wilson, J. (2016, May 24). Financial services: under attack from cyber criminals. Retrieved from http://internationalbanker.com/technology/financial-services-attack-cyber-criminals/