Forensic Artifact: Malware Analysis in Windows 8
Windows is the most used operating system worldwide. I have met a lot of IT guys in my country and also other computer elites. My discovery was that 90 percent of them use Windows. I felt maybe that was just in my country, then I decided to contact some friends from UK, USA, India, and Pakistan, and they said the same about the wide use of Windows OS in their countries. However, the case was a bit different for that of the guy in the USA and I also noticed that a lot of my friends there use the MAC OS X. This doesn't change the fact that Windows is still more used worldwide and because of this, hackers and intruders have had a lot more time to study Windows and create a lot of malware for it. The popular Windows OS has been tagged the most vulnerable OS. Now there is a new Windows OS. The question is: Is it vulnerable as well?
Learn Digital Forensics
This article focuses on the new version of Windows. Windows 8 was released on October 26, 2012. It was designed to work perfectly on a touch screen. The interface is so catchy!!
As a computer lover, I follow a page on Facebook named "computer freaks."

Recently, this picture was posted, showing that in the timeline of the Microsoft Windows operating system they have always had a good OS, then a bad OS, and then a good one again. Kind of like an arithmetic progression with a common difference of one among the good Windows operating system. Because of this, I decided to do an analysis on this Windows 8 edition of Microsoft Windows to see what will really make it bad or "SHIT," as the picture puts it.
I began to do research on Windows 8 and I discovered that three patches have already been released for Microsoft's new operating system. This reminds me of when Vista was released, there were so many patches that they just had to make a better version of Windows OS (Windows 7). I've used Windows 7 for a long time and I've also met some Windows 7 power users that can testify that it is a good one from Microsoft. However, I still think Windows XP stands a higher ranking when we focus on system stability.
Speaking more fully of malware, one of Microsoft's major objectives is to reduce the risk of their OS being infected by malware. As a result, several measures have been taken to reduce the chances of malware infection in Windows 8. Jason Garms of Microsoft has provided some tips on how to keep your PC free from malware in the link below:
http://blogs.msdn.com/b/b8/archive/2011/09/15/protecting-you-from-malware.aspx
Windows 8 has proven to be less vulnerable to malware, because the Windows Defender that comes with it is very active with good heuristics for detecting malwares. Even with all the new security, the common saying still remains true: there is no total security and therefore you cannot be totally secure from malware on Windows 8 but the risk of being affected by malware is just reduced. Windows 8 got better in a lot of ways to the point that their error page had a transformation.
This doesn't have to do with malware, but one thing I still don't like about the Windows OS is the inability to retain commands on the console (command prompt) after the cmd is closed and reopened. For those who work more on the console, you can imagine using a lot of very long commands and then, simply because you mistakenly closed this console session, when you open another, all those commands are gone and you need to retype them. This is unlike the terminal (console) in Linux.

I read and heard from different sources that Windows 8 was secure but I am a big time skeptic, so I had to prove it to myself. To be sure of the fact that Windows 8 is not so vulnerable to malware, I had to start by creating a proRAT Trojan server with my Windows 7 machine and then I sent it to my Windows 8. I have tried this Trojan several times and I'm no novice with it. I used it often in the days when I loved threatening schoolmates in the network, and I still have a good handle on it. As soon as I sent the server file to the Windows 8 OS with an external drive, Windows Defender deleted it. This was really amazing. I don't have any third-party AV installed and my computer could react that way with malware. I had even seen some Windows 7 OS with third-party AVs that will not detect the server file due to poor heuristics. However, one third-party AV you can rely on to some extent is Norton with its bloodhound heuristics. The image below is what I got when I put my Trojan server on Windows 8:

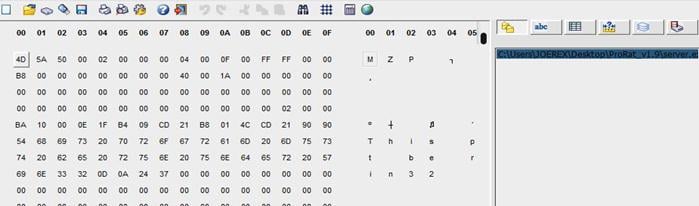
The image below contains the hexadecimal of the Trojan server that was used
Windows 8 is indisputably the most secure Microsoft Windows, but we cannot still match its malware detection with MAC OS X. I realized that the Windows 8 defender that protects us from malware is the popular Microsoft Security Essentials. It's good the way they saved us the cost of buying Microsoft Security Essentials separately.
