Hacking Air-Gapped Networks
Introduction
Air-gapped networks aren't totally secure, there are several ways to exfiltrate information from computers isolated from the internet. Each technique relies on a different vector to carry out data, from acoustic to electromagnetic waves.
The methods could also be exploited to exfiltrate information from Internet-connected systems whose network traffic is carefully monitored and inspected to avoid the theft of sensitive data.

FREE role-guided training plans
March 2105 - BitWhisper – hacking Air-Gapped PCs through heat emissions
In 2015, security researchers at the Israeli Ben Gurion University (Mordechai Guri, Matan Munitz and the professor Yuval Elovici) devised a method to establish a covert channel that can be used to steal information from computers in air-gapped networks by detecting the heat from one computer to a near machine.
The technique was dubbed BitWhisper and can be exploited to steal sensitive data like encryption keys and more, in general, any kind of data.
The method allows to establish a bridge between the two computers, the BitWhisper, and the researchers demonstrated how to exploit it to transfer information between the two air-gapped systems. The channel relies on something so called "thermal pings," a term used by the experts to identify the repeated fusion of two networks via proximity and heat.
The BitWhisper technique allows to establish a bidirectional communication channel between two computers by using the heat emitted by various internal components. The experts explained that to steal information from an isolated PC, it is necessary to infect a computer in the same air-gapped network.
"BitWhisper provides a feasible covert channel, suitable for delivering command and control (C&C) messages, and leaking short chunks of sensitive data such as passwords," continues the paper.
Figure 1 - BitWhisper Attack
The researchers published the paper, entitled "BitWhisper: Covert Signaling Channel between Air-Gapped Computers Using Thermal Manipulations," that describe the BitWhisper technique and findings of their experiment.
"At this stage, the attacker can communicate with the formerly isolated network, issuing commands and receiving responses," states the report.
The experts placed two computers at up to 15 inches from each other, then they tried to transmit up to 8 bits of data per hour, an amount of information that could be enough to steal sensitive data like user's login credentials, secret keys, or to send commands to any agent listening on the target machine.
In their experimental scenario, the researchers placed two computers parallel to each, one of the machines was connected to the Internet, and the other one was connected to the air-gapped network.
The researchers installed a malicious code on both computers, on sender-end, the heat generated by internal component workload (i.e. CPU, GPU) is transferred to the recipient which monitors the changes in temperature.
"BitWhisper establishes a covert channel by emitting heat from one PC to the other in a controlled manner. By regulating the heating patterns, binary data is modulated into thermal signals. In turn, the adjacent PC uses its built-in thermal sensors to measure the environmental changes. These changes are then sampled, processed, and demodulated into binary data," explained the researchers.
The BitWhisper attack is very complex, but it is very interesting because it doesn't require any dedicated or modified hardware.
Below is the BitWhisper video proof of concept.
June 2015 - Stealing crypto-keys from PCs using leaked radio emissions
The researchers Daniel Genkin, Lev Pachmanov, Itamar Pipman and Eran Tromer from Tel Aviv University started from research conducted by Genkin with his colleagues on the possibility to exfiltrate data from an isolated PC by analyzing the CPU sound emitted during a decryption routine.
Genkin demonstrated how to break 4096-bit RSA, and he alongside his new team, explained that encryption keys can be accidentally leaked from a PC via radio waves.
At the time of the first Genkin's research, the experts demonstrated how to extract private decryption keys from GnuPG on laptops within seconds by analyzing the electromagnetic emanations during the decryption of a chosen ciphertext.
In their second experiment, Genkin and his colleagues measured emissions within 1.6 and 1.75 MHz by using the Funcube Dongle Pro+ connected to a the Android embedded computer Rikomagic MK802 IV.
Figure 2 - Equipment used for the tests
The details of the experiment conducted by the group were reported in a paper titled "Stealing Keys from PCs using a Radio: Cheap Electromagnetic Attacks on Windowed Exponentiation,"
The researchers used a standard AM radio with the output audio recorded by an Android mobile device, they have successfully extracted keys from laptops of several models running GnuPG within a few seconds.
