Hackable Medical Devices
Introduction
Technology in healthcare has gone through incredible changes over the years. There are multiple options for wearable or implantable biomedical devices that have wireless capabilities.
Implementing HIPAA Controls
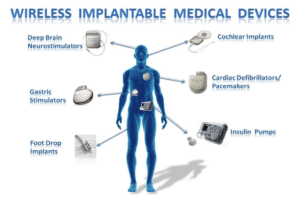
Some medical devices are in receive-only mode, or exclusively send information instead of receiving any, but some both send and receive, which are the most vulnerable of devices; but anything connected to the internet is at risk. Infusion pumps, surgical robots, pacemakers, insulin pumps, and cochlear implants are some of the devices that are wireless capable. Some of these have already been penetrated by security researchers and others are being evaluated, as the potential is there. Many security researchers are questioning if medical device hacking will be the biggest concern in upcoming years.
Warnings have been issued and guidelines have been created, but these guidelines don’t seem strong enough. The FDA, in collaboration with other federal departments, delivered a guidance document to provide some tips for cybersecurity considerations in medical devices. This document is not written as an enforceable decree, but merely as suggestions for those creating, manufacturing, and distributing wireless capable medical devices.
Some security functions that were suggested in the document include:
Limited access to the device by ensuring/enforcing:
- User authentication
- Session termination/timed sessions
- Use of strong passwords
- Physical security measures (e.g. locks)
Trusted software content by:
- Restricting updates to authenticated users
- Encryption methods
Detect (any intrusion attempt)
Respond (to any intrusion attempt)
Recover (from a successful intrusion by removing any implanted malware)
Ransomware is considered the biggest security threat to biomedical devices. A Ensuring that these devices have some level of security embedded is dependent upon the manufactures. What increases the vulnerabilities is that the end user has no control of the security of the device. A savvy user can buy a new router and place best practice security measures on that router, but cannot make any updates to devices responsible for keeping them alive.
(As of this writing, we were only able to find examples of successful lab hacks. There have been breaches to the network by hackers but no admitted device breaches.)
Many researchers feel cybersecurity training should be included in modern medical training to help determine if equipment failure is due to a malfunction or an attempted attack. So far, there have been no documented cases of nefarious attacks against any medical devices, just researchers testing the capability of attacks being performed, but knowing the capability is there creates the need to develop procedures to help protect against possible attacks.
Hospital Networks
Hacking of medical devices could create a backdoor into hospital networks. Medical information is just as valuable, if not more, then financial and other personal data. There have been medical network breaches, but much of the information surrounding how the attacks happened has not been released. Researchers have been able to identify ways the vulnerabilities in these medical devices can create vulnerabilities into the network.
Below, we discuss some of these hackable medical devices.
Infusion Pump
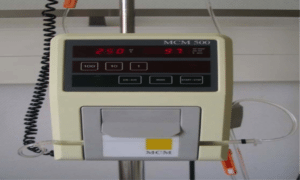
Infusion pumps are pre-programmed with a controlled amount of fluids that are to be delivered to a patient. These devices are normally used in a hospital or clinic setting while the patient is admitted. From 2005-2015, the FDA logged 56,000 reports of negative incidents with infusion pumps and some of these incidents involved fatalities. During the same time period, many manufactures of the pumps issued recalls. Due to these incidents, the FDA issued a report on the issues found with the pumps, and subsequently launched a pump improvement initiative. Some of the initial issues found were software errors, alarm errors, a questionably designed user interface that promoted user errors, over-heating batteries, and faulty electrical components that caused shocking and burning. None of the initial issues were cyber-related, outside of the software complaints, which consisted of an inoperable error appearing on the screen with no actual problem existing, and a single keystroke being interpreted as multiple keystrokes. It wasn’t until recently that researchers discovered the devices were vulnerable to hacking.
Hospira is one company that makes the pumps. The FDA issued a warning to the brand in reference to an exploitable vulnerability found in their pumps. The company was previously notified from cybersecurity researchers of vulnerabilities as well.
Surgical Robots
In 2001, a doctor in New York removed the gallbladder of a patient in France. This surgery was the first of its kind, a tele-surgery performed using a surgical robot. Having the ability to perform surgery from hundreds or even thousands of miles away has a number of benefits. The Department of Defense plans on using deployable "trauma pods" for surgery on soldiers while they are in the field. This type of technology could be used to operate on sailors on subs thousands of feet below sea level, helping to maintain operational status even in the case of an emergency. The problem is, a set of security researchers were able to control a surgical robot after remotely gaining access. They hacked into the router used by the doctor controlling the robot. By gaining control of the router they were then able to send commands that made the surgical actions performed by the robot shaky and erratic, as well as longer or shorter than initially intended (timing is very important in surgery). This triggered the automatic stop function embedded in the machine to halt the procedure, which allowed the white-hat hackers to take over the machine’s actions completely. There is no data encryption when information is transferred between the doctor and the robot which would be one big step in helping to better secure tele-surgery procedures. The video feeds are also easily accessible, as they are not securely authenticated and encrypted. Better network monitoring and sensitizing the software to errors and changes are movements in the right direction to making surgical robots more secure. The full report can be found here.
Pacemakers
iStan is a simulated human. “He” is a medical mannequin who was created to mimic human characteristics and to test the effects of certain drugs and to help medical students perform medical procedures without injuring an actual human.

A group of students used an iStan equipped with a pacemaker to test the possibility of hacking into the embedded pacemaker. These were not students with networking or IT expertise, but they were able to find some vulnerabilities within the network security and performed a brute force attack on the router the device was connected to. Once connected to the router, they were able to determine what software the iStan was using. Once it was determined that Adobe flash and Muse were being used, they penetrated a vulnerability within the software to gain control of the device and ultimately “kill” the patient by stopping the pacemaker from continuing to operate.
Insulin Pump
Insulin pumps are software-operated devices that are programmed to deliver a certain amount of insulin to diabetic patients to help them maintain appropriate glucose levels. It has been determined that much of the software used on these pumps is a bit out of date. During the 2013 Black Hat conference, it was demonstrated how to hack into an insulin pump and have it dump all of the medication at one time in order to kill a person. The specifics of the hack were not released, but with the outdated software it could be concluded that a vulnerability was exploited to gain control and dump the medication.

Conclusion
With the advances made in technology and medical devices, there are more opportunities to exploit wireless, implanted, biomedical devices and control the health, life, or death of patients. Many of these medical devices are using outdated software, not using encryption methods to ensure more secure communications, and even many hospitals where these devices could be used are not always using the most secure router and network settings, creating another avenue for hackers to penetrate these devices. With the issue of hackable devices and the grave results of a hack, many believe this is the number one cybersecurity issue to address. One step to alleviate this issue is having cyber-training included in medical training to help medical professionals identify intrusion attempts, implanted malware, or implanted ransomware that could turn a life saving device into an extortion tool. These devices are meant to save the lives of the patients they are issued to, so the manufactures and issuers should ensure that they don’t become weapons instead.
References
http://www.popsci.com/fda-issues-warning-cyber-security-risks-medical-devices
http://www.fda.gov/ucm/groups/fdagov-public/@fdagov-meddev-gen/documents/document/ucm356190.pdf
http://www.popsci.com/hackers-could-soon-hold-your-life-ransom-by-hijacking-your-medical-devices
http://www.popsci.com/robots-used-surgery-can-be-easily-hacked
http://arxiv.org/abs/1504.04339
http://arxiv.org/pdf/1504.04339v2.pdf
Implementing HIPAA Controls



