How Hackers Violate Privacy and Security of the Smart Home
The Technology Invades Our Living Room
The rapid growth of the paradigm of the Internet of Things is influencing in a significant way our concept of "house." Modern homes are full of smart devices and a new generation of smart appliances promises to make our life easier and more comfortable, but we cannot underestimate that risk of cyber attacks.
The solutions for home automation are flooding the market, but these devices in the majority of cases lack security; security experts are aware that smart cameras and meters are an easy target for hackers.

FREE role-guided training plans
Earlier in 2015, experts at Synack security firm analyzed 16 home automation devices from cameras to home automation controllers to thermostats. Unfortunately, the results of the tests are disconcerting, the researchers were able to hack almost every appliance.
"Really, the state of security on these things right now is pretty atrocious," said Colby Moore, security research engineer at Synack.
The experts played different attack scenarios simulating different situations that could expose our lives to hacking attacks, including the implant of nasty stuff before products leave the factory and the hijacking of mobile apps designed by manufacturers for their remote control.
By exploiting vulnerabilities in home automation devices, attackers can gather information on targets, threatening their privacy and safety, understanding their behavior and patterns.
According to the finding of the Synack study, connected cameras are the automotive devices having the greatest number of security vulnerabilities. Synack found that the smart devices tested don't encrypt data and implement weak password policies. All of the connected thermostats studied were affected by serious security issues that could be exploited to control them; even the home automation centers present numerous flaws.
The principal problem when dealing with Internet of Things devices is that manufacturers don't have strong backgrounds in cyber security. It is not easy for manufacturers to design smart objects that could be used in so different scenarios.
"A lot of these device manufacturers are just not security people and they really just don't have security people on staff, especially when it comes to IoT start-ups," Moore said. "What they are doing is phenomenal with all of these new uses for technology. But security isn't a concern for everybody. It's ship now and patch later mentality."
"There's no industry standard and there's is no way to tell if a product is secure or not if you are the average Joe. That is a big problem and it's a problem that the industry needs to address and is thinking about," Moore said.
A Hacker on the Doorstep
A recent research conducted by the security firm Veracode, titled "The Internet of Things: Security Research Study," analyzed household IoT devices, revealing that they are exposing users to a wide range of threats, including data theft and sabotage.
The devices analyzed in the study have a significant capability to interact with the physical environment (e.g., hardware sensors) and peer devices; for this reason, a cyber attack could result in a physical intrusion in the smart home where they are deployed.
The experts analyzed six household IoT devices with up-to-date firmware version and performed a set of uniform tests. The tests are focused on four different domains: user-facing cloud services, back-end cloud services, mobile application interface, and device debugging interfaces.
The six household IoT devices analyzed by the Veracode experts are:
- Chamberlain MyQ Internet Gateway: Internet-based remote control of garage doors.
- Chamberlain MyQ Garage: Internet-based remote control of garage doors, interior switches, and electrical outlets.
- SmartThings Hub: A central control device for home automation sensors, switches and door locks.
- Ubi: The Unified Computer Intelligence Corporation manufactures this always-on, voice-controlled device for answering questions, controlling home automation and performing tasks such as sending emails and SMS messages.
- Wink Hub: A central control device for home automation products.
- Wink Relay: A combination hub and control device for home automation sensors and products.
The researchers discovered a number of security issued affecting all the devices, including authentication flaws and arbitrary code execution flaws, which could be exploited to gain complete control of the devices.
The exploitation of the flaw allowed the researchers to control the garage door and collect information related to the presence of people in the house. This information exposes users to the risk of robbery.
Leveraging data managed from Ubi could enable attackers to collect a huge quantity of information on the user's habits, which can advantage a robbery, or even a stalking activity.
The hack of the Ubi device or Wink Relay could result is a serious violation of the user privacy because it could allow attackers to control the microphones inside the home environment.
Now we will analyze in detail other common smart objects present in modern houses, discovering why the lack of security by design could harm our security and privacy.
Smart TV, Smart Meters, Smart Fridge … Open Door to the Hackers
Modern houses are full of connected devices; smart TVs, smart meters and fridges collect a huge quantity of information regarding our behavior and in many cases this information is transmitted to remote servers without the user's knowledge.
In 2013, the researcher Malik Mesellem demonstrated that smart TV hacking is a real menace, we used for his test Samsung models which he forced to reboot by sending a specifically crafted HTTP GET request.
In the specific case, the researchers demonstrated the feasibility of a DoS attack, but it was just the beginning because, in recent months, experts uncovered security issues that could transform smart TV's entry point for hackers in our homes.