"We demonstrate the extraction of secret decryption keys from laptop computers, by non-intrusively measuring electromagnetic emanations for a few seconds from a distance of 50 cm. The attack can be executed using cheap and readily-available equipment: a consumer-grade radio receiver or a Software Defined Radio USB dongle. The setup is compact and can operate untethered; it can be easily concealed, e.g., inside pita bread. Common laptops, and popular implementations of RSA and ElGamal encryptions are vulnerable to this attack, including those that implement the decryption using modern exponentiation algorithms such as sliding-window, or even its side-channel resistant variant, fixed-window (m-ary) exponentiation." states the paper.
"We successfully extracted keys from laptops of various models running GnuPG (popular open source encryption software, implementing the OpenPGP standard), within a few seconds. The attack sends a few carefully-crafted ciphertexts, and when these are decrypted by the target computer, they trigger the occurrence of specially-structured values inside the decryption software. These special values cause observable fluctuations in the electromagnetic field surrounding the laptop, in a way that depends on the pattern of key bits (specifically, the key-bits window in the exponentiation routine). The secret key can be deduced from these fluctuations, through signal processing and cryptanalysis."
The technique exploited by the experts was not new at the time of the study, despite the success of the attack the researchers highlighted that it may be difficult to realize because computers elaborate multiple tasks at the same time making impossible to analyze the emissions related to a specific activity such as the execution of the decryption routine.
July 2015 - Hacking Air-gapped networks via a low-end basic phone.
Almost any sensitive work environment has strict security measures in place, the use of the air-gapped computers is very common such as the prohibition for the internal staff from inserting any USB stick into the computers. Security policies forbade employees from carrying their smart phones with them, especially when the work involves sensitive trade secrets or the management of classified information.
How to hack an extremely secure computer device isolated from the Internet?
You might be surprised that you don't need any technical skill or equipment to achieve that. To hack into an Air-Gapped computer all, you'd need is a simple cell phone. Even an old fashioned, dumb mobile from the past decade should work for you as well.
A team of Israeli security researchers devised a new attack to exfiltrate data from a computer device that's isolated from the web.
Figure 3 - Hacking Air-Gapped network with a mobile phone
This hack being capable of stealing data from a very secure computer makes use of:
GSM network
A basic low-end cell phone
Electromagnetic wave
Moradechai Guri is the lead security researcher behind this interesting study, he worked with the colleagues Gabi Kedma, Yisroel Mirsky, Ofer Hasson, Assaf Kachlon and Yuval Elovici.
The team of experts have used a nine-year-old Motorola C123 mobile phone to carry on the attack. The expert installed a particular malware on both, the target computer and mobile phone. Data got exfiltrated via computers that normally emit electromagnetic waves, these waves were captured by the researchers by using a malware they developed.
This means that attackers first need to hack the target computer to install the malicious code, then they steal any data from the isolated PC.
Unlike some other "recent work in this field, [this latest attack] exploits components that are virtually guaranteed to be present on any desktop/server computer and cellular phone," researchers explain in their research paper.
August 2015 - Funtenna can remotely steal data from air-gapped network using sound waves
Another method to send out data from a computer inside an isolated network leverages on sound waves. A group of experts developed an innovative hacking technique called Funtenna, which could be used by an attacker to exfiltrate data from a targeted computer even if it is in an Air-gapped network.
"Funtenna is a software-only technique which causes intentional compromising emanation in a wide spectrum of modern computing hardware for the purpose of covert, reliable data exfiltration through secured and air-gapped networks. We present a generalized Funtenna technique that reliably encodes and emanates arbitrary data across wide portions of the electromagnetic spectrum, ranging from the sub-acoustic to RF and beyond.
"The Funtenna technique is hardware agnostic, can operate within nearly all modern computer systems and embedded devices, and is specifically intended to operate within hardware not designed to act as RF transmitters." states the description of the talk at the Black Hat conference.
The importance of this discovery is enormous, as explained by the researcher Ang Cui of the Red Balloon Security firm. The Funtenna radio signal hack could allow attackers to exploit Internet of Things devices to spy on any target. Gaming console, printer, washing machine and refrigerators could steal data from computers, even if they are isolated from the Internet.
Also, in this case, it is necessary that the target computer is compromised, the attackers have to install malware that is used to control the electronic circuit of the device (general-purpose input/output circuits), the data are sent out through signals generated by vibrating them at specific frequencies.
Figure 4 - Funtenna attack
The attacker then captures the signals generated by the vibrations by using an AM radio antenna, the Funtenna, that could be located at a short distance.