There are interesting testimonies everywhere about Windows 8 and its safe usage and security but this doesn't make it impeccable. Although I've not personally found any faults in Windows 8, from my research I discovered that the new Windows version that was released already had its first security patch on November 13, 2012, which was just a few weeks after it was released.
Also, not that I'm very sure about this, but I came across an article that said the Bitdefender company had tested some malware on Windows 8 and one piece of malware had its way with Windows 8. This particular malware is capable of creating backdoors that allow hackers to remotely control the computer of the host and also to steal gaming credentials and a lot more.
However, the company used malware collected over the last six months, which is not ideal, because the test sample won't include every threat and also because every antivirus product misses some software nastiness, giving a greater chance to the attacker.
Bitdefender also tested the malware by fetching a copy of the malicious code from an internal FTP server and executing it to see how far the malware progresses--as opposed to visiting a booby-trapped web page that attempts to compromise the PC, which is a more common method of infection. In theory, there should be little difference, but this methodology bypasses Windows Defender's SmartScreen, which filters out phishing attacks and malware downloads when using Internet Explorer.
Well, this is not an issue to make you reconsider using Windows 8, because a lot of antivirus vendors are just trying to find a fault in the Windows Defender (built-in Microsoft Security Essentials) in order to provide a chance for their own AVs.
Another test I tried is the backdoor. I installed WAMP server in Windows 8 on my VMware and I tried to upload a backdoor shell onto it from my host operating system. I kept trying this but to no avail. Then I tried to manually drop the shell into the guest Windows 8 OS server directory. It turned out while cleaning up the file that I received a message notifying me that malware was detected and could not be accessed.
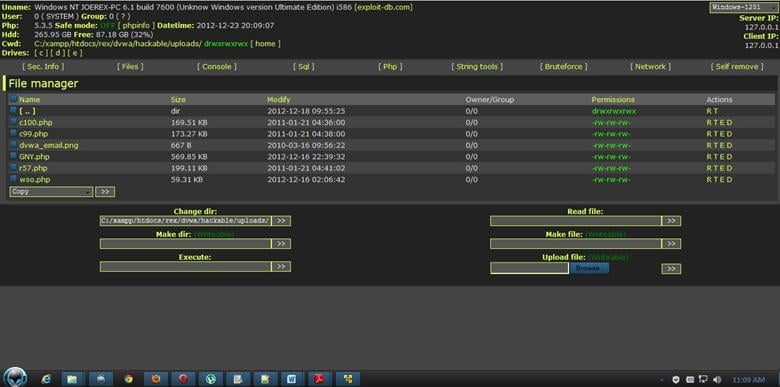
I know c99, c100, GNY, and r57 shells are very well-known and restricted by a lot of anti-malware programs. Because of this, I tried to use a WSO shell, but it was still functionless.
Left to me, I will say that Windows 8 is like a means to put an end to a hacker's invasion on web servers. Probably, if most webservers on Linux OS are moved to Windows 8, the hackers would have a lesser chance to upload backdoor shells to damage our web contents.
Since some of the antivirus companies have predicted future security shortcomings on the secure Windows 8, we also have to be prepared to keep our PCs protected.
I will start by providing you with good software for analyzing Windows executable files. With this software, you can check to see if there is anything attached with an executable application you want to run on your computer. It is called PEid, which identifies "portable executables."
