Microsoft Office Dynamic Data Exchange(DDE) attacks
Microsoft Office programs are widely exploited by malware authors by embedding links, objects, and other payloads. Its effects often depend on how the user will interact with documents. Customarily embedded payloads are executed when the user enables macros, but this is not the only way to infect users. There are other methods as well which can infect involving minimal interaction. In this article, we will cover one such technique which exploits Dynamic Data Exchange(DDE) protocol.
Before we look into the exploits, we must uncover DDE protocol a bit further.

FREE role-guided training plans
Windows uses several ways to transfer data between applications, including the DDE protocol. The DDE protocol is based on messaging architecture and sends messages between applications, using shared memory to exchange data among applications. Applications that start the application act as DDE clients and applications that respond act as the DDE server.
Now Researchers from Sensepost discovered that the DDE protocol could be exploited inside MS Word with very minimal user interaction. Per their research, MS Word uses DDE in fields. Fields are an important part of MS Word and are used for handling the dynamic content inside an MS Word document.
In the section below, we can see that how DDE can be exploited in MS Word.
- I have created a new document and put some text into it. Now we should insert fields.
-
Click on Insert > Quick Parts> Fields

- The dialog box below will appear:

- Select Field Names > ={Formula} and then click ok.
-
It will insert a field with the text '!Unexpected End of formula' like below

-
Right-click on the field and click on Toggle Field Codes like below

-
After clicking the Toggle Field Codes, the field will change like below
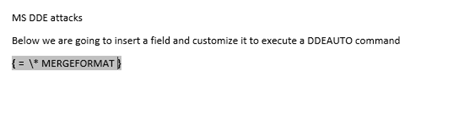
-
Now edit the text within {} to execute a command with DDEAUTO like below
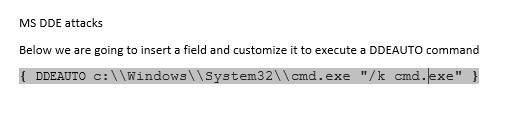
- This will tell Word to execute open cmd.exe automatically and create a persistent (/k switch) 'cmd.exe' process. Now save the document as .docx and then again open the document.
-
Since there is an embedded object, it asks the user to consent to whether they want the document to be updated from linked files or not because ultimately that is the whole purpose of the fields is to update the contents dynamically from linked files. If the user clicks 'yes,' then the attack proceeds, whereas if the user clicks No the attack is stopped right at this point.

-
If the user clicks 'Yes' in the above dialog, then the user is presented with below dialog box which says whether they want to start the application cmd.exe. This is an effect of DDEAUTO command. Again, if the user clicks Yes then the attack proceeds whereas if the user clicks No then again, the attack is stopped at this point.

-
If the user clicked 'Yes' then the below prompt appears. By this time, in this case, cmd.exe has already launched another instance of cmd.exe. In real-world exploit scenario, by this time, the user is already infected.

-
Execution of cmd.exe from MS Word

Researchers have also found that DDE is not only effective in MS-Word but also works for MS-Excel and MS-Outlook. In Outlook, this can be exploited even via calendar invites.
Per the latest news, malicious authors have already started using this weakness to entice users to click on their documents. Researchers have found out that an active campaign is exploiting this vulnerability and distributing Hancitor malware. Hancitor is a malware that downloads several Bank Trojans, and other ransomware onto the infected machine. It was distributed by malware authors as a macro-enabled document via a phishing email. Not only this, SANS reported that malware authors have updated the logic of Necurs Botnet (which is used to distribute Locky Ransomware) to exploit the DDE vulnerability from the old-fashioned Macro enabled MS document.
Now since DDE is a legitimate Microsoft feature, most antivirus vendors will not flag it, and expectedly they have not released any patch for it yet. So below are the some of the ways in which user can protect themselves.
- Thumb rule is never to open or provide consent to any document originated from an unknown source.
-
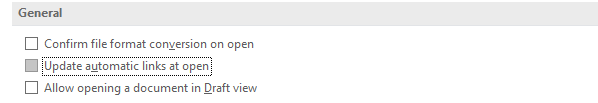
Turn off automatic update links opening
References
https://isc.sans.edu/forums/diary/Hancitor+malspam+uses+DDE+attack/22936/

FREE role-guided training plans
https://sensepost.com/blog/2017/macro-less-code-exec-in-msword/ss