The Funtenna hacking method allows an attack to bypass any network security solution, the researchers also provided a Video PoC of an attack scenario.
https://www.youtube.com/watch?v=E4uo_F37qNE
"You have network detection, firewalls… but this transmits data in a way that none of those things are monitoring, this fundamentally challenges how certain we can be of our network security," explained Cui.
June 2016 - How to steal encryption keys from the air through a PC's noises
A team of Israeli researchers (Daniel Genkin, Lev Pachmanov, Itamar Pipman, Adi Shamir, Eran Tromer) demonstrated how to steal a 4,096-bit encryption key by using acoustics from distances of around 10 meters (33 feet) from an air-gapped system. The technique is also very fast, the experts exfiltrated the key in just a few seconds.
The same team demonstrated in 2015 that encryption keys can be accidentally leaked from a PC via radio waves, then they demonstrated that this is possible by using a cheap consumer-grade kit.
Now, the researchers exploited the fact that the processor emits a high-frequency "coil whine" from the changing electrical current flowing through its components.
"The power consumption of a CPU and related chips changes drastically (by many Watts) depending on the computation being performed at each moment. Electronic components in a PC's internal power supply, struggling to provide constant voltage to the chips, are subject to mechanical forces due to fluctuations of voltages and currents. The resulting vibrations, as transmitted to the ambient air, create high-pitched acoustic noise, known as "coil whine," even though it often originates from capacitors. Because this noise is correlated with the ongoing computation, it leaks information about what applications are running and what data they process." reads the paper published by the experts.
"Most dramatically, it can acoustically leak secret keys during cryptographic operations. By recording such noise while a target is using the RSA algorithm to decrypt ciphertexts (sent to it by the attacker), the RSA secret key can be extracted within one hour for a high-grade 4,096-bit RSA key."
The principal drawback of the technique is that equipment is difficult to conceal, so the researcher tried to obtain the same results from a mobile phone's microphone placed 30 centimeters (12 inches) away from the target machine.

Figure 5 - An acoustic attack using a parabolic microphone (left) on a target laptop (right); keys can be extracted from a distance of 10 meters.
"We experimentally demonstrated this attack from as far as 10 meters away using a parabolic microphone (see Figure 5) or from 30cm away through a plain mobile phone placed next to the computer." states the paper.
"In some cases, it even suffices to record the target through the built-in microphone of a mobile phone placed in proximity to the target and running the attacker's mobile app."
The team is able to get the 4,096-bit RSA key in an hour of listening, even using a mobile phone.
"Side-channel leakage can be attenuated through such physical means as sound-absorbing enclosures against acoustic attacks, Faraday cages against electromagnetic attacks, insulating enclosures against chassis and touch attacks, and photoelectric decoupling or fiber-optic connections against 'far end of cable' attacks." said the experts.
The researchers provided recommendations to prevent such kind of side-channel attacks, in the specific case they suggest using acoustic dampening inside a PC.
They also suggest that coders insert in their software "blinding" routines that perform dummy calculations into cryptographic operations, in this, it is possible to prevent a wide range of side-channel attacks, including the acoustic one.
June 2016 - Fansmitter – exfiltrating data from Air-Gapped devices via fan noises
Once again the researchers at the Ben-Gurion University of the Negev led by Mordechai Guri have presented an acoustic data exfiltration method that leverages on a mobile phone placed in the vicinity of the targeted machine to monitor the computer fans (i.e. CPU and chassis fans), for this reason, the technique was dubbed Fansmitter.
The experts developed a malicious code that is able to control the fans of the device to exfiltrate data, the technique allows to send out bits of data to the mobile phone or any other nearby computer equipped with a microphone.
"Past research has demonstrated that malware can exfiltrate information through an air-gap by transmitting audio signals from the internal or external speakers of desktop computers." reads the Fansmitter paper published by experts.
"Using Fansmitter attackers can successfully exfiltrate passwords and encryption keys from a speakerless air-gapped computer to a mobile phone in the same room from various distances," researchers wrote in their paper. "Beyond desktop computers, our method is applicable to other kinds of audioless devices, equipped with cooling fans (various types and sizes of fans) such as printers, control systems, embedded devices, IoT devices, and more."
The tests conducted by the team demonstrate that researchers are able to analyze the frequency and the strength of the acoustic noise emitted by fans that depend on revolutions per minute (RPM). The malware developed by the researchers is able to control the fan rotation producing specific noises that are associated with binary digits (0,1).