One year later, in February 2014, researchers at ReVuln demonstrated how to exploit the last firmware update for Philips smart TV to steal user's cookies and other sensitive data.
The hack was very insidious: It took a few seconds to carry out and it was impossible for the victims to detect it.
Attackers connecting to a Miracast-enabled Wi-Fi network were able to browse and download any files that may be contained on USB drives plugged into the Philips smart TV. The researchers at ReVuln also demonstrated that it was possible to steal browser cookies that contain sensitive information and that are used in some cases by many web services for authentication purpose.
The researchers at ReVuln published a video to show how an attacker can easily steal from the Philips smart TV the authentication cookies for an existing Gmail account and also user's data from a USB drive connected to the device.
The attacks on smart TV are evolving and this class of smart devices is being exploited to hack systems inside the domestic network and exfiltrate user data.
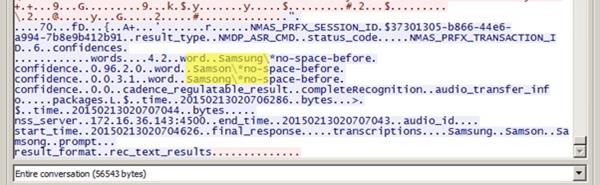
In 2015, things don't get better: Security researchers discovered that the Samsung smart TV sends unencrypted voice recognition data and text information across the Internet without encrypting it, allowing hackers to capture it.
Figure 1 - Samsung smart TV data traffic
A hacker could be able to spy on users exploiting the functionalities in modern smart TV and in this way accessing its domestic LAN. Such flaws and implementations open the doors also to surveillance activities that could be operated by persistent attackers (e.g., intelligence agencies) that could access user traffic directly from internet service providers or by accessing the Internet backbones.
Let's think for example about the smart meters. Last year, the researchers Javier Vazquez Vidal and Alberto Garcia Illera discovered millions of network-connected electricity meters that were susceptible to cyber attacks due to lack of proper security controls.
Figure 2 - Smart Meter
In Spain, there are three major utility companies, Endesa, E.ON, and Iberdrola and the number of installed Smart meters is nearly 8 million, which corresponds to nearly 30 percent of households.
Bad actors, accessing the smart meters, could cause a blackout or conduct fraudulent activities, including billing fraud. The researchers explained that poorly protected credentials stored in the devices provided by one of the companies could let attackers gain access of smart meters; during their session tests they were able to take full control of any device and modify its unique ID to impersonate other customer.
The researchers discovered a flaw that affects the code running on the smart meters. This vulnerability could be exploited remotely to shut down power supplies to individual households, access meter readings, transfer meter readings to other customers, and also inject "network worms" that could cause serious problems to the overall network.
The experts explained that the smart meters deployed by the Spanish utility company use AES-128 encryption to protect data, but this encryption algorithm is not invulnerable to a brute-force attack.
They were also able to use the smart meter to launch attacks against the power network. The researchers avoided disclosing also the name of the smart meter manufacturer for obvious reasons; immediately the Spanish utility company that deployed the smart meters started the necessary actions to mitigate the risks and improve the security of the devices.
The attack scenario is disconcerting because a threat actor could carry on an attack on a large scale and shut down an entire country by hacking the network of smart meters
"Oh wait? We can do this? We were really scared," said Vazquez Vidal, "We started thinking about the impact this could have. What happens if someone wants to attack an entire country?" he said.
Let's go on: What do you think about hacking smart thermostat?
Early 2015, security experts from TrapX Security demonstrated how to hack an Internet-connected thermostat produced by the company Nest, a firm controlled by Google. As explained several times, IoT devices in our home are equivalent to open doors for hackers, in the specific case the experts hacked the Nest thermostat and succeeded in hacking other devices sharing the same home network.
Figure 3 - NEST smart thermostat
The hack is not simple to implement because the attack chain starts with a physical access to the device. The TrapX experts started from a research released a couple of years ago by a group of researchers at the University of Central Florida, led by engineering professor Yier Jin. The group jailbreaked the Linux operating system running on the Nest Thermostat by accessing it through its USB port. Then they loaded their custom firmware on the thermostat that would stop your thermostat data from being sent back to Nest's servers. "The problem is with the way the hardware is built," said Jin in a phone interview on Thursday. "That's why, after we released this hack almost one year ago, there's still no fix yet. Nest can't repair that."
The experts at TrapX were also able to load their software onto the Nest's ARM7 processor chip, a procedure that allowed them to access various information managed by the thermostat, including the Wi-Fi password for the local network and data related to the presence of users at home.
