IOS Application Security Part 16 - Runtime Analysis of IOS Applications using iNalyzer
In the previous article, we looked at how we can perform static analysis of IOS Applications using iNalyzer. In this article, we will look at how we can use iNalyzer to perform runtime analysis of IOS applications. We can invoke methods during runtime, find the value of a particular instance variable at a particular time in the app, and basically do anything that we can do with Cycript.
In the last article, we were successfully able to generate the html files via Doxygen and open it up to view class information and other information about the app. For runtime analysis, we will be using the Firefox browser. The developer of this tool has personally recommended me to use Firefox as this may not work on other browsers. However, it seemed to be working fine for me on Chrome as well.
To open up the runtime interpreter, first of all open up the index.html file generated by Doxygen for the app that you want to analyze, then just double tap the left arrow key.
[caption id="" align="alignnone" width="621"]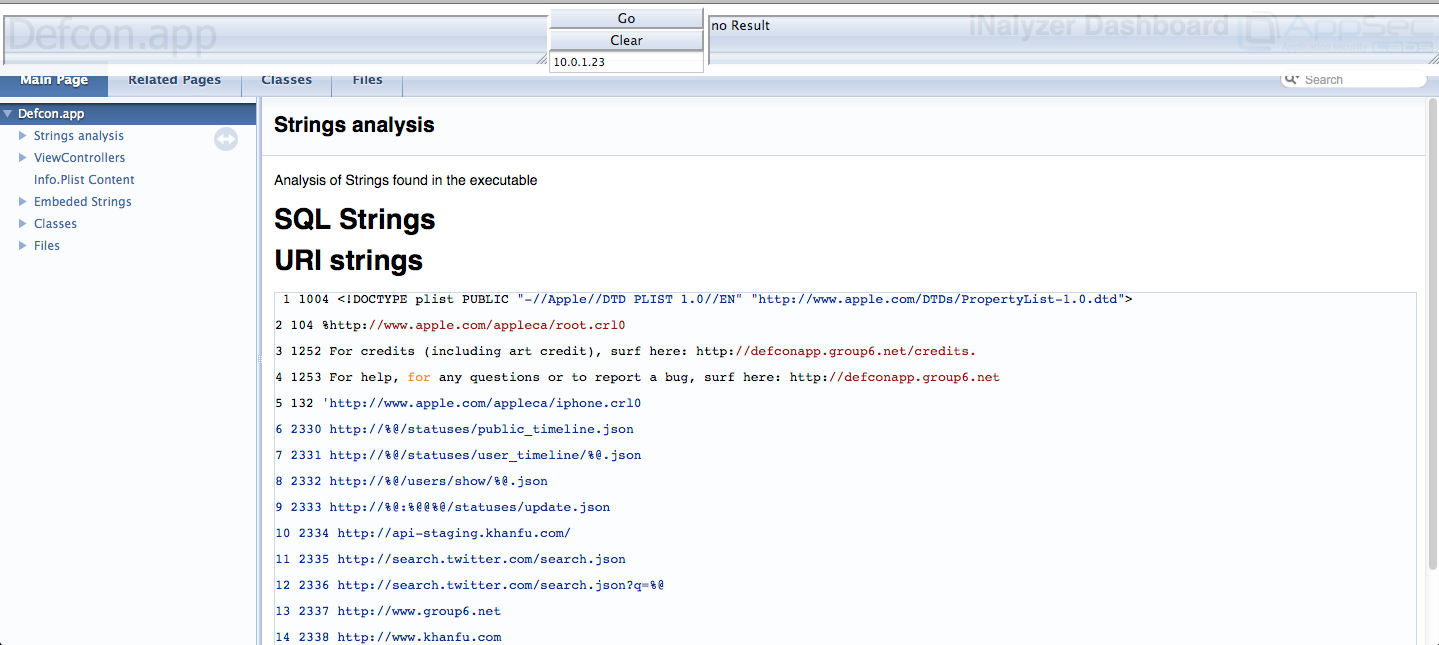 Click to Enlarge[/caption]
Click to Enlarge[/caption]
You will see a console come up on the top as shown in the figure above where we can type commands. The first thing to do is to tell iNalyzer the ip address of your device, which in this case is 10.0.1.23. So let me just enter that on the box in the middle and press enter.
