Malware Delivery in Phishing Campaigns
Malware has become more and more sophisticated, and with so many delivery methods and increasingly advanced phishing campaigns, it is not always easily detected or avoidable. To get started, let’s make sure you understand what malware and phishing are. Malware is a word used to describe any type of malicious software. It encompasses all terms used for this type of software to include, viruses, ransomware, Trojans, adware, spyware, etc.
Phishing is the use of technology to lure victims into providing sensitive and personal information. An attacker will use a phishing email, website, text message or even a phone call to trick a victim into providing information “voluntarily” or into clicking a malicious link that will redirect them to a nefarious website or download malicious software. Phishing is one way of delivering malware and using it to gather and obtain access to this sensitive data.
See Infosec IQ in action
There are two types of malware delivery you should understand, malicious attachments and download links.
Malicious Attachments
One way malware is delivered in phishing emails is through the use of malicious attachments. Emails are sent with attachments that are embedded with the malware. This is one of the most popular forms of malware delivery. An email appears with an attachment that may seem innocent, named something like “family photos,” and it appears to come from a trusted source so it could be easy to download the file without taking pause.
One of the first steps you should take to protect yourself is to set your email to not automatically download attachments. Also, before downloading an attachment you should scan your emails with up-to-date antivirus software. However, some malware are sent in a compressed format. Compressed files that are still in the email as an attachment may not get truly scanned by the antivirus software. If you are still suspicious of a particular attachment you can save the file to your hard drive and scan from there. This gives the antivirus better access to the code embedded in the file.
Ransomware has been on the rise recently, though this is not a new phenomenon. The first reported case of encrypting ransomware dates back to 1989. Ransomware is when a hacker sends malware to a victim that takes over their systems and encrypts it, making it very difficult to regain control. Without having access to the key used in the malware it can be difficult to detect when it is sent as an attachment in an email. Once the hacker gains control, they then demand some form of payment to release the decryption key giving the victim access to their system and precious files again.
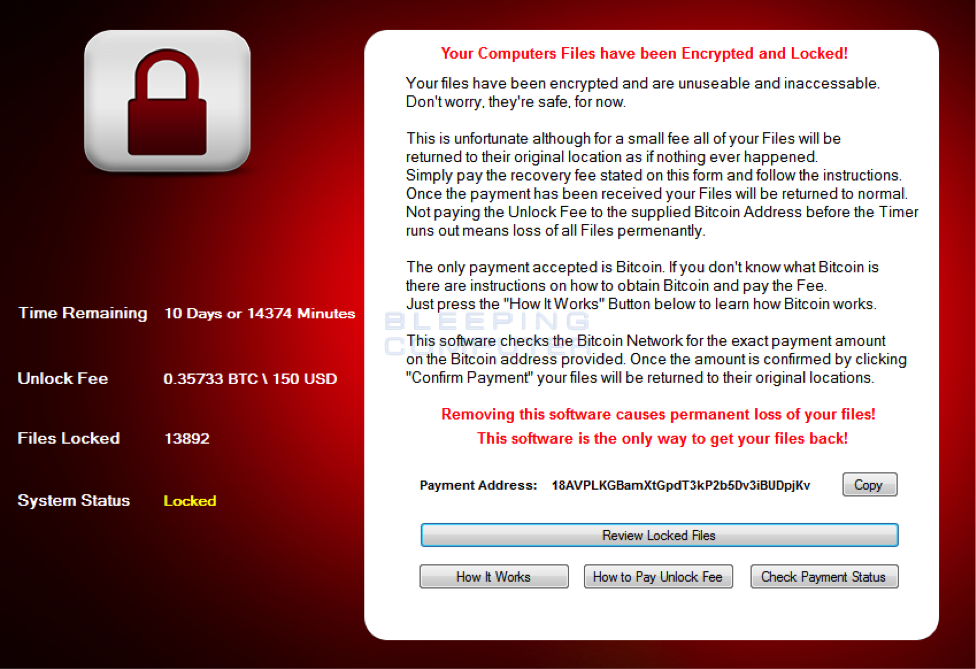
Over the past five years there have been more sophisticated attacks. In 2013, Cryptolocker claimed multiple victims. Cryptolocker was a Trojan that was sent as an attachment in an email, and once downloaded it would lock the computer screen then demand payment. In 2014, the wave rose with the release of more ransom Trojans, and an increase in victims. This trend does not seem to be slowing. CryptoHost is a recent attack that is bundled with a uTorrent installer and released upon installation. Once on the system it copies all of the files over into a password protected RAR file. Here is a screenshot of the CryptoHost ransomware splash screen:
Though most of these Trojans are targeting Windows systems, OS X users should not feel left out. KeRanger is a recent attack that uses a 2048-RSA public key to encrypt files and hold them for ransom. There are ways to avoid paying these ransoms which is what the FBI suggests. Symantec has laid out ways to alleviate ransomware if you become a victim, but the goal is to avoid ever becoming one.