The noise produced by the fan is included in the 100-600 Hz range. This range of noise is audible by humans, so to avoid detection, the researchers can instruct the malware for transmitting data during hours when no one is in the room.
The experts used a common Dell desktop computer with CPU and chassis fans for their test session, noises were captured with a Samsung Galaxy S4 smartphone. It is interesting to note that the experts conducted the test in the presence of other background noises produced by other computers in their lab and the air conditioning system.

Figure 6 - Fansmitter attack scenario
The results were very interesting, the experts transmitted 3 bits per minute using low frequencies (1000 RPM for "0" and 1600 RPM for "1") over a distance of one meter, this means that each character of a password or an encryption key could be sent out in just three minutes
Increasing the frequency in the Fansmitter, it is possible to have a better transfer rate, for example, using a rotation range of 2000-2500 RPM the experts transferred 10 bits per minute over a four-meter distance. At 4000 – 4250 RPM, the team transmitted 15 bits per minute over a one-meter distance.
July 2016 - DiskFiltration – hacking air-gapped networks with acoustic signals
The DiskFiltration is a hacking technique that was devised by a group of researchers from the Ben-Gurion University.
The team, composed of the experts Mordechai Guri, Yosef Solewicz, Andrey Daidakulov, and Yuval Elovici, devised a method to steal data from isolated networks relying on acoustic signals emitted from the hard drive of computers.
The experts published a paper titled "DiskFiltration: Data Exfiltration from Speakerless Air-Gapped Computers via Covert Hard Drive Noise" the contains a detailed analysis of the technique.
The DiskFiltration leverages on the interpretation of the sounds emitted by hard drives during the movements of the actuator component, which is the arm that accesses specific parts of disk allowing read or write data.
The movements of the actuator are called 'seek operations,' the noise produced while accessing a data could be analyzed to discover the content accessed on the hard drive, including passwords and cryptographic keys.
The researchers also published a video Proof-of-Concept of the method.
The experts conducted several tests to analyze the efficiency of the DiskFiltration technique. They demonstrated that the attack method is effective in a range of six feet, it could be used to transfer 180 bits per minute, a speed that could allow exfiltrating a 4096-bit key in about 25 minutes.
The DiskFiltration technique is effective, the tests demonstrated that it also works when the hard drive uses a system to reduce the acoustic noise. The unique problems noticed by the experts were observed in the presence of casual noise emissions from other running processes, in this scenario they can sometimes interfere with exfiltration technique.
"Since our covert channel is based on HDD activity, casual file operations of other running processes may interfere with the transmissions and interrupt them." the researchers wrote in their paper.
In the following table are reported the countermeasures to mitigate the DiskFiltration attack (hardware based, software based, and procedural based measures)
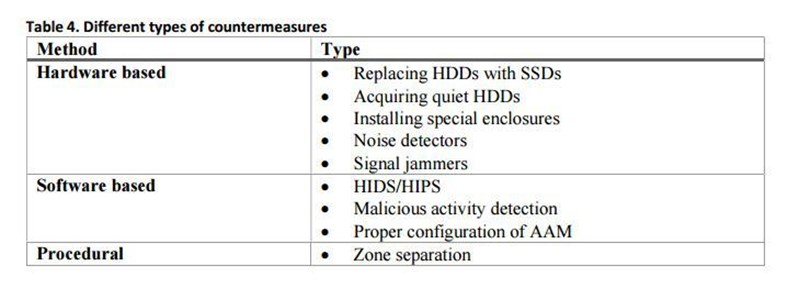
Figure 7 - Countermeasures for the DiskFiltration attack
August 2015 - USBee exfiltrates data from Air-Gapped networks via electromagnetic emission from USB
Mordechai Guri, head of R&D at Ben-Gurion's Cyber Security Center and the chief scientist officer at Morphisec Endpoint Security, and his team have devised a new technique dubbed USBee to hack air-gapped networks and exfiltrate information.
The Israeli researchers exploited covert-channel via electromagnetic emission from USB. The USBee technique leverages USB connectors implanted with RF transmitters to steal sensitive data.
In this scenario, the USBee application is installed on a compromised computer. The attacker exploits a USB thumb drive already connected to the computer and establish a short-range RF transmission modulated with data. On the other end of the communication, the data transmitted is received by a nearby receiver and decoded.