[caption id="" align="alignnone" width="620"]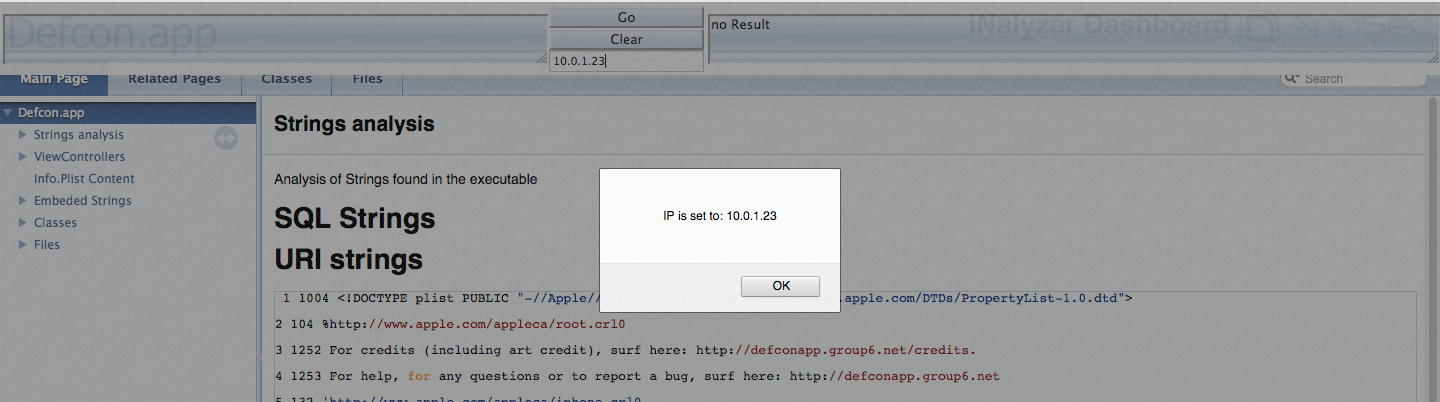 Click to Enlarge[/caption]
Click to Enlarge[/caption]
Once the IP address has been set, make sure that the app that you want to analyze is open (i.e on foreground) on your device and your device is not in sleep mode. This is important because if your app is in the background or the device is in sleep mode, then your app is temporarily paused by the operating system and hence it is not possible to perform any kind of runtime analysis on the app.
Once the app is open, just type any command on the console, just like you would type on Cycript.
[caption id="" align="alignnone" width="629"]![]() Click to Enlarge[/caption]
Click to Enlarge[/caption]
As we can see, we get a response. We can now type any cycript command that we want here.
Let's hide the status bar from the app. We can do this with the command [[UIApplication sharedApplication] setStatusBarHidden:YES animated:YES];
[caption id="" align="alignnone" width="614"]![]() Click to Enlarge[/caption]
Click to Enlarge[/caption]
We see that we don't get a response. Its because the response type of this method is void.
[caption id="" align="alignnone" width="611"]![]() Click to Enlarge[/caption]
Click to Enlarge[/caption]
However, the status bar has been hidden in the app. Note that we no longer see the time on the top.
Similarly, we can also find the delegate class of this app.
[caption id="" align="alignnone" width="626"]![]() Click to Enlarge[/caption]
Click to Enlarge[/caption]
We can also set the application icon badge number. In this case, let us set it to 9000.
[caption id="" align="alignnone" width="612"]![]() Click to Enlarge[/caption]
Click to Enlarge[/caption]
And it works.

Since this is exactly similar as having a cycript console, we can enter javascript code as well or any other command from Cycript's documentation. Here is a command i entered from the Cycript tricks page.
[caption id="" align="alignnone" width="626"]![]() Click to Enlarge[/caption]
Click to Enlarge[/caption]
Similarly, i can create a function using both Objective-C and javascript syntax. If you are not following cycript here, please refer to the earlier parts on this series that talk about Cycript and its usage in detail.
