Limiting Automated Access
Automated tools are used to carry out many security attacks to online services. There are different protection mechanisms to narrow down such attacks and one such mechanism is the usage of CAPTCHA. CAPTCHA or Completely Automated Public Turing test to tell Computers and Humans Apart is a mechanism adopted by many webservers to limit automated access. The term "CAPTCHA" was coined in 2000 by Luis Von Ahn, Manuel Blum, and Nicholas J. Hopper of Carnegie Mellon University, and John Langford of IBM. They are challenge-response tests to ensure that the users are indeed human. The purpose of a CAPTCHA is to block form submissions from spam bots – automated scripts that harvest email addresses from publicly available web forms. A common kind of CAPTCHA used on most websites requires the users to enter the string of characters that appear in a distorted form on the screen.
CAPTCHAs are used because of the fact that it is difficult for the computers to extract the text from such a distorted image, whereas it is relatively easy for a human to understand the text hidden behind the distortions. If a CAPTCHA is solved successfully, then it is assumed that the user is human and not a bot. Even if a bot succeeded in solving one of the CAPTCHA, there is no guarantee that it will be successful the next time, since CAPTCHA's are chosen from a wide variety of selections.

11 courses, 8+ hours of training
Many websites use CAPTCHA to tell Computers and Humans Apart in an attempt to block automated interactions with their sites. These efforts may be crucial to the success of these sites in various ways. For example, Gmail improves its service by blocking access to automated spammers, eBay improves its marketplace by blocking bots from flooding the site with scams, and Facebook limits creation of fraudulent profiles used to spam honest users or cheat at games. The most widely used CAPTCHA schemes use combinations of distorted characters and obfuscation techniques that humans can recognize but that may be difficult for automated scripts.
1. How to create a CAPTCHA
To create a CAPTCHA, first look at different ways humans and machines process information. If something falls outside the structure of those instructions, then the computer is not capable to process it. It should be coded with proper instructions, and only then can the information be processed.
In case of reCAPTCHA an Optical Character Recognition (OCR) can be used to read the letters from the books and is stored in the database. Then the OCR reports the words that cannot be correctly read by it and these words are given to the users to fill the CAPTCHA.
One way to create a CAPTCHA is to pre-determine the images and solutions it will use. This approach requires a collection of CAPTCHA solutions that include all the different varieties. If a spammer managed to find a list of all CAPTCHA solutions, then an application can be created to brute force the CAPTCHA with every possible match. Then that application's database must contain more than 10K different CAPTCHAs to be within the boundary line of a good CAPTCHA.
2. CAPTCHA Implementation
These are the simple guidelines that must be ensured for CAPTCHA implementation.
Embeddable CAPTCHAs
The easiest implementation of a CAPTCHA to a Website would be to insert a few lines of CAPTCHA code into the Website's HTML code. An open source CAPTCHA builder can be used which will provide the authentication services remotely. One of the most popular among them is reCAPTCHA project.
CAPTCHA Logic
First some random texts are generated and some random effects are applied and it is converted into an image. Then the original text is stored somewhere, which is the correct answer to the converted image. This original text can be stored as a server-side session variable, cookie, file, or database entry. The generated CAPTCHA is presented to the user, and prompted to submit the answer. Then a back-end script checks the answer supplied by the user by comparing it with the original text, i.e., the answer. If the value is empty or incorrect, then a new CAPTCHA is generated. It is ensured that users don't get a second chance to answer the same CAPTCHA.
If the answer supplied by the user is correct, then the form post is set as successful and processing can continue. If applicable, the generated CAPTCHA image is deleted.
Accessibility
It must be accessible and should be based solely on reading text or other visual-perception tasks. If a CAPTCHA prevents visually impaired users from accessing the protected resource, such CAPTCHAs may make a site incompatible with disability access rules in most countries. Any implementation of a CAPTCHA should allow blind users to get around the barrier, for example, by permitting users to opt for an audio or sound CAPTCHA.
Image Security
CAPTCHA images of text should be distorted randomly before being presented to the user. Many implementations of CAPTCHAs use undistorted text, or text with only minor distortions. These implementations are vulnerable to simple automated attacks.
Script
Security
A high-level of script security should be enabled, and building a secure CAPTCHA code is not easy. In addition to making the images unreadable by computers, the system should ensure that there are no easy ways around it at the script level. One of the steps is that the system must pass the answer to the CAPTCHA in plain text as part of the Web form. Also, systems with a solution to the same CAPTCHA should not be used multiple times.
Scalability
CAPTCHA should be scalable in the sense that, even after the widespread adoption of the same in a large number of websites, it should provide security. In some CAPTCHA cases, if some of them were adopted in a large number of websites, then their security would become flawed and they would be vulnerable to bot attacks. One of the examples is of a CAPTCHA puzzle asking text-based questions, such as a mathematical question "what is 2+2". Since a parser could easily be written that would allow bots to bypass this test, such "CAPTCHAs" rely on the fact that few sites use them, and thus that a bot author has no incentive to program their bot to solve that challenge. True CAPTCHAs should be secure even after a significant number of websites adopt them.
3. Types of CAPTCHA
Text-Based CAPTCHAs
These are simple to implement and are based on some questions that are given to users that can only be solved by a human being. Such questions can be like any of the following:
- Which word from the list: "claw, generous, verbosity" has "v" as a first letter?
- What is the color in the list: coat, school, apple, pink or tongue?
- If yesterday was a Sunday, what is today?
Text-based CAPTCHAS also involve text distortion and are classified as follows:
reCAPTCHA
reCAPTCHA is a free CAPTCHA service that helps to digitize books, newspapers and old time radio shows. reCAPTCHA improves the process of digitizing books by sending words that cannot be read by computers to the Web in the form of CAPTCHAs for humans to decipher. More specifically, each word that cannot be read correctly by OCR is placed on an image and used as a CAPTCHA. This is possible because most OCR programs alert you when a word cannot be read correctly.
Each new word that cannot be read correctly by OCR is given to a user in conjunction with another word for which the answer is already known. The user is then asked to read both words. If they solve the one for which the answer is known, the system assumes their answer is correct for the new one. The system then gives the new image to a number of other people to determine, with higher confidence, whether the original answer was correct.
Answers to reCAPTCHA challenges are used to digitize textual documents. It's not easy, but through a sophisticated combination of multiple OCR programs, probabilistic language models, and most importantly the answers from millions of humans on the Internet, reCAPTCHA is able to achieve over 99.5% transcription accuracy at the word level.
GIMPY
Gimpy works by choosing ten words randomly from a dictionary, and displaying them in a distorted and overlapped manner. It arranges the words in pairs and the each word pair overlaps one another. Then, the users have to type the three correct words to pass the CAPTCHA test. It is one of the more difficult variants of a word-based CAPTCHA.