Download with the MediaFire link: http://www.mediafire.com/?f2yu4wzbrq3bp2a
If it happens an attacker successfully finds way to drop his malware on your PC, you can also remove it manually from your computer, but you must be very careful because there are some malwares with anti-tracing features that can make your OS crash the moment you detect them.
So to find them, you will go to your registry and follow the given registry keys to check for these malwares:
HKEY_LOCAL_MACHINESoftwareMicrosoftActive SetupInstalled Components
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentversionexplorerUsershell folders
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServices
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrenVersionRunServicesOnce
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRunOnce
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerShell
HKEY_LOCAL_MACHINESoftwareMicrosoftActive SetupInstalled Components
HKEY_LOCAL_MACHINESystemCurrentControlSetControlVMM32Files
The reason for locating the malware yourself is because of polymorphic malwares. These are malwares that make it impossible for antivirus and firewalls to detect them.
Some of the malwares can make themselves run at your system startup by replicating themselves to the following:
Config.sys (a system32 folder)
Autoexec.bat (rootdrive)
System.ini (Windows folder)
Before using the registry keys to locate the files, you may consider disconnecting yourself from the network where it's likely an attacker is using the malware to attack you.
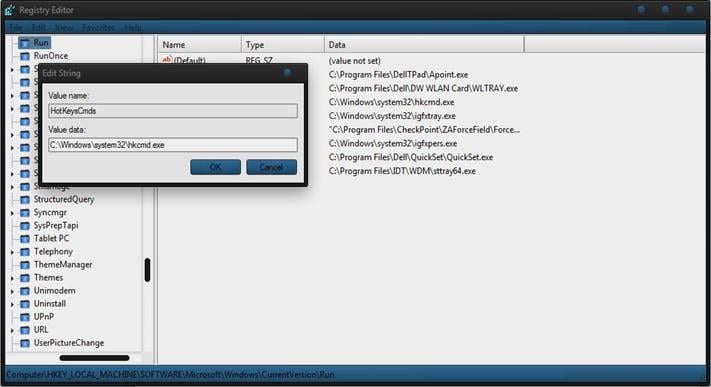
After locating any suspicious file in the registry keys, you can double-click the file to find its path, as the image below shows:
As a regular Windows user, you should know we can't delete files that are working in the background, so we need to check for this file in the task manager processes and stop it.
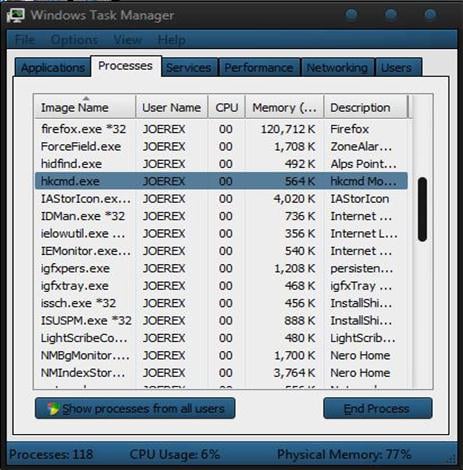
That's not malicious software, but it's the exact file I examined in the registry. If it were malicious, I would just click the "End Process" button to put an end to its work. Now you can go back to the directory you were given by the registry and delete the file. After this, you will need to restart your PC if you know the malicious software has not caused much damage to your computer. If it has eaten some of your system files up, you may need to upgrade your Windows OS by using an installation CD to go through the installation process again. This way your files remain intact in a folder, "WindowsOld," in your C: directory.
I have given a link to download the PEid. Now I will show you a little way to make use of this software in examining your executable files.