Macro viruses are another way to deliver malware through attachments. Macros themselves are harmless, useful tools that are created to shorten steps, or to reuse code in development. You can take a long string of instructions and create a macro that will shorten the input to execute those instructions. Macros are very popular in Microsoft Office products, especially Word and Excel. People create them so they can save time as the macro will execute repetitive or tedious tasks with minimal commands or keystrokes.
Macro viruses are application based vice operating systems, meaning they can reach more users. Even though it is not specific to a certain operating system, applications use their own macro language so a virus written for Microsoft Word probably won’t work in Excel. The macro viruses are embedded in an affected document and emailed to the intended targets. How-To Geek explains how Office files can be dangerous to the health of your system. With the security updates in Microsoft products, the best way to avoid these types of viruses are to keep macro security features enabled and ensure your antivirus software is up to date.
Download Links
A majority of phishing emails contain links to malicious URLs that will either download code once clicked, redirect you to a malicious website that may gather your personal information based on your inputs, or release malware onto your system.
One recent popular malware delivery via links is through phishing eFax emails. These emails show a successful fax report that has an embedded link to a Dropbox account stating that’s where the fax is located. If an unsuspecting user clicks the link, the malware is installed on the computer. Many times variants of the CryptoLocker ransomware, often Cryptowall, or other Trojans are loaded. It then encrypts the files and holds the system hostage.
Other email types have embedded links that redirect the user to what appears to be a legitimate website, but is actually fraudulent. These types of emails vary in their approach. One approach is the threatening email. This is an email that is sent suggesting you have issues with some type of account you own and unless you click the link included in the email your account will be closed or be in some type of jeopardy.
Over the years these types of emails have gained validity. Hackers are getting better at including valid logos and company pictures. They are even spoofing company websites which makes the email appear authentic.
Another technique includes cybersquatting or typosquatting on website addresses that are close to legitimate sites. Cybersquatting, as defined on nolo.com, is registering a domain that is tied to someone else’s trademark, and then using that purchase to try and extort money out of businesses associated with those names. When the internet increased in popularity in the 90s and early 2000s, this happened often. McAfee® defines Typosquatting as a form of cybersquatting where a potential hacker will obtain a domain close to a popular site. This would be like someone buying yahooo.com waiting for someone to make that mistake when typing in Yahoo into their browser. They would then set up a malicious spoofing site that may look very similar to Yahoo leading the victim to believe they are at the correct place.
Typosquatting URLs are also used in phishing emails hoping the potential victim won’t notice the small typo. McAfee also discussed some of the early instances of this issue. When Annual Credit Report launched their website, AnnualCreditReport.com, so users could easily obtain their yearly credit report, many other sites popped up with similar names and emails were sent out with offers to users to visit the malicious URLs to obtain their free reports; instead they entered their personal information and contributed to their own identity theft.
Microsoft provides some tips on how to spot and avoid falling victim to Cyber and Typo Squatting, as well as loading potentially malicious links. Ensure your browsers are up to date with all security patches. Most browsers have failsafes in place to avoid committing a typo in reference to popular sites, even providing warnings if you go to a suspicious site. Most browsers are also up to date with known suspicious sites outside of those with similar URL names. It is suggested you set most visited sites to your favorites so you can use your favorites to avoid a typo. Legitimate websites that require you to enter personal information, e.g. AnnualCreditReport.com, or Paypal.com, for example, will use SSL to protect the user. These types of sites will have a lock in the web address and are normally proceeded with https:// versus http:// as shown below:
If you receive a threatening email stating your account is in jeopardy, do not click on any links embedded in the email, either call the company directly or go to their website that is hopefully stored in your favorites.
If you receive an email with links and you are not sure about the validity of the email take your mouse and hover over the hyperlink. DO NOT click on the link, you just want the mouse to hover over so you can match the link with what it should represent.