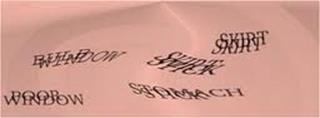
Ez – Gimpy
This type of CAPTCHA works by picking words from dictionary, applying it with distortion and cluttered background. Ez- Gimpy can also be said as a simplified variant of Gimpy CAPTCHA. The difference is that it picks only a single word from dictionary.


Baffle text
Unlike Gimpy variant CAPTCHAs, baffle text produces pronounceable character strings that are not in the English dictionary. This method was developed by Henry Baird at University of California. It produces a random masking to degrade images of non-pronounceable character strings.
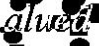
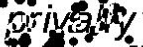
MSN CAPTCHA
The proprietary CAPTCHA of Microsoft that contains eight characters with a combination of upper characters and digits.
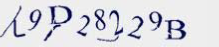

Graphic-based CAPTCHAs
This type of CAPTCHA produces challenges with a combination of pictures or objects that have some similarity for the user to guess around.
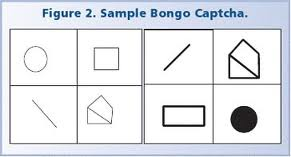
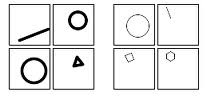
Bongo CAPTCHA
Bongo CAPTCHA uses visual patterns and prompts users to solve the problem. Normally this type of CAPTCHA provides two types of images, and the user is given another image. Then the user has to match the two images with the latter one.
PIX
PIX contains a large database of labeled images of various concrete objects including horse, flower, house etc. Then the program randomly chooses one of the objects and selects four random images of the same. Then this will be presented to the user and asked about what the picture is of.