The experts discovered that the network traffic generated by the Nest device was not encrypted. By exploiting the ARP protocol, the researchers forced other devices in the same network to exchange data with the compromised Nest device. They were able to exploit the device as an entry point in the host network; using it, they were able to localize other appliances, including a baby monitor, and hack them.
"In testing, TrapX was able to go through the compromised thermostat to exploit known software vulnerabilities found in devices like baby monitors and even a PC with an older, unpatched operating system to gain control of them," reported Forbes in a blog post.
"Once we're inside the network, it's quite trivial to escalate," said Carl Wright, executive vice president and general manager at TrapX. "There's a lot of devices in the home we're able to jump off of and compromise."
Despite there is no evidence that a Nest device has ever been compromised in the wild, the case presented highlights once again the need of security by design for IoT devices.
The surprises don't end here: Do you know smart light bulbs?
Also these components of a modern home could be exploited to enter into our everyday life.
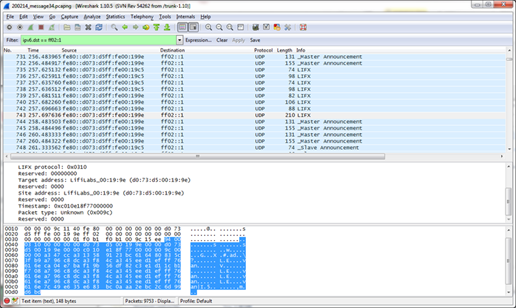
Last year, experts at Context Information Security firm discovered a security vulnerability in LIFX smart LED light bulbs.
The Wi-Fi-enabled bulbs can be remotely controlled via mobile devices. By exploiting the flaw, an attacker was able to access the master bulb and control every other connected light bulb in the house and expose user network configurations.
The architecture, LIFX, is based on a meshed network; it requires that only one bulb has to be connected to the Wi-Fi at a time. The experts at Context Information Security were able to analyze the traffic on the mesh network, identifying the packets used to share the encrypted network configuration among the bulbs on the network.
Figure 4 - Light Bulb Mesh Network Data Traffic
Once the traffic was identified, the researchers injected packets without any authentication into the mesh network interfering with the bulbs.
The company promptly identified the vulnerability with the support of the experts at Context Information Security and released a firmware update to fix it.
Figure 5 - Smart Light Bulbs
"It should be noted, since this attack works on the 802.15.4 6LoWPAN wireless mesh network, an attacker would need to be within wireless range, ~30 meters, of a vulnerable LIFX bulb to perform this attack, severely limiting the practicality for exploitation on a large scale," states the official blog post of Context.
A Prying Eyes in Our Homes
Let's close our short tour by introducing another category of smart device that recently raised a heated debate on the security of IoT devices in our homes, the baby monitors.
Security researchers from Rapid7 have discovered major security flaws in popular networked video baby monitor products that could allow attackers to snoop on babies and families.
Rapid7 analyzed baby monitors from six vendors, ranging in price from $55 to $260, in order to evaluate their overall security. The list of baby monitor analyzed includes the Philips In.Sight B120/37, the iBaby M3S and M6 models, the Summer Infant Baby Zoom, TrendNet Wi-Fi Baby Cam, the Lens Peek-a-View, and a Gynoii device.
"I really wanted to figure out if cameras of a higher price [range] were more secure or less secure," he explained.
The flaws discovered in the baby monitors represent a serious threat to the privacy of the families. Baby monitors are smart devices, always online and equipped with a camera and a microphone, all the necessary equipment to spy on the surrounding environment.
The researchers have discovered numerous security issues, such as hardcoded backdoor credentials, a privilege escalation bug in one of the baby monitors, an authentication bypass flaw in another, a direct browsing flaw in another, an information leakage flaw in another, and a reflective, stored cross-site scripting (XSS) bug in another.
Baby Monitors are wrongly considered secure and harmful devices by families that completely ignore the risks of a cyber attack, and hackers could exploit the lack of security by design of these devices that could become the entry point in domestic environments.
"It's a safety device that seems innocuous and friendly," explained Stanislav.
The researchers from Rapid7 haven't discovered evidence of mass exploitation of the baby monitors, despite the fact that none of them had been already fixed.
The Philips Electronics audio/video In.Sight Wireless HD Baby Monitor B120E/37 was affected by three of the vulnerabilities, hardcoded credentials, reflective and stored XSS in the cloud-based Web service, and a flaw in the remote viewing feature.
Figure 6 - Baby Monitor
The attacker can exploit the flaws to access the device and open a video stream without authentication.
"It's exposing the entire camera Web app server on the Net," explained Stanislav. "If you connect to the device and you're not the person who initiated the connection and is authorized to view it, you shouldn't" be allowed to view it, he says. "The vuln is [that it's] not requiring any authentication," he says.