[caption id="" align="alignnone" width="619"]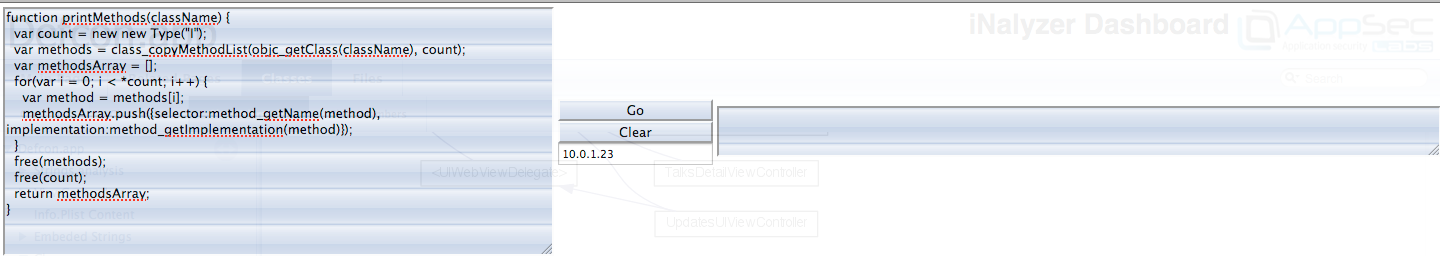 Click to Enlarge[/caption]
Click to Enlarge[/caption]
I can then use that method whenever i like.
[caption id="" align="alignnone" width="622"]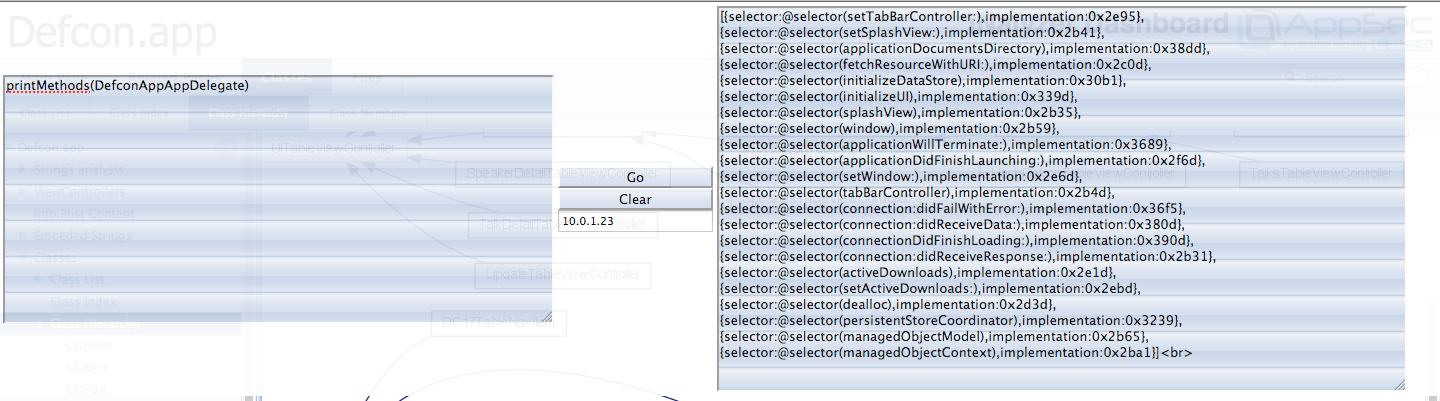 Click to Enlarge[/caption]
Click to Enlarge[/caption]
In part 9 on this series, we had discussed about an application named Snoop-it. iNalyzer is very similar to Snoop-it. However both have their advantages and disadvantages. At the time of writing of the article on Snoop-it, it didn't allow for method swizzling, whereas iNalyzer does. Similarly, iNalyzer doesn't allow us to monitor api calls whereas Snoop-it does have that feature. Hence, both these applications have their pros and cons.
Conclusion
In this article, we looked at looked at how we can leverage the power of iNalyzer to perform runtime analysis of IOS applications. iNalyzer is a great tool in the arsenal for anyone interested in learning IOS application security as it makes our task much more easier and efficient.
References
- iNalyzer