ESP-PIX
This is one of the variants of PIX CAPTCHA, where a picture is selected with word that best describes the image. The important factor is that ESP-PIX is a CAPTCHA script that instead of asking to type letters, requires that you look at a set of pictures and then select the word that best describes all the images.

3D CAPTCHA
These are CAPTCHA's with three-dimensional pictures, which makes it more difficult for the computer to recognize and is easier for a human. The advantage is that any image can be transformed into a CAPTCHA image and it will be easier for humans to solve the 3D CAPTCHA than the text based ones. But the risk in 3D CAPTCHA is that an image analysis tool can be used by a bot to solve it.

Image Orientation CAPTCHA
This type of CAPTCHA was developed by Google, in which a large database of images is paired with automatic image orientation detectors that can be easily reoriented by the users. Then a social feedback mechanism is given by Google to verify whether the remaining images have a human-recognizable upright orientation. The advantage of this type of CAPTCHA is that it is language independent and does not require text entry.

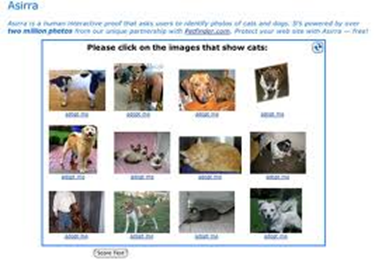
Microsoft ASIRRA or Image recognition CAPTCHA
Microsoft ASIRRA (Animal Species Image Recognition for Restricting Access) or Image recognition CAPTCHA contains a database of labelled images provided by petfinder.com. In this, users have to match the images of cat and dog in order to pass the test. Firstly the CAPTCHA was thought of as a success and couldn't be breached by the computer. But later it was proved that it is not difficult to distinguish a cat and dog by computer.
Geometric CAPTCHA
This type of CAPTCHA can also be said as a variant of the math CAPTCHA, which gives bot-challenging objectives to humans as well as computers. This CAPTCHA is also breakable by providing random answers and is not secure.

Audio-based CAPTCHAs
The CAPTCHA picks a word or letters or its combinations and transforms into a downloadable sound clip and insert some type of noise as distortion. This distorted sound clip is presented to users, who are asked to enter the contents after hearing it.
Audio-based CAPTCHA utilizes the human ability to recognize the sound, even if added with the distortion. This type of CAPTCHA is mainly intended for vision-impaired people and was proposed by Carnegie Mellon University and is now owned by Google. These sound-based CAPTCHAs have been deployed on Google, Facebook, and Yahoo and so on.
An audio CAPTCHA is usually located as part of the same interface as the text CAPTCHA, and is given as an alternative for users with poor vision. The user is normally asked to click on the sound icon, upon which they will hear spoken words that sound rather distorted, or which are placed on top of a noisy background. The disadvantages of audio CAPTCHA is that the noise provided in the background sometimes overwhelms the main message.
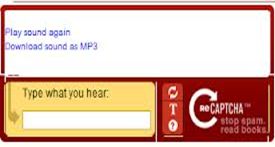
Google Audio CAPTCHA
Video-based CAPTCHAs
This type of CAPTCHA uses video or animation techniques which a user is required to watch and give input. One of the top providers of video CAPTCHA is NuCaptcha that provides CAPTCHA implementation using animation techniques in order to make it harder for spam bots to decipher the characters. Its creators claim that NuCaptcha has the highest usability and security levels of any CAPTCHA on the market.
NuCaptcha uses patent-pending next generation animated CAPTCHA technology. Testing has shown that animated CAPTCHA puzzles are easier for humans to recognize and solve than static, scrambled CAPTCHA images.
NuCaptcha uses patent-pending next generation animated CAPTCHA technology. Testing has shown that animated CAPTCHA puzzles are easier for humans to recognize and solve than static, scrambled CAPTCHA images.