Figure 8 -USBee attack
"In recent years researchers have demonstrated how attackers could use USB connectors implanted with RF transmitters to exfiltrate data from secure, and even air-gapped, computers (e.g., COTTONMOUTH in the leaked NSA ANT catalog). Such methods require a hardware modification of the USB plug or device, in which a dedicated RF transmitter is embedded." reads the introduction to the paper published by the experts. "In this paper we present USBee, a software that can utilize an unmodified USB device connected to a computer as a RF transmitter. We demonstrate how software can intentionally generate controlled electromagnetic emissions from the data bus of a USB connector. We also show that the emitted RF signals can be controlled and modulated with arbitrary binary data. We implement a prototype of USBee and discuss its design and implementation details including signal generation and modulation. We evaluate the transmitter by building a receiver and demodulator using GNU Radio. Our evaluation shows that USBee can be used for transmitting binary data to a nearby receiver at a bandwidth of 20 to 80 BPS (bytes per second)."
The researchers discovered that the transmission of a sequence of '0' bits to a USB port generates a detectable emission between 240ℎ and 480ℎ. The researchers exploited this mechanism by sending data from the compromised computer to a USB device to generate controllable EMR that can carry modulated data. The researcher used a nearby RF receiver to receive the EMR and decode the information.
Guri and his team were able to exfiltrate 80 bytes per second using this technique, a transmission speed that could allow an attacker to send out a 4,096-bit crypto key in less than 10 seconds, very interesting when hacking air-gapped networks if compared with other hacking techniques.
The experts explained that it is possible to create a basic carrier wave using this algorithm:
inline static void fill_buffer_freq
(u32 *buf, int size, double freq)
{
int i = 0;
u32 x = 0;
double t = freq / 4800 * 2;
for (i = 0, x = 0x00000000; i<size*8; i++)
{
x = x<<1;
if ((int)(i*t)%2==0)
x++;
if((i%32)==31)
{
*(buf++) = x;
x=0x00000000;
}
}
}
The transmission starts when the application writes the fill_buffer_freq to an arbitrary data block in the USB device, the application just requires the permission to create a file on the device.
"The actual data transmission is done by writing the byte pattern generated by fill_buffer_freq to an arbitrary data block or stream in the USB device. For our purposes, we used a temporary file within the USB thumb drive's file system. The transmission process doesn't require special privileges (e.g., root or admin). It only requires permission to create a file on the removable device." reads the paper.
The researchers also published a video PoC of the attack that shows how the data is exfiltrated by a laptop with a $30 radio antenna from around 15 feet away.
Conclusions
An Air-gapped network still represents a stringent security measure when it is necessary to isolate a system from the Internet to preserve it and the data it manages, typical applications are military networks and industrial control systems architectures.
Unfortunately, a persistent attacker could bypass the security measure in different ways, by infecting a network with a USB key, like happened to the Stuxnet virus or the Fanny tool used by the Equation Group APT).
The method exposed demonstrated that an attack against a system isolated from the Internet is possible.
Nothing is totally secure!
References
http://securityaffairs.co/wordpress/50245/hacking/diskfiltration-air-gapped-networks.html
http://securityaffairs.co/wordpress/35298/hacking/bitwhisper-air-gapped-pcs.html
http://securityaffairs.co/wordpress/38908/hacking/air-gapped-computer-hacking.html
http://securityaffairs.co/wordpress/48025/hacking/encryption-keys-exfiltration.html
http://securityaffairs.co/wordpress/48678/hacking/fansmitter-exfiltrating-data.html
http://securityaffairs.co/wordpress/39167/hacking/funtenna-hacking-technique.html
http://securityaffairs.co/wordpress/37950/hacking/stealing-crypto-keys-radio-emissions.html
https://www.rt.com/usa/311689-funtenna-hacking-sound-waves/
http://cyber.bgu.ac.il/blog/bitwhisper-heat-air-gap
https://arxiv.org/abs/1608.03431
http://www.tau.ac.il/~tromer/radioexp/
http://cacm.acm.org/magazines/2016/6/202646-physical-key-extraction-attacks-on-pcs/fulltext
https://arxiv.org/ftp/arxiv/papers/1606/1606.05915.pdf
https://www.usenix.org/conference/usenixsecurity15/technical-sessions/presentation/guri
http://securityaffairs.co/wordpress/50811/hacking/usbee-air-gapped-networks.html

What should you learn next?