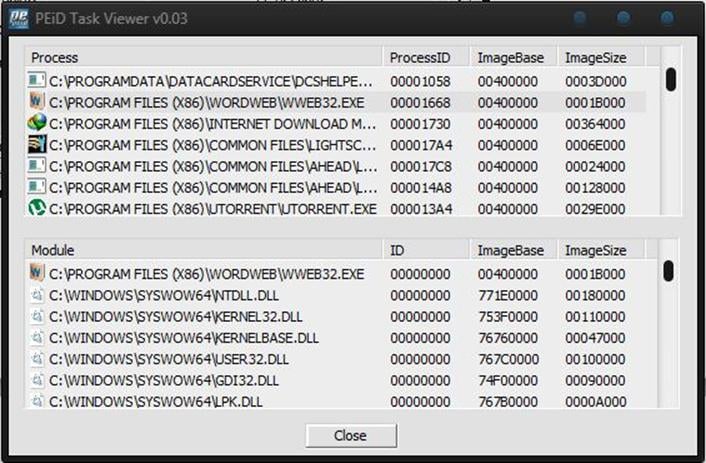
When you unpack the rar file I gave in the link, you will see an interface like the one below:
Do not mind the Windows Explorer look of my own software, it's just a skinpack. On your PC, the three blue dots should be minimize, maximize, and close button. To check details about a particular exe file, you can select the file in the first option of the PEid GUI.
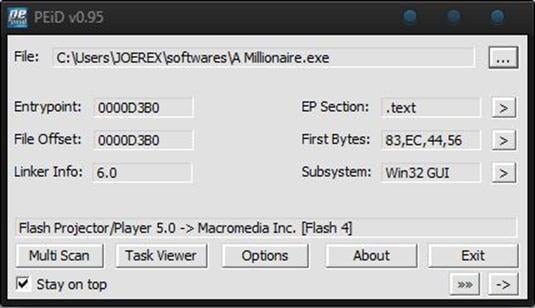
Now to check the active processes that may include the malware, you can click "Task Viewer," which gives you a result like the task manager does. When you select any task, it will show every file attached to the process and working with it. PEid is a really good solution for malware detection.
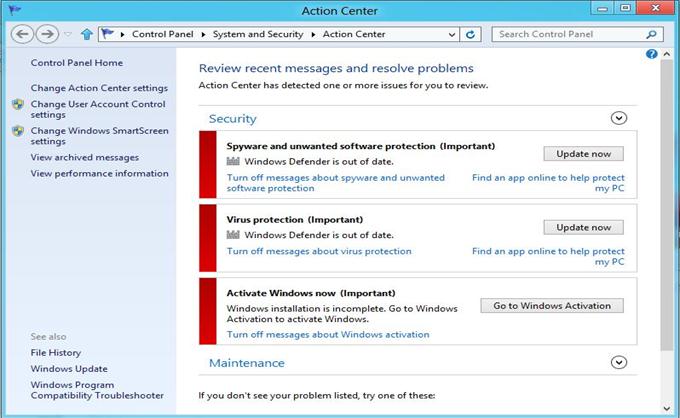
Windows 8 Defender uses the colors green, yellow, and red to show its security level. To make your Windows 8 more secure from malwares, I will advise that you should update Windows Defender as often as possible, as you would any third-party antivirus if you really want to stay secure.
Sometimes malware will be placed in software that you already have on your PC. For instance, suppose you downloaded a game that was functioning properly before it started malfunctioning. It is advisable to do an md5 checksum on downloaded files so when it gets suspicious, you can do a checksum again to compare with the previous test and then you will be able to say if it has been tampered with. You can download software for checking your md5 on Windows here:
http://www.4shared.com/zip/qsq6WC8O/NetTools4574.html
References
Learn Digital Forensics
http://www.pcworld.com/article/2013807/windows-8-already-getting-security-patches.html
http://blogs.msdn.com/b/b8/archive/2011/09/15/protecting-you-from-malware.aspx
http://www.anandtech.com/show/4822/windows-8-malware-protection-detailed
http://windows.microsoft.com/en-US/windows-8/windows-defender#1TC=t1
http://www.theregister.co.uk/2012/06/21/win8_security/