4. Bypassing a CAPTCHA
Bypassing a CAPTCHA is a challenging one, because it is not about listing what it says. The core task is to teach a computer how to process information in a way similar to humans. Breaking CAPTCHAs doesn't mean to concentrate on making computers smarter, but reducing the complexity of the problem posed by the CAPTCHA.
For example: an online form is protected using a CAPTCHA that displays English words and the application warps the font slightly, stretching and bending the letters in unpredictable ways. In addition, the CAPTCHA includes a randomly generated background behind the word.
A programmer wishing to break this CAPTCHA could approach the problem in phases. Firstly an algorithm should be written; in this one step might be to convert the image in grayscale. That means the application should remove all the color from the image, with one of the levels of obfuscation the CAPTCHA employs.
Then, the algorithm should tell the computer to detect patterns in the black and white image. The comparison of each pattern to normal letters should be carried out and it should match with normal letters. If in this case only a few letters are matched, then it might cross reference those letters with a dictionary of English words. Thus the similar ones should be put into the submit field. This is one of the effective ways of bypassing a CAPTCHA. It doesn't guarantee success all the time. But it can provide an average range of success and thus gives a way to bypass the CAPTCHA.
If the program can only match a few of the letters, it might cross reference those letters with a database of English words. Then it would plug in likely candidates into the submit field. This approach can be surprisingly effective. It might not work 100 percent of the time, but it can work often enough to be worthwhile to spammers.
4.1 Breaking CAPTCHAs using Session ID
CAPTCHAs normally don't delete the session even if the correct answer is entered. This session can be reused and can be used to bypass the CAPTCHA by automating the request to the CAPTCHA. This is done storing the session ID of the CAPTCHA and the CAPTCHA plain text. This process can be automated by resending the session ID and CAPTCHA plain text multiple numbers of times by changing the user data. This automated process can handle multiple requests in a stretch until the session expires, and in case of expiration, manual steps can be used to reconnect with a new session ID and CAPTCHA text.
Normally CAPTCHA-breaking software uses image recognition routines to decode CAPTCHA images, and this can be used to bypass and thus make it easy to hack the CAPTCHA images.
4.2 Breaking a visual CAPTCHA
Gimpy CAPTCHA is just an application of a general framework that we have used to compare images of everyday objects and even find and track people in video sequences.
- Locate possible letters at various locations:
A shape-matching technique is used to guess the letters in the image by looking at points in the image. Then these points are compared point by point on each of the 26 letters. The comparison is carried out by recognizing the background clutter and deformation of letters. Then the output given is that of 3 to 5 letters per each letter in the image.
The first step is to hypothesize a set of candidate letters in the image. This is done using our shape-matching techniques. The method essentially looks at a bunch of points in the image at random, and compares these points to points on each of the 26 letters. The comparison is done in a way that is very robust to background clutter and deformation of the letters. The process usually results in 3-5 candidate letters per actual letter in the image. In the example shown in Fig 5.1, the "p" of profit matches well to both an "o" or a "p", the border between the "p" and the "r" look a bit like a "u", and so forth. At this stage we keep many candidates, to be sure we don't miss anything for later steps.
- Construct graph of consistent letters:
The pair of letters is analyzed to check whether it is consistent or not and these words can be used to form a word. Next, we analyze pairs of letters to see whether or not they are "consistent", or can be used consecutively to form a word.
- Look for plausible words in the graph:
From the graph, there are multiple words, and this has to be shortlisted to choose the appropriate one. For this we have to select the real words and give them a score to match their individual letters to the image and thus the CAPTCHA can be bypassed.
4.3 Social Engineering attacks on CAPTCHA