For example, you receive an email from PayPal stating you need to click on the link in the email to reset your password due to suspicious activity. If this were a valid email and you hovered over the link with your mouse, it would start with the paypal.com address with maybe a /passwordreset extension added. If the address appears to look odd, contact Paypal or whatever the legitimate company is to verify your account is fine, and they may ask you to forward the email to them so they can add it to their repository.
If you hover over the link and it has been shorted using tinyURL or Bitty, you can copy the shortened link and use a URL expander to get the full address. There are a few available like LongURL and Untiny.me. Copy the link into the extender and then examine it. Look for strange characters, like an excess amount of symbols instead of words, or suspicious naming schemes. They may not write badwebsite.com, but there will still be clues. Keep your virus scanning software up to date and scan emails you are unsure of.
Another way to avoid the results of downloading malware via a malicious URL is to use sandboxing techniques. Sandboxie is one sandboxing product that, once installed, allows the user to open attachments and will confine any potential malware that is downloaded within the confines of the sandbox, keeping all files outside of the sandbox safe. It is a way of separating your applications from the kernel running your operating system by creating a separate partition. Google Chrome also provides sandbox features. Every time a user opens a new tab, the activity that happens in the new tab is separate from the rest of the browser activity. This feature is still dependent on Windows so it is still susceptible to vulnerabilities, but in most cases, once you close that tab any malicious activity closes with it. You can also use Chrome or other browsers within a program like Sandboxie to provide even deeper protection.
Useful Tips
Before even opening a potential phishing email that may have a link or file, there are some things to pay attention to when you get a suspicious email: the “To” and “From” in the address lines. Make sure it comes from someone you actually know, not just an email address that appears close to a friend or relative. Before opening an email, you can hover over it with your mouse to see if the Sender that appears in your inbox is the actual sender.
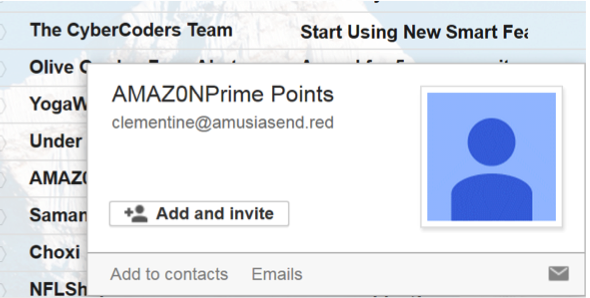
In the picture below an email came from someone that tried suggesting they were from Amazon, “Amazon Prime Points” in particular. At first examination, what should be a letter O in Amazon is actually a zero which is an initial clue. As the mouse was placed over the email the information popped up with the sender information. Examining the email address shows that this is not from anyone at Amazon whatsoever so there is no need to even open this email. It should be deleted immediately.
Another thing to check in the “To” line is if the email is addressed to a bunch of people you don’t know. At times phishing emails are sent to a mass list of users, often with similar email addresses. For example, if your email address is Bob@domain.com, and you receive an email addressed to you, bob1@domain.com, bob2@domain.com, bobb@domain.com, etc., this is probably a phishing email hoping to catch a bite. In the body of the email, check for spelling errors and poor grammar. Phishing emails tend to be riddled with them. Make sure you use the spam settings to catch emails like this before they even make it to your inbox. Always mark suspicious emails as spam.
Conclusion
The Department of Homeland Security has a United States Computer Emergency Readiness Team (US-CERT). They release warnings in relation with current technology threats and ways to prevent becoming a victim. During the holidays the use of phishing scams increases, so the US-CERT website is a great place to check for current threats and general security tips.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
US-CERT has also provided some overall tips to avoid being scammed by phishing emails. One is setting up multiple email accounts, one exclusively for checking emails, and another for web surfing. You could also have a computer exclusively for internet access, and one air gapped (completely offline) system used to store data. Always scan files with up to date antivirus, but the biggest tip is to just trust your instincts. If something seems suspicious it probably is. Better to delete an email being overly cautious than to become a victim. You can always have the sender of a valid email resend the email if it is needed, but if your system gets damaged from being infected by malware, that can take time, effort and possibly money to repair. Unfortunately, cybercrime is not on a decline and will only continue to rise, so we have to be even more vigilant and cautious in protecting our assets and possibly our sanity.