Philips promptly replied to the report by providing a timeline for patches; the company added that the Philips device is now managed by Gibson Innovations. The patches are expected to release by September 4.
"As part of our responsible disclosure policy and processes, Philips has been in contact with both Gibson Innovations and the security research firm investigating this issue, to promptly and transparently address known and potential vulnerabilities in Philips products," a Philips spokesperson said.
Another disconcerting aspect of the story is that it is very easy to discover baby monitors, and other IoT devices, online by using the Shodan search engine for internet-connected devices.
In the following table are reported the vulnerabilities discovered by the researchers:
Remote
R7-2015-11.1
Predictable Information Leak
iBaby M6
Local Net, Device
R7-2015-11.2
Backdoor Credentials
iBaby M3S
Local Net, Device
R7-2015-12.1
Backdoor Credentials
Philips In.Sight B120/37
Remote
R7-2015-12.2
Reflective, Stored XSS
Philips In.Sight B120/37
Remote
R7-2015-12.3
Direct Browsing
Philips In.Sight B120/37
Remote
R7-2015-13.1
Authentication Bypass
Summer Baby Zoom Wi-Fi Monitor & Internet Viewing System
Remote
R7-2015-13.2
Privilege Escalation
Summer Baby Zoom Wi-Fi Monitor & Internet Viewing System
Local Net, Device
R7-2015-14
Backdoor Credentials
Lens Peek-a-View
Local Net
R7-2015-15
Backdoor Credentials
Gynoii
The problem is not new and it is extended to common IP cameras used for domestic surveillance.
Early 2014, a bug in the software that powers a broad array of Webcams, IP surveillance cameras, and baby monitors made by the Chinese camera giant Foscam allowed anyone to access the connected device and view live and recorded video footage.
In 2012, a group of researchers revealed that a large number of IP cameras made by TRENDnet were affected by a similar flaw.
In that circumstance, the instructions to access the IP cameras worldwide were available online; a number of websites published the links to the compromised feeds.
Other website started to publish nudity image taken with the hacked cameras; screenshots were made and posted to 4chan.
A hacker can easily locate the IP address of a poorly configured IP camera and hack it once necessary information on the model is collected. Specialized search engines like SHODAN make easy the research and hackers can use them to pinpoint flawed IP cameras.
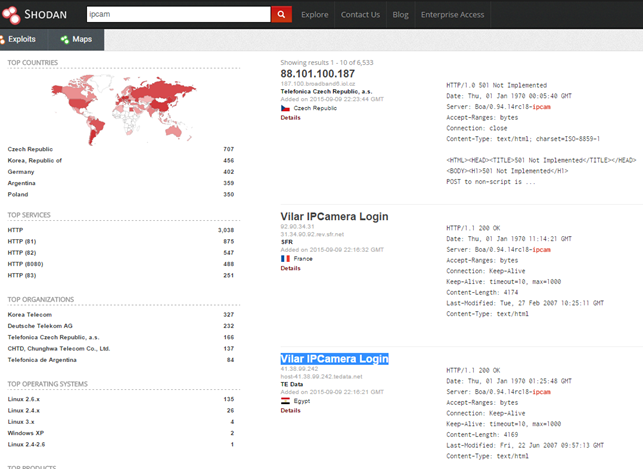
Figure 7 - SHODAN search engine
Conclusions
I have presented just a few examples of Internet of Things easy to find in modern homes. These smart devices in many cases are poorly configured and lack security by design, opening the domestic network to cyber intruders.
We cannot forget that IoT devices are always connected to the Internet and for this reason are easy to find and exploit by hackers by using search engines like SHODAN.
It is curious to think that users buy IoT devices to make their home more comfortable and secure, but instead they are opening the door of their home to crooks and hackers.
References
http://securityaffairs.co/wordpress/33238/digital-id/samsung-smarttv-privacy-issue.html
http://securityaffairs.co/wordpress/39811/hacking/hacking-baby-monitors.html
http://securityaffairs.co/wordpress/29353/security/smart-meters-hacking.html
http://securityaffairs.co/wordpress/33950/hacking/samsung-smarttv-issues.html
http://securityaffairs.co/wordpress/34576/hacking/hacking-nest-home-networks.html
http://www.theverge.com/2012/2/3/2767453/trendnet-ip-camera-exploit-4chan
http://krebsonsecurity.com/2014/01/bug-exposes-ip-cameras-baby-monitors/
https://www.synack.com/labs/blog/home-automation-benchmarking-results/
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
http://uk.businessinsider.com/how-smart-homes-can-be-hacked-2015-7?r=US&IR=T