Trojans combined with social engineering activity can be used to crack the CAPTCHA. A Trojan named TROJ_CAPTCHAR can acts a game and at each stage of the game the user is asked to solve a CAPTCHA. Then the result is relayed to a remote server where a malicious user is provided with the same. Thus the CAPTCHAs of legitimate sites can be solved and the solutions can be matched to bypass the CAPTCHA in an automated manner.
5. Applications of CAPTCHAs
CAPTCHAs are used in various applications to identify human users and to restrict access to them.
Some of them are:
- Online Polls
Online polls were affected by bots that vote automatically to create large counts to the respective side. They might create a large number of votes which would then falsely represent the poll winner. Thus CAPTCHAs can be used in websites that have polls to protect them from being accessed by bots, and hence increase the reliability of the polls.
- Blogs and Forums
Spam comments on blogs and forums were one the major problems that bloggers and other forums administrators faced. Almost all bloggers are familiar with bots that submit a large number of posts with some URL embedded in order to increase the SEO. CAPTCHAs can be used in order to prevent a bot from commenting on a large number of posts in the blogs. But it doesn't mean that it will stop a spammer from posting manually in the comment space provided.
- Email account registration
Email service providers like Google and Yahoo were flooded by accounts created by bots. In order to stop these spam accounts, several email service providers and web registration service providers use CAPTCHAs in their account registration page. This is to ensure that no bots intervene in the activity of form filling.
- Search engine bots
Web pages can be kept as unindexed to prevent search engines from finding them easily. An HTML tag can be used to prevent search engine bots from reading web pages. However, this tag doesn't ensure that search engine bots don't index them. In order to truly guarantee that bots won't enter a web site, CAPTCHAs can be used by restricting to only human indexers.
- Spam Email
All over the Internet there are several email addresses embedded in Websites. Bots are used by spammers in order to collect those email addresses and used to forward junk and spam emails. This can be eliminated by using CAPTCHAs to retrieve the full email address.
- Dictionary Attacks
CAPTCHAs can also be used to prevent dictionary attacks in password systems. It prevents a brute force attack from iterating through the entire space of passwords. A CAPTCHA can also be popped up, requiring the user to solve after a certain number of unsuccessful logins.
- reCAPTCHA (Digitizing Books)
reCAPTCHA is a free CAPTCHA service that helps to digitize books, newspapers and old time radio shows. reCAPTCHA improves the process of digitizing books by sending words that cannot be read by computers to the Web in the form of CAPTCHAs for humans to decipher. More specifically, each word that cannot be read correctly by OCR is placed on an image and used as a CAPTCHA.
6. Conclusion
Surely CAPTCHA can be used to prevent automated collection or access to Webservers, and there are a lot of issues related to CAPTCHA in cases like text and image distortion that become difficult for humans to solve. There are several issues related with text-based CAPTCHAs like Gimpy. Most commonly the issue arises when there is confusion with the conversion of letters on characters like 'm' confused with 'rn', and 'd' with 'cl' etc. Also a language problem also arises when a person who is unfamiliar with English or some other language is presented with a CAPTCHA of the same language. When longer length CAPTCHAs are used, it becomes difficult for users to solve them without any mistakes. Also, the CAPTCHA's presentation should be carried out in a way that it should not be confused with font color and background color.
In the case of audio CAPTCHAs, when a large distortion is provided in the background noise, then it becomes difficult for the users to categorize the original sound and the noise. Also the contents in the audio CAPTCHAs are based on specific language, and if a user is unfamiliar with the pronunciation and style of that specific content, it would become hard to solve it. Audio CAPTCHAs can also cause compatibility issues, and may require the use of Jscript in that particular Webpage.
7. References
http://computer.howstuffworks.com/captcha.htm
http://dspace.cusat.ac.in/jspui/bitstream/123456789/2228/1/CAPTCHA.pdf
http://cdn.ly.tl/publications/text-based-captcha-strengths-and-weaknesses.pdf
http://textcaptcha.com/

11 courses, 8+ hours of training
http://www.ijens.org/Vol_11_I_05/117005-8383-IJVIPNS-IJENS.pdf



